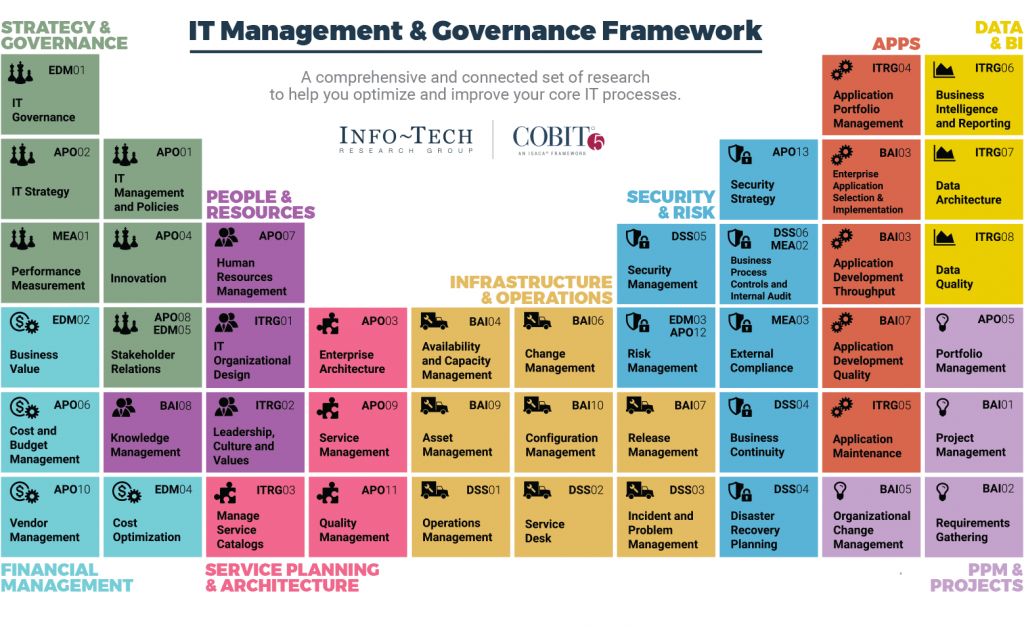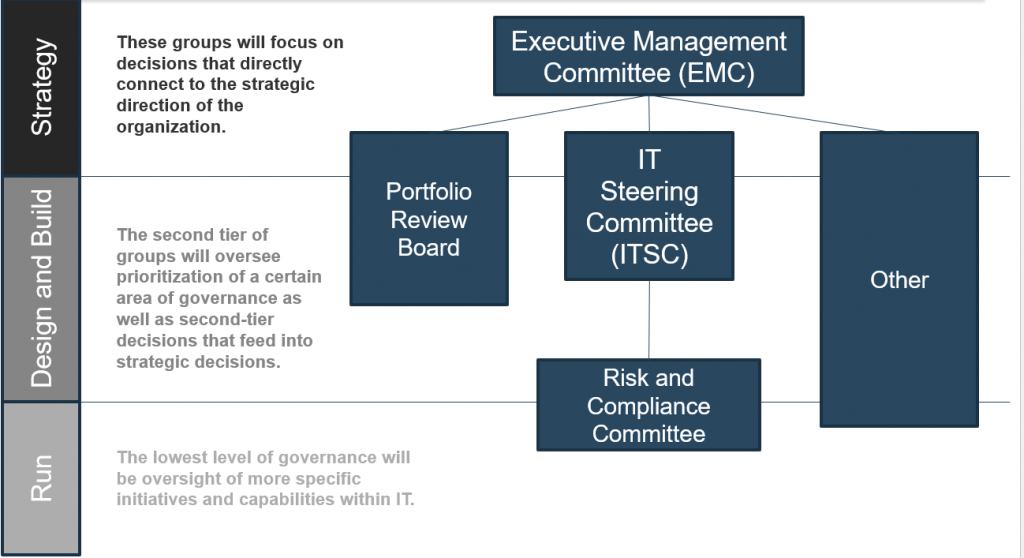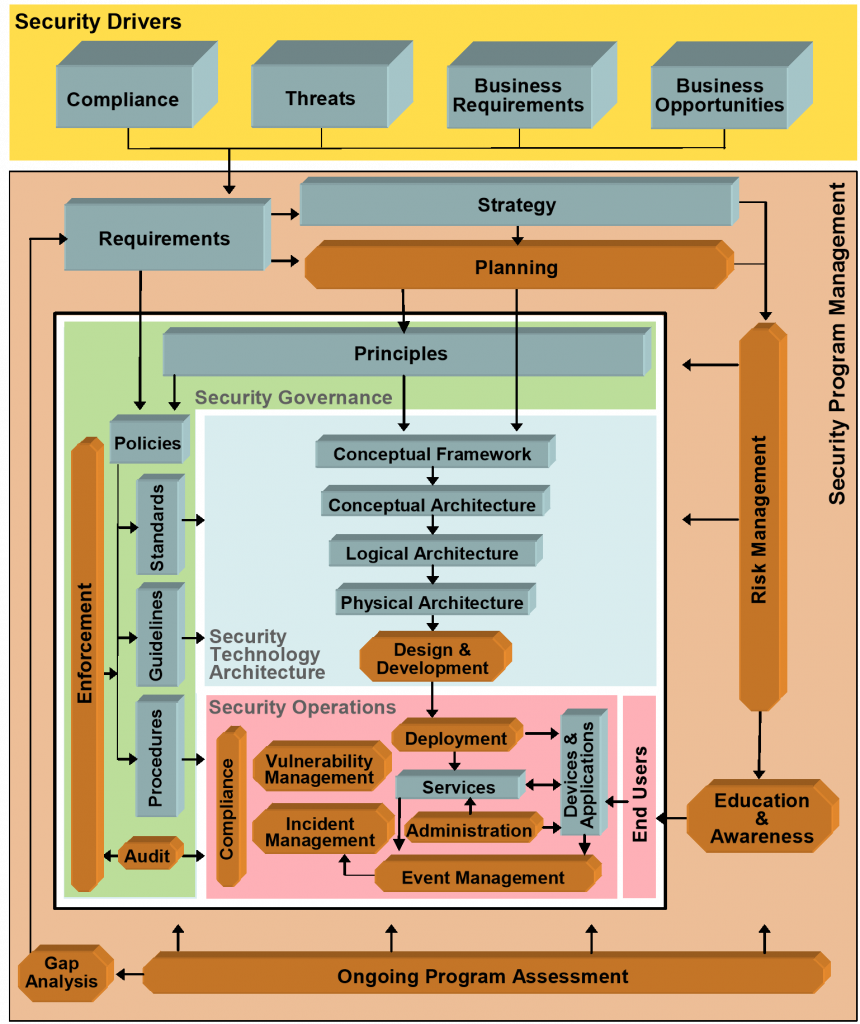
The Integrated Approach to Information Security Management: COBIT, Balanced Scorecard, and SSE-CMM
In the continuously evolving digital landscape, Information Security Management (ISM) has emerged as a pivotal concern for organizations worldwide. As cyber threats become more sophisticated, the necessity for a robust, strategic ISM framework has never been more critical. This article explores an innovative integrated approach that combines COBIT, Balanced Scorecard, and SSE-CMM into a cohesive strategic framework for enhancing information security governance and management. This holistic methodology not only aims at ensuring a high level of security but also aligns information security strategies with business objectives, optimizing performance and resource allocation in pursuit of organizational goals.
Information Security Management (ISM) involves the systematic management of an organization’s information assets to protect integrity, confidentiality, and availability. Traditional ISM approaches often operate in silos, focusing narrowly on technical challenges and overlooking the broader business context. In contrast, the integration of COBIT (Control Objectives for Information and Related Technology), Balanced Scorecard, and SSE-CMM (Systems Security Engineering Capability Maturity Model) offers a strategic, holistic approach, ensuring that information security is tightly aligned with overall business strategies and objectives.
