
Bolstering Cybersecurity Capabilities: Strengthening Defenses in a Digital World
In today’s interconnected world, where digital technology permeates every aspect of our lives, cybersecurity has become a paramount concern. From personal data protection to safeguarding critical infrastructure, the stakes have never been higher.
As cyber threats continue to evolve in sophistication and frequency, organizations and individuals alike must take proactive measures to bolster their cybersecurity capabilities.
i. Understanding the Landscape
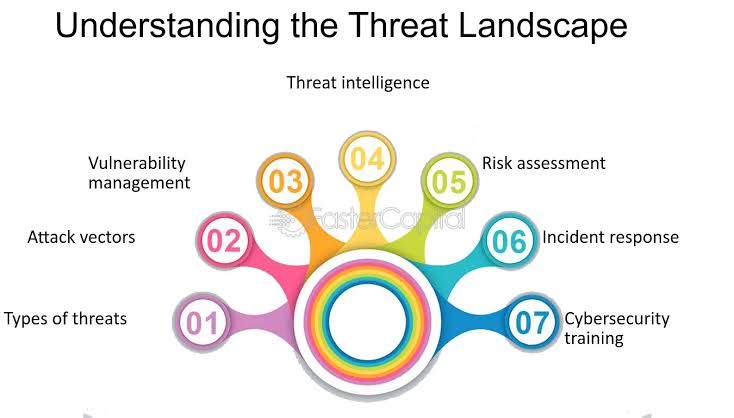
The first step in enhancing cybersecurity capabilities is understanding the rapidly evolving threat landscape. Cyber threats can range from malware and phishing attacks to sophisticated nation-state-sponsored cyber espionage. Keeping abreast of the latest types of cyber threats and attack methodologies is crucial for developing effective defense mechanisms.
ii. Comprehensive Risk Assessment

Conducting thorough risk assessments allows organizations to identify their most valuable assets and the potential vulnerabilities that could be exploited by cyberattacks. This process involves evaluating the existing security infrastructure, identifying gaps, and prioritizing risks based on their potential impact. A comprehensive risk assessment forms the foundation for any robust cybersecurity strategy.
iii. Building a Strong Cybersecurity Foundation

Bolstering cybersecurity capabilities begins with building a strong foundation based on best practices and industry standards. This includes implementing robust security policies, conducting regular risk assessments, and ensuring compliance with relevant regulations and frameworks such as GDPR, HIPAA, and NIST Cybersecurity Framework. Additionally, organizations should prioritize cybersecurity awareness and training programs to educate employees about common threats and security best practices.
iv. Implementation of Layered Security Measures
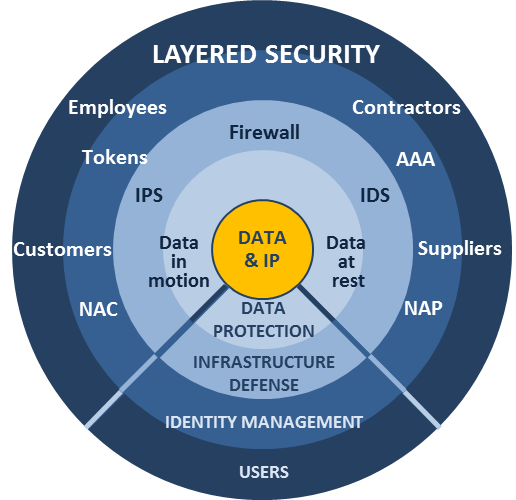
Cybersecurity is not a one-size-fits-all proposition. An effective approach involves implementing multiple layers of security measures to protect against a wide range of threats.
This can include:
o Endpoint Protection: Utilizing antivirus software, intrusion detection systems, and firewall protection for all devices connected to the network.
o Encryption: Employing encryption for data at rest and in transit, ensuring that sensitive information remains secure.
o Access Control: Adopting strict access control policies, including the use of multi-factor authentication (MFA) to prevent unauthorized access to systems and data.
o Network Security: Securing the network infrastructure through segmentation, monitoring, and regular security assessments to detect and respond to threats promptly.
v. Crucial Measures for Enhanced Cybersecurity

