AI Management Systems: The Business Blueprint for the Age of Intelligence
AI management systems refer to a suite of tools and practices designed to control, manage, and optimally utilize Artificial Intelligence (AI) in a business setting.
The eruption of artificial intelligence (AI) across the corporate landscape has sparked a transformation unlike any other. With this intelligent disruption comes the challenge of managing AI systems across an enterprise.
From the mom-and-pop shop adopting a chatbot to multinational corporations implementing complex AI algorithms, each business must navigate a new world where AI is a core part of the management strategy.
AI Management Systems (AIMS) can help navigate this complexity, ensuring responsible and successful AI implementation.
i. What are AIMS?

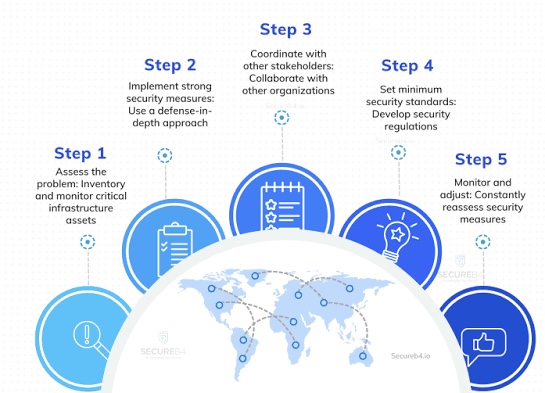
AIMS are frameworks and tools that guide the planning, development, deployment, and monitoring of AI initiatives within an organization.
They encompass elements like:
o Governance: Policies and procedures for ethical, responsible, and transparent AI use.
A. Risk Management: Identifying, assessing, and mitigating risks associated with AI projects.
B. Data Management: Ensuring data quality, security, and privacy for AI models.
C. Model Development & Deployment: Implementing robust processes for building, testing, and deploying AI models.
D. Performance Monitoring: Continuously evaluating and improving the effectiveness of AI solutions.
ii. Why do businesses need them?

AIMS offer several benefits:
A. Reduced Risks: Mitigates potential biases, privacy concerns, and safety hazards associated with AI.
B. Improved Governance: Ensures transparency and accountability in AI decision-making.
C. Enhanced Efficiency: Streamlines AI development and deployment processes.
D. Increased ROI: Maximizes the value and impact of AI investments.
E. Compliance: Helps comply with regulations and ethical standards governing AI.
iii. Key considerations for implementation:

A. Alignment with business strategy: Ensure AI objectives align with overall business goals.
B. Stakeholder engagement: Involve diverse stakeholders in AIMS development and implementation.
C. Data infrastructure: Establish a robust data infrastructure to support AI development.
D. Talent and resources: Invest in building internal expertise or seek external support.
E. Continuous improvement: Regularly review and update the AIMS to adapt to evolving needs.
iv. Choosing the right AIMS:

Several AIMS frameworks are available, each with its strengths and weaknesses. Consider factors like:
A. Industry and regulatory requirements.
B. Size and complexity of your organization.
C. Specific AI use cases and risks.
D. Available resources and budget.
v. How businesses can appreciate the value AI brings and align AI objectives with business goals.
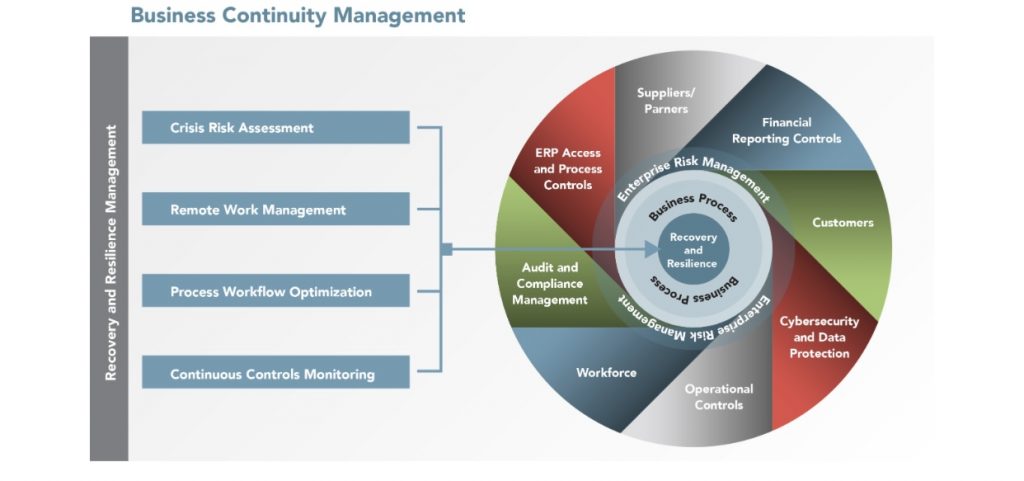
A. Data: The Lifeblood of AI Systems:
AI feeds on data. Robust data governance and management are foundational to an effective AI system. Businesses must not only ensure access to high-volume data but also guarantee its relevance, quality, and integrity. Clean and well-structured data directly influence the effectiveness and reliability of AI outcomes.
B. Integration: The Harmony of Systems:
True power lies not in AI alone but in its integration with existing business systems. It’s imperative for AI to mesh seamlessly with legacy systems, CRM software, or any digital interface that drives the business. When AI becomes a cog integrated into the larger machine, it empowers the whole unit to operate more efficiently.
C. Ethics and Bias: The Guiding Principles:
As we entrust AI with the decision-making process, we must scrutinize the principles that guide it. Potential biases in algorithmic decisions can lead to discriminatory outcomes, while issues of transparency remain hot topics. A vigilant approach to ethics in AI ensures businesses maintain trust and comply with societal norms and expectations.

