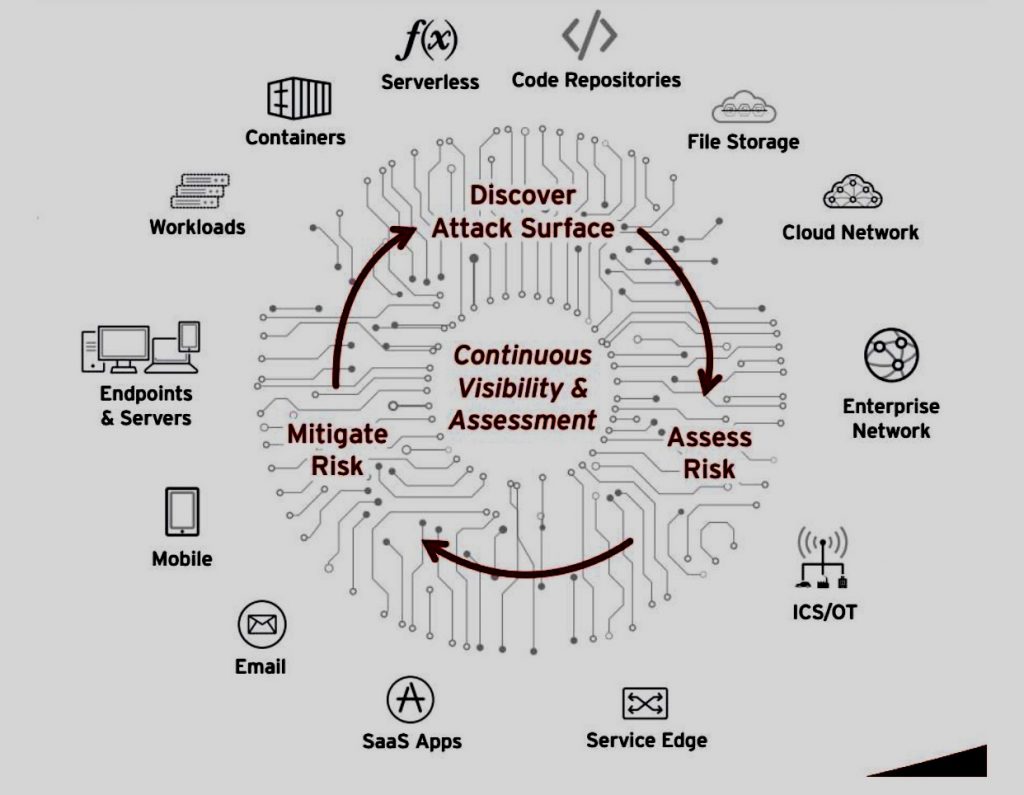
In the ever-evolving landscape of technology, proactive IT risk management has become increasingly crucial for organizations to safeguard their data, systems, and reputation. As emerging technologies continue to reshape the digital world, organizations must adapt their risk management strategies to address the unique challenges and opportunities presented by these advancements.
i. Understanding the Landscape of Emerging Technologies
Emerging technologies, such as artificial intelligence (AI), cloud computing, the Internet of Things (IoT), and blockchain, offer immense potential for improving efficiency, innovation, and competitiveness. However, these technologies also introduce new risks and vulnerabilities that organizations must be prepared to mitigate.
Key Challenges of Emerging Technologies for IT Risk Management
A. Rapidly Changing Environment: The fast-paced development and adoption of emerging technologies create a dynamic risk landscape, requiring organizations to continuously adapt their risk management strategies.
B. Interconnectedness and Complexity: Emerging technologies often involve complex integrations and interdependencies, making it difficult to identify and assess potential risks across the entire technology ecosystem.
C. Data Privacy and Security: The increasing volume and sensitivity of data generated by emerging technologies pose significant privacy and security challenges, requiring robust data protection measures.
D. Third-Party Dependencies: Organizations often rely on third-party vendors and service providers for emerging technologies, introducing additional risks related to supply chain security and data sharing practices.
As businesses incorporate new technologies such as artificial intelligence, blockchain, and the Internet of Things, they must also assess the potential risks associated with these innovations.
To effectively manage IT risks, organizations need to adopt a proactive approach rather than reacting to incidents after they occur.
ii. Strategies for Proactive IT Risk Management in an Era of Emerging Technologies
A. Identify and assess emerging risks: Stay up-to-date with the latest technological advancements and assess their potential impact on your organization. Identify the risks associated with these technologies, such as vulnerabilities, data breaches, regulatory compliance issues, and operational disruptions.