o Educate Users: Empowering employees with cybersecurity awareness training is critical. Educated users can recognize phishing attempts, avoid suspicious links, and practice safe password management.
o Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring a second verification step beyond a simple password. This significantly reduces the risk of unauthorized access.
o Prioritize Regular Patching: Software vulnerabilities are entry points for cyberattacks. Regularly patching your systems and applications addresses these vulnerabilities and keeps your defenses up-to-date.
o Embrace Endpoint Security Solutions: Endpoint security software safeguards devices like computers, laptops, and mobile phones from malware, ransomware, and other threats.
o Maintain Robust Backups: Regularly backing up your data ensures you have a copy in case of a cyberattack. Backups should be stored securely and disconnected from your main systems.
vi. Adopting a Defense-in-Depth Approach
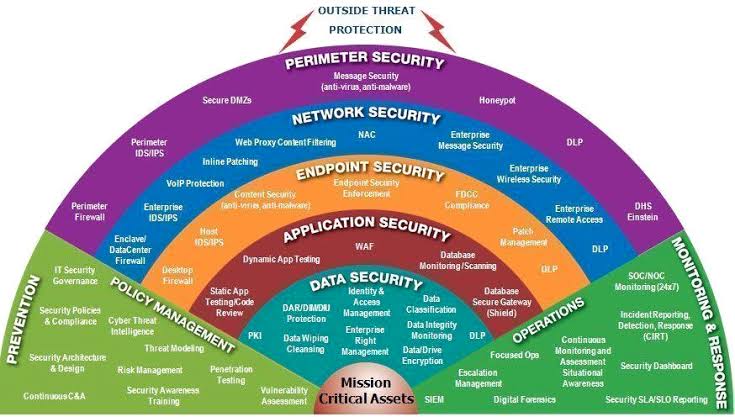
A defense-in-depth strategy involves layering multiple security measures to create overlapping defenses, thereby minimizing the likelihood of a successful cyber attack. This approach includes deploying firewalls, intrusion detection systems, antivirus software, and endpoint security solutions to protect against various threat vectors. Network segmentation, encryption, and access controls further enhance security by limiting the impact of potential breaches and unauthorized access.
vii. Cultivating Cybersecurity Talent

While technology is a crucial component of cybersecurity, the human element cannot be understated. Cultivating a skilled cybersecurity workforce is essential to understanding and mitigating cyber threats effectively.
This involves not only recruiting individuals with specialized technical skills but also providing ongoing training and education to keep pace with the rapidly changing threat landscape.
Moreover, fostering a culture of cybersecurity awareness across all levels of an organization is key to ensuring that all employees understand their role in protecting digital assets.
viii. Regular Software Updates and Patch Management
Attackers often exploit vulnerabilities in outdated software to gain unauthorized access. Maintaining a rigorous schedule for updating and patching operating systems, applications, and firmware is a critical defense mechanism against such exploits. Automated patch management systems can help streamline this process, ensuring that all components are up-to-date.
ix. Embracing Advanced Threat Detection and Response
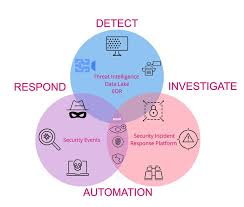
Traditional security measures alone may not be sufficient to defend against advanced and persistent cyber threats. Adopting advanced threat detection and response capabilities is crucial for identifying and mitigating sophisticated attacks in real-time. This includes deploying security information and event management (SIEM) systems, endpoint detection and response (EDR) solutions, and threat intelligence platforms to monitor for suspicious activities and proactively respond to security incidents.
x. Securing Cloud and Remote Work Environments
The shift toward cloud computing and remote work has introduced new cybersecurity challenges, as organizations grapple with securing decentralized infrastructure and endpoints. Securing cloud environments requires implementing robust identity and access management (IAM) controls, encryption, and data loss prevention (DLP) solutions. Similarly, securing remote work environments necessitates securing endpoints, enforcing VPN and multi-factor authentication (MFA), and providing security awareness training to remote employees.
xi. Embracing Advanced Technologies

