Addressing the Digital Skills Deficit: Equipping Organizations for the Artificial Intelligence Era
The specter of the AI Era looms large, promising both innovation and disruption. While artificial intelligence offers exciting possibilities for businesses, a significant hurdle stands in the way – the digital skills gap.
Organizations struggling to find talent equipped to harness this transformative technology risk falling behind. But fear not, for there are solutions!
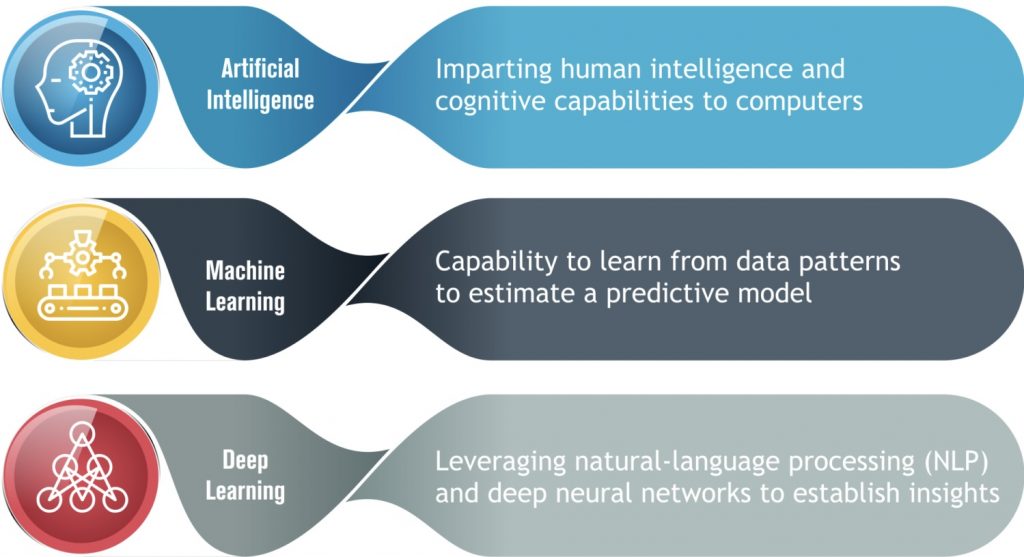
The digital skills gap refers to the discrepancy between the digital skills employers require and the skills their current workforce possesses. This gap is particularly acute in areas like data science, cybersecurity, and AI itself.
As AI becomes more pervasive, the need for professionals who can understand, manage, and leverage its potential will skyrocket.
i. Understanding the Digital Skills Gap
The digital skills gap refers to the disparity between the skills required to effectively implement and utilize new technologies and the current capabilities of the workforce.
In the context of AI, this gap includes a broad range of competencies:
o Technical skills: Proficiency in AI and machine learning (ML), data analytics, programming languages (such as Python and R), and familiarity with AI tools and frameworks.
o Soft skills: Critical thinking, problem-solving, adaptability, and creativity – essential for leveraging AI in innovative ways.
o Business acumen: Understanding how AI can drive strategic business goals, improve customer experiences, and optimize operations.
ii. Steps to Bridge the Digital Skills Gap
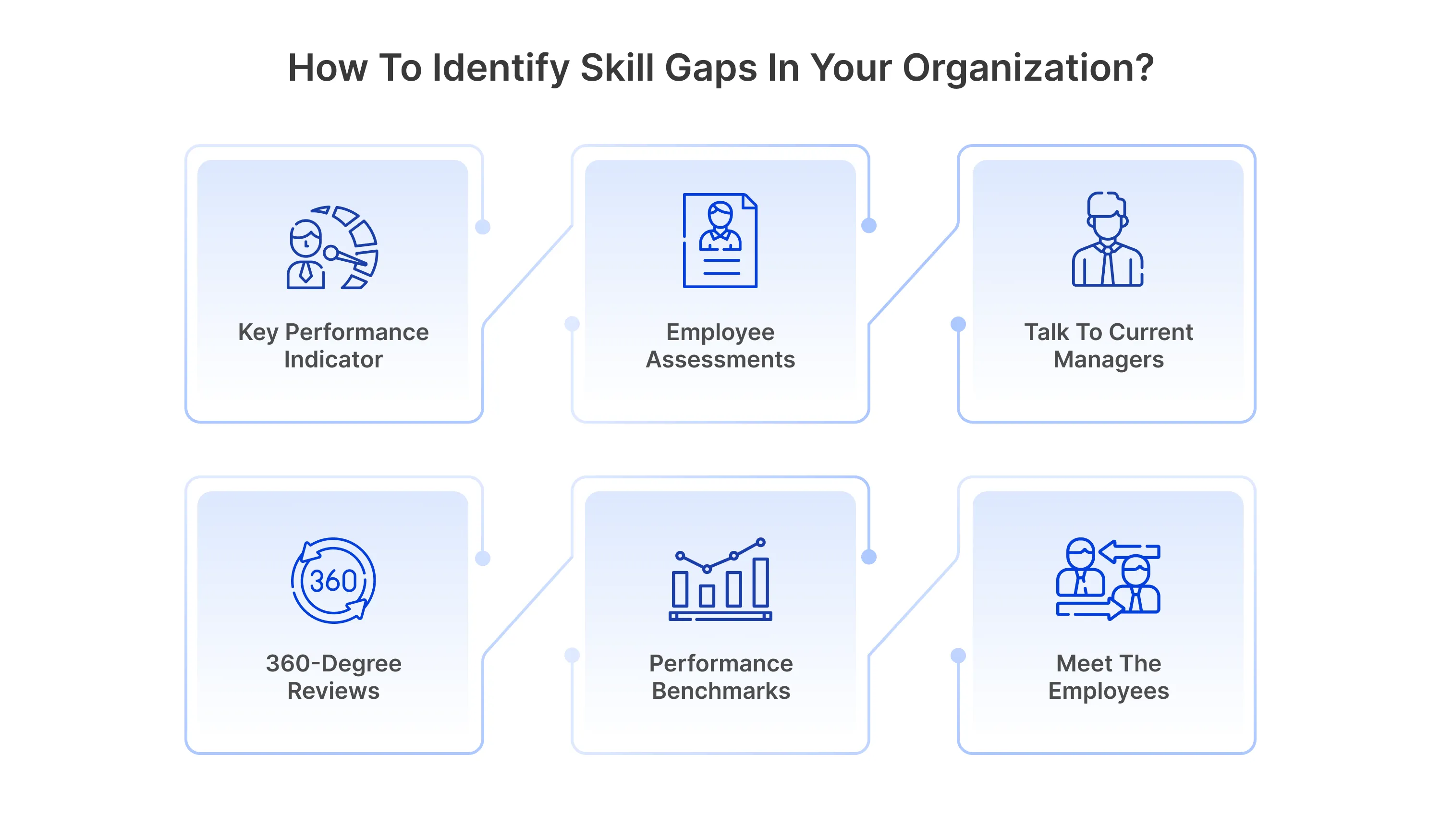
A. Conduct a Skills Assessment
Before implementing any training program, it’s crucial for organizations to understand their current capabilities and identify specific skill gaps. This can be achieved through:
o Surveys and interviews: Gathering insights from employees about their existing skills and aspirations.
