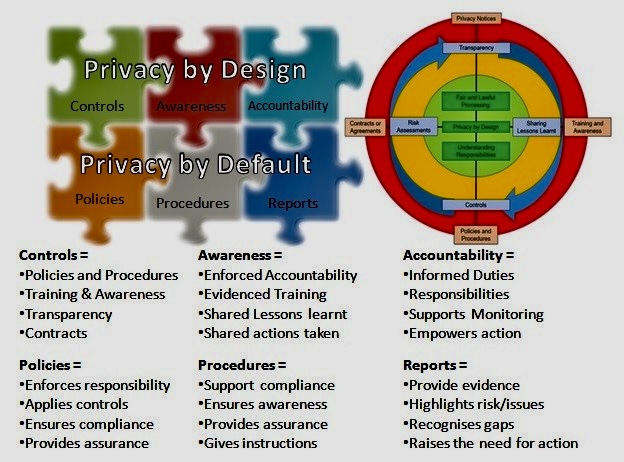
Deming’s Principles: Strengthening Cybersecurity in an Evolving Landscape
In an era dominated by digital connectivity, the significance of cybersecurity has never been more paramount. As organizations grapple with the ever-evolving threat landscape, the principles of W. Edwards Deming, renowned for his contributions to quality management, find resonance in fortifying the defenses of the digital realm.
i. Here’s how Deming’s philosophy can reshape our approach to defending against cyber threats:
A. Shifting the Mindset:
o From blame to systems: Deming argued that blaming individuals for quality issues ignores the flaws within the system itself. Similarly, in cybersecurity, focusing on individual errors overlooks systemic vulnerabilities in software, communication, and organizational structure. Instead, Deming encourages analyzing and improving the systems that create these vulnerabilities.
o From fear to continuous improvement: Instead of panicking after each attack, Deming proposes constant learning and adaptation. This means embracing experimentation, data-driven decision making, and a culture of open communication, even when things go wrong. By viewing breaches as opportunities to learn and strengthen defenses, organizations can become more resilient to future attacks.
ii. Deming’s 14 Points for Transformation:
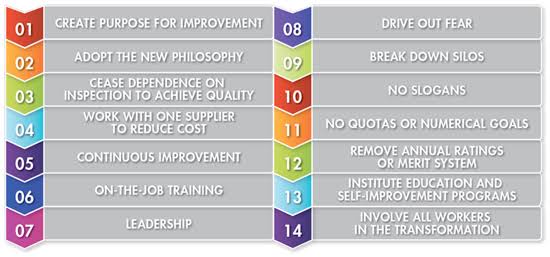
These principles, applied to cybersecurity, can provide a roadmap for building a more robust and proactive defense:
o Point 1: Create Constancy of Purpose: Establish a clear, long-term vision for cybersecurity, prioritizing risk management and prevention over reactive measures.
o Point 2: Learn from New Knowledge: Continuously learn from new vulnerabilities, attack trends, and emerging technologies, adapting defenses accordingly.
o Point 3: Don’t Depend on Mass Inspection: Relying solely on automated tools can miss subtle threats. Encourage vigilance and reporting from all employees to create a human layer of defense.
o Point 4: Stop End-of-Pipe Inspection: Don’t just fix breaches after they happen. Focus on building secure software, systems, and processes from the ground up.
o Point 5: Optimize for the System, not Short-Term Profits: Prioritize long-term security over short-term gains that might compromise systems.
o Point 6: Institute Training On the Job: Continuously train and educate employees on cybersecurity best practices to foster awareness and vigilance.
o Point 7: Drive Out Fear: Create a culture of open communication and trust, where employees feel empowered to report issues without fear of blame.
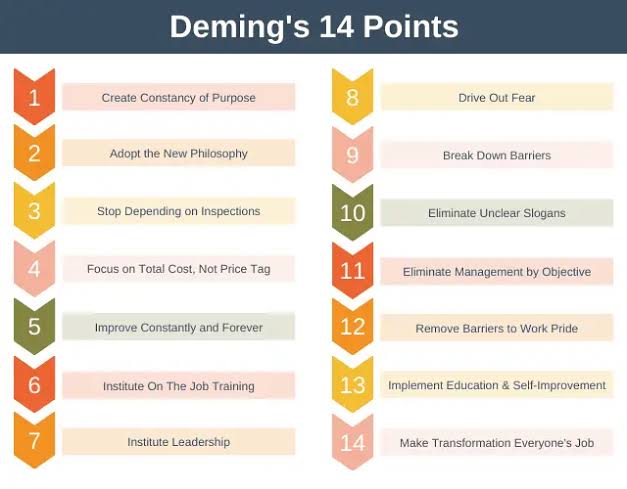
o Point 8: Break Down Barriers: Eliminate silos and foster collaboration between IT, security teams, and other departments to develop holistic security strategies.
o Point 9: Eliminate Slogans, Exhortations, and Targets: Deming warns against empty slogans and unrealistic goals. Focus on measurable, data-driven improvements.
