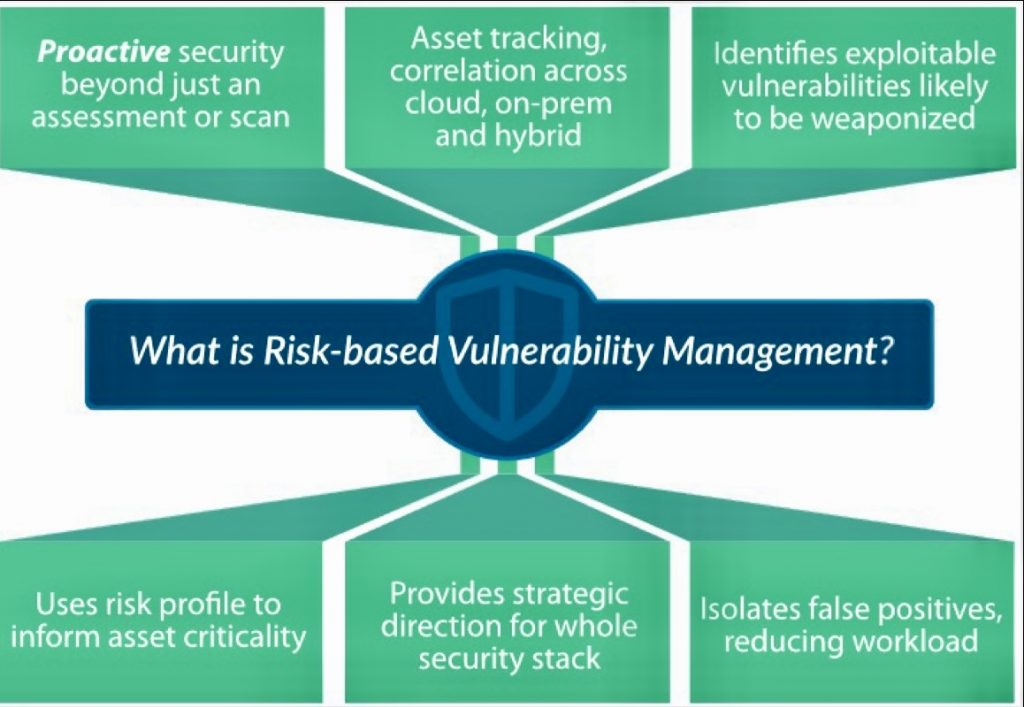
Building a proactive security strategy with risk-based vulnerability management involves a comprehensive approach to identifying, prioritizing, and remediating vulnerabilities before they can be exploited.
This approach focuses on preventing threats rather than simply reacting to them, ensuring that organizations can effectively protect their valuable data and systems.
Key Steps for Building a Proactive Security Strategy with Risk-Based Vulnerability Management:
A. Risk Assessment: Begin with a comprehensive risk assessment to identify potential threats and vulnerabilities specific to your organization. Consider both internal and external factors that may pose risks to your systems, data, and operations.
B. Policy and Compliance: Maintain and enforce policies that minimize the risk posed by vulnerabilities, such as a policy for regular patching of systems.
C. Asset Inventory: Develop and maintain an inventory of all assets within your organization. This includes hardware, software, networks, and data repositories. Knowing your assets is crucial for understanding potential vulnerabilities.
D. Establish a Comprehensive Vulnerability Management Program: Implement a structured vulnerability management program that encompasses the following steps:
o Discovery: Identify and inventory all assets within the organization’s network, including servers, endpoints, cloud applications, and IoT devices.
o Assessment: Regularly scan and assess assets to identify vulnerabilities and misconfigurations.
o Prioritization: Prioritize vulnerabilities based on their severity, potential impact, and exploitability.
o Remediation: Develop and implement remediation plans to address vulnerabilities promptly.
o Measurement: Track and measure the effectiveness of the vulnerability management program.
