Forging the Front Line: How to Prepare for the CISO Role
In today’s digital age, the role of the Chief Information Security Officer (CISO) has never been more critical. As cyber threats become increasingly sophisticated and pervasive, organizations need a strong leader to oversee their information security strategies and safeguard their digital assets. Preparing for the CISO role requires a blend of technical expertise, strategic thinking, leadership skills, and continuous learning.
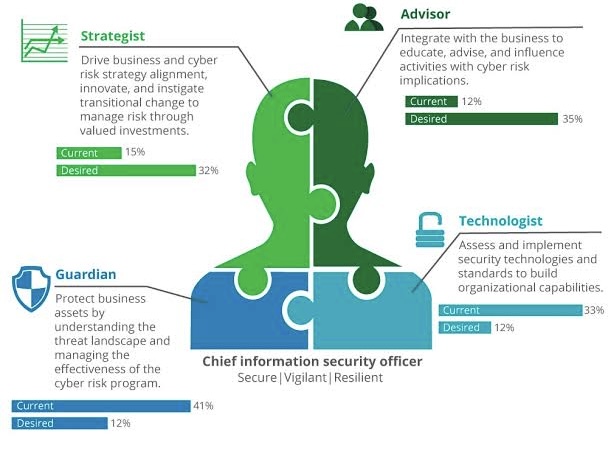
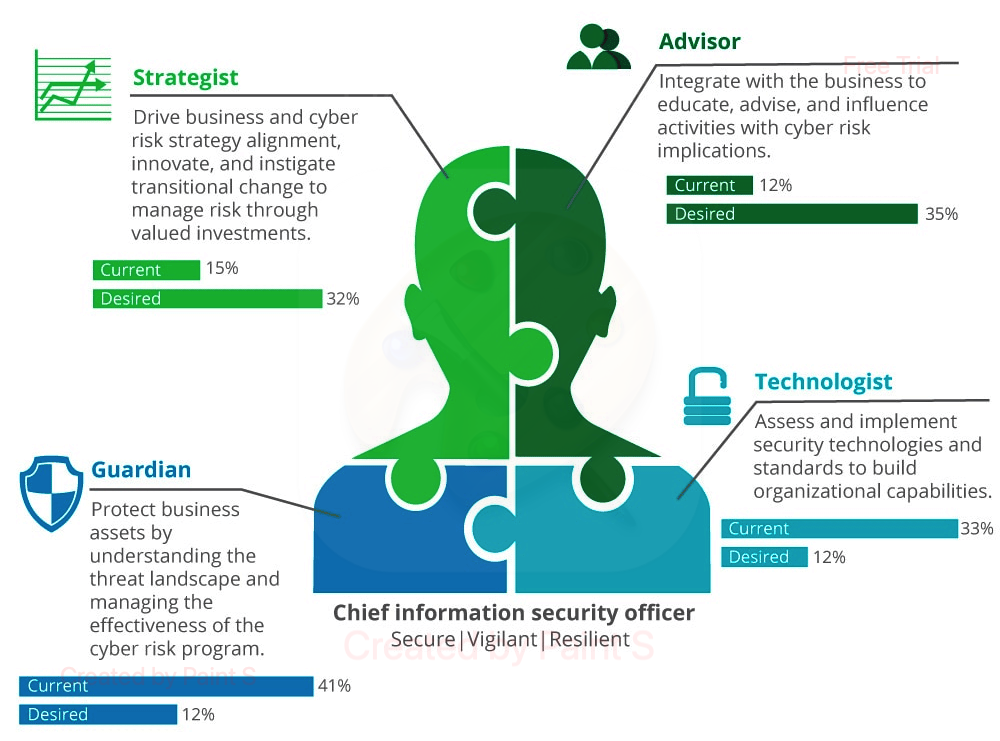
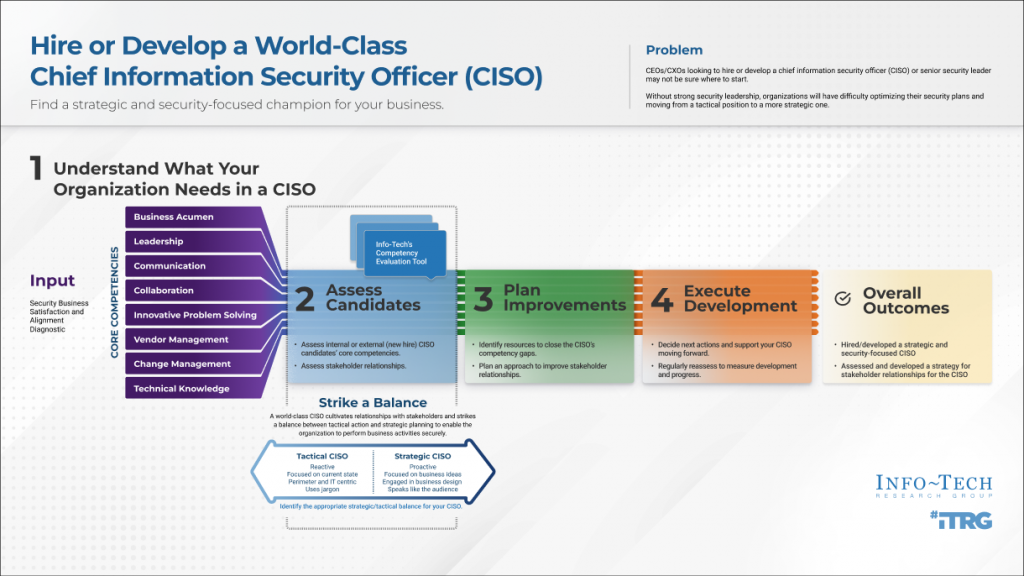
i. Understanding the Role
Key Responsibilities
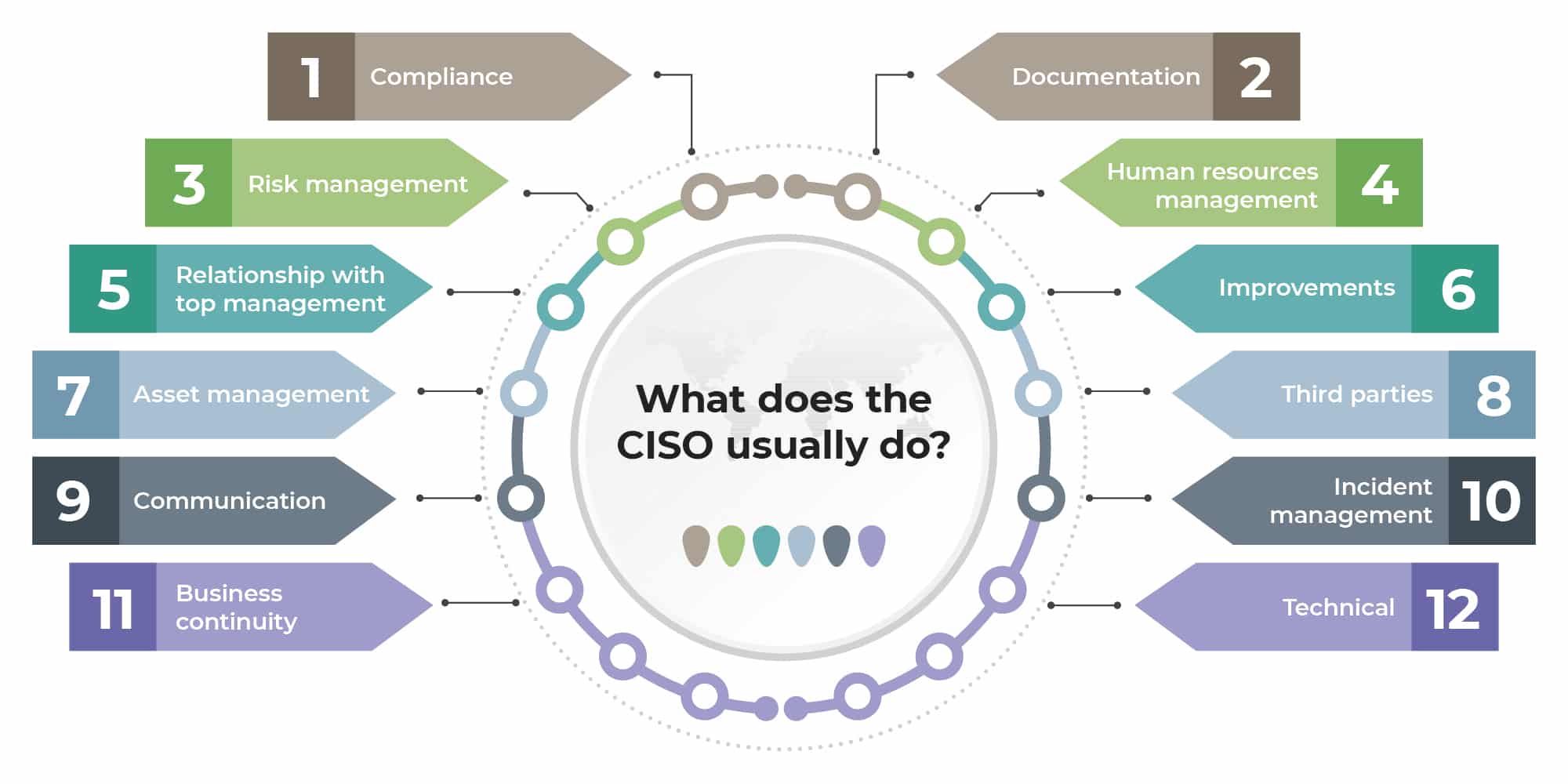
A CISO is tasked with developing and implementing an information security strategy, protecting the organization’s information assets, and ensuring compliance with regulatory requirements. Their responsibilities typically include:
- Establishing and maintaining the enterprise’s cybersecurity vision and strategy.
- Leading security operations to protect data and manage incidents.
- Coordinating with other executives to align security goals with business objectives.
- Managing security budgets, resources, and vendor relationships.
