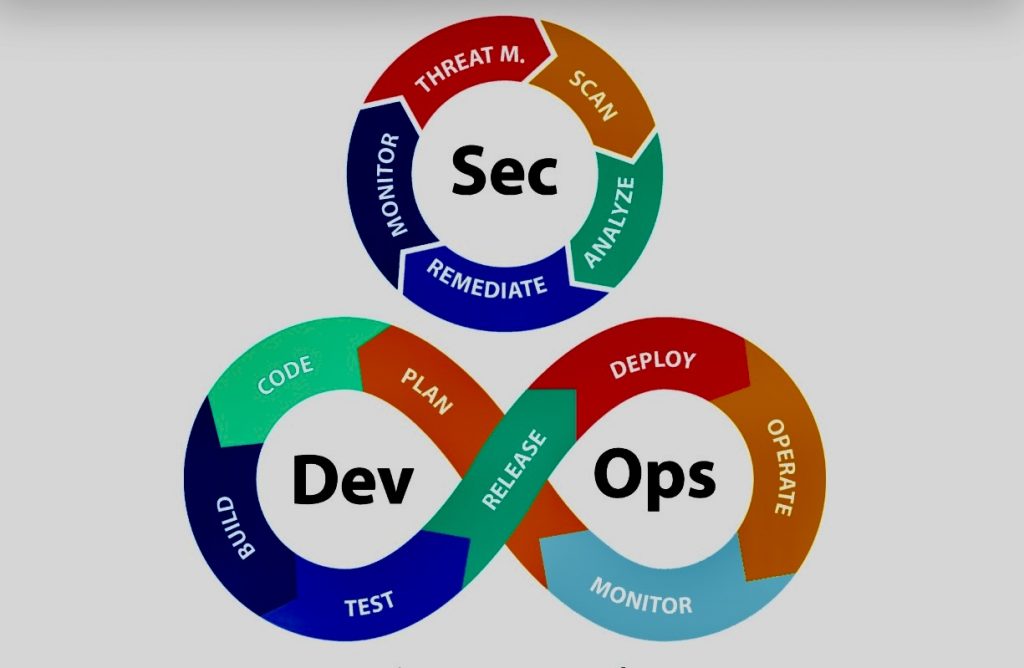
DevSecOps, which integrates security practices within the DevOps process, has gained considerable traction for building a more secure and efficient infrastructure. Here are some top best practices for successful DevSecOps:
A. Shift Security Left: Integrate security testing and controls into the early stages of the SDLC, rather than treating it as an afterthought. This enables early identification and resolution of security vulnerabilities, reducing the risk of costly late-stage rework.
B. Early Integration: Include security considerations from the earliest stages of your DevOps cycle, even starting as early as the design and planning phase.
C. Implement a Security-First Culture: Security should be everyone’s job, not just the security team’s. Encourage a security-conscious culture across all teams involved in the DevSecOps pipeline.
D. Automate Security: Automated security scans and checks should be incorporated into the CI/CD pipeline. Tools can be used for static application security testing (SAST), dynamic application security testing (DAST), and container security.

E. Automate Security Testing and Monitoring: Automate security testing processes throughout the SDLC, including static code analysis, dynamic application security testing (DAST), and software composition analysis (SCA). Continuous monitoring of infrastructure and applications helps detect and respond to security threats promptly.
F. Utilize Infrastructure as Code (IaC): Manage infrastructure using IaC tools, such as Terraform or Ansible, to enforce consistent security configurations and ensure compliance with security policies. IaC also enables automated infrastructure provisioning and deployment, reducing manual errors and improving security posture.
G. Adopt a Continuous Integration (CI) and Continuous Delivery (CD) Pipeline: Implement a CI/CD pipeline to automate the build, test, and deployment process. This streamlines software delivery and ensures that security measures are integrated into each stage.
H. Embrace DevSecOps Collaboration: Foster a collaborative culture between development, security, and operations teams. Encourage communication, shared ownership of security responsibilities, and regular feedback loops to break down silos and promote a unified approach to security.
