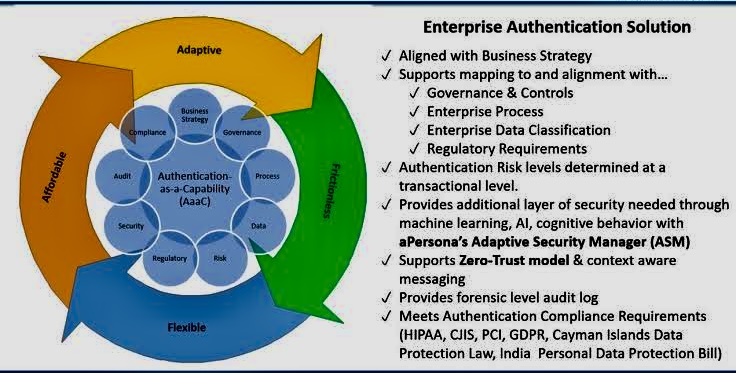
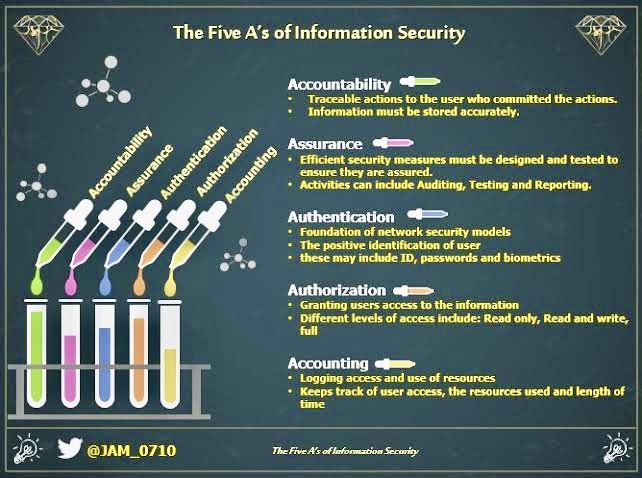
Authentication Tools and Trends: Securing the Digital Frontier
In the digital age, where data breaches and unauthorized access are increasing threats, robust authentication mechanisms are more crucial than ever. Authentication—the process of verifying the identity of a user, device, or entity—serves as the first line of defense against cyber threats.
The evolution of authentication technologies has been rapid, driven by the need for more secure and user-friendly solutions. This article explores the latest tools and trends in authentication, highlighting how they are shaping the future of digital security.
i. Authentication Tools: From Basic to Advanced

A. Password-Based Authentication: Traditionally, passwords have been the cornerstone of authentication. However, their vulnerability to brute-force attacks, phishing, and human error has necessitated the development of more secure alternatives.
B. Two-Factor Authentication (2FA): 2FA adds an extra layer of security by requiring two forms of identification: something you know (like a password) and something you have (like a smartphone). Common 2FA methods include SMS codes and authentication apps. Despite its increased security, 2FA can still be vulnerable to sophisticated phishing attacks.
C. Multi-Factor Authentication (MFA): Building on 2FA, MFA requires two or more verification factors, significantly increasing security. MFA implementations may include biometric verification, hardware tokens, and location information, making unauthorized access exponentially more challenging.

D. Biometric Authentication: Utilizing unique biological characteristics such as fingerprints, facial recognition, and iris scans, biometric authentication offers a high level of security and convenience. Advances in biometric technology have led to its widespread adoption in smartphones, laptops, and secure access systems.
E. Behavioral Biometrics: An emerging trend, behavioral biometrics analyzes patterns in user behavior such as typing rhythm, mouse movements, and interaction patterns. Because these patterns are unique and difficult to replicate, behavioral biometrics offer a non-intrusive yet highly secure form of authentication.
F. Single Sign-On (SSO) and Federated Identity: SSO allows users to access multiple services or applications with one set of credentials, improving user experience while maintaining security. Federated identity systems extend this concept across different organizations, enabling secure and convenient access across a wide range of services.
ii. Traditional Methods: Still Relevant, But Evolving
o Passwords: The classic password remains a staple, but its limitations are well-known. Multi-factor authentication (MFA) is increasingly becoming the norm, adding an extra layer of security by requiring a second verification factor, like a code from your phone or a fingerprint scan.
o Biometrics: Fingerprint scanners, facial recognition, and iris scans offer a more convenient way to authenticate compared to passwords. However, concerns about privacy and potential biases in facial recognition algorithms remain.
iii. Emerging Trends and Future Directions
A. Passwordless Authentication: Aiming to eliminate the weakest link—passwords—passwordless authentication methods use emails, text messages, or biometric information for verification. This approach not only enhances security but also significantly improves the user experience.
B. Adaptive Authentication: Adaptive or risk-based authentication adjusts the authentication requirements based on the context of access requests, such as the user’s location, device, or time of access. This dynamic approach balances security with user convenience, applying stricter measures only when necessary.
C. Decentralized Identity: Leveraging blockchain technology, decentralized identity offers a user-centric approach to authentication, allowing individuals to own and control their identity data. This not only enhances privacy and security but also reduces reliance on central authorities.
D. Quantum Authentication: With the advent of quantum computing, quantum authentication presents a theoretically unbreakable form of security. Though still in its infancy, quantum key distribution (QKD) could revolutionize authentication in the coming years.
iv. Emerging Trends: The Future of Authentication

o Passwordless Authentication: Moving beyond passwords altogether, this trend focuses on methods like magic links, biometric authentication, and security keys for a more streamlined login experience.
o FIDO (Fast Identity Online) Alliance: This industry consortium is developing standards for interoperable authentication methods, allowing users to seamlessly access various platforms using the same credentials.
o Behavioral Biometrics: This approach analyzes how you interact with your device, such as typing patterns or mouse movements, to create a unique “behavioral fingerprint” for authentication.

