Navigating New Horizons: Emerging ITSM Job Roles in the Age of AI
As Artificial Intelligence (AI) continues its relentless march into every facet of technology, widespread adoption in the realm of IT Service Management (ITSM) is not just a possibility—it’s an inevitability.
This seismic shift promises not only to reshape existing roles but also to catalyze the creation of entirely new positions.
For ITSM professionals, this evolution presents an unparalleled opportunity to pioneer roles at the forefront of AI integration in IT services.
In this dynamic environment, several emerging job roles stand out as critical to managing and leveraging AI within ITSM frameworks.
i. From Automation Experts to AI Orchestrators

o AI Implementation Specialists: With the influx of AI tools, specialists will be needed to design, implement, and integrate these tools within existing ITSM frameworks. They will ensure seamless operation and maximize the value derived from AI.
o Data Analysts for AI-Driven Insights: Data is the fuel for AI. ITSM professionals with strong data analysis skills will be crucial to interpret the data generated by AI-powered tools, identify actionable insights, and optimize service delivery.
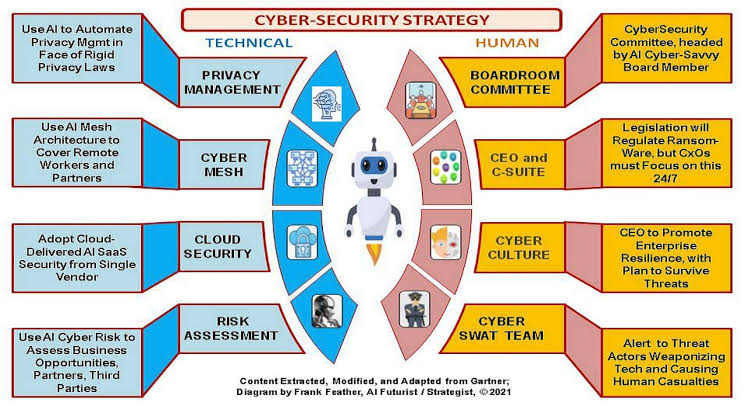
o ITSM Security Specialists for the AI Era: As AI becomes more prevalent, securing AI systems and data will be paramount. ITSM professionals with expertise in cybersecurity will be sought after to safeguard AI tools and prevent potential breaches.
ii. The Evolving Role of the ITSM Professional

These new roles highlight the evolving nature of the ITSM profession. While core ITSM principles remain important, the ability to collaborate with AI, leverage data for insights, and ensure security will be key differentiators.
iii. AI Adoption in ITSM: Breeding Ground for New Opportunities

iii.i Governance and Strategy

A. AI Governance and Strategy Consultants
As organizations navigate the complexities of AI adoption, there is a growing demand for consultants who can provide strategic guidance and governance frameworks tailored to the unique needs of ITSM environments. AI governance and strategy consultants help organizations develop roadmaps, define objectives, and establish governance structures to align AI initiatives with business goals and ensure long-term success.
B. Digital Transformation Consultant
Organizations adopting AI within their ITSM processes are essentially undergoing a digital transformation. Digital Transformation Consultants specialize in guiding organizations through this journey. They assess current ITSM practices, identify opportunities for AI integration, and develop strategies to leverage AI for service improvement. Their role is critical in ensuring a seamless transition to AI-powered ITSM, minimizing disruption, and maximizing the benefits of AI adoption.
C. AI-Enhanced ITSM Strategy Architect
The AI-Enhanced ITSM Strategy Architect will play a pivotal role in designing the overarching ITSM strategy, ensuring seamless integration of AI technologies. This role involves analyzing organizational needs, evaluating AI technologies, and crafting strategic plans that leverage AI to optimize IT service delivery. These architects will bridge the gap between AI possibilities and ITSM necessities, ensuring that AI initiatives align with business objectives and ITSM frameworks.
D. AI Ethics Compliance Manager
As organizations navigate the complexities of ethical AI use, the role of an AI Ethics Compliance Manager becomes increasingly significant. This professional is responsible for ensuring that AI implementations adhere to ethical guidelines, regulatory requirements, and organizational values. They will work closely with AI developers, ITSM teams, and legal departments to scrutinize AI algorithms for biases, privacy concerns, and potential ethical pitfalls, ensuring transparent and fair use of AI technologies.
E. AI Ethicists and Compliance Officers
As AI technologies become more pervasive, organizations must address ethical considerations and ensure compliance with regulatory standards. AI ethicists and compliance officers within ITSM teams are responsible for developing and enforcing ethical guidelines, data privacy policies, and regulatory compliance frameworks to mitigate risks associated with AI implementation and usage.
F. Data Trustee
AI systems rely heavily on data—to learn, make decisions, and provide insights. The Data Trustee is responsible for managing and safeguarding this data within the ITSM context. This role involves ensuring data accuracy, integrity, and privacy, as well as managing access permissions to sensitive data used by AI systems. Data Trustees play a crucial role in establishing trust in AI systems by ensuring data is handled responsibly and ethically.
iii.ii Design and Tactics