o Performance metrics: Analyzing productivity, efficiency, and innovation levels to pinpoint areas for improvement.
o Market analysis: Understanding industry standards and benchmarking against competitors.
B. Develop Customized Training Programs
Once the skills gaps are identified, organizations should design tailored training programs that address their unique needs. Effective training strategies include:
o In-house training: Developing courses and workshops led by internal experts or hiring specialized trainers.
o Online learning platforms: Leveraging resources like Coursera, Udacity, and LinkedIn Learning to provide employees with flexible, on-demand education.
o Certification programs: Encouraging employees to pursue certifications from reputable institutions, which validate their expertise in specific areas.
C. Encourage a Culture of Continuous Learning
Technology evolves rapidly, and so must the skills of the workforce. Fostering a culture that values continuous learning is critical for long-term success. Strategies to achieve this include:
o Leadership support: Ensuring that top management champions learning initiatives and allocates necessary resources.
o Incentives and recognition: Rewarding employees who actively participate in training programs and apply their new skills.
o Knowledge sharing: Creating platforms for employees to share insights, collaborate on projects, and mentor peers.
D. Collaborate with External Partners
Organizations don’t have to tackle the digital skills gap alone. Partnerships with educational institutions, industry associations, and technology vendors can provide valuable support:
o Academic collaborations: Working with universities to co-develop curricula that align with industry needs and offer internships or co-op programs.
o Industry forums: Participating in conferences, workshops, and roundtables to stay abreast of trends and best practices.
o Vendor training: Leveraging training resources from technology providers to ensure employees are proficient with the latest tools and platforms.
