
Securities and Exchange Commission (SEC) cybersecurity guidelines are intended to protect the financial industry and investors from the threats of cyber attacks, fraud, and data breaches.
These rules and regulations take various forms and apply to broker-dealers, investment advisers, and investment companies.
i. This is a high-level overview, and specific requirements may differ based on the firm’s operations and the exact rules applicable:
A. Understand the SEC Guidelines and Rules: Familiarize yourself with the SEC’s cybersecurity rules and guidance, including the Cybersecurity Disclosure Guidance, Regulation S-P (Privacy of Consumer Financial Information), and Regulation S-ID (Red Flags Rule), among others.
B. Risk Assessment: Regularly perform thorough risk assessments to identify potential cybersecurity risks within your firm. Understanding the types and sensitivities of data held, assessing the vulnerability of systems, and evaluating defense mechanisms are all essential.
C. Data Protection and Privacy: Implement measures to protect sensitive and non-public information. SEC regulations often involve considerations for the protection of investor data and other confidential information.
D. Cybersecurity Policies and Procedures: Develop comprehensive written policies and procedures designed to ensure the confidentiality, integrity, and availability of sensitive client data. This can encompass data encryption, access controls, network segmentation, and more.
E. Access Controls and Authentication: Implement strong access controls to restrict unauthorized access to systems and data. Utilize multi-factor authentication to enhance the security of user accounts and systems.
F. Encryption: Employ encryption measures for sensitive data in transit and at rest. This helps safeguard information from unauthorized access and ensures the confidentiality of sensitive communications.
G. Incident Response Plan: Adopt a well-structured incident response plan capable of addressing potential cyber incidents effectively. This plan should outline roles and responsibilities during a cyber event, including communication strategies and recovery steps.
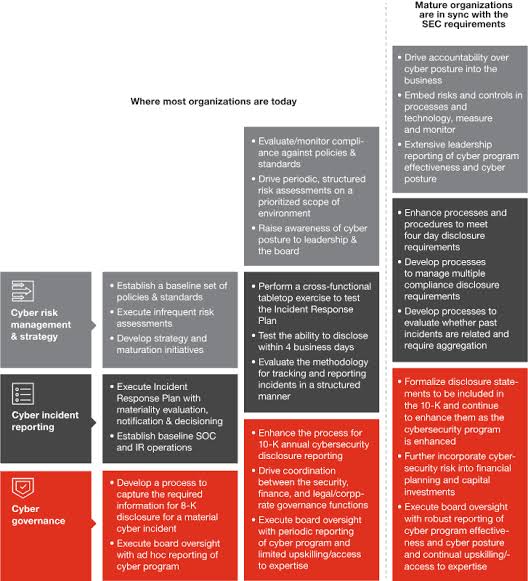
H. Regular Reviews and Updates: The cybersecurity program should not be static. It must be reviewed and updated regularly to adapt to evolving threats and changes in business practices and technologies.
I. Employee Training: All staff should be trained on the firm’s cybersecurity policies and procedures. Training should include how to identify and respond to signs of a potential cyber threat.
J. Vendor Management: Apply due diligence and monitoring for third-party vendors that have access to your network or handle your firm’s data. Contracts should clearly articulate cybersecurity expectations and responsibilities.
K. Cybersecurity Insurance: Consider purchasing insurance that will help mitigate the financial impact of a cyber incident.
L. Continuous Monitoring and Detection: Implement systems and procedures that allow for the continuous monitoring of the security networks and early detection of unauthorized activity.
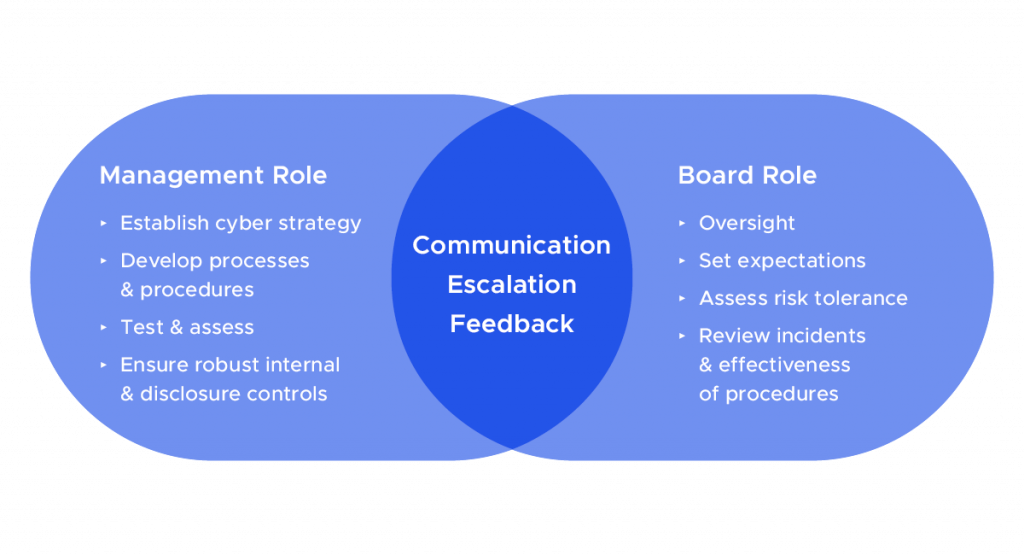
M. Board and Senior Management Engagement: Ensure that the board of directors and senior management are engaged in the cybersecurity program. They should receive regular updates on cyber risks and the effectiveness of the firm’s cyber policies and protocols.
N. Regular Audits and Assessments: Conduct regular cybersecurity audits and assessments to evaluate the effectiveness of security controls. Identify areas for improvement and address any deficiencies promptly.
O. Regulatory Updates and Adaptation: Stay adaptable to changes in SEC cybersecurity regulations. Regularly reassess cybersecurity measures to align with evolving regulatory requirements.
P. Disclosure of Cyber Risks and Incidents: Prepare to disclose material cyber risks and incidents as required by SEC regulations. This includes informing investors about material cybersecurity risks and, in the case of an incident, its potential impact and remediation efforts.
Q. Regulatory Reporting: Be aware of and comply with any SEC reporting requirements related to cybersecurity incidents.
R. Documentation and Recordkeeping: Document efforts to comply with cybersecurity policies and keep records of compliance activities in case of regulatory audits or investigations.
ii. Here’s how the SEC Cybersecurity Rules apply to different entities:

A. For Public Companies:
o Disclosure requirements: Companies must disclose material cybersecurity incidents within four business days, including details like the nature, scope, timing, and potential impact.
o Cybersecurity risk management: Companies must describe their cybersecurity risk management program, including governance, strategies, and incident response plans, in their annual 10-K filings.
o Board oversight: The Board of Directors should actively oversee cybersecurity risks and ensure appropriate resources are allocated for managing them.
B. For Public Companies and Private Foreign Issuers:

o Vulnerability assessments and penetration testing: These should be conducted regularly to identify and address potential security weaknesses.
o Security awareness training: Employees should be trained on cybersecurity best practices to prevent phishing attacks and other threats.
o Incident response planning and testing: Companies should have a documented plan for responding to cybersecurity incidents and test it regularly.
iii. Additional Resources:

o SEC Cybersecurity Rules website: [https://www.sec.gov/corpfin/secg-cybersecurity](https://www.sec.gov/corpfin/secg-cybersecurity)
o PwC SEC Cybersecurity Rules Guide: [https://www.pwc.com/us/en/ghosts/viewpoint/sec-cybersecurity-disclosure-rules.html](https://www.pwc.com/us/en/ghosts/viewpoint/sec-cybersecurity-disclosure-rules.html)
o CyberSaint SEC Cybersecurity Compliance Guide: [https://www.cybersaint.io/](https://www.cybersaint.io/)
Ultimately, ensuring compliance with SEC cybersecurity guidelines involves a comprehensive, multi-faceted approach which should be customized to suit the needs and circumstances of each organization.
Remember that while these steps provide a foundation, compliance requires a detailed understanding of both the current SEC rules and any relevant state, federal, and international cybersecurity laws.
Specific SEC cybersecurity rules may be subject to change, and it’s crucial to consult with legal and compliance experts to ensure accurate and up-to-date adherence to regulatory requirements.
Regularly review the SEC’s official guidance and engage with legal professionals who specialize in securities regulation and cybersecurity compliance.
https://www.sec.gov/news/press-release/2023-139
https://www.auditboard.com/blog/sec-cybersecurity-rules/
https://www.ey.com/en_us/cybersecurity/new-sec-cybersecurity-rules-require-integrated-approach
https://dart.deloitte.com/USDART/home/publications/deloitte/heads-up/2023/sec-rule-cyber-disclosures
