The Cyber Security Body of Knowledge (CyBOK) is a comprehensive and authoritative source of cyber security information.
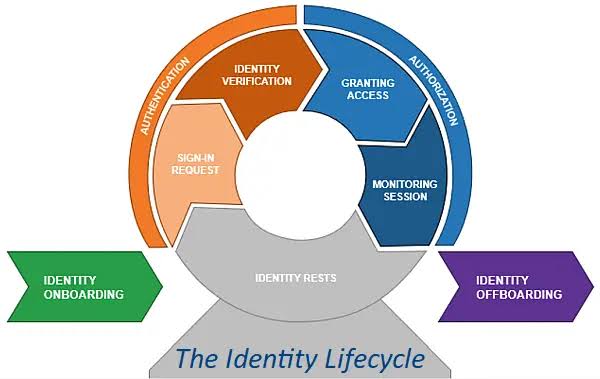
Within CyBOK, Authentication, Authorization, and Accountability (AAA) form a crucial trio of concepts in the domain of identity and access management (IAM), which altogether ensure that only legitimate users can access system resources, and that they only access resources appropriate to their permissions, with appropriate tracking of their activities.
i. Let us briefly elaborate on each:
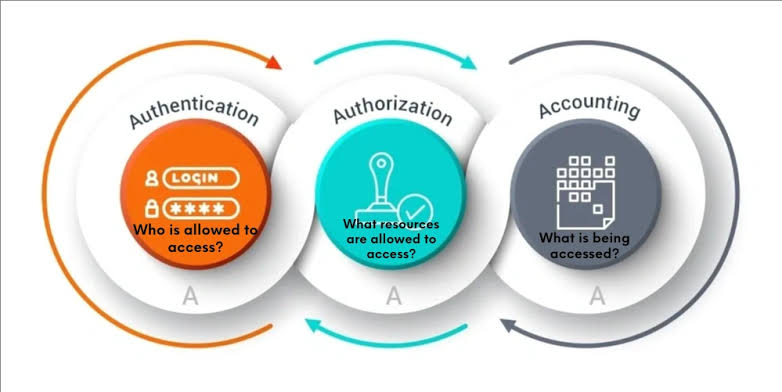
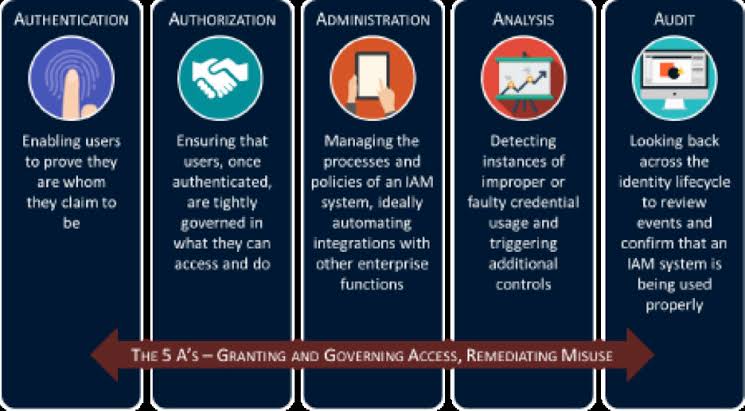
A. Authentication: This is the process of verifying the identity of a user, device, or other entity in a computer system, often as a prerequisite to allowing access to resources in that system. Authentication can involve various methods, including passwords, biometric scans, smart cards, or more complex multi-factor authentication (MFA) mechanisms.
B. Authorization: Once authentication is confirmed, authorization is the process that determines what an authenticated user is allowed to do. For example, a regular user might have permission to read certain files but not to change them, while an administrator might have broader access. Authorization ensures that users have access to the appropriate levels of functionality or data that they’re permitted to and prevents them from accessing areas they shouldn’t.
C. Accountability: Accountability refers to the ability to trace actions performed on a system back to the individual who performed them. This is typically realized through logging and audit trails, which helps in maintaining records of user activities, and is essential for various purposes like security monitoring, forensic analysis, and regulatory compliance.
ii. Key Themes:
A. Authentication:
o Establishing the identity of a user or entity attempting to access a system or resource.
o Examining various authentication factors (something you know, something you have, something you are) and techniques (passwords, multi-factor authentication, biometrics).
o Exploring vulnerabilities and countermeasures for common authentication attacks (password cracking, phishing, credential stuffing).
B. Authorization:
o Controlling access to resources and operations based on user permissions and roles.
o Analyzing access control models (discretionary, mandatory, role-based, attribute-based) and their applications in different contexts.
o Discussing techniques for managing and enforcing authorization policies effectively.
C. Accountability:
o Ensuring that actions taken within a system are traceable to specific individuals or entities.
o Implementing audit trails, logging mechanisms, and non-repudiation techniques for accountability.
o Addressing privacy concerns and compliance requirements related to accountability measures.
