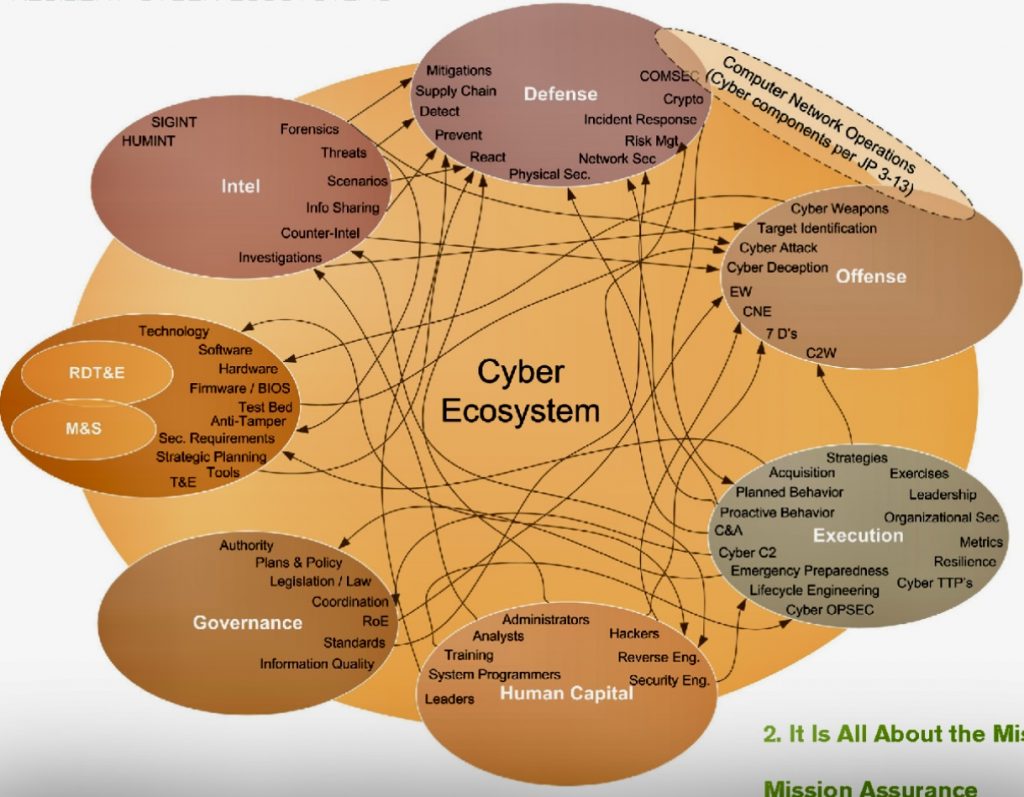
The cybersecurity ecosystem is a complex system that comprises numerous interconnected elements, each playing a crucial role in maintaining secure and reliable operations.
i. A cybersecurity ecosystem encompasses a wide range of stakeholders, including:
A. Cybersecurity vendors: Companies that develop and sell cybersecurity products and services, such as antivirus software, firewalls, and intrusion detection systems.
B. Cybersecurity service providers: Companies that provide cybersecurity services, such as penetration testing, vulnerability assessments, and incident response.
C. Third-Party Vendors: Sometimes, an organization’s security is only as strong as its weakest link, which can often be third-party vendors who have access to the organization’s data or systems.
D. Government agencies: Government agencies that play a role in cybersecurity, such as the National Security Agency (NSA) in the United States and the National Cyber Security Centre (NCSC) in the United Kingdom.
E. Academia: Universities and research institutions that conduct cybersecurity research and educate the next generation of cybersecurity professionals.
F. Non-profit organizations: Non-profit organizations that promote cybersecurity awareness and education, such as the SANS Institute and the International Information System Security Certification Consortium (ISC²).
G. Cybersecurity Teams: Security Professionals: Skilled cybersecurity professionals, including ethical hackers, analysts, incident responders, and Chief Information Security Officers (CISOs), who play key roles in implementing and managing security measures.
H. Technology Providers: Security Solution Vendors: Engaging with technology vendors to acquire and implement security solutions, ranging from antivirus software to advanced threat detection systems.
I. End users: Individuals and organizations that use technology, such as consumers, businesses, and governments.
J. Threat Actors: These include hackers, cybercriminals, insider threats, and nation-state actors. Their motivations can range from financial gain to espionage or even political disruption.
ii. Some of the key functions of the cybersecurity ecosystem
A. Identifying and assessing cybersecurity risks: The cybersecurity ecosystem helps to identify and assess cybersecurity risks by conducting research, developing threat intelligence, and sharing information about vulnerabilities and exploits.
