Building an Effective Crisis Management Team: Preparing for the Unexpected
In today’s unpredictable world, businesses are constantly exposed to potential crises. These can range from public relations disasters and data breaches to natural disasters and supply chain disruptions. To navigate the formation of an effective crisis management team (CMT) is indispensable.
Having a well-prepared and effective crisis management team in place is crucial to navigating these tumultuous times successfully, and protecting your organization’s reputation, operations, and employees.
i. Understanding the Role of a Crisis Management Team

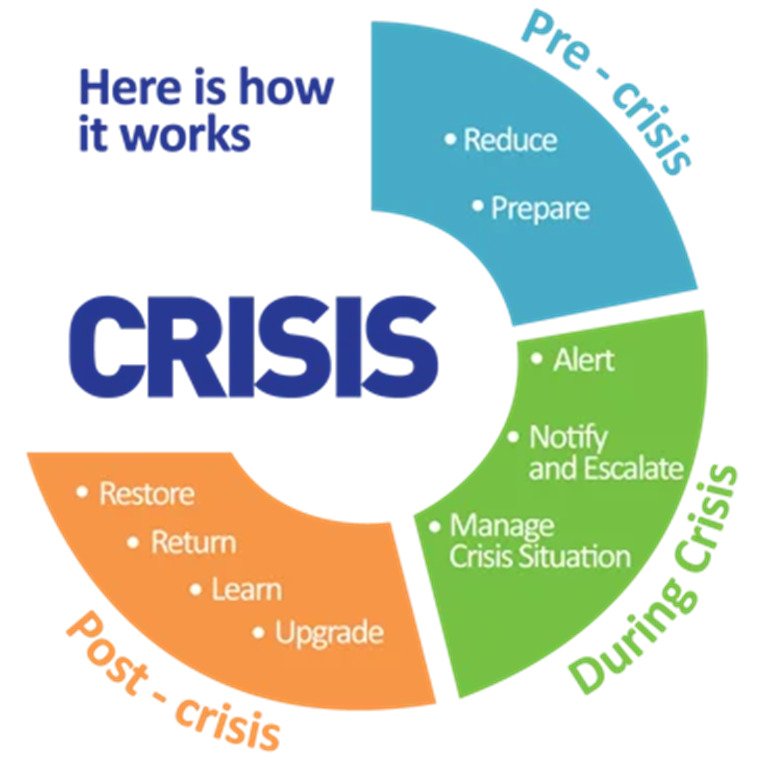
A crisis management team is a group of individuals tasked with preparing for, responding to, and recovering from any emergency or crisis. This team is responsible not just for immediate response, but also for strategic planning to minimize the impact of crises on the organization’s operations, reputation, and stakeholders.
ii. Key Steps to Building an Effective Crisis Management Team
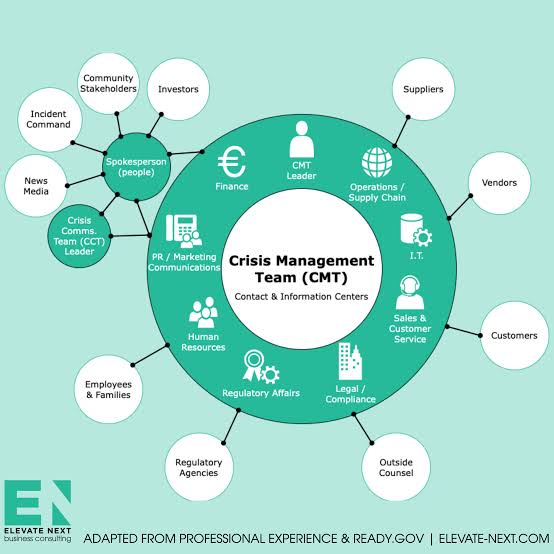
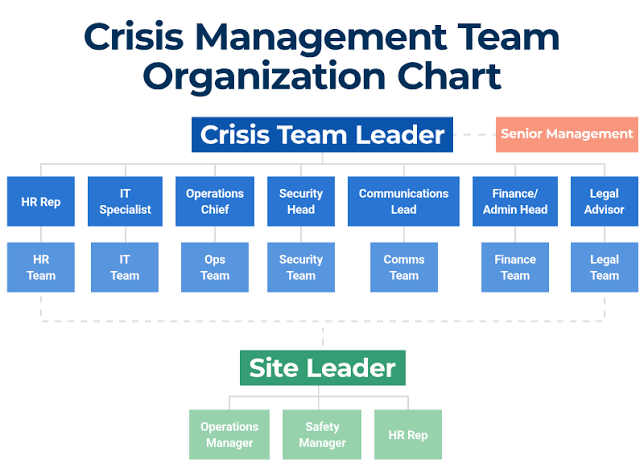
A. Selecting the Right Team Members
The composition of the team is critical. Members should be selected based on their expertise, decision-making abilities, and leadership skills. It’s essential to have a diverse group that includes representatives from various departments (e.g., HR, IT, operations, finance, and legal) to ensure all aspects of the organization are considered in crisis planning and response.
