
Establishing Resilience Against Cyber Threats
Building resilience against cyber threats is not just an IT concern; it requires the organization as a whole to participate actively.
Such resilience means implementing a comprehensive approach that combines IT solutions, policy, education, and awareness.
i. Building resilience against these threats becomes crucial for individuals, organizations, and even entire nations.

Here are some key steps to consider:
A. Understand the Landscape:
o Identify potential threats: Familiarize yourself with the different types of cyberattacks, vulnerabilities they exploit, and potential consequences. Analyze your specific environment and its unique risks.
o Know your assets: Inventory your devices, networks, data, and online presences. Classify them based on sensitivity and criticality to prioritize protection efforts.
B. Fortify Your Defenses:
o Implement strong security measures: Install antivirus software, firewalls, and intrusion detection/prevention systems. Maintain updated software and operating systems to patch vulnerabilities.
o Practice good password hygiene: Use strong, unique passwords for each account and enable multi-factor authentication wherever possible.
o Secure your network: Encrypt sensitive data, segment your network to limit potential damage, and use secure protocols for communication.

C. Prepare for the Inevitable:
o Develop an incident response plan: Define roles, responsibilities, and communication protocols in case of a cyberattack. Practice your plan regularly and test its effectiveness.
o Back up your data regularly: Maintain secure backups of your data offline and off-site to ensure rapid recovery in case of an attack or technical failure.
o Implement disaster recovery procedures: Have a plan for resuming operations quickly and minimizing disruptions in case of a cyberattack or other incident.
D. Build a Culture of Security:
o Train your people: Educate your employees, family members, and anyone involved in your systems about cyber threats and best practices for staying safe online.
o Foster a culture of awareness: Encourage open communication about security concerns and suspicious activity. Make reporting these issues easy and accessible.
o Embrace continuous improvement: Keep up-to-date on the latest threats and vulnerabilities, and continually update your security measures and practices.
E. Seek Outside Help:
o Partner with cybersecurity professionals: Utilize experts to audit your security posture, conduct penetration testing, and provide ongoing guidance.
o Stay informed: Follow reputable cybersecurity news sources and alerts to stay aware of emerging threats and vulnerabilities.
o Share information: Collaborate with other individuals and organizations to share best practices and intelligence about cyber threats.
ii. In a world where cyber threats are an ever-present risk, here are some essential steps that organizations can follow:
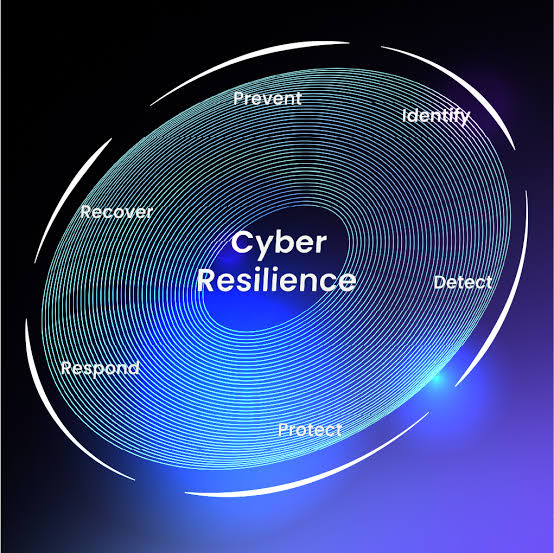
A. Risk Assessment: The first step towards building resilience is identifying potential vulnerabilities within the system. Regularly conducting risk assessments helps in highlighting areas of weakness and loopholes within the systems that may be exploited by hackers.
B. Develop a Cybersecurity Framework: Leaning on frameworks such as those developed by the National Institute of Standards and Technology (NIST), an organization can develop its internal guidelines. The framework should involve identifying existing security measures, implementing protective safeguards, detecting anomalies, responding to incidents, and a plan for recovery post-incident.
C. Implement Robust Security Measures: Utilize the latest cybersecurity tools, such as state-of-the-art firewalls, intrusion detection systems, antivirus software, and encryption methods for data protection. Monitor all device connections and ensure IoT devices are secured. Regularly update and patch software and systems to reduce vulnerabilities.
D. Endpoint Security: Implement robust endpoint protection measures, including antivirus software, intrusion detection systems, and regular software updates to secure devices from potential threats.
E. Network Security: Establish a strong network security posture by using firewalls, intrusion prevention systems (IPS), and regularly monitoring network traffic for suspicious activities.
F. Employee Training and Awareness: Cybersecurity education and awareness should be a part of all employees’ training, as human error often leads to security breaches. Regular training sessions on identifying phishing attempts, proper password practices, and safe internet usage can significantly improve the organization’s cyber resilience.