B. Establish a risk management framework: Develop a comprehensive risk management framework that aligns with your organization’s goals and objectives. This framework should define roles, responsibilities, processes, and methodologies for identifying, assessing, and mitigating IT risks.
C. Data Privacy and Compliance: Stay abreast of evolving data privacy regulations and compliance standards related to emerging technologies. Ensure that the adoption of these technologies aligns with legal requirements.
D. Prioritize Data Security: Implement robust data security measures, including encryption, data loss prevention (DLP) technologies, and secure data disposal practices, to protect sensitive information.
E. Monitor and Manage Third-Party Risks: Carefully evaluate and manage risks associated with third-party vendors and service providers, establishing clear contractual obligations and ongoing monitoring procedures.
F. Adaptive Governance Structures: Establish adaptive governance structures that can accommodate the dynamic nature of emerging technologies. This includes agile frameworks that allow for quick adjustments in response to new risks and opportunities.
G. Stay Informed About Emerging Technologies: Develop a deep understanding of emerging technologies relevant to your industry. This includes artificial intelligence, blockchain, IoT, and other disruptive innovations. Stay informed about their applications and potential risks.
H. Cross-Functional Collaboration: Foster collaboration between IT and other business units. Engage in cross-functional discussions to understand how emerging technologies may impact various aspects of the organization, including operations, finance, and compliance.
I. Implement robust cybersecurity measures: As emerging technologies often rely on data and interconnected networks, it’s crucial to prioritize cybersecurity. Implement strong security measures, including encryption, firewalls, access controls, and continuous monitoring to detect and prevent potential threats.
J. Conduct regular risk assessments: Regularly assess your IT infrastructure, systems, and processes to identify existing and emerging risks. This includes vulnerability scanning, penetration testing, and third-party risk assessments. Stay alert to new threat vectors and continually enhance security controls.
K. Threat Intelligence Monitoring: Implement robust threat intelligence monitoring to identify potential cybersecurity threats associated with emerging technologies. Stay vigilant about new vulnerabilities and attack vectors.
L. Implement Robust Access Controls: Enforce strict access controls and role-based permissions to limit access to sensitive data and systems, minimizing potential unauthorized access or data breaches.
M. Security by Design: Incorporate security measures into the design phase of emerging technology projects. Implement a “security by design” approach to minimize vulnerabilities and enhance overall system resilience.
N. Employee Training and Awareness: Provide ongoing training to employees on the responsible use and potential risks of emerging technologies. Foster a culture of awareness and accountability to mitigate the risk of human error.
O. Risk Quantification: Develop methods to quantify and prioritize IT risks associated with emerging technologies. This allows for a more strategic allocation of resources toward addressing the most critical risks.
P. Regular Testing and Simulation: Conduct regular testing and simulation exercises to evaluate the effectiveness of security measures in place. Simulate potential cybersecurity incidents related to emerging technologies to enhance preparedness.
Q. Incident Response Planning: Develop and regularly update incident response plans specific to the risks associated with emerging technologies. Ensure that the response team is well-prepared to address incidents promptly and effectively.
R. Ethical Considerations: Consider ethical implications associated with emerging technologies, especially those involving AI, machine learning, and automation. Establish ethical guidelines and frameworks to guide the responsible use of these technologies.
S. Scenario Planning: Conduct scenario planning exercises to anticipate potential risks associated with the adoption of emerging technologies. Identify various scenarios and develop mitigation strategies for each.
T. Foster a risk-aware culture: Promote a culture of risk awareness and accountability across the organization. Educate employees about IT risks, their roles in risk management, and best practices for mitigating threats. Encourage reporting of potential risks and create channels for open communication.
U. Engage in collaboration and knowledge sharing: Participate in industry groups, conferences, and forums to stay abreast of emerging IT risks and share knowledge with peers. Collaborate with experts in the field to understand best practices and innovative approaches to IT risk management.
V. Monitor regulatory changes: Stay informed about evolving regulations and compliance requirements related to emerging technologies. Ensure that your risk management practices align with industry standards and legal obligations.
W. Embrace Continuous Improvement: Continuously review and improve risk management practices, adapting to the evolving threat landscape and incorporating lessons learned from incidents or near misses.
By adopting a proactive IT risk management approach, organizations can harness the benefits of emerging technologies while effectively mitigating potential risks.
This approach helps safeguard critical assets, maintain customer trust, and enable the successful integration of emerging technologies into business practices.
It requires a combination of strategic planning, collaboration, and a commitment to staying ahead of the curve in the ever-evolving tech landscape.
https://www.trendmicro.com/en_hk/ciso/22/d/proactive-cyber-risk-management-strategies.html