G. AI Change Management Specialists
The introduction of AI into ITSM workflows often necessitates significant organizational changes. AI change management specialists play a crucial role in facilitating smooth transitions by assessing the impact of AI initiatives, engaging stakeholders, and implementing change strategies to promote user adoption, mitigate resistance, and ensure successful AI integration.
H. AI User Experience (UX) Specialist
The integration of AI into ITSM tools will fundamentally change how users interact with IT services. An AI User Experience (UX) Specialist will be essential for designing user interfaces and experiences that are intuitive, engaging, and effective. This role involves understanding human behavior, AI capabilities, and ITSM processes to create user interactions that enhance satisfaction and productivity.
I. AI Service Designers
With AI playing a significant role in service delivery and customer support, there is a growing demand for professionals who can design AI-driven service experiences. AI service designers collaborate with cross-functional teams to conceptualize, prototype, and deploy AI-powered service solutions that enhance user satisfaction, streamline processes, and drive business outcomes.
J. AI Security Analysts
As AI systems become more integrated into ITSM environments, the need for security professionals adept at safeguarding AI technologies against cyber threats grows. AI security analysts specialize in identifying vulnerabilities, implementing robust security measures, and conducting regular audits to protect AI algorithms, data, and infrastructure from malicious attacks and breaches.
iii.iii Implementation and Operation

K. AI Implementation Specialists
With the integration of AI technologies into ITSM frameworks, there arises a need for specialists who can oversee the seamless implementation of AI-powered solutions. These professionals are responsible for understanding the organization’s unique requirements, selecting appropriate AI tools and platforms, and integrating them into existing ITSM processes while ensuring compliance and security.
L. AI Operations Analysts
As AI systems become integral to ITSM operations, the demand for analysts who can monitor, maintain, and optimize AI algorithms and models increases. AI operations analysts leverage data analytics and machine learning techniques to continuously improve AI performance, identify anomalies, and troubleshoot issues to ensure the reliability and efficiency of AI-driven ITSM processes.
M. AI Service Manager
The AI Service Manager role encompasses managing the lifecycle of AI-powered services within the ITSM framework. This includes planning, designing, delivering, and improving AI services to meet organizational objectives and user needs. They act as a bridge between ITSM teams, AI developers, and business units, ensuring that AI services align with business goals and deliver value. Their responsibilities also include monitoring the performance of AI services and gathering feedback for continual service improvement.
N. AI Operations Specialist
With AI systems becoming integral to IT service delivery, there is a burgeoning need for specialists who can manage the operational aspects of AI technology. An AI Operations Specialist will oversee the deployment, maintenance, and optimization of AI tools and solutions within the ITSM ecosystem. This role involves ensuring that AI systems are running efficiently, troubleshooting any issues, and updating systems to adapt to new requirements or to leverage new AI advancements.
O. AI Training and Development Coordinators
To maximize the benefits of AI technologies, organizations need employees who are proficient in leveraging AI tools effectively. AI training and development coordinators design and deliver training programs, workshops, and resources to upskill ITSM professionals and empower them to harness the full potential of AI-driven capabilities in their roles.
iv. A Thriving Future for ITSM Professionals

The future of ITSM is bright. By embracing AI and developing the necessary skillsets, ITSM professionals can thrive in this new era. The human-AI partnership will lead to a more efficient, intelligent, and future-proof approach to IT service management.
v. Conclusion

The advent of AI in ITSM opens up a myriad of opportunities for ITSM professionals willing to adapt and evolve.
The emergence of these new roles underscores the importance of AI in the future of IT service management and highlights the need for a skilled workforce that can harness the power of AI to drive service excellence.
As the landscape continues to change, continuous learning and adaptability will be key for ITSM professionals aiming to thrive in this new era.
ITSM professionals who embrace these emerging job roles and acquire the necessary skills will be well-positioned to thrive in an AI-driven future.
vi. Further references
LinkedIn · Resume Mansion1 month agoNavigating the age of AI: Emerging job roles for the future
edXhttps://campus.edx.org › ed…PDFNAVIGATING THE WORKPLACE IN THE AGE OF AI
CIO Divehttps://www.ciodive.com › news3 CIO considerations for the generative AI onslaught
Ranktrackerhttps://www.ranktracker.com › blogThe Future of ITSM with AI Technology …
CIO | The voice of IT leadershiphttps://www.cio.com › article › wh…Where is the AI?
Black Hathttps://www.blackhat.com › webcastWebinar: Perspectives on AI, Hype and Security