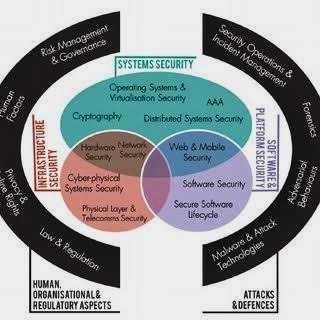
The Human Factors Knowledge Area (KA) within the Cyber Security Body of Knowledge (CyBOK) focuses on understanding the role of human behavior in cybersecurity.
It recognizes that humans are not simply components in a system, but rather active participants whose choices and actions can significantly impact sectors outcomes.
i. Key aspects of the Human Factors Knowledge Area (KA)
A. Individual factors: This includes understanding human capabilities and limitations, mental models, decision-making processes, and biases.
B. Social and cultural factors: This explores how social norms, group dynamics, and cultural differences influence cybersecurity behaviors.
C. Technological factors: This examines how technology design, usability, and human-computer interaction affect cybersecurity practices.
D. Organizational factors: This analyzes how organizational structure, culture, policies, and procedures impact cybersecurity awareness and behavior.
ii. Key concepts covered in the Human Factors Knowledge Area (KA)
A. Security awareness and training: Increasing user knowledge and skills to make informed decisions regarding cybersecurity.
B. Usable security design: Creating systems and interfaces that are easy to use while maintaining security principles.
C. Motivational factors: Understanding what drives people to behave securely or insecurely.
D. Risk perception: Analyzing how individuals perceive and respond to cybersecurity risks.
E. Decision-making processes: Examining how individuals make security-related decisions and how biases can influence them.
F. Social engineering: Understanding how attackers exploit human factors to trick individuals into compromising security.
iii. Benefits of understanding Human Factors in Cybersecurity

A. Improved security posture: By addressing human vulnerabilities, organizations can create a more robust and resilient security environment.
B. Reduced human error: Increased awareness and understanding of human factors can lead to fewer unintentional security mistakes.
C. Effective security awareness programs: Tailoring programs to address specific human factors can improve their effectiveness and impact.
D. Enhanced user experience: Security measures that consider human factors can be more user-friendly and less disruptive to daily operations.
E. Improved decision-making: By recognizing and mitigating human biases, individuals can make more informed and secure decisions.
iv. Key aspects covered in the Human Factors Knowledge Area
A. User-Centered Design:
o Focus: Designing cybersecurity systems and interfaces with a primary emphasis on user needs and capabilities.
o Objective: Enhances user acceptance and promotes effective interaction with security measures.
B. Security Education and Awareness:
o Focus: Providing education and raising awareness among users about cybersecurity practices.
o Objective: Empowers users to make informed decisions and reduces the risk of human-related security incidents.
C. Usability and Human-Computer Interaction (HCI):
o Focus: Ensuring that cybersecurity systems are user-friendly and optimize human-computer interaction.
o Objective: Improves the effectiveness of security measures by reducing user errors and enhancing user experience.
D. Social Engineering:
o Focus: Understanding and mitigating the impact of manipulative techniques used by attackers to exploit human vulnerabilities.
o Objective: Addresses the human element as a potential weak link in cybersecurity defenses.
E. Psychology of Security:
o Focus: Examining psychological aspects that influence individuals’ security-related behaviors.
o Objective: Provides insights into why individuals may deviate from secure practices and informs strategies to influence positive behavior.
F. Human Factors in Incident Response:
o Focus: Incorporating human factors considerations into incident response planning and execution.
o Objective: Ensures that incident response strategies align with human capabilities and limitations.
G. Human Factors in Access Control:
o Focus: Designing access control systems that consider human factors, such as usability and authentication.
o Objective: Balances security requirements with the need for convenient and efficient access.
H. Human Factors in Authentication:
o Focus: Examining the usability and effectiveness of authentication methods from a human-centric perspective.
o Objective: Encourages the adoption of secure authentication practices by considering user experience.
I. Cultural and Organizational Influences:
o Focus: Understanding how cultural and organizational factors impact cybersecurity practices.
o Objective: Tailors cybersecurity approaches to align with specific organizational contexts and cultural norms.