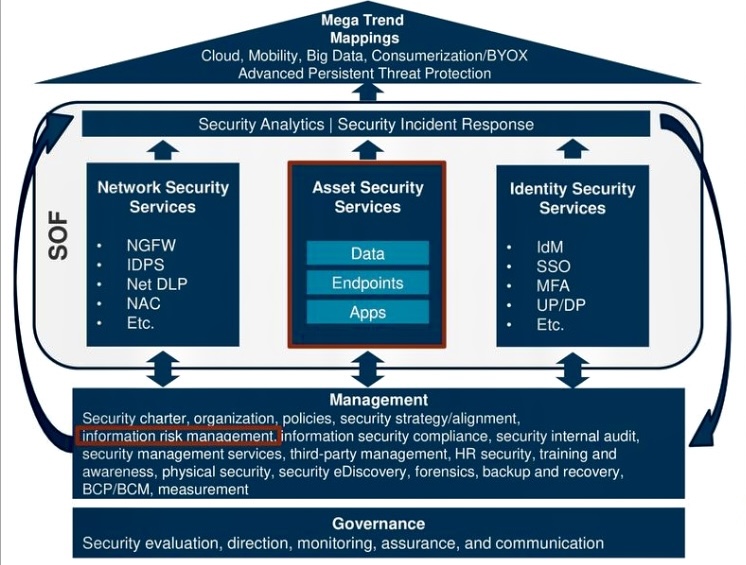
E. Integrate Risk Assessment into Vulnerability Management: Integrate risk assessment into the vulnerability management process to determine the potential impact of vulnerabilities on the organization’s business operations. This involves assessing the likelihood of exploitation and the potential damage that could result from a successful attack.
F. Categorize and Prioritize Risks: Categorize identified vulnerabilities based on the level of risk they pose to your organization. Prioritize them according to factors such as the likelihood of exploitation and the potential impact on business operations.
G. Asset Criticality: Assess the criticality of each asset in relation to your business operations. Determine the impact of a security breach on each asset to guide prioritization efforts.
H. Risk Tolerance and Appetite: Define your organization’s risk tolerance and appetite. This establishes the threshold for acceptable risk levels and guides decision-making on which vulnerabilities to address first.
I. Integration with Threat Intelligence: Integrate threat intelligence into your vulnerability management program. Stay informed about emerging threats and use this information to contextualize the risk associated with specific vulnerabilities.
J. Automate Vulnerability Management Processes: Automate vulnerability scanning, assessment, and prioritization tasks to streamline the process and improve efficiency. This allows security teams to focus on more complex tasks, such as remediation and incident response.
K. Apply Context: Use threat intelligence and business context to better understand and prioritize your vulnerabilities. This includes understanding which systems contain sensitive data, are mission critical, or house publicly accessible services.
L. Establish Clear Security Policies and Procedures: Develop and enforce clear security policies and procedures to govern the use of systems, data, and access privileges. These policies should address vulnerability management practices, password requirements, and incident reporting procedures.
M. Implement Continuous Monitoring and Logging: Implement continuous monitoring of network traffic, endpoint behavior, and user activity to detect suspicious activity and potential threats. This allows security teams to identify and respond to anomalies before they escalate into security incidents.
N. Conduct Regular Security Awareness Training: Provide regular security awareness training to employees to educate them about cybersecurity threats, social engineering tactics, and safe online practices. This can significantly reduce the risk of human error leading to security breaches.
O. Establish a Culture of Security: Cultivate a culture of security within the organization by emphasizing the importance of cybersecurity to all employees. This can be achieved through regular communication, training, and incentives for adhering to security practices.
P. Continuously Refine and Update Security Strategies: Regularly review and update security strategies to adapt to evolving threats, emerging technologies, and changing business needs. This ensures that the organization’s security posture remains effective in the face of a constantly changing threat landscape.
Q. Patch Management: Develop a robust patch management process to address known vulnerabilities promptly. Regularly update systems, applications, and firmware to mitigate security risks associated with outdated software.