- Overseeing regulatory compliance and risk management processes.
ii. Required Skills
A. Acquire a Strong Educational Foundation
- Formal Education:
- Start with a bachelor’s degree in information technology, computer science, cybersecurity, or a related field. Advanced degrees such as a Master’s in Business Administration (MBA) with a focus on technology or a Master’s in Information Security can provide a competitive edge.
- Certifications:
- Professional certifications are crucial.
- Certified Information Systems Security Professional (CISSP): Widely recognized and covers a broad range of cybersecurity topics.
- Certified Information Security Manager (CISM): Focuses on managing and governing an enterprise’s information security program.
- Certified Information Systems Auditor (CISA): Emphasizes audit, control, and assurance skills.
- Certified Ethical Hacker (CEH): Provides knowledge on hacking methodologies and countermeasures.
- Professional certifications are crucial.
- Master Core Security Principles:
- Possess a deep understanding of core cybersecurity principles like access control, encryption, network security, and incident response.
- Stay Current with Threats:
- The cybersecurity landscape is constantly changing. Actively stay informed about emerging threats and vulnerabilities to ensure your defenses remain effective.
B. Developing Business Acumen
- Understand the Business Landscape:
- While technical expertise is crucial, a successful CISO understands the organization they serve. Gain a thorough understanding of your company’s business goals, challenges, and risk tolerance.
- Align Security with Business Objectives:
- Cybersecurity shouldn’t be an isolated function. Learn to translate business goals into a comprehensive cybersecurity strategy that protects the organization’s critical assets.
C. Gain Extensive Experience in Information Security
- Diverse Roles:
- Work in various roles within the IT and cybersecurity fields. Experience in network security, incident response, risk management, and compliance is essential. Aim to understand different aspects of information security to develop a well-rounded skill set.
- Leadership Positions:
- Seek leadership roles such as Security Manager or IT Director. These positions help you develop managerial skills, understand business operations, and gain experience in leading security teams and projects.