i. Combining Frameworks for Stronger Information Security

Organizations are increasingly reliant on information security to protect their digital assets and ensure business continuity.A robust Information Security Management (ISM) framework is essential to achieve this. Integrating COBIT, the Balanced Scorecard (BSC), and the Systems Security Engineering Capability Maturity Model (SSE-CMM) can provide a comprehensive approach to ISM.
ii. Understanding the Frameworks

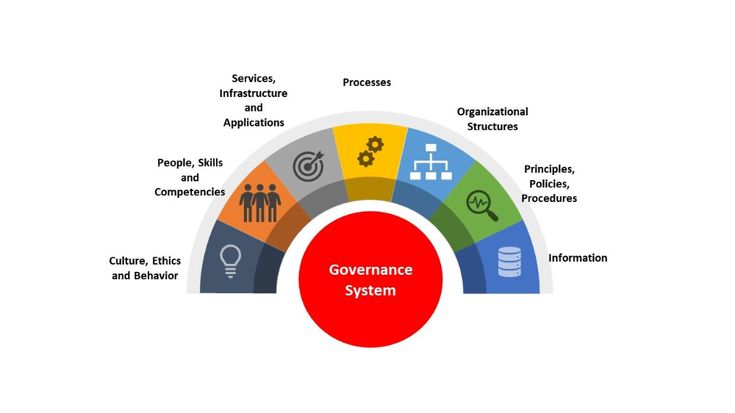
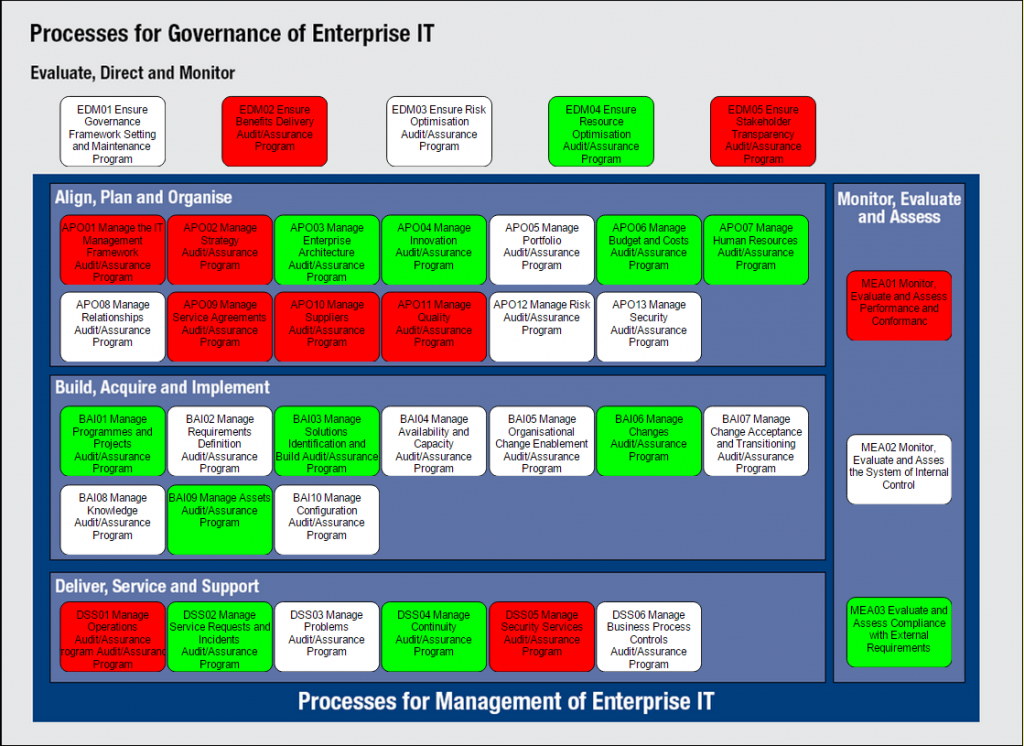
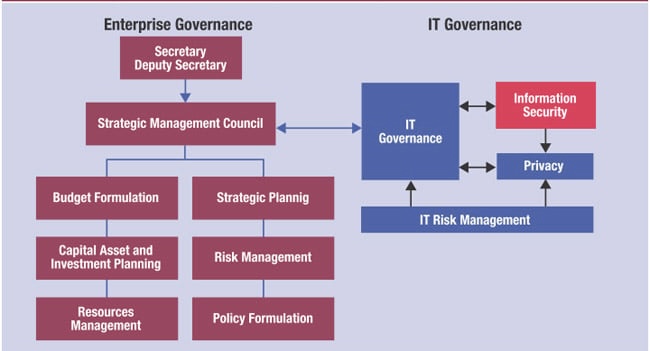
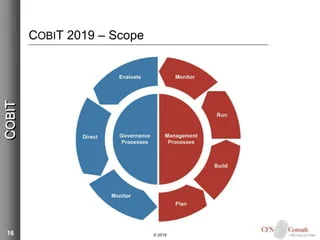
A. COBIT: A Roadmap for IT Governance
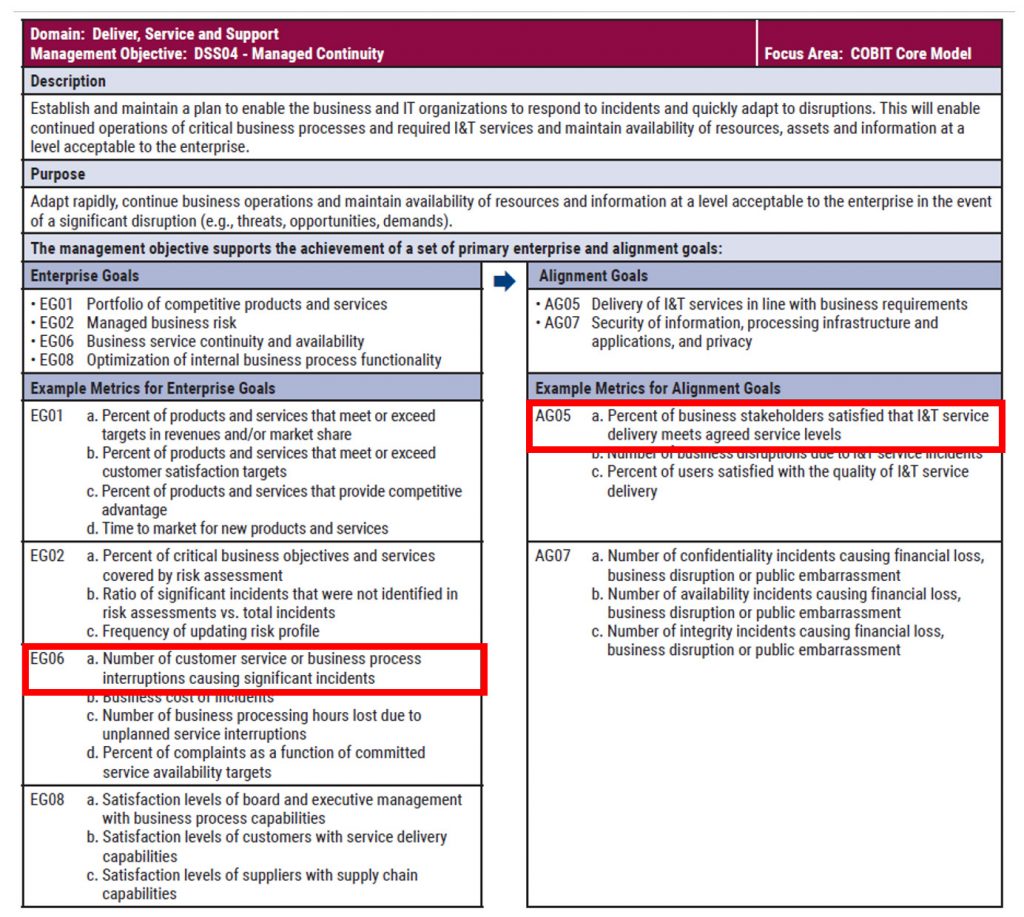
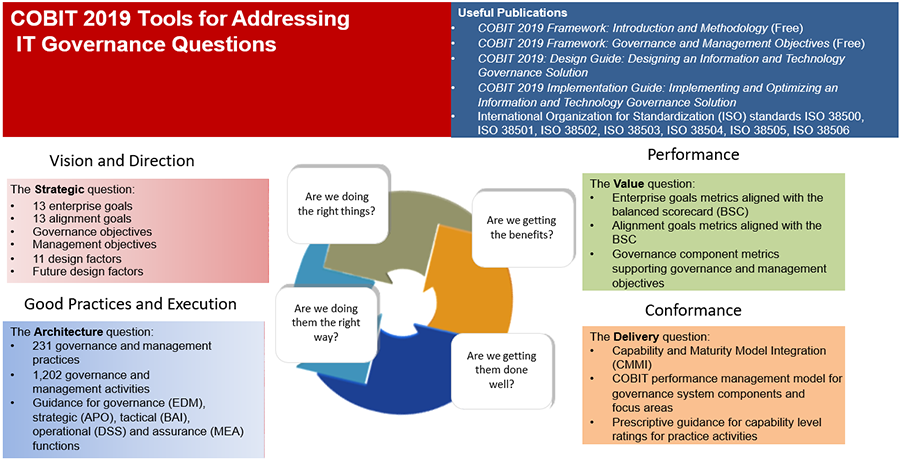
COBIT is a comprehensive framework for the governance and management of enterprise IT.