D. Access Control Systems:
o Exploring different types of access control systems (centralized, decentralized, federated) and their architectures.
o Examining the implementation and management of access control systems in various environments.
E. Identity Management:
o Understanding the processes and technologies for managing digital identities securely.
o Covering identity life cycle management (provisioning, authentication, authorization, revocation) and identity federation concepts.
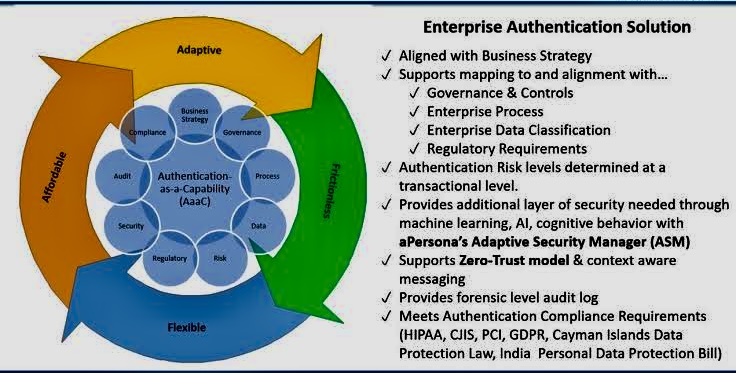
F. Emerging Trends:
o Discussing trends like passwordless authentication, continuous authentication, and blockchain-based identity management.
o Areas such as zero-trust security models, continuous authentication, and the integration of AI in access control.
iii. Benefits of Understanding the AAA Knowledge Area:
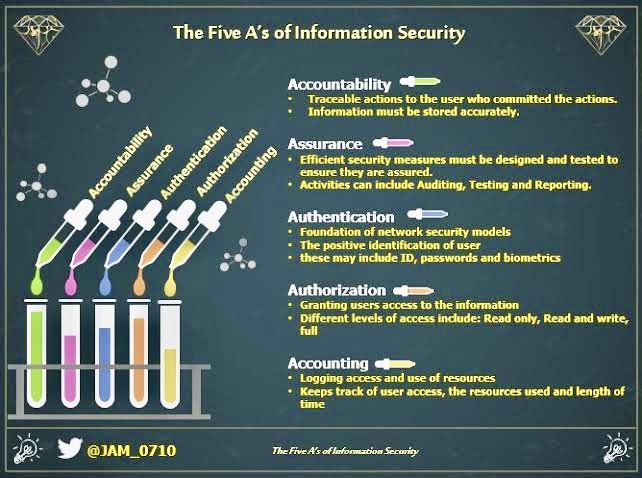
A. Enhanced security posture: Implementing robust AAA mechanisms is crucial for protecting systems and data from unauthorized access and misuse.
B. Compliance with regulations: Many industry and government regulations mandate strong authentication and access control practices.
C. Improved user experience: Balancing security with usability through efficient and user-friendly AAA mechanisms enhances user satisfaction.
D. Reduced risk of data breaches: Effective AAA helps prevent unauthorized access to sensitive data, reducing the risk of breaches and associated costs.
E. Enhanced accountability: Traceability of actions enables investigations, audits, and compliance with legal requirements.
iv. Resources:
A. Books:
o “Computer Security: Principles and Practice” by William Stallings and Lawrie Brown.
o “Guide to Computer Network Security” by Joseph Migga Kizza.
o “Identity and Data Security for Web Development” by Jonathan LeBlanc and Tim Messerschmidt.
B. Research Papers & Reports:
o “The Protection of Information in Computer Systems” by Jerome Saltzer and Michael D. Schroeder.
o NIST’s resource on Identity and Access Management.
o The IETF RFC 7633, “X.509v3 Transport Layer Security (TLS) Client Authentication”.
C. Websites & Online Resources:
o The Open Web Application Security Project (OWASP).
o Resources on Identity and Access Management from NIST.
D. Courses & Tutorials:
o Udacity’s course on “Authentication & Authorization: OAuth,”
o Course on “Information Security: Authentication and Access Control” on Coursera.
E. Webinars, Podcasts, & Videos:
o Conversations around identity and access management on the podcast “Identity, Unlocked.”
o Webinars about AAA on ISACA’s resources page.
The AAA framework is central to designing secure systems and is implemented through various protocols and systems, like Kerberos for authentication, Role Based Access Control (RBAC) for authorization, and logging and monitoring tools for accountability.
CyBOK and other literature in the cyber security field provide extensive details on these concepts, their implementations, best practices, and the challenges associated with them.
Overall, CyBOK’s Authentication, Authorization, and Accountability Knowledge Area provides a structured approach to understanding, implementing, and adapting security measures in the ever-changing landscape of digital systems and cyber threats.
