Exploring the Critical Importance of Data Engineers in Securing Information
In the data-driven landscape of the modern enterprise, the role of data engineers has expanded from traditional tasks of data processing and management to encompass the crucial area of data security.
Data engineers architect the systems that store, process, and retrieve an organization’s most valuable information assets, making them key players in the protection of data.
Here’s a look at their critical role in ensuring data security:
A. Data Architecture and Design
Data engineers are responsible for designing and implementing the architecture that governs how data is stored, processed, and accessed. A well-designed data architecture forms the foundation for robust security measures. It includes considerations for encryption, access controls, and data lifecycle management, ensuring that security is ingrained in the very structure of the data environment.
B. Data Encryption
Data engineers implement encryption protocols to protect data at rest, in transit, and during processing. Encryption transforms sensitive information into unreadable code without the appropriate decryption key, making it significantly more challenging for unauthorized entities to access or manipulate data. Data engineers choose and implement encryption algorithms suitable for the specific security requirements of their systems.
C. Data Management and Integrity
Maintaining the integrity and quality of data is key to security. Data engineers ensure that the data is accurate, consistent, and reliable, which is critical for security analytics and threat detection.
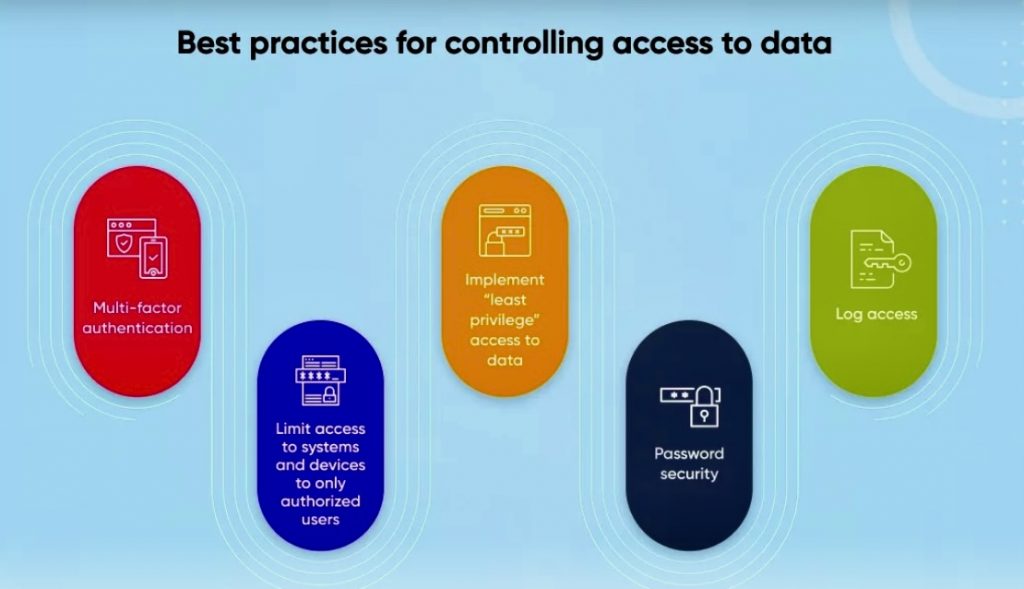
D. Access Controls and Authentication
Controlling who has access to what data is a critical aspect of data security. Data engineers establish access controls and authentication mechanisms to ensure that only authorized personnel can view or manipulate specific datasets. This involves implementing user authentication, role-based access controls, and monitoring tools to track and audit data access activities.
E. Compliance and Regulatory Adherence
With regulations such as GDPR and HIPAA setting stringent requirements for data privacy and security, data engineers play an essential role in ensuring systems comply with legal and industry standards.
F. Data Masking and Anonymization
In scenarios where data needs to be shared for analysis or development, data engineers employ techniques like data masking and anonymization to protect sensitive information. Data masking involves replacing original data with fictional but realistic data, while anonymization removes personally identifiable information, reducing the risk of privacy breaches during collaborative projects.
G. Data Quality and Error Handling
Ensuring data quality is not just about accuracy but also about security. Data engineers implement measures to identify and handle errors, preventing potential vulnerabilities that could be exploited by malicious actors. By maintaining data quality standards, they contribute to a more secure and reliable data ecosystem.
H. Data Lifecycle Management
Data engineers define policies regarding the lifecycle of data which includes safe data retention, archival, and destruction practices, preventing exposure of sensitive information.
I. Collaboration with Cybersecurity Teams
Effective collaboration between data engineers and cybersecurity teams is vital. Data engineers provide insights into the intricacies of the data environment, helping cybersecurity professionals devise targeted security strategies. This collaboration ensures a holistic approach to data security, considering both infrastructure and cybersecurity perspectives.
J. Incident Response and Recovery
Data Backup and Recovery: Data engineers play a crucial role in establishing and maintaining robust data backup and recovery procedures. This ensures that data can be restored quickly and efficiently in case of a security incident or system failure.
Incident Investigation: They collaborate with security teams to investigate data security incidents, analyze logs, and identify the root cause of the problem. This information is vital for learning from the incident and implementing effective preventive measures in the future.

K. Monitoring and Auditing
Data engineers set up monitoring and auditing systems to track data access patterns, system changes, and potential security incidents. These mechanisms allow for the timely detection of anomalies or unauthorized activities, enabling a swift response to mitigate risks and maintain data integrity.
L. Educating Stakeholders
Data engineers educate other team members and stakeholders about best practices for data security. By fostering a culture of security awareness, they contribute to the overall defensive posture of the organization.

M. Continuous Monitoring and Improvement:
The data landscape is continuously changing, with new security threats emerging regularly. Data engineers are responsible for keeping data secure through ongoing monitoring and by updating systems and practices in response to new threats.
Conclusion

In essence, data engineers are the custodians of data security, not just gatekeepers of data flow and functionality. Their role is a blend of technical acumen, an understanding of the evolving threat landscape, and an ability to work collaboratively with cross-functional teams to ensure the comprehensive protection of data assets.
In conclusion, data engineers are the silent guardians of data security, weaving intricate layers of protection into the very fabric of data systems. Their role extends beyond architecture and design to encompass encryption, access controls, monitoring, and collaboration with cybersecurity experts.
Acknowledging and understanding the pivotal role of data engineers is essential for organizations aiming to build and maintain resilient defenses in the face of ever-evolving data security challenges.
Further information
Understanding the Crucial Role of Data Engineers in Data Security – LinkedIn
DataGalaxyhttps://www.datagalaxy.com › blogThe Data Engineer’s role in data governance
iabachttps://iabac.org › blog › the-role-o…The Role of Data Engineers in Ethical Data Practices
LinkedIn · Volmatica5 reactionsUnderstanding Data Engineering in Depth: A Comprehensive Guide
iabachttps://iabac.org › blog › data-engin…Data Engineer Roles and Responsibilities
Atlanhttps://atlan.com › responsibilities-o…13 Key Responsibilities of a Data Engineering Manager