Implementing a secure BYOD (Bring Your Own Device) policy requires strategic planning along with robust security measures in place. Implementing such a policy involves a comprehensive approach that addresses both technology and people-related challenges.
Here are some steps that can enhance the security of your BYOD policy:
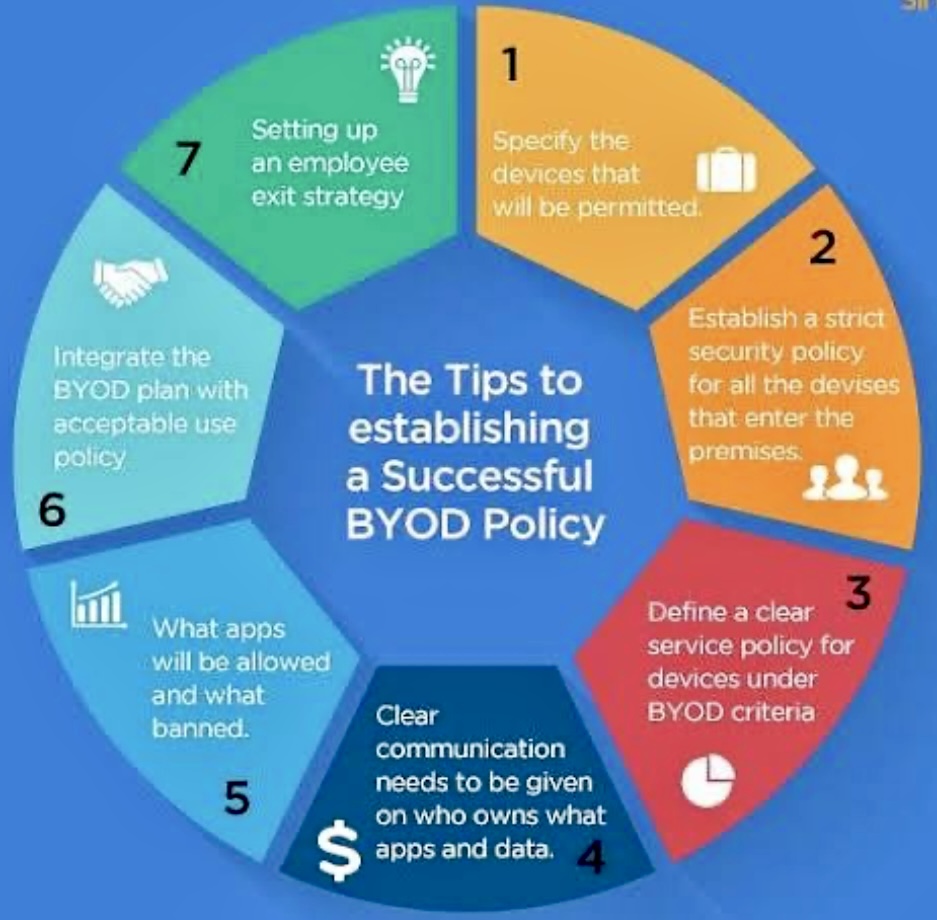
A. Define a Clear BYOD Policy:
a. Develop a comprehensive BYOD policy outlining acceptable use, security requirements, and employee responsibilities.
b. Clearly communicate the policy to all employees and ensure they understand the expectations.
c. Clearly communicate what types of devices are allowed, how and when they can access the network, what types of data they may access, and what happens if the device is lost/stolen or the employee leaves the company.
B. User Agreement: Every employee who brings their own device should sign a detailed user agreement. It should outline the security measures taken by the company, the user’s responsibilities, and the possible risks.
C. Device Requirements: To maintain a secure network, it is essential to state the minimum security requirements for personal devices. This might include necessary security software, a minimum operating system version, and regular system updates.
D. Use a mobile application management (MAM) solution: MAM solutions can be used to manage and secure corporate applications on BYOD devices. They can be used to enforce security policies, such as data encryption and access control, and to remotely wipe corporate applications from devices if necessary.