G. Multi-Factor Authentication: Implement multi-factor authentication for all internal systems and processes, significantly reducing the chance of unauthorized access to sensitive information.
H. Data Encryption: Implement end-to-end encryption for sensitive data to protect it during transmission and storage. This ensures that even if unauthorized access occurs, the data remains unreadable.
I. Implement Strong Cyber Hygiene Practices:
o Regularly update and patch systems and software to eliminate vulnerabilities.
o Enforce strong password policies and use multi-factor authentication.
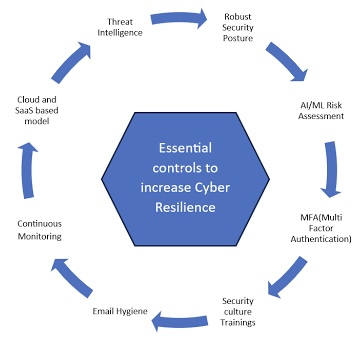
J. Secure Configuration:
o Harden systems by configuring security settings appropriately.
o Limit the number of privileged accounts and monitor their activity.
K. Incident Response Plan: Have a clear incident response plan in place. In the event of a breach, time is of the essence to minimize damage. A well-prepared plan would include roles and responsibilities, communication plan, and recovery steps.
L. Data Backups and Recovery Plan: Regularly back up critical data in multiple locations, including offline storage. In event of a breach or ransomware attack, backups will help the organization recover without paying ransom or losing vital data.

M. Cyber Insurances: Consider adopting cyber insurance policies. While these don’t prevent attacks, they can certainly mitigate financial losses in case of a significant cybersecurity incident.
N. Vendor Security Assessment: Assess the security measures of third-party vendors and partners. Ensure they adhere to high cybersecurity standards, as weaknesses in their systems can impact your organization.
O. Continuous Monitoring: Implement continuous monitoring of your IT infrastructure and network. This involves real-time analysis of security events to detect and respond to threats promptly.
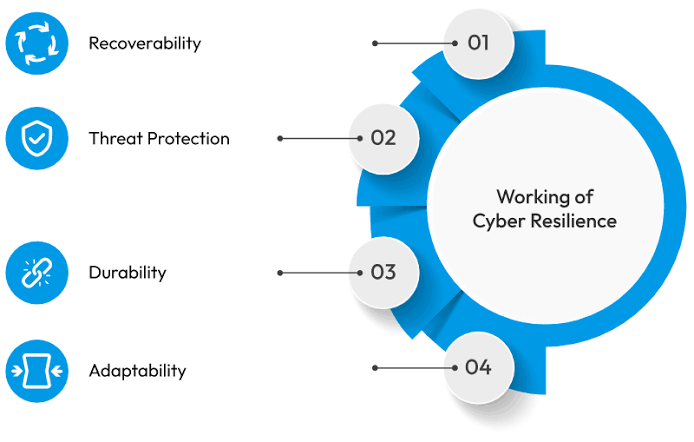
P. Governance and Compliance: Establish strong governance policies and ensure compliance with industry regulations and standards. This provides a structured framework for maintaining a secure environment.
Q. Business Continuity and Disaster Recovery:
o Create and test a business continuity plan that includes strategies for dealing with cyber incidents.
o Set up redundant systems and data backups to maintain operations during and after an attack.
R. Regular Audits and Tests: Regular cybersecurity audits and penetration tests help identify weaknesses in the existing systems and ensure the organization’s defenses can withstand attempted breaches.
S. Threat Intelligence: Stay informed about emerging cyber threats and vulnerabilities by leveraging threat intelligence sources. This knowledge helps in proactively adjusting security measures.
T. Collaboration and Information Sharing: Collaborate with industry peers and participate in information-sharing initiatives. Understanding the threat landscape and learning from others’ experiences can enhance your resilience.
U. Stay Updated: Cyber threats are constantly evolving. Keep abreast of the latest developments, threat vectors, and protective measures.
iii. Conclusion
Building resilience against cyber threats is not a one-time effort, but rather an ongoing process. By embracing these steps and fostering a proactive approach, you can significantly reduce your risk, minimize potential damage, and create a more secure environment for yourself and those around you.
In conclusion, building resilience against cyber threats requires a holistic approach including technology, people and processes working together to anticipate, prevent, detect and respond to cyber threats.
Additionally, adopting a framework like NIST Cybersecurity Framework can help in organizing and prioritizing the efforts to build resilience against cyber threats. It’s important to stay informed about emerging threats and continuously evolve your cybersecurity practices to address new challenges.
iv. Further references
10 Tips for Creating a Cyber Resilience Strategy – CybeReady
InformationWeekhttps://www.informationweek.com › …How to Build True Cyber Resilience
Forbeswww.forbes.comFrom Awareness To Resilience: The Evolution Of People-Centric Cybersecurity