D. Regulation: The Invisible Fences:
Businesses are no strangers to regulatory constrictions. With AI, especially in areas involving personal data, understanding and adhering to regulations like GDPR are non-negotiable. The cost of non-compliance does not only hit financially but can also impair brand reputation.
E. Talent: The Human Element in AI:
The scarcity of AI talent has put a premium on skilled professionals who can navigate the complex landscape of AI technologies. Businesses must cultivate a pool of talent, be it through new hires or upskilling existing employees, to manage and evolve AI capabilities.
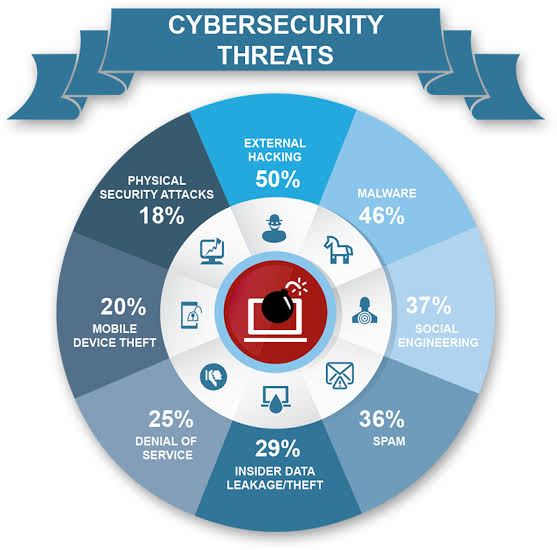
F. Security: The Protective Shield:
AI systems, with their treasure trove of data, can be irresistible targets for cyberattacks. Protecting AI assets goes beyond safeguarding data; it includes defending the integrity of AI algorithms and ensuring they function as intended.
G. Scalability: Growing Smart:
Scalability should be a core consideration as it dictates the long-term viability of AI systems. As business demands balloon, AI infrastructure must soar in tandem to support growth while maintaining performance standards.
H. Monitoring and Maintenance: Keeping the Pulse:
Continuous oversight is not a luxury but a necessity for any AI deployment. It ensures efficiency, allows for timely interventions, and keeps the AI systems in sync with evolving business landscapes.

I. Performance Metrics: Measuring Success:
Not everything that counts can be counted, but in the business world, what gets measured gets managed. Defining clear KPIs to track AI’s performance is crucial for evaluating success. It informs the business whether the AI deployment is a cost center or a game-changer.
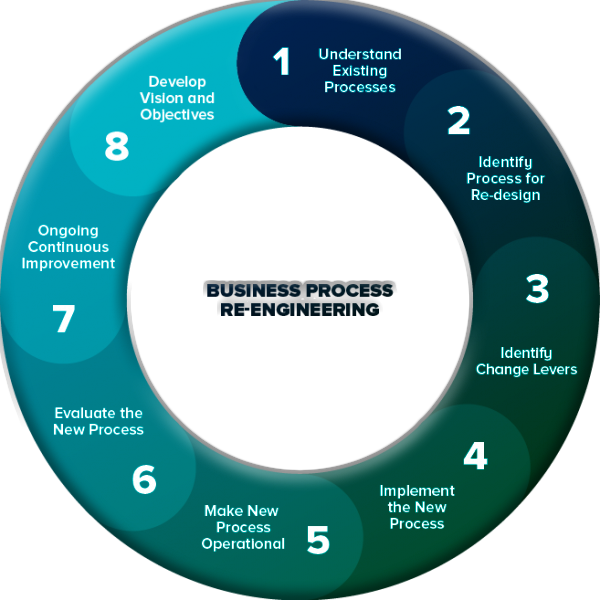
J. Continuous Improvement: The Never-ending Journey:
AI is not a set-and-forget system but a living entity within the corporate framework. It must evolve through iterative enhancements and learning from real-world feedback. This philosophy of continual refinement must permeate the business’s culture to realize AI’s full potential.
vi. The future of AIMS:
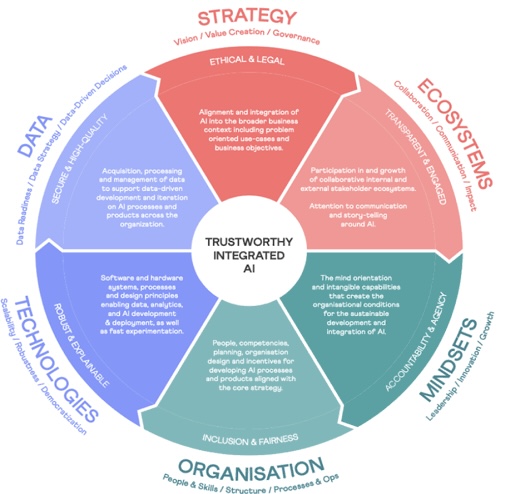
As AI technology evolves, AIMS will need to adapt. Emerging trends include:
o Standardization of best practices and regulations.
o Integration with existing management systems.
o Increased focus on explainability and accountability of AI.
o Development of AI-powered AIMS for advanced automation.
vii. Conclusion:

Understanding AI and Its Enterprise Impact:
Before diving into the management of AI, businesses must first grasp AI’s capabilities and the magnitude of its impact on enterprise strategy. This technology isn’t a mere tool but rather a transformative force capable of remolding entire operational processes.
viii. Further references
AI management systems: What businesses need to know – ISO
Qualeticshttps://qualetics.com › ai-manageme…AI Management System – Part 1: The Fundamentals
PwC Australiahttps://www.pwc.com.au › pdfPDFArtificial intelligence: What directors need to know