It provides a globally accepted set of practices, analytical tools, and models that ensure IT is working effectively to support business goals and objectives. COBIT’s principles and practices are instrumental in identifying the critical aspects of information security that need governance and management, including risk management, regulatory compliance, and optimization of IT resources.
It outlines key control objectives across various IT processes, ensuring alignment with business goals.
Key benefits of COBIT in ISM include:
o Alignment with Business Goals: Ensures IT initiatives are directly supporting business objectives.
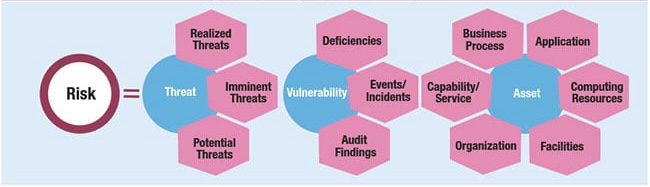
o Comprehensive Risk Management: Identifies and manages IT-related risks effectively.
o Performance Measurement: Offers metrics and maturity models to gauge the effectiveness of IT governance.
B. Balanced Scorecard: Aligning Security with Strategy
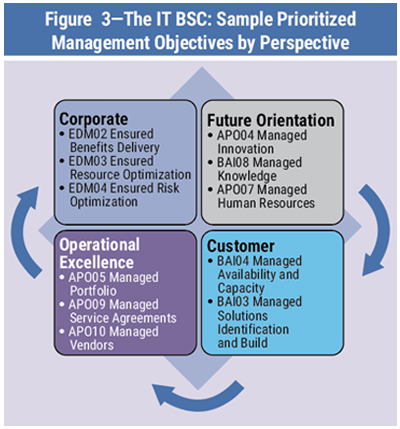
The Balanced Scorecard (BSC) translates strategy into measurable objectives and metrics. By incorporating security objectives into the BSC, organizations can ensure information security aligns with overall business strategy. The Balanced Scorecard is a strategic planning and management system used extensively in business and industry, government, and nonprofit organizations worldwide. It translates an organization’s mission and vision into actual (operational) actions (strategic planning). In the context of ISM, it can be used to link security initiatives to business objectives, monitor performance against strategic targets, and focus on the measures that information security contributes to value creation.
Benefits of using the Balanced Scorecard in ISM include:
o Strategic Alignment: Ensures security measures support overall business strategy.
o Holistic Performance Measurement: Tracks security performance across multiple dimensions.
o Continuous Improvement: Identifies areas for improvement through a structured feedback loop.