B. Developing and deploying cybersecurity solutions: The cybersecurity ecosystem develops and deploys cybersecurity solutions to protect against cyber threats. This includes developing new products and services, updating existing solutions, and patching vulnerabilities.
C. Educating and training cybersecurity professionals: The cybersecurity ecosystem educates and trains cybersecurity professionals to help them develop the skills and knowledge they need to protect against cyber threats.
D. Responding to cyber incidents: The cybersecurity ecosystem responds to cyber incidents by investigating attacks, containing damage, and restoring systems.
E. Promoting cybersecurity awareness: The cybersecurity ecosystem promotes cybersecurity awareness to help individuals and organizations understand the importance of cybersecurity and how to protect themselves from cyber threats.
iii. Key elements within the cybersecurity ecosystem
A. Security Infrastructure: This includes hardware and software tools designed to guard against cyber threats. Examples include firewalls, intrusion detection systems, antivirus software, and encryption tools.
B. Threat Landscape: Cyber Threats: Various types of cyber threats, including malware, ransomware, phishing, and advanced persistent threats (APTs), continually evolve, posing risks to organizations and individuals.
C. Security Policies and Governance: Policy Frameworks: Establishing and enforcing cybersecurity policies and governance frameworks to define security controls, risk management, and compliance measures.
D. Regulatory Frameworks: Governments and industry bodies set standards and regulations that define minimum cybersecurity requirements. Examples include the General Data Protection Regulation (GDPR) in the EU, the Payment Card Industry Data Security Standard (PCI DSS), and the Health Insurance Portability and Accountability Act (HIPAA) in the US.
E. Data: This is what everyone in the ecosystem is ultimately trying to secure. It can include everything from customer information and intellectual property to employee records and financial data.
F. Network Security: Firewalls, IDS/IPS: Deploying network security solutions such as firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to safeguard networks from unauthorized access and malicious activities.
G. Endpoint Security: Antivirus, EDR: Implementing endpoint security measures, including antivirus software and Endpoint Detection and Response (EDR) solutions, to protect individual devices from malware and other threats.
H. Identity and Access Management (IAM): Authentication, Authorization: IAM systems manage user identities, ensuring appropriate access controls through authentication and authorization mechanisms.
I. Security Awareness Training: Employee Education: Providing ongoing cybersecurity awareness training to employees to enhance their understanding of security best practices and reduce the risk of social engineering attacks.
J. Incident Response and Forensics: IR Plans, Forensic Tools: Developing incident response (IR) plans and leveraging forensic tools to investigate and mitigate security incidents effectively.
K. Security Operations Center (SOC): SOC Analysts, SIEM: Operating a Security Operations Center with analysts monitoring security alerts using Security Information and Event Management (SIEM) tools to detect and respond to threats.
L. Encryption and Data Protection: Data Encryption: Implementing encryption mechanisms to protect sensitive data both in transit and at rest, mitigating the risk of unauthorized access.
M. Vulnerability Management: Scanning, Patching: Conducting regular vulnerability assessments, scanning systems for weaknesses, and applying patches to address identified vulnerabilities.
N. Security Intelligence: Threat Intelligence Feeds: Leveraging threat intelligence feeds to stay informed about the latest cyber threats, vulnerabilities, and adversary tactics.
O. Cloud Security: CASB, Cloud Security Policies: Implementing Cloud Access Security Broker (CASB) solutions and defining cloud security policies to secure data and applications in cloud environments.
P. Collaboration with Law Enforcement: Public-Private Partnerships: Collaboration with law enforcement agencies and public-private partnerships to share threat intelligence and address cybercrime.
Q. Regulatory Compliance: Compliance Frameworks: Adhering to regulatory compliance frameworks and industry standards to meet legal and industry-specific cybersecurity requirements.
R. Cyber Insurance: Insurance Policies: Obtaining cyber insurance policies to mitigate financial risks associated with cybersecurity incidents.
S. Research and Development: Innovation and Adaptation: Ongoing research and development efforts to innovate and adapt cybersecurity technologies and strategies to address emerging threats.
T. International Collaboration: Information Sharing: Collaboration on an international level for information sharing and coordinated responses to global cyber threats.
U. Cybersecurity Awareness Campaigns: Public Education Initiatives: Government and private-sector initiatives to raise awareness about cybersecurity risks and promote good cyber hygiene practices among the general public.
The cybersecurity ecosystem is dynamic and requires continuous adaptation to the evolving threat landscape. Collaboration, information sharing, and a holistic approach to security are essential for effectively safeguarding digital assets in this interconnected environment.
https://csrc.nist.gov/glossary/term/cyber_ecosystem
https://ieeexplore.ieee.org/document/10125775