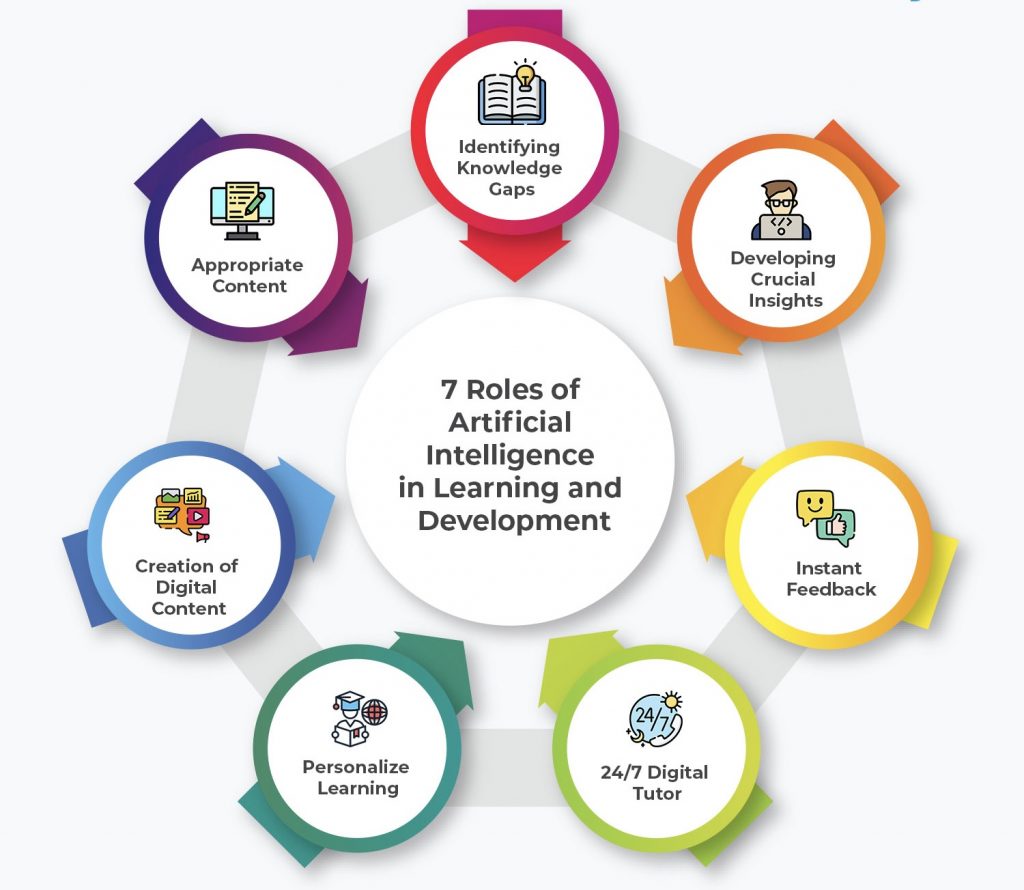
E. Adopt AI Tools to Facilitate Learning
Ironically, AI itself can be a powerful ally in bridging the digital skills gap. AI-driven learning platforms can personalize training experiences, recommend relevant content, and offer real-time feedback. Additionally, AI can assist in:
o Talent identification: Using data analytics to identify employees with the potential to develop critical AI skills.
o Skill mapping: Automating the analysis of existing skills and predicting future needs to ensure training programs remain relevant.
F. Embrace Lifelong Learning
Technology is constantly evolving. Foster a culture of continuous learning within your organization. Encourage employees to pursue online courses, certifications, or even internal knowledge-sharing initiatives.
G. Think Outside the Box
Don’t limit your talent pool to traditional four-year degrees. Consider alternative training paths like bootcamps, micro-credentials, or upskilling programs specifically designed for career changers.
H. Invest in Reskilling
Many existing employees possess valuable skills and experience. Invest in reskilling programs that bridge the gap between their current skillset and the demands of the AI Era.

I. Promote Digital Fluency at All Levels
Leadership must champion digital fluency across the organization.Encourage open communication and collaboration between technical and non-technical teams.
iii. Measuring Success and Adapting Strategies

To ensure the effectiveness of efforts to bridge the digital skills gap, organizations should regularly measure and evaluate their strategies. Key performance indicators (KPIs) might include:
o Skill Acquisition Rates: Track the number of employees gaining AI-related skills and certifications.
o Project Outcomes: Assess the success of AI projects and the contribution of newly acquired skills to these projects.
o Employee Engagement and Retention: Monitor employee satisfaction and retention rates, particularly among those participating in upskilling programs.
iv. Conclusion

As AI continues to shape the future of work, organizations must proactively address the digital skills gap to secure their competitive edge and foster a resilient, innovative workforce.
By conducting thorough skills assessments, developing customized training programs, fostering a culture of continuous learning, leveraging external partnerships, and adopting AI-driven learning tools, organizations can effectively bridge the digital skills gap.
Preparing for an AI-driven future is not merely a technological challenge but a strategic imperative.
Companies that invest in their people today will be the leaders of tomorrow, poised to harness the power of AI for innovation, growth, and competitive advantage.
The future is here, and it is digital; preparing for it is not just an option but a necessity for success.
v. Further references
The Digital Skills Gap Solution: How Organizations Can Prepare for the AI Era
Harnhamhttps://www.harnham.com › the-ai-s…Addressing the AI and digital skills gap
SAPhttps://www.sap.com › viewpointsUpskilling Your Workforce for the AI Er
LinkedInhttps://www.linkedin.com › pulseCreating a future-proof workforce: Using AI for …
MIT CISRhttps://cisr.mit.edu › publicationResolving Workforce Skills Gaps with AI-Powered Insights
AI Businesshttps://aibusiness.com › how-you-…How you can bridge the AI skills gap
CIO Divehttps://www.ciodive.com › newsSkills gap threatens new tech implementation, executives say