
Application classification can refer to a number of concepts, many of which revolve around organizing software, data, and functions based on their purpose, features, or functionality.
i. Purposes of Application Classification
A. Resource Allocation: Application classification helps organizations identify applications with similar resource requirements, enabling efficient resource allocation and planning.
B. Risk Management: Classifying applications based on their sensitivity and potential impact helps prioritize risk mitigation efforts and safeguard critical assets.
C. Cost Optimization: Identifying redundant or underutilized applications through classification can lead to cost savings and optimization of software licensing and maintenance expenses.
D. Compliance: Classifying applications based on data types, security requirements, and regulatory compliance can streamline compliance audits and ensure adherence to industry standards.
E. Application Rationalization: Application classification facilitates the identification of overlapping or outdated applications, enabling rationalization decisions to optimize the application portfolio.
ii. key aspects of application classification
A. Business Function: Classifying applications based on the business process they support, such as customer relationship management (CRM), supply chain management (SCM), or financial management.
B. Criticality to Business: Critical, Essential, Non-Essential: Classify applications based on their criticality to business operations. Critical applications are vital for core business functions, while non-essential applications may have less impact if disrupted.
C. Sensitivity of Data: Sensitive Data Handling: Classify applications based on the sensitivity of data they handle. Applications dealing with personally identifiable information (PII), financial data, or intellectual property may require heightened security measures.
D. User Access and Permissions: Privileged Access Applications: Identify applications that require elevated access levels or involve privileged operations. This classification helps manage user permissions and restrict access to sensitive functionalities.
E. Regulatory Compliance: Compliance-Critical Applications: Classify applications based on their relevance to regulatory compliance requirements. Certain applications may handle data subject to specific regulations, such as healthcare (HIPAA) or finance (PCI DSS).
F. Technology: Classifying applications based on their underlying technology stack, such as Java, .NET, or web applications.
G. Cloud-Native vs. Legacy: Cloud-Ready or Legacy: Differentiate between applications that are designed for cloud environments and those that may require modification or migration. This classification informs cloud adoption and modernization strategies.
H. Deployment Model: Classifying applications based on their deployment model, such as on-premises, cloud-based, or hybrid.
I. Lifecycle Stage: Development, Testing, Production: Classify applications based on their lifecycle stages. This helps manage development and testing environments separately from production and ensures appropriate controls at each stage.
J. Dependency Mapping: Interconnected Applications: Identify applications with dependencies on others. Understanding interconnections helps manage updates, maintenance, and potential impact on related systems.
K. Vendor Criticality: Vendor Dependency: Classify applications based on their reliance on specific vendors. Vendor criticality assessments inform risk management strategies, especially when dealing with third-party applications.
L. Access Channels: Web, Mobile, Desktop: Classify applications based on the channels through which users access them. This distinction helps tailor security measures for different access points.
M. Authentication Requirements: Authentication Intensity: Categorize applications based on the level of authentication required. High-security applications may demand multi-factor authentication, while others may rely on standard credentials.
N. Data Storage Locations: On-Premises, Cloud, Hybrid: Classify applications based on where they store data. Understanding data storage locations informs data residency considerations and compliance with data protection regulations.
O. Integration Complexity: Simple, Moderate, Complex: Assess the integration complexity of applications. This classification aids in prioritizing integration efforts and understanding potential challenges in interconnected systems.
P. User Impact upon Outage: High, Medium, Low Impact: Classify applications based on the potential impact on users in case of downtime. Critical applications with high impact may require more robust redundancy and disaster recovery measures.
Q. Security Posture: Secure, Needs Improvement: Evaluate the security posture of applications. This classification guides efforts to enhance security controls and address vulnerabilities.
iii. Benefits of Application Classification
A. Improved Application Portfolio Management: Classification provides a clear understanding of the application landscape, enabling better decision-making for rationalization, modernization, and resource allocation.
B. Enhanced Risk Management: Classification helps identify and prioritize security risks associated with different application types, enabling effective mitigation strategies.
C. Optimized IT Operations: Classification facilitates efficient resource allocation, cost optimization, and streamlined incident management.
D. Streamlined Compliance: Classification simplifies compliance audits and ensures adherence to industry standards and regulatory requirements.