D. Develop Strategic Thinking and Business Acumen
- Understand Business Operations:
- A successful CISO needs to align security strategies with business objectives. Gain insights into business operations, financial management, and strategic planning. An MBA can be particularly beneficial in developing this understanding.
- Risk Management:
- Master the art of risk management. Learn how to identify, assess, and mitigate risks. This involves understanding regulatory requirements, compliance standards, and how to balance security needs with business goals.
E. Hone Your Leadership and Communication Skills
- Team Leadership:
- Develop strong leadership skills. Learn how to build, manage, and motivate security teams. Effective leadership involves setting clear goals, providing guidance, and fostering a collaborative environment.
- Master the Art of Communication:
- CISOs need to communicate effectively with diverse audiences – from technical teams to executives and the board. Refine your communication skills to articulate complex security concepts in a clear and concise manner.
- Lead by Example:
- Effective CISOs inspire and motivate their teams. Develop strong leadership skills and create a culture of security awareness within the organization.
F. Cultivating Collaboration and Advocacy
- Foster Collaboration:
- Cybersecurity is a team effort. Build strong relationships with IT, legal, and compliance departments to ensure a coordinated approach to security.
- Become a Security Advocate:
- Champion the importance of cybersecurity within the organization. Educate employees on security best practices and secure buy-in for security initiatives from senior management.

G. Stay Updated with Industry Trends and Technologies
- Continuous Learning:
- The cybersecurity landscape is constantly evolving. Stay updated with the latest threats, technologies, and best practices. Attend conferences, participate in webinars, and subscribe to industry publications.
- Networking:
- Join professional organizations like ISACA, (ISC)², and local cybersecurity groups. Networking with peers can provide valuable insights, support, and opportunities for collaboration.

H. Build a Solid Security Framework
- Policies and Procedures:
- Develop and implement robust security policies and procedures. Ensure they align with industry standards such as NIST, ISO 27001, and GDPR.
- Incident Response:
- Create and maintain a comprehensive incident response plan. Regularly test and update the plan to ensure readiness for potential security breaches.
I. Adopting a Holistic Approach
- Risk-Based Strategy
- Focus on a risk-based approach to prioritize and address the most critical threats and vulnerabilities.
- Building a Security Culture
- Foster a culture of security awareness across the organization. Regular training and awareness programs are essential.
- Incident Response and Crisis Management
- Develop and refine robust incident response plans. Being prepared to handle security breaches efficiently is crucial.
- Employee Training:
- Promote security awareness across the organization. Conduct regular training sessions to educate employees about the importance of cybersecurity and their role in protecting the organization.
- Collaboration:
- Foster a culture of collaboration between IT, security, and other departments. Encourage open communication and teamwork to address security challenges effectively.

J. Gaining Experience and Building Credibility
- Seek Leadership Opportunities:
- Look for opportunities to lead security projects or initiatives within your current organization. This allows you to demonstrate your leadership skills and ability to deliver results.
- Consider Additional Certifications:
- While not mandatory, pursuing certifications relevant to the CISO role can enhance your credibility and showcase your commitment to continuous learning.