o Continuous Authentication: Shifting from a one-time login to ongoing monitoring, continuous authentication analyzes user behavior throughout a session to detect suspicious activity and prevent unauthorized access.
o Zero Trust Architecture: Zero Trust Architecture (ZTA) operates under the principle of “never trust, always verify.” Instead of relying on perimeter-based security, ZTA verifies every user and device attempting to access resources, regardless of their location or network. This approach minimizes the risk of lateral movement by attackers and enhances overall security posture.
o Multi-device Authentication: As we use a multitude of devices, authentication methods are becoming more flexible, allowing seamless logins from any device without needing to re-enter credentials on each one.
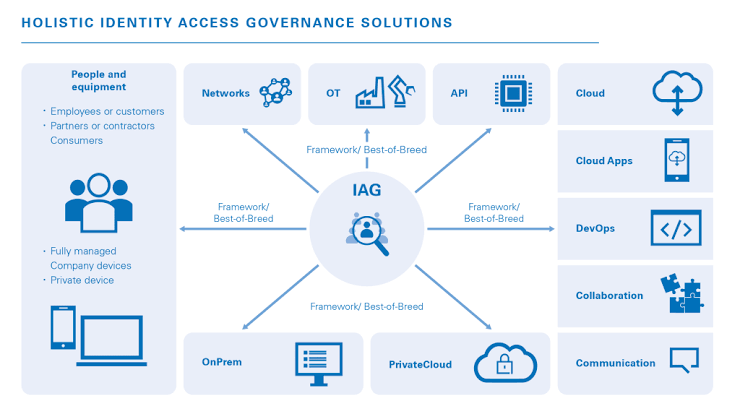
o Adaptive Authentication: Adaptive authentication solutions assess various risk factors, such as user behavior, location, and device information, to dynamically adjust the level of authentication required. By analyzing contextual data in real-time, adaptive authentication systems can provide a seamless user experience while maintaining a high level of security. This approach enables organizations to tailor authentication methods based on the risk profile of each interaction, enhancing overall security posture.
o Blockchain-Based Authentication: Blockchain technology is increasingly being utilized to enhance authentication processes through decentralized and tamper-resistant identity verification. By leveraging blockchain’s immutable ledger and cryptographic principles, organizations can establish a secure and transparent authentication framework. Blockchain-based authentication solutions offer increased data privacy, integrity, and resistance to fraud, making them a promising trend in the realm of cybersecurity.
o AI-Powered Authentication: Artificial intelligence (AI) and machine learning (ML) technologies are increasingly being utilized to enhance authentication processes. AI-powered authentication systems can analyze vast amounts of data to detect patterns and anomalies, improving accuracy and reducing false positives.
v. The Benefits of Embracing New Trends

o Enhanced Security: New authentication methods can significantly reduce the risk of unauthorized access by adding layers of complexity and making it harder for attackers to bypass security measures.
o Improved User Experience: Moving beyond passwords can create a more convenient and faster login process, reducing frustration for users.
o Reduced Reliance on Passwords: Eliminating the need for complex, memorable passwords can improve overall security posture and reduce password-related vulnerabilities.
vi. Challenges and Considerations

o Implementation Costs: New authentication methods may require investment in new infrastructure and user training.
o User Adoption: Encouraging users to adopt new authentication methods can be a challenge, requiring clear communication and education.
o Privacy Concerns: Balancing security with user privacy is crucial. Transparency regarding data collection and usage is essential for building trust.
vii. The Future of Authentication: A Collaborative Effort

The future of authentication lies in a collaborative effort between technology providers, security professionals, and users. By embracing new trends while addressing user concerns and privacy considerations, we can create a more secure and user-friendly authentication experience for everyone.
viii. Conclusion

The landscape of authentication is rapidly evolving, driven by technological advances and changing security challenges. As organizations and individuals grapple with the increasing sophistication of cyber threats, the adoption of multi-layered, user-friendly authentication methods becomes paramount.
By staying abreast of the latest tools and trends, we can fortify our digital defenses and navigate the cyber world with greater assurance and safety. The future of authentication promises not only enhanced security but also an improved digital experience, shaping a landscape where trust and convenience coexist.
ix. Further references
Newest Authentication Technologies and Tools for Data Security – LinkedIn
Wultrahttps://www.wultra.com › blog › t…The Top 5 Emerging Trends in Banking Authentication – Blog
CBT Nuggetshttps://www.cbtnuggets.com › blog6 App Security Trends from OWASP Top 10 2024