R. Prioritize High-Risk Vulnerabilities: Focus on addressing high-risk vulnerabilities first. Allocate resources to remediate vulnerabilities that have the potential for severe impact, especially those that are actively exploited in the wild.
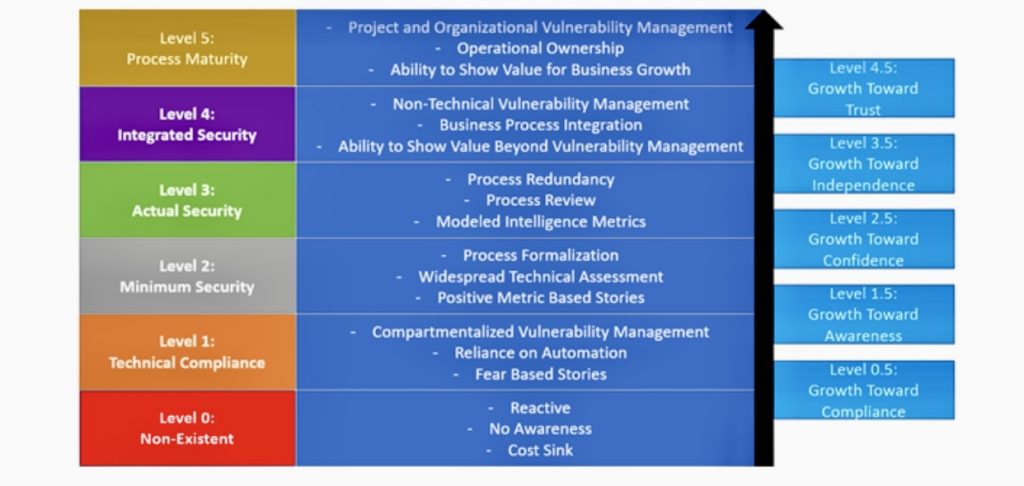
S. Remediation Planning: Develop detailed remediation plans for identified vulnerabilities. Clearly define responsibilities, timelines, and success criteria for addressing each vulnerability. Consider factors such as business impact and resource availability.
T. Remediate based on Risk: Develop remediation plans for prioritized vulnerabilities, such as patching systems, implementing compensating controls, or accepting the risk for lesser issues.
U. Validation: Once a vulnerability is patched, validate that the patch actually resolved the vulnerability.
V. Continuous Communication: Maintain open communication channels between security teams, IT operations, and business stakeholders. Transparent communication ensures that everyone is aware of the organization’s security posture and the progress of remediation efforts.
W. Metrics and Reporting: Establish key performance indicators (KPIs) and metrics to measure the effectiveness of your vulnerability management program. Regularly report on progress and improvements to demonstrate the value of proactive security measures.
X. Training and Awareness: Provide ongoing training and awareness programs for employees. Educate them about security best practices, the importance of reporting vulnerabilities, and their role in maintaining a secure environment.
Y. Continuous Improvement: Embrace a culture of continuous improvement. Regularly review and update your vulnerability management strategy based on lessons learned, changes in the threat landscape, and advancements in security technologies.
By incorporating risk-based vulnerability management into your proactive security strategy, you can systematically address security risks and enhance your organization’s resilience against evolving threats.
This approach ensures that resources are allocated efficiently to mitigate the most critical vulnerabilities, aligning security efforts with business priorities.
https://www.darkreading.com/omdia/proactive-security-what-it-means-for-enterprise-security-strategy
https://www.linkedin.com/pulse/risk-based-vulnerability-management-pragmatic-risk-riou-duchemin
https://www.getastra.com/blog/security-audit/risk-based-vulnerability-management/
https://heimdalsecurity.com/blog/what-is-vulnerability-risk-management/

Good morning, I am an aspiring GRC and AWS cybersecurity professional inquiring about which certifications and software programs I should have, and what are the job titles in the marketplace should I look for?