C. SSE-CMM: A Path to Continuous Improvement
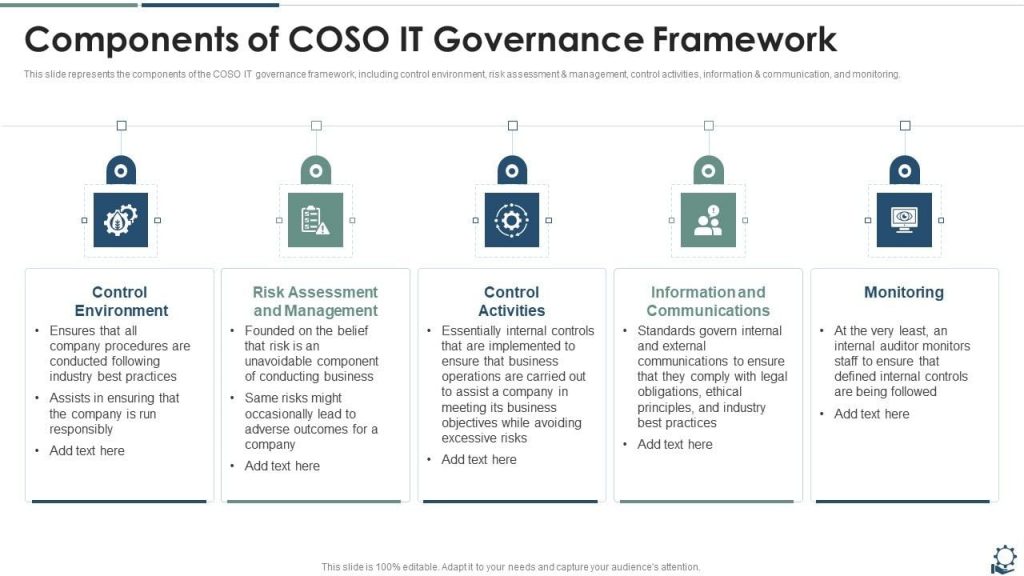
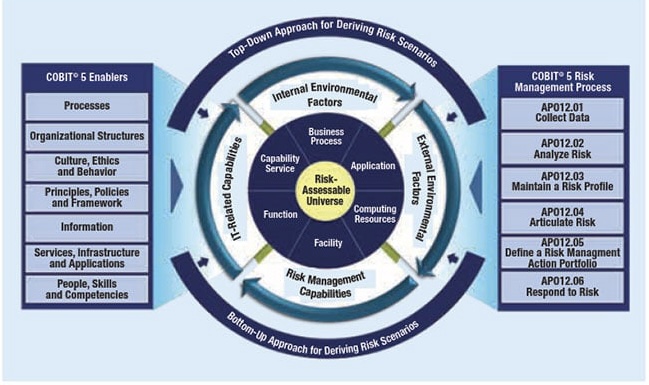
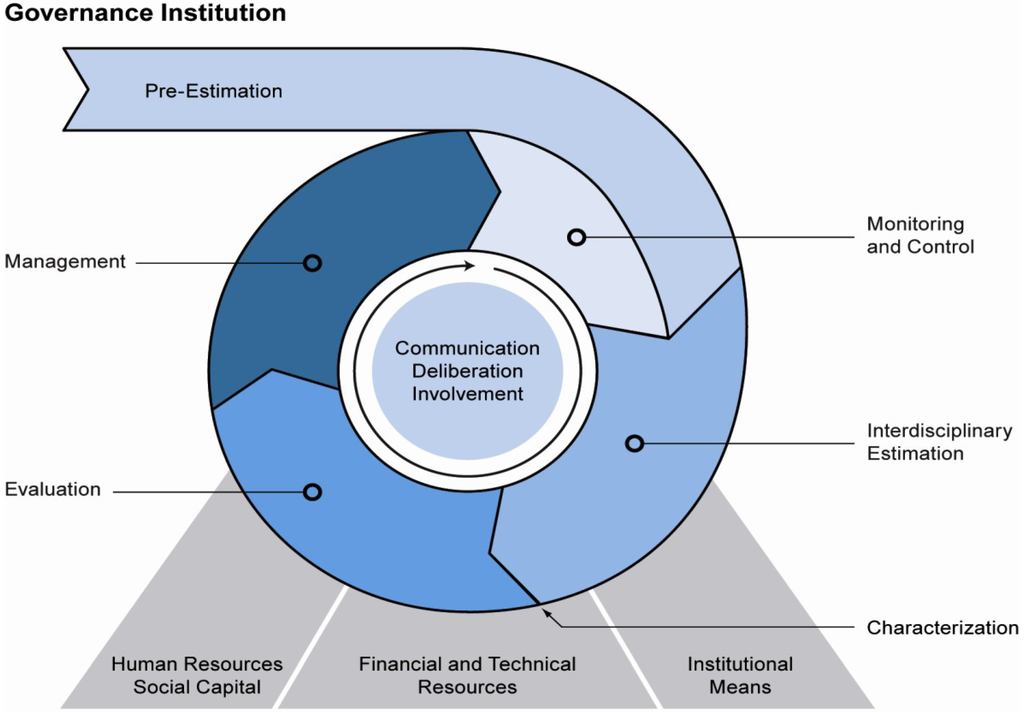
The Systems Security Engineering Capability Maturity Model (SSE-CMM) is a framework used to measure and improve performance in the domain of system security engineering. It provides a means to evaluate and improve security engineering capabilities in a structured and consistent manner. SSE-CMM’s process-oriented approach is vital in ensuring that security considerations are integrated into all phases of system development and lifecycle management.
The primary advantages of integrating SSE-CMM into ISM are:
o Process Improvement: Provides a roadmap for improving security engineering processes.
o Capability Assessment: Helps in assessing the current maturity of security processes.
o Best Practices: Encourages the adoption of industry best practices in security engineering.
ii. Integrating COBIT, Balanced Scorecard, and SSE-CMM

The integration of COBIT, Balanced Scorecard, and SSE-CMM into a strategic ISM framework allows organizations to cover all bases—governance, strategy, and operational effectiveness—in their information security efforts.
A. Strategic Alignment and Governance (COBIT and Balanced Scorecard): This integration ensures that information security strategies are fully aligned with business strategies, as articulated through the Balanced Scorecard approach. This alignment ensures that information security initiatives are always contributing to the achievement of key business objectives.
o Use COBIT to define governance structures and ensure alignment with business objectives.
o Implement the Balanced Scorecard to translate these objectives into measurable security goals across financial, customer, internal processes, and learning and growth perspectives.
