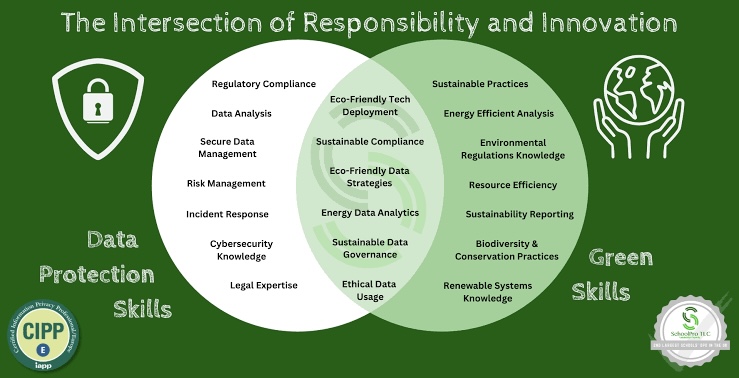
Safeguarding Sustainability: How Data Privacy may contribute in Environmental Initiatives
i. The landscape of environmental efforts
In the ever-evolving landscape of environmental initiatives, the convergence of sustainability and data privacy emerges as a crucial consideration. As societies worldwide intensify efforts to mitigate climate change and promote ecological conservation, the utilization of data plays an increasingly pivotal role.
However, as organizations harness data to drive sustainable practices, the imperative to safeguard individual privacy becomes equally paramount. Balancing the imperatives of sustainability and data privacy presents a complex challenge, but one that is essential for building trust, fostering innovation, and achieving lasting environmental impact.
Data lies at the heart of modern sustainability initiatives, enabling organizations to monitor, analyze, and optimize their environmental footprint. From tracking carbon emissions to optimizing energy consumption, data-driven insights empower businesses, governments, and NGOs to make informed decisions that drive positive environmental outcomes. Whether through remote sensing technologies, IoT devices, or satellite imagery, the proliferation of data sources offers unprecedented opportunities to address pressing environmental challenges.

However, as data becomes increasingly intertwined with sustainability efforts, concerns over privacy and security escalate. The collection, storage, and utilization of personal and environmental data raise ethical questions regarding consent, transparency, and accountability. Individuals rightly expect their personal information to be handled responsibly, with stringent safeguards in place to prevent misuse or unauthorized access. Likewise, communities and ecosystems subject to environmental monitoring deserve assurances that their data will be utilized ethically and for the collective benefit.
Addressing these dual imperatives requires a multifaceted approach that integrates data privacy considerations into the fabric of environmental initiatives.
ii. The Nexus Between Environmental Sustainability and Data Privacy

Environmental initiatives often rely on extensive data collection to monitor pollution levels, track wildlife, or even assess the impact of climate change. This data collection, while invaluable for research and policy-making, involves the acquisition of vast amounts of information, some of which can be sensitive or personally identifiable. The nexus between sustainability and privacy lies in the responsible handling of this data to prevent misuse, ensuring that initiatives intended to protect the environment do not inadvertently compromise individual privacy.
iii. The Importance of Data Privacy in Environmental Initiatives
A. Trust and Participation: Public trust is paramount in environmental initiatives. When individuals trust that their data is being used responsibly and with respect for their privacy, they are more likely to participate in and support sustainability programs, such as smart energy grids or waste reduction apps. Ensuring data privacy is thus essential not just for compliance with regulations but for fostering a culture of trust and collaboration in environmental efforts.
B. Ethical Use of Data: As data becomes a key asset in the fight against environmental degradation, the ethical implications of its use come under scrutiny. Organizations must navigate the fine line between leveraging data for environmental benefits and respecting individuals’ rights to privacy. This includes being transparent about data collection methods, the purpose of data use, and the measures in place to protect personal information.
C. Preventing Misuse of Data: In the age of digital technology, data collected for environmental monitoring could be repurposed for other, less benign uses. Strong privacy protections help prevent such misuse, ensuring that data collected for conservation efforts, for example, isn’t later used for commercial exploitation of natural resources.
