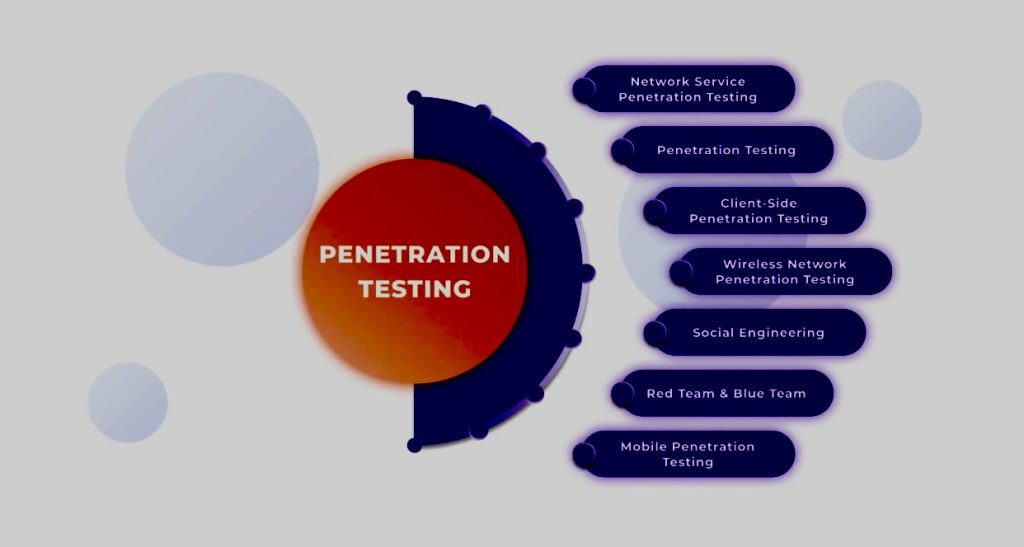
Third-party penetration testing, also known as ethical hacking, is a proactive and authorized attempt that offers various benefits to organizations seeking to enhance their cybersecurity posture.
Here are some significant benefits of opting for this:
A. Identifying Vulnerabilities: Penetration testing helps identify vulnerabilities in systems, networks, and applications that could be exploited by malicious actors. This proactive approach allows organizations to address weaknesses before they can be leveraged for cyberattacks.
B. Real-World Simulation: Penetration tests simulate real-world cyberattacks, providing a realistic assessment of an organization’s security resilience. This approach helps organizations understand how well their defenses hold up under simulated attack scenarios.
C. Risk Mitigation: By uncovering and addressing vulnerabilities, penetration testing assists in mitigating potential risks. Organizations can prioritize and fix identified issues, reducing the likelihood of successful cyberattacks.
D. Compliance Assurance: Many industry regulations and standards require organizations to conduct regular security assessments, including penetration testing. Some industries require regular third-party penetration testing for compliance with regulations such as PCI DSS and HIPAA.
E. Unbiased Assessment: A third party can provide an objective view of your security posture. They won’t overlook anything due to familiarity or bias and will assess your system from a new perspective.
F. Verification of Security Controls: Penetration testing verifies the effectiveness of existing security controls. This includes firewalls, intrusion detection/prevention systems, and other security mechanisms. The testing helps ensure that these controls operate as intended.
G. Protecting Sensitive Data: Organizations often handle sensitive information, and a breach could lead to data loss or compromise. Penetration testing helps identify and address vulnerabilities that could be exploited to gain unauthorized access to sensitive data.
H. Understanding Attack Paths: Penetration testers analyze potential attack paths that adversaries might use to infiltrate an organization’s systems. This understanding enables organizations to fortify their defenses in critical areas.