B. Governance and Management: COBIT’s framework provides the governance and management backbone, ensuring that information security efforts are in line with organizational governance requirements, including compliance with applicable laws, regulations, and internal policies.
o Alignment of Objectives and Goals: The integration starts with aligning the objectives of COBIT, BSC, and SSE-CMM with the overall business strategy. COBIT ensures IT processes support business goals, the BSC translates these goals into actionable metrics and performance indicators, and SSE-CMM focuses on maturity and capability in security processes.
C. Process Improvement and Maturity Assessment (SSE-CMM and COBIT): COBIT’s process-oriented structure can integrate with SSE-CMM’s security practices, ensuring that each security process is governed and managed in line with COBIT’s guidelines. This creates a coherent governance framework where security processes are regularly assessed and improved based on SSE-CMM’s maturity model.
o Apply SSE-CMM to evaluate and enhance security engineering processes.
o Use COBIT’s maturity models to integrate these improvements into broader IT governance practices.
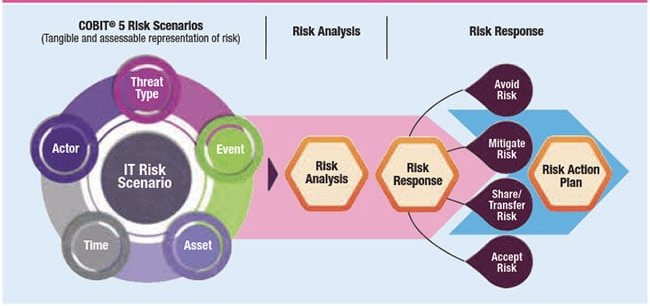
D. Risk Management and Performance Measurement (COBIT and Balanced Scorecard): The integration facilitates the establishment of clear metrics (derived from Balanced Scorecard) for measuring the performance of information security initiatives, ensuring a performance management system that aligns with strategic business goals.
o Utilize COBIT’s risk management processes to identify and mitigate IT risks.
o Incorporate these risks and controls into the Balanced Scorecard to track their impact on overall performance.
