A vendor risk assessment is a critical process in evaluating and managing the potential risks associated with third-party vendors or suppliers.
It helps organizations ensure that their partners adhere to security and compliance standards, safeguarding the organization from various risks.
It consists of assessing a vendor’s financial, operational, compliance, and reputational health.
i. Why is vendor risk assessment important?
Vendors play a critical role in the operations of many organizations. They provide a wide range of products and services, from IT infrastructure and software to marketing and consulting. As a result, organizations rely on their vendors to maintain confidentiality, integrity, and availability of their data.
ii. However, vendors can also pose significant risks to organizations. These risks can include:
A. Data breaches: Vendors may have access to sensitive data, such as customer information or financial data. If a vendor’s systems are compromised, this data could be stolen or lost.
B. Financial losses: Vendors may make errors or fail to fulfill their contractual obligations. This could lead to financial losses for the organization.
C. Operational disruptions: Vendors may experience outages or other disruptions that could impact the organization’s operations.
iii. A VRA can help organizations to identify, assess, and manage these risks by:
A. Identifying potential risks: The first step in a VRA is to identify the potential risks associated with each vendor. This can be done by reviewing the vendor’s security policies and procedures, conducting interviews with vendor staff, and assessing the vendor’s past performance.
B. Assessing the severity of risks: Once the potential risks have been identified, the next step is to assess the severity of each risk. This will help the organization to prioritize its risk mitigation efforts.
C. Developing mitigation strategies: For each identified risk, the organization should develop a mitigation strategy. This may include implementing additional security controls, requiring the vendor to purchase insurance, or conducting regular audits of the vendor’s systems.
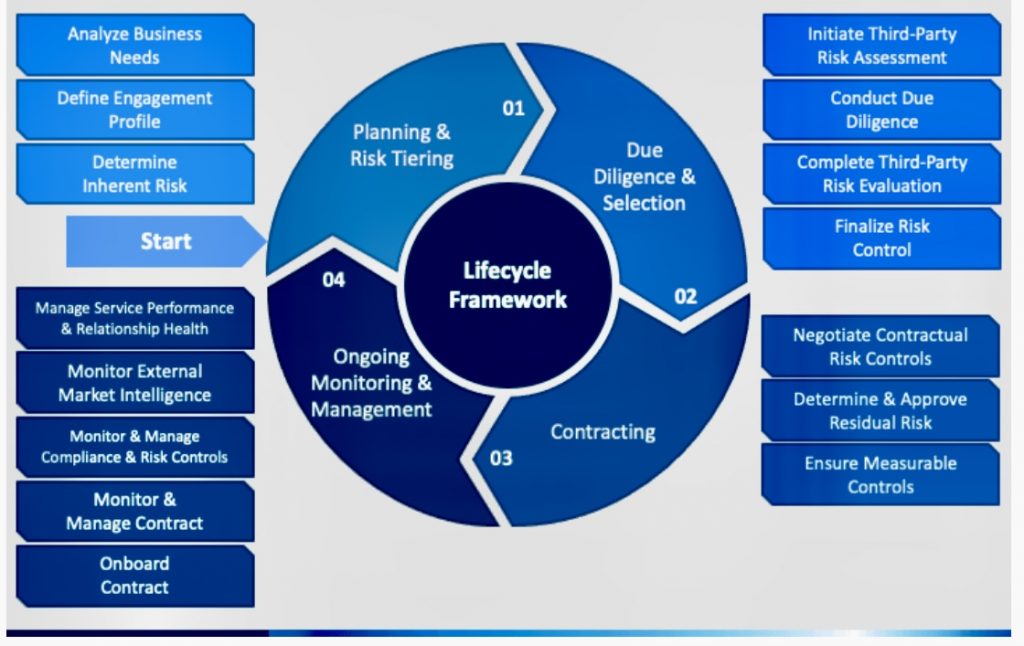
iv. Here are key steps and considerations for conducting a vendor risk assessment:
A. Develop a VRA policy: The first step is to develop a VRA policy that outlines the organization’s approach to vendor risk management. This policy should include the scope of the VRA program, the frequency of VRAs, and the roles and responsibilities of stakeholders.
B. Define Assessment Criteria: Clearly define the criteria against which vendors will be assessed. This may include security practices, compliance with regulations, financial stability, data protection measures, and business continuity plans.
C. Identify Critical Vendors: Identify vendors that have significant access to your organization’s sensitive data or play a crucial role in your business operations. Focus on assessing vendors with higher inherent risks.
D. Risk Categorization: Categorize vendors based on the level of risk they pose to your organization. High-risk vendors may require more extensive assessments and ongoing monitoring.
E. Questionnaire and Documentation: Develop a vendor risk assessment questionnaire that covers essential aspects such as security controls, data protection, incident response, and compliance. Request relevant documentation to support the vendor’s responses.
F. Regulatory Compliance: Ensure that vendors comply with relevant regulations and industry standards. This may include data protection laws, industry-specific regulations, and cybersecurity frameworks.
G. Security Controls and Practices: Assess the vendor’s security controls and practices, including access controls, encryption methods, network security, and vulnerability management. Verify that they have implemented adequate measures to protect data.
H. Data Protection and Privacy: Evaluate how vendors handle and protect sensitive data. Assess their data protection policies, encryption practices, data breach response plans, and adherence to privacy regulations.
I. Financial Stability: Assess the financial stability of the vendor to ensure they can meet their contractual obligations and continue providing services without disruptions.
J. Business Continuity and Disaster Recovery: Examine the vendor’s business continuity and disaster recovery plans. Ensure they have measures in place to maintain critical operations in the event of disruptions.
K. Incident Response Capability: Assess the vendor’s incident response capability. Verify their ability to detect, respond to, and recover from security incidents, and ensure they have a documented incident response plan.
L. Contractual Obligations: Review contractual agreements with vendors to ensure they include appropriate security and compliance clauses. Clearly outline expectations, responsibilities, and consequences for non-compliance.
M. Ongoing Monitoring: Establish processes for ongoing monitoring of vendor activities. Regularly review their security posture and performance to ensure continued compliance with your organization’s standards.
N. Third-Party Audits and Certifications: Consider whether the vendor has undergone third-party audits or holds relevant certifications. Certifications like ISO 27001 or SOC 2 indicate a commitment to security best practices.
O. Exit Strategy: Develop an exit strategy in case the relationship with the vendor needs to be terminated. Ensure that data is securely transferred or deleted, and that the transition process is smooth.
P. Communication and Collaboration: Maintain open communication with vendors throughout the assessment process. Collaboration ensures a shared understanding of expectations and facilitates the resolution of any identified issues.
Q. Documentation and Reporting: Document the results of the vendor risk assessment and create a comprehensive report. Share the findings with relevant stakeholders and use the information to inform decision-making.
R. Continuous Improvement: Implement a process for continuous improvement based on lessons learned from vendor assessments. Regularly update assessment criteria and adjust procedures to adapt to evolving risks.
By systematically conducting vendor risk assessments, organizations can proactively manage and mitigate the potential risks associated with their vendor ecosystem.
This process contributes to a more secure and resilient supply chain, protecting sensitive data and maintaining business continuity.
https://mitratech.com/en_gb/resource-hub/blog/what-is-vendor-risk-assessment/
https://blog.riskrecon.com/vendor-risk-assessment