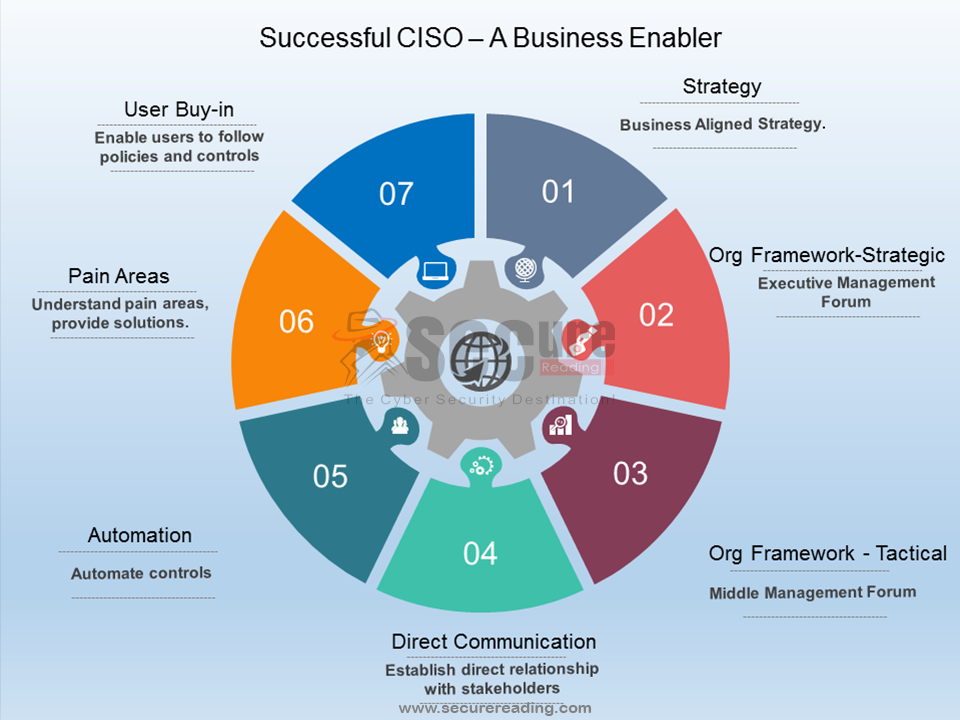
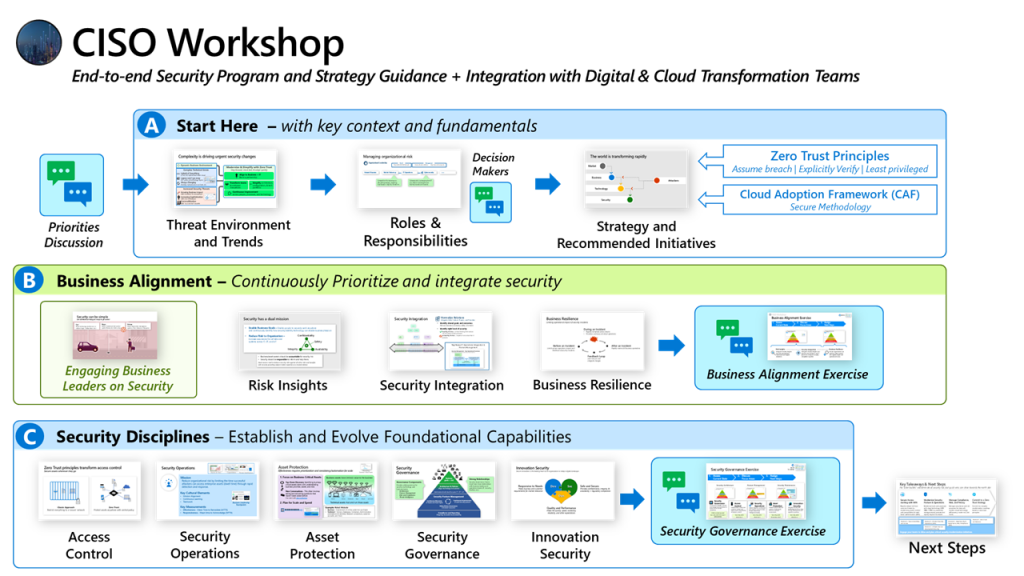
iii. Conclusion

The Journey to becoming a CISO is a continuous process of learning, development, and experience. By focusing on these key areas, you can develop the skills and expertise necessary to excel in this critical leadership role. Remember, a successful CISO is not just a technical expert; they are a strategic business leader who safeguards the organization’s crown jewels and fosters a culture of security awareness across the entire organization.
Preparing for the CISO role is a multifaceted journey that requires a blend of technical expertise, business acumen, leadership skills, and continuous learning. By following this comprehensive guide, aspiring CISOs can develop the necessary skills and experience to lead an organization’s information security efforts effectively. As cyber threats continue to evolve, the demand for skilled and strategic CISOs will only grow, making this an exciting and rewarding career path.
iv. Further references
Effective crisis management for CISOsDeloittehttps://www.deloitte.com › … › Services › Risk Advisory