E. Informed Decision-Making: Classification provides valuable insights for strategic planning, budgeting, and technology roadmap development.
The way an application is classified can affect various things such as its development process, how it is marketed, its user interface design, and how it integrates with other software.
Application classification is an essential practice for organizations that manage diverse application portfolios. It provides a structured approach to understanding, managing, and optimizing the application landscape, leading to improved IT governance, risk management, and cost efficiency.
https://www.geeksforgeeks.org/software-engineering-classification-software/
https://www.leanix.net/en/wiki/ea/application-criticality-assessment-and-matrix
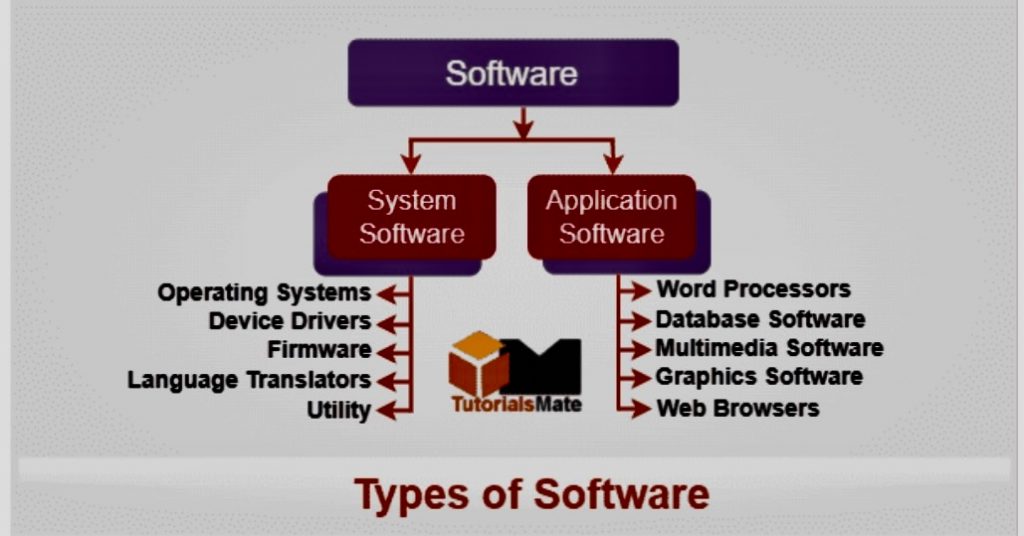
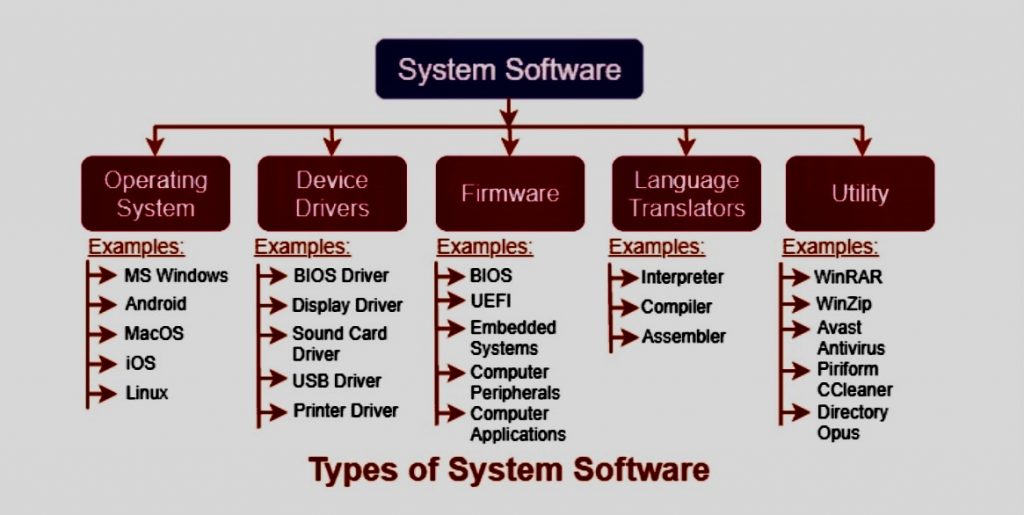
https://www.tutorialsmate.com/2021/09/types-of-software.html?m=1