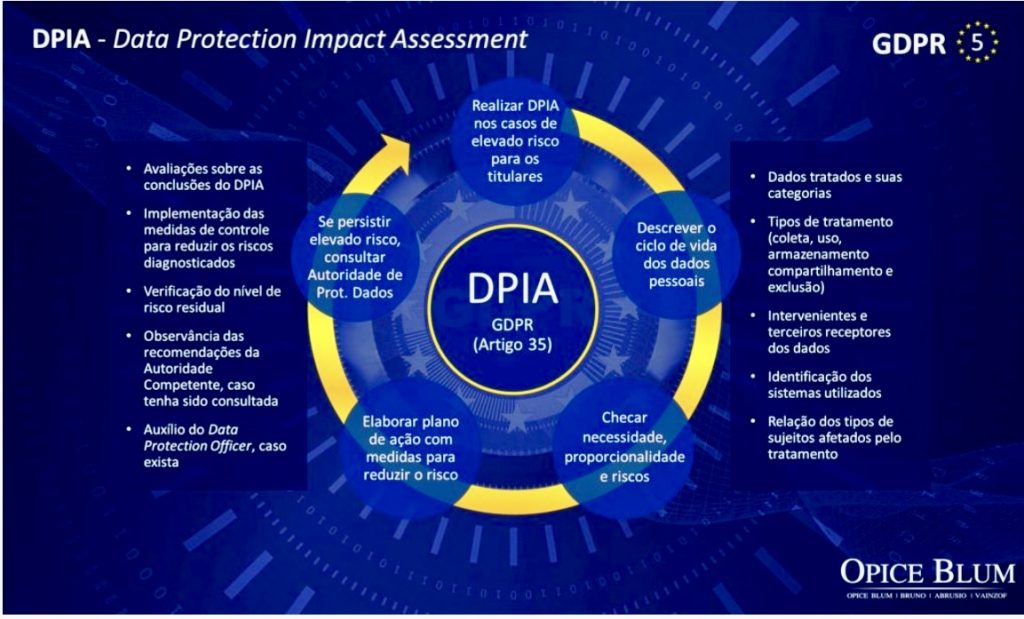
D. Regulatory Compliance: With the advent of stringent data protection regulations like the General Data Protection Regulation (GDPR) in Europe and the California Consumer Privacy Act (CCPA), environmental initiatives must ensure compliance to avoid legal and financial repercussions. These regulations mandate clear consent mechanisms, data minimization, and strong data security practices, directly impacting how organizations collect and utilize data in their sustainability projects.
E. Facilitating Global Collaboration: The fight against environmental challenges is a global effort. Data privacy norms that respect international standards can facilitate the sharing and collaboration between countries and organizations, enabling more effective and unified global responses to environmental crises.
iv. Balancing Data Utilization with Privacy

Achieving a balance between leveraging data for sustainability and ensuring privacy requires a multifaceted approach:
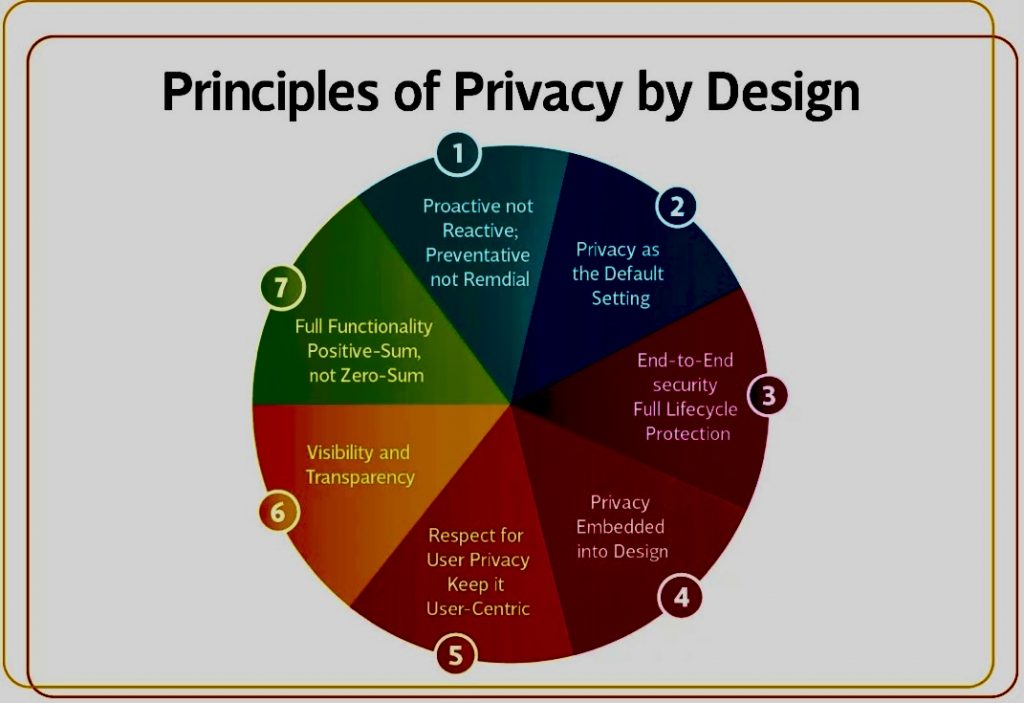
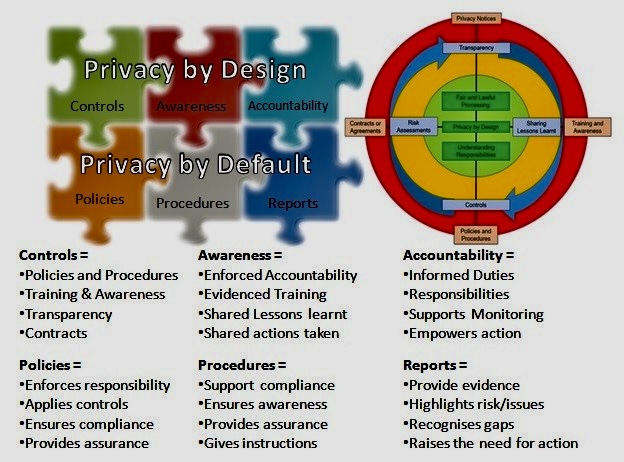
A. Privacy by Design: Integrating privacy considerations into the development phase of environmental technology projects ensures that data protection is a foundational element rather than an afterthought. This approach encompasses data minimization, encryption, and anonymization techniques to protect individuals’ information while still enabling valuable environmental insights.