B. Defining Roles and Responsibilities
Clearly defined roles prevent confusion during a crisis. Each member should know their specific responsibilities, how they fit into the larger response effort, and who they report to or collaborate with within the team.
o Team Leader: Appoint a clear leader to guide the team’s overall response and ensure all members are informed and aligned.
o Communication Specialist: Designate a dedicated individual to manage external communications, including media relations and messaging to stakeholders.
o Internal Communications: Assign someone to handle internal communications, keeping employees informed, managing anxiety, and maintaining morale.
o Subject Matter Experts: Identify specific team members with expertise relevant to the potential crisis scenarios, who can offer specific guidance and support.
C. Training and Preparedness
Training is a cornerstone of an effective CMT. Regular drills and simulation exercises should be conducted to prepare the team for various crisis scenarios. This not only helps in refining response strategies but also in identifying potential gaps in preparedness. Continuous education on crisis management best practices is also vital.
D. Developing a Comprehensive Crisis Management Plan
A well-crafted crisis management plan (CMP) is the team’s playbook. It should outline the procedures for different types of crises, communication strategies, stakeholder management, and recovery processes.
o Identify Potential Risks: Conduct a thorough risk assessment to identify potential vulnerabilities and the likelihood of different crisis scenarios.
o Develop Response Protocols: Create detailed protocols for various crisis scenarios, outlining communication strategies, decision-making processes, and resource allocation plans.
o Regular Training and Drills: Regularly conduct training exercises and simulations to ensure the team is familiar with the plan, can work effectively together, and practice their roles under pressure.
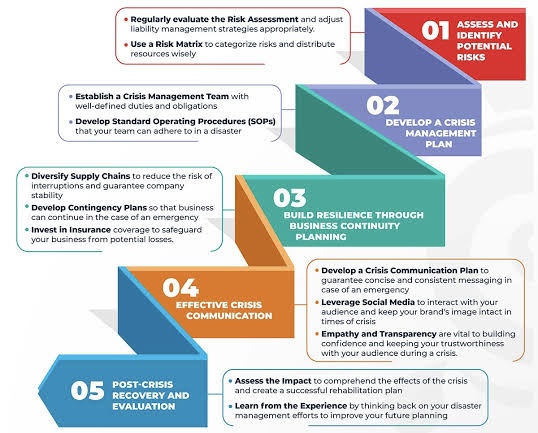
E. Effective Communication
Communication during a crisis must be clear, consistent, and transparent. The CMT should establish protocols for internal and external communications, including predefined templates for public statements. It’s also crucial to identify a spokesperson skilled in media relations to ensure the organization speaks with one voice.
F. Stakeholder Engagement
Identifying and engaging stakeholders is critical before, during, and after a crisis. Understanding stakeholders’ expectations and concerns can guide the crisis response and communication strategy, helping to maintain trust and confidence in the organization.
G. Review and Learn
Post-crisis, the team should conduct a thorough review of the response to identify successes and areas for improvement. This should involve feedback from all levels of the organization and, where appropriate, from external stakeholders. Lessons learned should inform future revisions of the CMP.

H. Crisis Communication Tools
Invest in communication tools and platforms that facilitate efficient information sharing within the team and with stakeholders.
I. Continuous Improvement
Regularly review and update your crisis management plan and protocols to reflect evolving risks and lessons learned from past experiences.
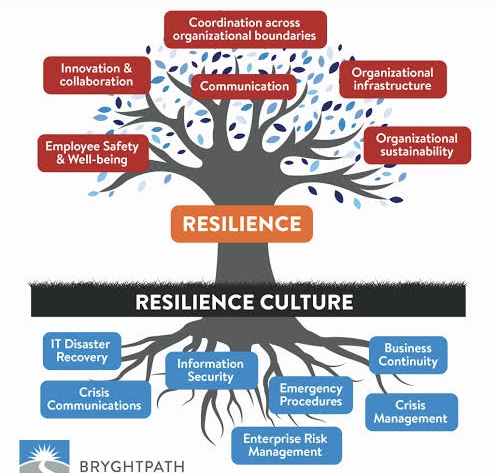
iii. Conclusion
Building an effective crisis management team takes time, dedication, and ongoing effort; it requires careful planning, dedication, and ongoing refinement. Such a team becomes the organization’s anchor during crises, providing direction, reducing chaos, and enabling a more resilient organization. By prioritizing the development of a skilled and prepared CMT, businesses can navigate crises with confidence, safeguarding their operations, reputation, and future.
Remember, a well-prepared team can help mitigate the impact of a crisis, protect your reputation, and ensure the continued success of your organization.
iv. Further references
6 Steps to Creating a Capable Crisis Management Team – PreparedEx
Continuity2continuity2.comCrisis Management Team: Function, Roles & Responsibilities
Agility Recoveryhttps://www.agilityrecovery.com › …6 Keys to Assembling a Crisis Management Team
Universal Classhttps://www.universalclass.com › de…Developing a Team for Crisis Management