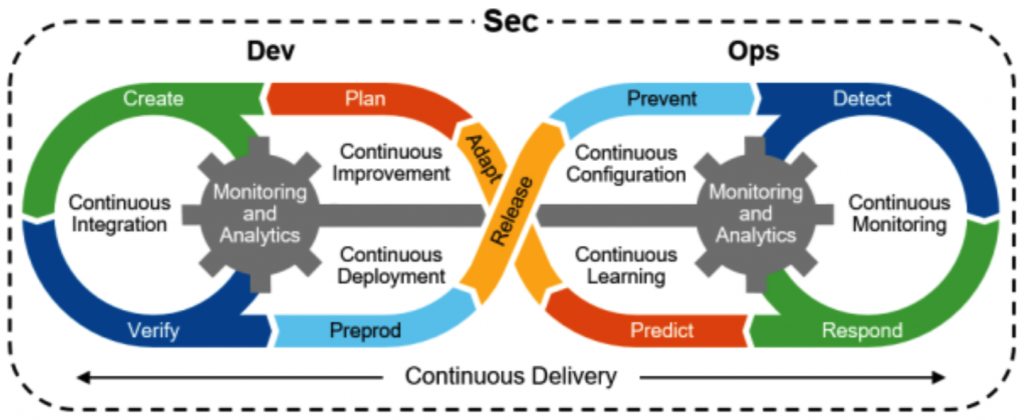
Software has already taken the world by storm, and the DevOps movement helped make that happen. IT organizations today are shipping software faster than ever and using technologies, including containers and Kubernetes, that blur the lines between application development and operations.
Even still, new technology and apps have a tendency to multiply security concerns. By embracing a DevSecOps mindset, organizations can take advantage of these technological advances without putting themselves or their customers at risk.
As time passes and the adoption of agile methodologies becomes more and more evident for all types of companies, we must ask ourselves again, if delivery and “Time to Market” is everything …
Many things can happen if we only pay attention to comply with tight times, due to pressure from the business itself, to have our products ready to be put into production. But we have done little to maintain and consider basic security things …
Such as the fact of trying to keep our old platforms up to date, or having a plan to migrate these old platforms as soon as possible and finally, continually continue to educate our users, informing them about the dangers that exist (and that really exist …) when, for example, we visit sites of which we know little or nothing or, of opening emails of which we do not know their senders and that we only do so because the title is looks attractive …
Every day we learn from the news about cyber-attacks on this or that company that has been a victim of these attacks and they intensify every day.
So … What to do? Are our users really aware that these attacks exist? Does our organization really know the risks?
To answer these questions, it is important to know if the organization for which we work or provide services is well trained regarding Cybersecurity issues, or if it has updated Cybersecurity Policies that are known by the entire organization. Perhaps this small but important point allows the risk of exposure to this type of attack to be somewhat minimized.
Among the activities to which we must pay attention first would be:
- Is there an updated Security Policy, known and used in the organization?
- Are our platforms updated?
- Do the workstations have Anti-malware and are they updated? How often?
- Are there tools to filter Internet content?
- Do users know who to turn to when faced with a potential Cybersecurity threat?
- Do we follow up on Cybersecurity incidents? …
Over the years, we have witnessed that companies make many efforts to cover Cybersecurity but many others simply think that a Systems area is only a consequence since the purpose of the business is a completely different one. That is when we allow incidents to occur in our organizations. As well as minimizing the probability of cyber-attacks, thinking that “this is not going to happen to us” …
We believe that the key points to pay close attention and dedicate an annual budget to raise the level of security in our organizations are:
- Assemble awareness programs consistent with the organization’s objectives and be aligned with the best Cybersecurity practices
- Constantly train our users regarding Cybersecurity incidents, measure their impact and follow up
- Encourage each user that Cybersecurity belongs to each of us and is not something isolated to IT Security areas.
- Have a short-term plan to depreciate those platforms that are obsolete or that are about to fulfill their life cycle and support.
- Apply restrictions on the users’ desktops in a centralized way to prevent the installation of non-approved Software, control of USB ports and mass storage.
- Have Antivirus platforms that are constantly updated and that offer EDR protection.
- Educate our users regarding the use of email and the Internet, indicating that it is a valuable asset for the organization.
- Do not share sensitive information about our organization regarding code developed and that you want to expose on tools for publishing and consulting other developers’ code.
- Work on an Internal Cybersecurity Regulatory Framework and make it known.
- Have tools for automated deployment of patches and hot fixes to avoid or minimize the risk of zero-day attacks and / or vulnerabilities.
- Implement a technological stack that supports the deployment and continuous integration (CI / CD) safely, applying controls and automated remediation by security stages.
- Declare those control points or touch points where the premises of Cybersecurity intersect with those business processes that are declared important, and follow up on them.
- Assemble and then publish a Cybersecurity Regulatory Framework for Software development.
- Work and then adopt a Secure Software Development Cycle or S-SDLC.
- Define a “Risk Appetite” in the organization.
- Work on a BIA and RIA to build DRP
