
Social Engineering: The Human Factor in Cybercrime
Social engineering is a psychological manipulation tactic used by cybercriminals to trick individuals or organizations into revealing sensitive information or taking actions that compromise security. It exploits human vulnerabilities like trust, fear, curiosity, and greed to achieve their goals.
Due to its effectiveness, social engineering is present in a significant portion of cyberattacks, estimated to be involved in up to 90% of cases.
i. Understanding Social Engineering
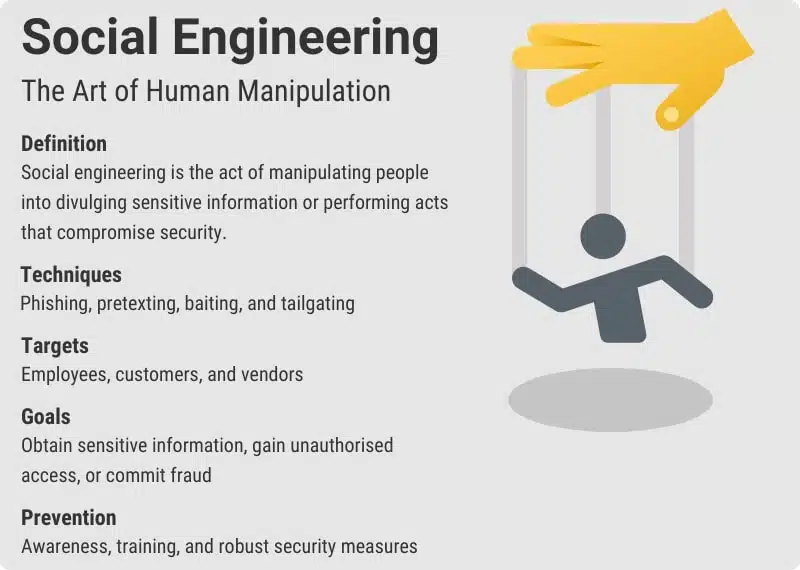
Social engineering is a form of psychological manipulation that exploits human behavior to gain access to confidential information. Unlike traditional hacking methods that focus on exploiting technical vulnerabilities, social engineering targets the human element – often the weakest link in the security chain. Cybercriminals use various tactics to deceive individuals into divulging sensitive data, such as passwords, financial details, or access codes.
ii. How Social Engineering Works
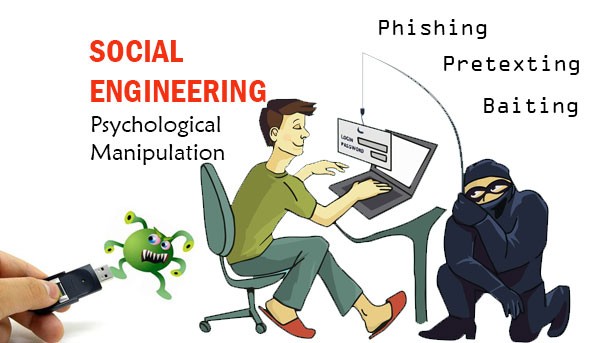
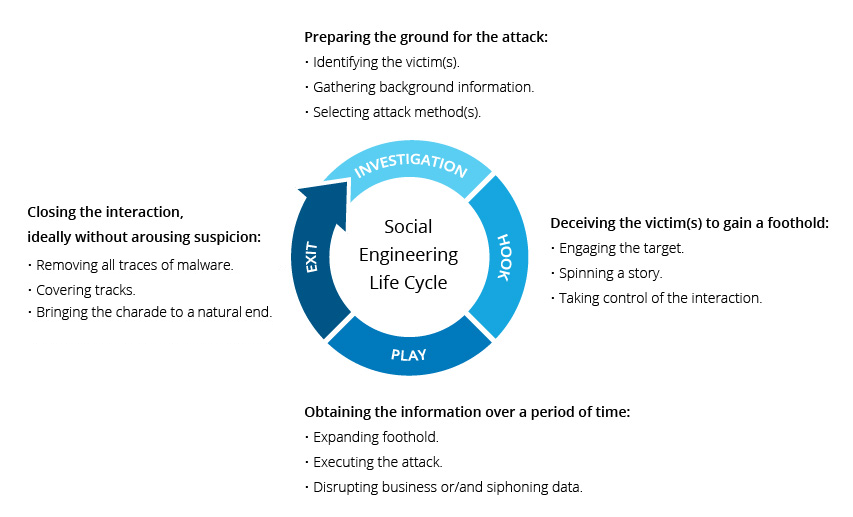
Social engineering attacks follow a three-step process:
A. Reconnaissance: Attackers gather information about their target, such as their name, job title, interests, and vulnerabilities. This information can be obtained through various means, including social media, public records, and phishing emails.
B. Building trust and rapport: Attackers pose as someone trustworthy, such as a colleague, IT support personnel, or a legitimate company. They may create a sense of urgency, fear, or excitement to manipulate the victim’s emotions.
C. Deception and manipulation: Once trust is established, attackers trick the victim into performing actions that compromise security, such as:
o Clicking on malicious links or attachments
o Sharing personal information like passwords or credit card details
o Downloading malware
o Granting unauthorized access to systems or data
iii. Here are some common forms of social engineering and the risks they pose in cyber-attacks:

A. Phishing: The most prevalent form of social engineering, phishing involves sending deceptive emails or messages that appear to be from a legitimate source. These messages often contain malicious links or attachments designed to trick recipients into revealing sensitive information like passwords, credit card numbers, or login credentials. Falling for phishing attacks can lead to data breaches, financial loss, and unauthorized access to personal or corporate information.
B. Pretexting: In pretexting attacks, the attacker creates a fabricated scenario to deceive targets into giving up sensitive information or access to confidential data. This could involve pretending to be a trusted individual or authority figure to extract information that can be used in further attacks.
C. Baiting: Baiting involves enticing targets with the promise of something desirable, such as a free download or prize, in exchange for personal information or login credentials. Once the victim takes the bait, their system could be compromised by malware or their information stolen.
D. Tailgating: Also known as piggybacking, this technique involves physically following someone into a restricted area by closely walking behind them. This can be used to gain unauthorized access to secure locations or sensitive information.
E. Quid Pro Quo: This technique involves offering a service or benefit in exchange for information, exploiting the natural inclination to reciprocate.
iv. The Human Factor: A Vulnerable Link

While cybersecurity measures continue to advance, humans remain susceptible to manipulation. Social engineering exploits inherent human traits, such as trust, curiosity, and the desire to help, making it a persistent threat.
v. The risks associated with social engineering attacks include:

A. Data breaches: Attackers can gain access to sensitive data like customer information, trade secrets, or financial records through social engineering tactics.
B. Financial loss: Social engineering attacks can lead to fraudulent transactions, identity theft, or ransom demands, resulting in financial losses for individuals or organizations.
C. Reputation damage: A successful social engineering attack can tarnish an organization’s reputation if customer data is compromised or confidential information is leaked.
D. Legal consequences: Failure to protect sensitive data from social engineering attacks can lead to legal repercussions, such as fines under data protection regulations like GDPR or HIPAA.
E. Compromised Security Systems: Social engineering attacks can serve as an entry point for more extensive cyber-attacks, compromising entire networks or systems.
vi. Mitigating the Risks
A. Education and Awareness: Training individuals to recognize and resist social engineering tactics is crucial. Regular awareness programs can empower users to identify potential threats.
B. Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of protection, even if login credentials are compromised.
C. Vigilance in Communication: Encouraging skepticism towards unsolicited communication and verifying the legitimacy of requests can thwart many social engineering attempts.
D. Regular Security Audits: Conducting frequent security audits helps identify vulnerabilities and ensures that systems are fortified against potential threats.
E. Report suspicious activity: If you suspect a social engineering attempt, report it to the appropriate authorities and your IT department.
vii. Conclusion
Social engineering poses a substantial risk in the realm of cyber-attacks, leveraging human psychology as a gateway to sensitive information. Recognizing the tactics employed and implementing proactive measures is crucial for individuals and organizations alike. As technology evolves, so too must our defenses against the subtle art of social engineering to safeguard the digital landscapes we navigate.
It is also essential to foster a culture of security awareness to empower individuals to identify and report suspicious activities promptly.
viii. Further information
9 Examples of Social Engineering Attacks | Terranova Security
PECBhttps://pecb.com › article › social-e…Social Engineering and Risk from Cyber-Attacks
SecureWorldwww.secureworld.ioThe Impact of AI on Social Engineering Cyber Attacks
LinkedIn · Sennovate6 reactionsSocial Engineering: The Psychology Behind the Attack
LinkedInhttps://www.linkedin.com › pulseAI And Its Influence on Social Engineering In …
Forbeswww.forbes.comWhat Is Social Engineering? Types Of Attacks To Beware Of
Invictihttps://www.invicti.com › blog › so…The Dangers of Social Engineering Attacks | Invicti