B. Transparent Communication: Organizations must be transparent about their data practices, clearly explaining to users how their data is collected, used, and protected. This transparency builds trust and empowers individuals to make informed choices about their participation in environmental programs.
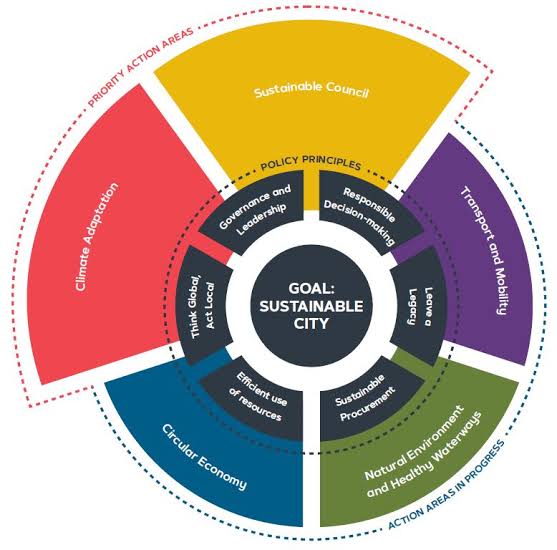
C. Partnership and Collaboration: By collaborating with privacy experts, regulators, and the public, organizations can develop and refine best practices for data privacy in environmental initiatives. This collaborative approach helps align sustainability efforts with evolving privacy norms and expectations.
D. Secure Data Storage and Transfer: Implementing advanced cybersecurity measures to protect data against breaches is critical. This includes secure storage solutions and encrypted data transfer protocols, especially when dealing with cross-border data sharing.
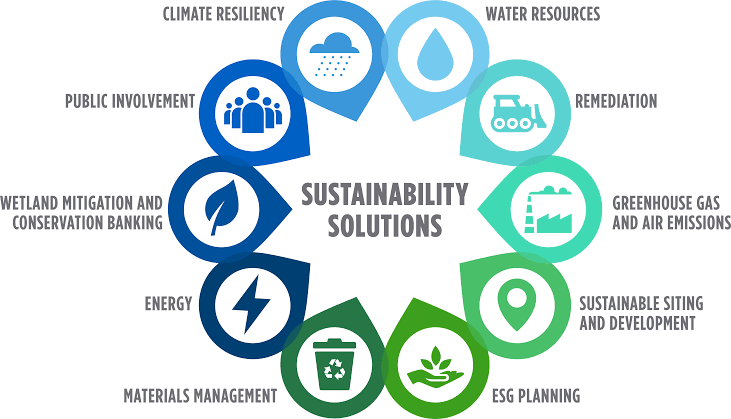
E. Compliance with Global Standards: Adhering to international data privacy laws and frameworks, such as the General Data Protection Regulation (GDPR) in Europe, ensures that initiatives maintain high standards of data protection, facilitating international cooperation.
F. Regular Audits and Impact Assessments: Regularly auditing data practices and conducting impact assessments can help identify potential privacy risks and ensure continuous improvement of data management practices.
v. Conclusion

In conclusion, safeguarding sustainability requires a holistic approach that integrates data privacy principles into every stage of environmental initiatives.
Transparency, accountability, and collaboration are essential in balancing the imperatives of sustainability and privacy, ensuring that data-driven efforts yield positive environmental outcomes while upholding individual rights and societal values.
As we navigate the complex challenges of the 21st century, the integration of sustainability and data privacy emerges as a cornerstone of responsible innovation and inclusive progress.
vi. Further references
Bird & Birdhttps://www.twobirds.com › …PDFDATA PROTECTION AS PART OF AN ENVIRONMENTAL, SOCIAL AND …
Skillcasthttps://www.skillcast.com › blogUnderstanding Data Security & Privacy in ESG
LinkedInhttps://www.linkedin.com › pulseSafeguarding Sustainability: The Role of Data …
KPMGhttps://assets.kpmg.com › pdfPDFCybersecurity in ESG
PwC Nederlandhttps://www.pwc.nl › topics › how…How privacy contributes to your ESG ambitions – Blogs