ISO 27001 risk assessment methodology
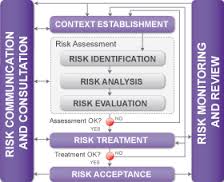
Risk assessment is the most complex step in the ISO 27001 implementation; however, many companies make this step even more difficult by defining the wrong methodology (or by not defining the methodology at all).
What does ISO 27001 really require?
ISO 27001 requires you to document the whole process of risk assessment (clause 6.1.2), and this is usually done in the document called Risk assessment methodology. Unfortunately, this is where too many companies make the first big mistake: they start implementing the risk assessment without the methodology – in other words, without any clear rules on how to do it. See also this article: ISO 27001 risk assessment & treatment – 6 basic steps.
There are many myths regarding what the risk assessment should look like, but in reality ISO 27001:2013 requirements are not very difficult – here is what clause 6.1.2 requires:
1) Define how to identify the risks that could cause the loss of confidentiality, integrity and/or availability of your information
2) Define how to identify the risk owners
3) Define criteria for assessing consequences and assessing the likelihood of the risk
4) Define how the risk will be calculated
5) Define criteria for accepting risks
And yes – you need to ensure that the risk assessment results are consistent – that is, you have to define such methodology that will produce comparable results in all the departments of your company.
Which options are available?
Of course, there are many options available for the above 5 elements – here is what you can choose from:
Risk identification
In the 2005 revision of ISO 27001 the methodology for identification was prescribed: you needed to identify assets, threats and vulnerabilities (see also What has changed in risk assessment in ISO 27001:2013). The current 2013 revision of ISO 27001 does not require such identification, which means you can identify risks based on your processes, based on your departments, using only threats and not vulnerabilities, or any other methodology you like; however, my personal preference is still the good old assets-threats-vulnerabilities method. (See also this list of threats and vulnerabilities.)
Risk owners
Basically, you should choose a person who is both interested in resolving a risk, and positioned highly enough in the organization to do something about it.
Assessing consequences and likelihood
You should assess separately the consequences and likelihood for each of your risks; you are completely free to use whichever scales you like – e.g., Low-Medium-High, or 1 to 5, or 1 to 10 – whatever suits you best. Of course, if you want to make it simple, go for Low-Medium-High.
Method of risk calculation
This is usually done through addition (e.g., 2 + 5 = 7) or through multiplication (e.g., 2 x 5 = 10). If you use scales Low-Medium-High, then this is the same as using scale 1-2-3, so you have numbers again for calculation.
Criteria for accepting risks
If your method of risk calculation produces values from 2 to 10, then you can decide that an acceptable level of risk is, e.g., 7 – this would mean that only the risks valued at 8, 9 and 10 need treatment. Alternatively, you can examine each individual risk and decide which should be treated or not based on your insight and experience, using no pre-defined values.
Methodology first, everything else afterwards
So the point is this: you shouldn’t start assessing the risks using some sheet you downloaded somewhere from the Internet – this sheet might be using a methodology that is completely inappropriate for your company. You shouldn’t start using the methodology prescribed by the risk assessment tool you purchased; instead, you should choose the risk assessment tool that fits your methodology. (Or you may decide you don’t need a tool at all, and that you can do it using simple Excel sheets.)
In any case, you should not start assessing the risks before you adapt the methodology to your specific circumstances and to your needs.

This is the first time I’ve read about the ISO 27001 standard and executing it through the tools provided to you is important to match your specific needs to what the tool could offer. If I were a business owner, I would understand how consulting these services is crucial to support the business. It would be great to have a company that you could consult in these sorts of standards.