E. Comprehensive Metrics and KPIs: Using the BSC’s perspective-based approach, organizations can develop a balanced set of Key Performance Indicators (KPIs) that span financial performance, customer satisfaction, internal processes, and learning and growth. COBIT’s governance and management objectives help identify relevant IT and security metrics, while SSE-CMM provides maturity indicators for these security processes.
F. Operational Excellence: SSE-CMM ensures that security is designed into systems and processes from the ground up, promoting a secure-by-design philosophy that is fundamental for operational excellence in ISM.
G. Measuring and Improving Security Posture: The Balanced Scorecard framework helps in mapping security objectives to business outcomes, enabling organizations to measure the effectiveness of their security strategies. SSE-CMM’s maturity levels can then be used to identify areas for improvement and guide the development of action plans to enhance security posture, which is continually monitored and refined using BSC metrics.
H. Continuous Improvement and Feedback Loop (Balanced Scorecard and SSE-CMM):
o Use the Balanced Scorecard’s structured feedback loop to identify areas for improvement.
o Apply SSE-CMM’s maturity model to systematically enhance these areas, ensuring continuous improvement.
I. Strategic Reporting and Communication: Integrating these frameworks facilitates comprehensive and strategic reporting. COBIT’s structured approach to IT governance and management, combined with BSC’s clear performance metrics, and SSE-CMM’s maturity assessments, provide a rich, multi-faceted view of the organization’s security and IT landscape. This improved visibility supports informed decision-making and strategic communication with stakeholders.
iii. Integration Benefits
Integrating these frameworks can address the limitations of each and create a more holistic ISM approach. COBIT and BSC bridge the gap between business strategy and security controls. SSE-CMM provides a mechanism for continuous improvement, ensuring the ISM framework remains effective.
o Strategic Alignment: Ensures that information security initiatives are aligned with business goals.
o Improved Governance: Integrates comprehensive governance structures, facilitating better oversight and management of IT and security processes.
o Enhanced Performance Measurement: Offers a robust mechanism for measuring performance through a balanced set of metrics.
o Continuous Improvement: Incorporates maturity assessments to guide ongoing improvements in security processes.
iv. Recommendations for Implementation
A. Assess Current Capabilities: Organizations should begin by assessing their current information security capabilities against the requirements and criteria set forth in COBIT, Balanced Scorecard, and SSE-CMM.
B. Strategic Planning: Engage in strategic planning sessions to align information security strategies with business objectives, utilizing the Balanced Scorecard methodology.
C. Framework Implementation: Gradually implement the integrated framework, ensuring that governance structures, processes, and operational practices reflect the integrated principles.
D. Continuous Improvement: Use the performance metrics and maturity models of the integrated framework to continually assess and improve information security management practices.
By following these steps, organizations can make significant strides towards achieving a strategic, integrated approach to information security management, thereby enhancing their resilience against cyber threats while driving business performance.
v. Conclusion
In today’s complex and risk-laden digital environment, adopting a strategic, holistic approach to information security management is paramount. By combining COBIT, BSC, and SSE-CMM, organizations can establish a strategic ISM framework that aligns security with business goals, implements effective controls, and fosters continuous improvement. This integrated approach can significantly enhance an organization’s information security posture. Integration presents a robust framework that aligns information security management with business objectives, promotes effective governance and management practices, and ensures operational excellence.
By leveraging the strengths of each framework, organizations can create a resilient and adaptive ISM strategy capable of addressing the dynamic challenges of today’s digital environment.
vi. Further references
The maturity level assessment of internal controlJKU ePUBhttps://epub.jku.at › download › pdf
Effective Capability and Maturity Assessment Using COBIT 2019ISACAhttps://www.isaca.org
SOC-CMM – Improving security operations globallySOC-CMMhttps://www.soc-cmm.com