o Point 10: Eliminate Management by Numbers, Substitute Leadership: Leaders should inspire and guide a culture of security, not just enforce metrics.
o Point 11: Work Continuously on the Improvement of Processes: Regularly assess and improve security processes, adapting to changing threats and technologies.
o Point 12: Bring Everyone in the Company to Work for the Transformation: Cybersecurity is not just for IT – everyone in the organization plays a role in defense.
o Point 13: The Transformation is Every Person’s Job: Foster a sense of ownership and responsibility for security among all employees.
o Point 14: It’s Never Late to Start: Implementing Deming’s principles is a continuous journey, not a one-time effort. Start small, learn, and adapt as you go.
iii. How the application of Deming’s principles could benefit the field of cybersecurity
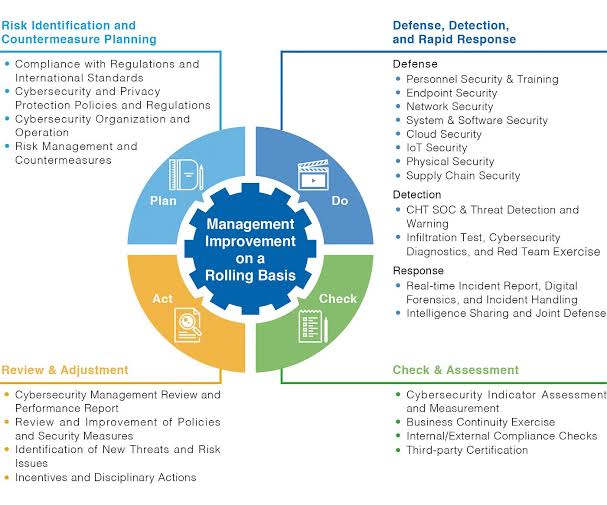
A. Proactive Approach:
Deming’s philosophy encourages a proactive stance towards quality management. Similarly, in cybersecurity, a proactive approach is vital. Instead of merely reacting to threats, organizations must anticipate and prevent potential security breaches. Regular risk assessments, threat modeling, and vulnerability assessments align with Deming’s emphasis on identifying issues before they escalate.
B. Continuous Improvement:
The concept of continuous improvement is at the core of Deming’s teachings. Applied to cybersecurity, this means ongoing refinement of security measures. Regularly updating and upgrading systems, implementing the latest security patches, and fostering a culture of continuous learning among cybersecurity professionals are key components of this principle.
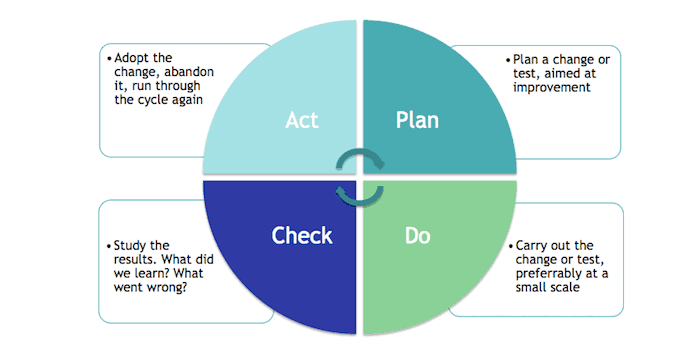
C. System Thinking:
Deming advocated for understanding processes as interconnected systems. In cybersecurity, this translates to comprehending the holistic nature of security. A breach in one area can affect the entire system. Implementing measures like defense-in-depth strategies, where multiple layers of security are deployed, aligns with Deming’s system-thinking approach.
D. Collaboration and Communication:
Effective communication and collaboration are cornerstones of Deming’s principles. In the context of cybersecurity, this means breaking down silos between different departments. A collaborative approach ensures that security measures are integrated seamlessly into all aspects of an organization, fostering a united front against cyber threats.
E. Data-Driven Decision Making:
Deming emphasized the importance of data in decision-making processes. In cybersecurity, data-driven insights are crucial for understanding emerging threats, monitoring security metrics, and making informed decisions. Utilizing analytics tools and leveraging threat intelligence contribute to a proactive and data-informed cybersecurity strategy.
F. Employee Involvement:
Deming stressed the involvement of all employees in quality improvement efforts. In the cybersecurity landscape, creating a culture of security awareness among all staff members is essential. Training programs, simulated phishing exercises, and clear communication about security policies empower employees to become active participants in the organization’s defense against cyber threats.
In the context of cybersecurity, Deming’s principles encourage a holistic and integrated approach, promoting continuous improvement and the important role of human factors, not just the technical aspects.
Adopting these principles can lead organizations to develop more resilient defenses against cyber threats and build a culture that values quality and security in all aspects of their digital operations.
https://www.csoonline.com/article/552083/cybersecurity-lessons-from-w-edwards-deming.html
https://www.imf.org/-/media/Files/Publications/DP/2019/English/CRSEA.ashx