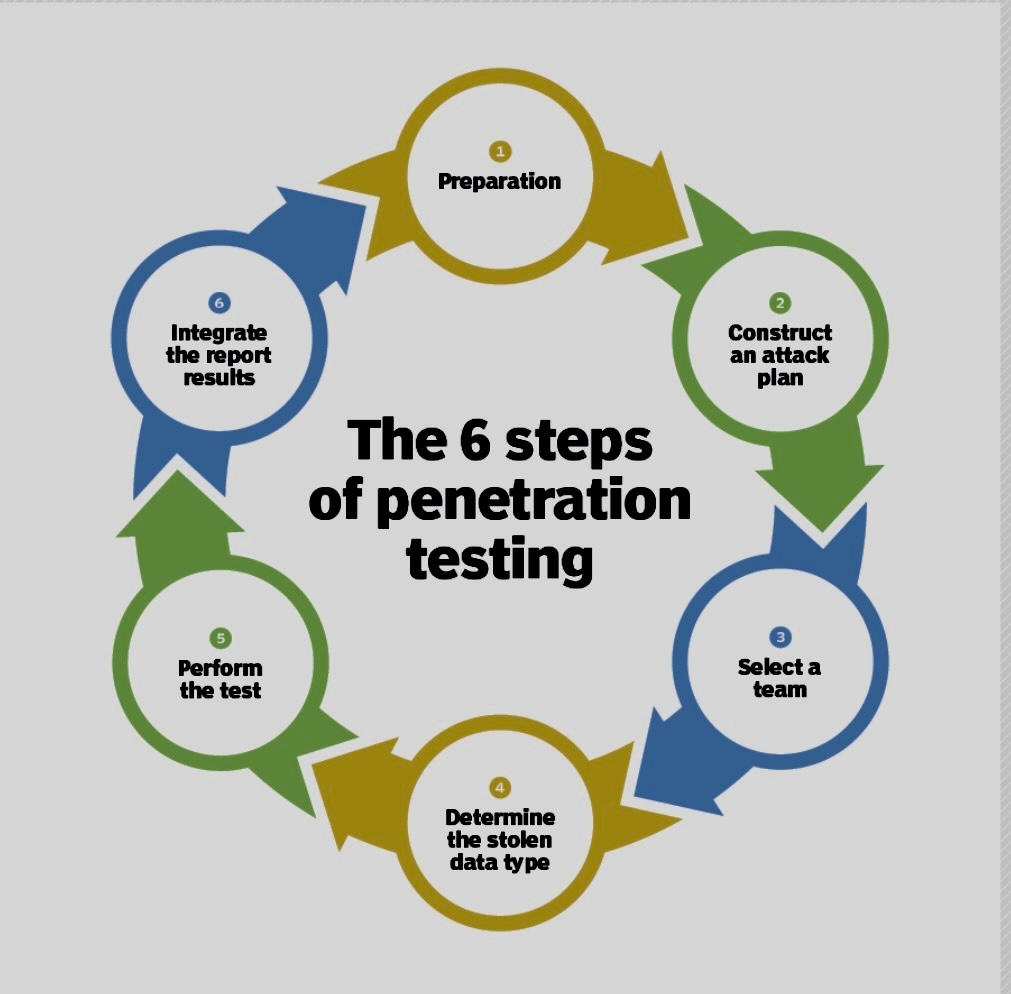
I. Prioritizing Remediation Efforts: Penetration test reports provide insights into the severity of vulnerabilities, allowing organizations to prioritize remediation efforts. This helps allocate resources efficiently, focusing on addressing the most critical issues first.
J. Enhancing Incident Response: In the event of a security incident, having undergone penetration testing enhances an organization’s incident response capabilities. Teams are better prepared to detect, contain, and remediate security breaches effectively.
K. Building Stakeholder Confidence: Demonstrating a commitment to security through regular penetration testing builds confidence among customers, partners, and stakeholders. It signals that the organization takes proactive measures to protect its digital assets.
L. Trust Building: Demonstrating that your organization undertakes regular third-party penetration testing can help build trust with customers, partners, and stakeholders.
M. Security Awareness Improvement: Penetration testing raises awareness about potential security threats among employees. It encourages a security-conscious culture and promotes better adherence to security policies and practices.
N. Continuous Improvement: Penetration testing is not a one-time activity; it’s an iterative process. Regular testing allows organizations to continuously improve their security measures, adapting to evolving cyber threats.
O. Avoiding Business Disruption: Identifying and fixing vulnerabilities before they are exploited helps avoid potential business disruptions caused by cyberattacks. This proactive stance safeguards operations and maintains business continuity.
P. Cost Savings in the Long Run: While there’s an investment in conducting penetration tests, it often leads to long-term cost savings. Addressing vulnerabilities before they result in a breach is more cost-effective than dealing with the aftermath of a successful attack.
Q. Competitive Advantage: Organizations that prioritize and demonstrate a commitment to cybersecurity through penetration testing gain a competitive advantage. It can be a differentiator in the eyes of clients and partners who prioritize security in their business relationships.
R. Expertise: Third-party testers bring a wealth of knowledge from different industries and cases. Their expertise can help find vulnerabilities that an internal team might miss.
Third-party penetration testing plays a crucial role in enhancing cybersecurity by identifying and addressing vulnerabilities, improving incident response capabilities, and building stakeholder confidence. It is a proactive and strategic investment that contributes to the overall resilience of an organization’s digital infrastructure.
https://www.digitalxraid.com/3rd-party-penetration-testing/
https://drata.com/blog/penetration-testing
https://www.guidepointsecurity.com/penetration-testing-as-a-service/
https://www.knowledgehut.com/blog/security/penetration-testing-guide
https://networkassured.com/security/penetration-testing-for-small-business/