Emerging technologies like artificial intelligence (AI) and machine learning (ML) are playing increasingly vital roles in cybersecurity. These technologies can analyze patterns, detect anomalies, and predict potential threats more efficiently than traditional methods. Investing in advanced cybersecurity technologies can provide organizations with a proactive rather than reactive posture against cyber threats.
xii. Implementing a Proactive Security Posture

A proactive security posture is characterized by anticipating and preparing for cyber threats before they occur, rather than reacting to them after the fact. This approach includes conducting regular security audits, vulnerability assessments, and penetration testing to identify and address potential weaknesses in the system.
Additionally, developing and maintaining an incident response plan ensures that an organization can respond swiftly and effectively in the event of a cyber attack, minimizing damage and restoring operations as quickly as possible.
xiii. Fostering Collaboration and Information Sharing

Cybersecurity is a collective effort that requires collaboration and information sharing among stakeholders, including government agencies, industry partners, and cybersecurity professionals. Sharing threat intelligence, best practices, and lessons learned can enhance collective defense capabilities and enable organizations to better anticipate and respond to emerging cyber threats. Public-private partnerships and collaboration forums play a crucial role in fostering a resilient cybersecurity ecosystem.
xiv. Conclusion

In an increasingly digitized world, cybersecurity is paramount to safeguarding data, privacy, and critical infrastructure from cyber threats.
Bolstering cybersecurity capabilities requires a multifaceted approach encompassing robust security policies, advanced technologies, and ongoing education and collaboration.
By adopting a proactive stance and implementing best practices, organizations and individuals can strengthen their defenses and mitigate the risks posed by evolving cyber threats. Together, we can build a more secure and resilient digital future.
xv. Further references
LinkedIn · Luiz Firmino, CISSP, CISM, CRISC, CCISO1 reaction · 4 months agoDecoupling for Cybersecurity: Strengthening Digital Defenses in an …
Ironhackhttps://www.ironhack.com › blogIntersections of AI and Cybersecurity: Strengthening Defenses
Medium · LeewayHertz1 like · 5 months agoStrengthening Digital Defense: The Role of AI in Cybersecurity | by LeewayHertz | Predict
LinkedIn · Robert Burkett4 reactions · 2 weeks agoCybersecurity: Strengthening Defenses & Resilience
Kloud9 IT, Inc.https://www.kloud9it.com › 2023/08Strengthening Your Digital Defenses: A Comprehensive Guide to Cybersecurity
LinkedInhttps://www.linkedin.com › pulseEffective Strategies for Strengthening … – LinkedIn
Superfast IThttps://blog.superfast-it.com › stre…Strengthening Your Business’s Cyber Security
SC Mediahttps://www.scmagazine.com › briefGoogle seeks to bolster cybersecurity with AI
ResearchGatehttps://www.researchgate.net › 3593…(PDF) Digital Innovation on Cyber Security-An …
ResearchGatehttps://www.researchgate.net › 375…(PDF) CYBERSECURITY IN THE DIGITAL SPACE
ScienceDirect.comhttps://www.sciencedirect.com › piiAttributes impacting cybersecurity policy development: An evidence from seven …
Amaris Consultinghttps://amaris.com › ViewpointResilient Guardians: The Human Firewall of the Digital Realm
ResearchGatehttps://www.researchgate.net › 376…Artificial Intelligence and Cybersecurity: Innovations, Threats, and Defense …
USThttps://www.ust.com › InsightsEmbracing Generative AI in Cybersecurity: A Guide for Professionals, Decision-Makers …