J. Human Factors in Security Policy:
o Focus: Integrating human factors considerations into the development and communication of security policies.
o Objective: Enhances policy adherence by aligning security requirements with human behavior and cognition.
v. Resources for further exploration
A. CyBOK: Human Factors Knowledge Area – [https://www.cybok.org/media/downloads/Human_Factors_issue_1.0.pdf](https://www.cybok.org/media/downloads/Human_Factors_issue_1.0.pdf)
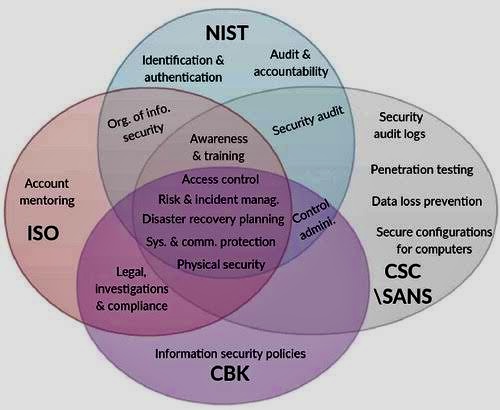
B. National Institute of Standards and Technology (NIST) Cybersecurity Framework – [https://www.nist.gov/cyberframework](https://www.nist.gov/cyberframework)
C. SANS Security Awareness – [https://www.sans.org/security-awareness-training/](https://www.sans.org/security-awareness-training/)
The Human Factors Knowledge Area in CyBOK recognizes the critical role of human factors in the success of cybersecurity initiatives and aims to guide professionals in incorporating these considerations into various aspects of cybersecurity planning, design, and implementation.
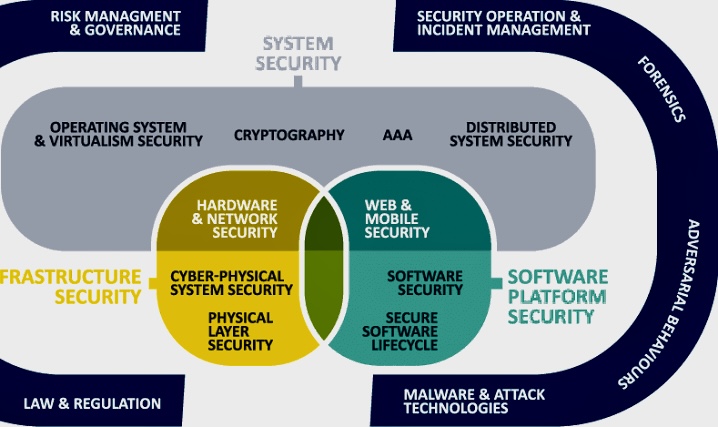
https://www.researchgate.net/figure/The-19-Knowledge-Areas-in-the-CyBOK_fig1_352912571
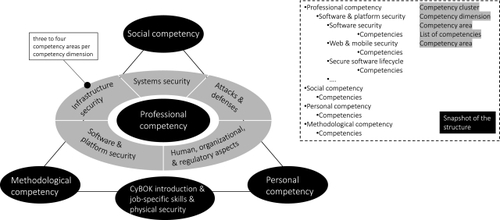
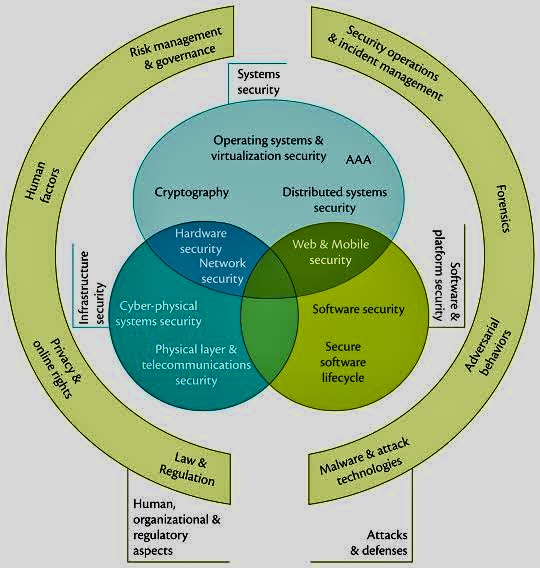
https://cybok.org/media/downloads/CyBOK_MappingBooklet_v_2.1_2023_final.pdf