E. Regular Software Updates: Ensure that all BYODs have the latest security patches and updates.
F. Mobile Device Management (MDM) Software: Implement MDM software across all devices.
a. This software can enforce security policies, monitor devices for malicious activity, and can provide strong controls over the BYOD devices including password enforcement, locking or wiping the device remotely if lost or stolen, segregating personal and business data, etc.
b. Implement a device registration and management system to keep track of all devices used for work.
c. Enforce security configurations and settings on registered devices to ensure compliance with organizational standards.
G. Restrict Data Sharing: Block data from being shared with non-approved applications and use encryption to protect data stored on the device as well as data in transit.
H. Network Security:
a. Where possible, create separate Wi-Fi networks for BYOD devices and guests that are separated from the main corporate network.
b. Encourage the use of secure Wi-Fi connections and educate employees about the risks of connecting to unsecured networks.
c. Consider implementing a virtual private network (VPN) for secure communication when accessing sensitive information.
I. VPN and Secure Connections: All data transmitted between personal devices and the company’s network should be through a secure, encrypted connection such as a Virtual Private Network (VPN).
J. Data Encryption:
a. Enforce encryption for data both in transit and at rest on BYOD devices.
b. Encourage or require the use of encrypted messaging and communication apps for work-related conversations.
K. Regular Audits and Compliance Checks:
a. Regular system audits are a crucial measure for maintaining security. Audits can reveal inconsistencies and vulnerabilities, providing opportunities to enhance security.
b. Conduct regular audits and compliance checks on devices to ensure they adhere to security policies.
c. Address any non-compliance issues promptly.
L. Antivirus & Anti-malware Software: Make sure all BYODs are equipped with updated anti-virus and anti-malware software to protect against threats.
M. Employee Training: Regularly train employees on best security practices.
a. This training might include topics like how to identify phishing attempts, secure browsing practices, and importance of regularly updating and patching their devices.
b. Provide thorough training on security best practices for BYOD.
c. Educate employees about the risks associated with using personal devices for work and the importance of adhering to security guidelines.
N. Use Containerization:
a. Utilize containerization solutions to segregate work-related data and applications from personal information on BYOD devices.
b. Separate business and personal data on the device. Business applications and data can reside in a separately managed container, so if necessary, corporate data can be wiped without affecting personal data.
c. This helps in maintaining a clear separation between corporate and personal data.
O. Password Policies: Enforce strong password policies that require the use of complex and unique passwords. A password manager can help employees manage this responsibility.
P. Strong Authentication Mechanisms: Implement biometric authentication (like fingerprints or facial recognition), two-factor or multi-factor authentication to enhance the security level.
Q. Multi-Factor Authentication (MFA): Implement MFA where possible as it adds an additional layer of security that can help mitigate the risk of a data breach.
R. Control Access: Implement strict access control measures, making sure employees can only access the information and systems necessary for their duties.
S. Create an Incident Response Plan: In case of a security breach, have a clear response plan that outlines the steps to be taken, who needs to be notified, and how to mitigate damages.
T. Data Backup:
a. Encourage or enforce regular backups of work-related data on BYOD devices.
b. This helps prevent data loss in case of device issues or loss.
U. Legal and Privacy Compliance:
a. Ensure that your BYOD policy complies with relevant laws and regulations regarding data privacy.
b. Clearly outline the organization’s rights and responsibilities regarding personal data on employee-owned devices.
V. Exit Strategy: Define a clear exit strategy for when an employee leaves the organization, including the removal of work-related data and applications from their BYOD device.
W. Continuous Monitoring:
a. Implement continuous monitoring of BYOD devices for security threats and anomalies.
b. Utilize mobile device management (MDM) solutions for enhanced monitoring and control.
These measures, combined with an emphasis on regular review and adherence to regulatory standards for data protection, can significantly improve the security of a workplace operating under a BYOD policy.
A successful BYOD policy constitutes striking a balance between security and user friendliness. Employee training and awareness about the policies and their importance can play a vital role in the success of the BYOD policy.
Regular reviews and updates to the BYOD policy are essential to address evolving security challenges.
https://www.ncsc.gov.uk/collection/device-security-guidance/bring-your-own-device