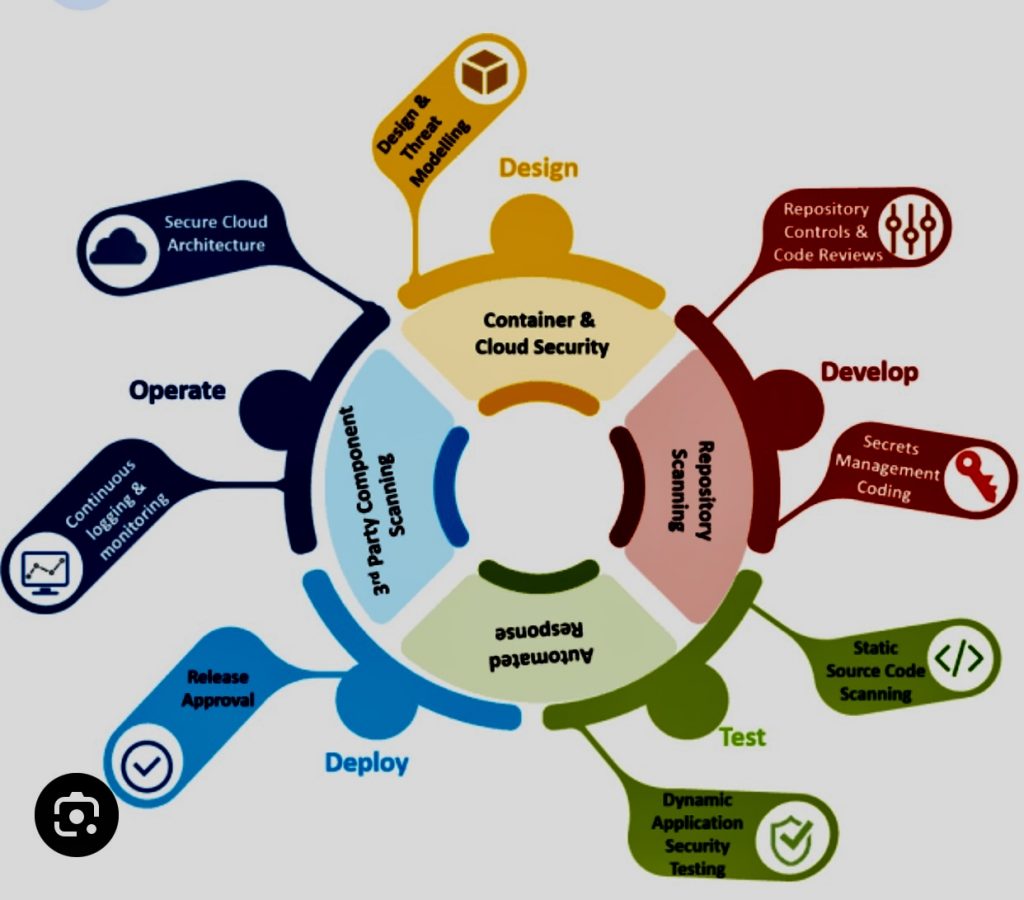
I. Educate and Train Teams: Provide regular security awareness training to all employees, including developers, operations staff, and management. This helps them understand security risks, recognize potential threats, and follow best practices to protect sensitive data.
J. Implement Secure Coding Standards: Establish and enforce secure coding standards and guidelines to prevent common vulnerabilities and promote secure coding practices. This can be done using static code analysis tools and code reviews.
K. Container Security:
o Practice: Implement security measures for containerized environments.
o Benefits: Ensure that containers and orchestration platforms are configured securely, reducing the risk of container-related vulnerabilities.
L. Utilize Vulnerability Management Tools: Implement vulnerability management tools to identify, prioritize, and remediate security vulnerabilities in a timely manner. These tools should integrate with the CI/CD pipeline to automate vulnerability scanning and reporting.
M. Incident Response Plan: Have a clear and well-practiced incident response plan in place. This allows addressing security issues in a timely and coordinated manner if they arise.
N. Adopt Zero Trust Security: Implement Zero Trust principles, which assume no user or device is inherently trustworthy and continuously verify their identity and access privileges before granting access to resources. This approach reduces the risk of unauthorized access and data breaches.
O. Monitor Third-Party Vendors: Establish a robust third-party vendor management program to ensure that vendors adhere to your organization’s security policies and standards. This includes conducting security assessments, requiring vendor compliance with security regulations, and monitoring vendor access to sensitive data.
P. Compliance Management: Maintain clear details about the security and compliance policies that need to be followed. Regulatory compliance should be a foundation of any DevSecOps strategy.
Q. Securing Endpoints: Given the rise of remote working and increased use of mobile devices, it is critical to protect every endpoint that can access the network.
R. Threat Modeling:
o Practice: Conduct threat modeling exercises during the design phase.
o Benefits: Identify and mitigate potential security threats early in the development process, preventing security issues from progressing to later stages.
S. Continuous Feedback Loop:
o Practice: Establish a continuous feedback loop for security improvements.
o Benefits: Gather feedback from incidents, testing, and monitoring to continuously enhance security practices and adapt to emerging threats.
T. Immutable Infrastructure:
o Practice: Embrace immutable infrastructure principles.
o Benefits: Reduce the attack surface by creating and deploying immutable infrastructure, making it more difficult for attackers to exploit vulnerabilities.
U. Multi-Cloud Security Considerations:
o Practice: Address security considerations when deploying applications across multiple cloud environments.
o Benefits: Ensure consistent security measures and compliance across diverse cloud platforms.
V. Audit Trail and Logging:
o Practice: Implement comprehensive logging and maintain audit trails.
o Benefits: Enable effective investigation and analysis of security incidents, facilitating compliance and accountability.
W. Continuous Monitoring: Continuous monitoring and real-time analysis can help detect vulnerabilities and unusual behavior early, allowing teams to respond quickly to potential threats.
Through adopting these DevSecOps best practices, organizations can create a culture of security, enhance collaboration, and build a software development lifecycle that prioritizes the identification and mitigation of security risks.
https://www.practical-devsecops.com/devsecops-best-practices/
https://www.linkedin.com/pulse/best-practices-implementing-devsecops-your-shiju-daniel
https://www.synopsys.com/blogs/software-security/devsecops-best-practices.html
https://developers.redhat.com/articles/2022/06/15/best-practices-successful-devsecops
https://www.dynatrace.com/news/blog/what-is-devsecops/
https://tech-stack.com/blog/integrating-security-in-devops-best-practices-tools-and-challenges/
