Building a Work Oasis: Security Measures for an Evolving Workspace
The modern workplace is constantly changing. Remote work is on the rise, new technologies emerge daily, and collaboration takes on ever-more fluid forms. In this dynamic landscape, security becomes not just a necessity, but a foundation for growth and innovation.
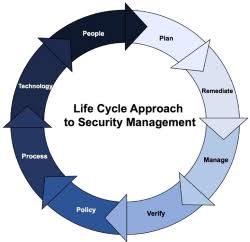
Establishing an evolving work environment while ensuring security measures involves creating a balance between flexibility, adaptability, and the protection of information and systems. The goal is to have an environment that can adapt to changing business needs and technological advancements without compromising the confidentiality, integrity, and availability of data.
i. Here are key steps to ensure a secure and flexible work environment:
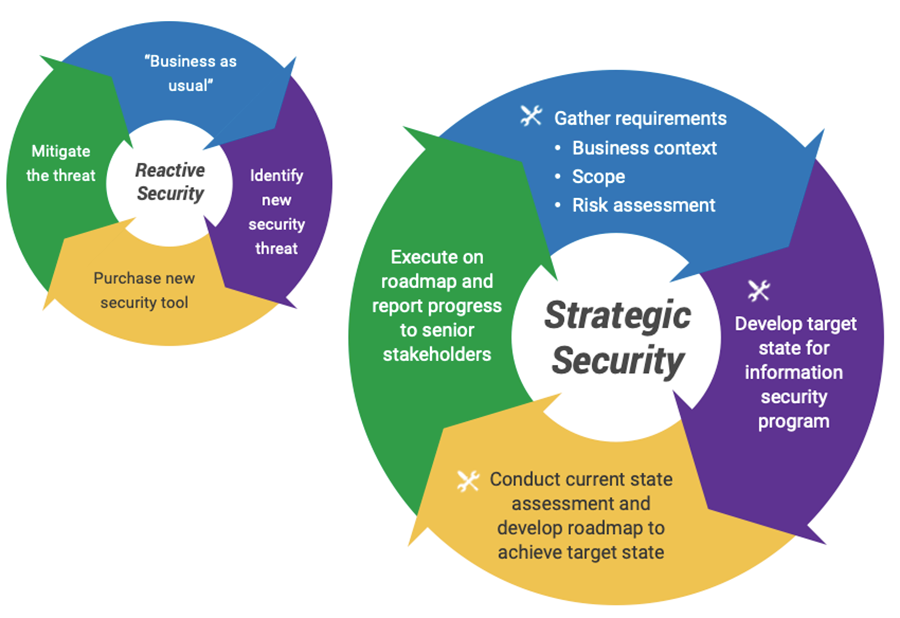
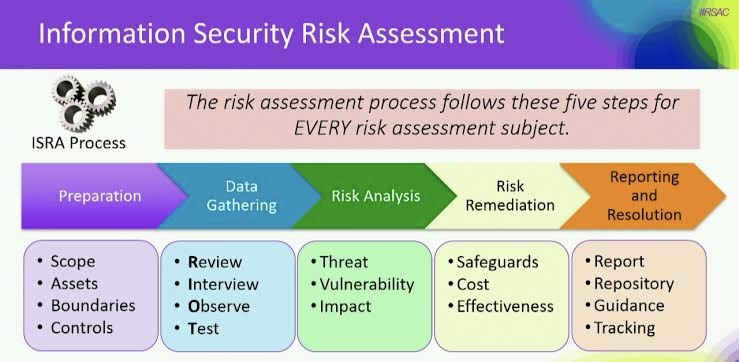
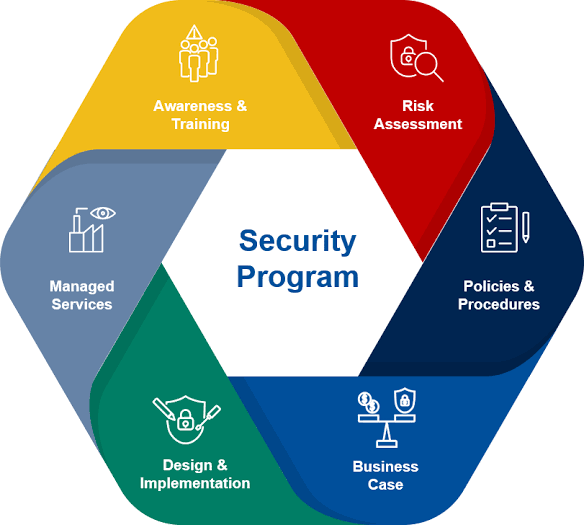
A. Risk Assessment: Conduct regular risk assessments to identify potential threats and vulnerabilities. Consider the evolving nature of the work environment, including remote work and the use of diverse devices.
B. Technology Implementation
o Secure-by-Design: Incorporate security features at the design phase of all projects, services, and processes.
o Encryption and Access Control: Use strong encryption for data at rest and in transit. Implement robust access control measures that adapt to various employment scenarios, such as remote work or BYOD (Bring Your Own Device).
C. Security Policies and Frameworks
o Adaptive Policies: Develop security policies that can adapt to new business models and technologies.
o Frameworks and Standards: Utilize recognized frameworks (like ISO/IEC 27001) and standards to create a structured approach to security, ensuring alignment with best practices.
D. Cybersecurity Culture
o Promote Security as a Core Value: Encourage all employees to take responsibility for the organization’s security.
o Reward and Recognize: Acknowledge employees who proactively contribute to improving security.
E. Remote and Flexible Work Environments
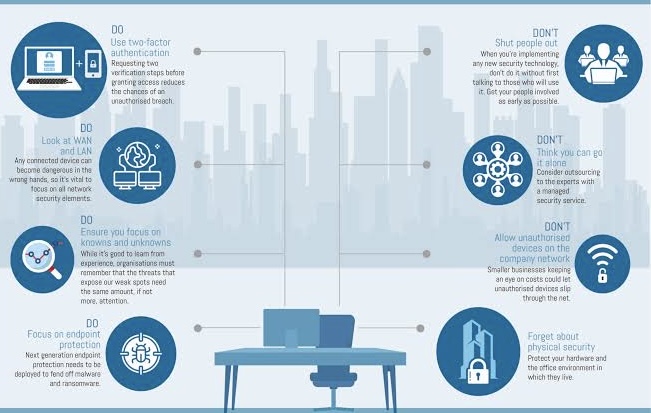
o Remote Access Solutions: Implement secure VPN access, multi-factor authentication, and endpoint protection for remote workers.
o Policy for Remote Work: Establish clear guidelines and best practices for employees who work remotely.
F. Technology and Workforce Flexibility
o Cloud Services: Utilize cloud services that provide scalability and flexibility while maintaining security measures.
o Diverse Skill Sets: Foster a team with a variety of skills to handle evolving technologies and challenges.
G. Endpoint Protection: Employ endpoint protection solutions to secure devices connected to the corporate network. Regularly update and patch software to address vulnerabilities.
H. Identity and Access Management (IAM): Implement IAM solutions to manage user access and authentication. This becomes crucial in an evolving work environment with varying access points.
I. Collaboration Tool Security: Secure collaboration tools and platforms by configuring access controls, enabling encryption, and staying informed about the security features of the tools used for remote communication.
J. Training and Awareness
o Ongoing Education: Provide continuous security awareness training for all employees, emphasizing the evolving nature of threats.
o Simulated Attacks: Regularly test staff with simulated phishing and social engineering attacks to raise awareness.
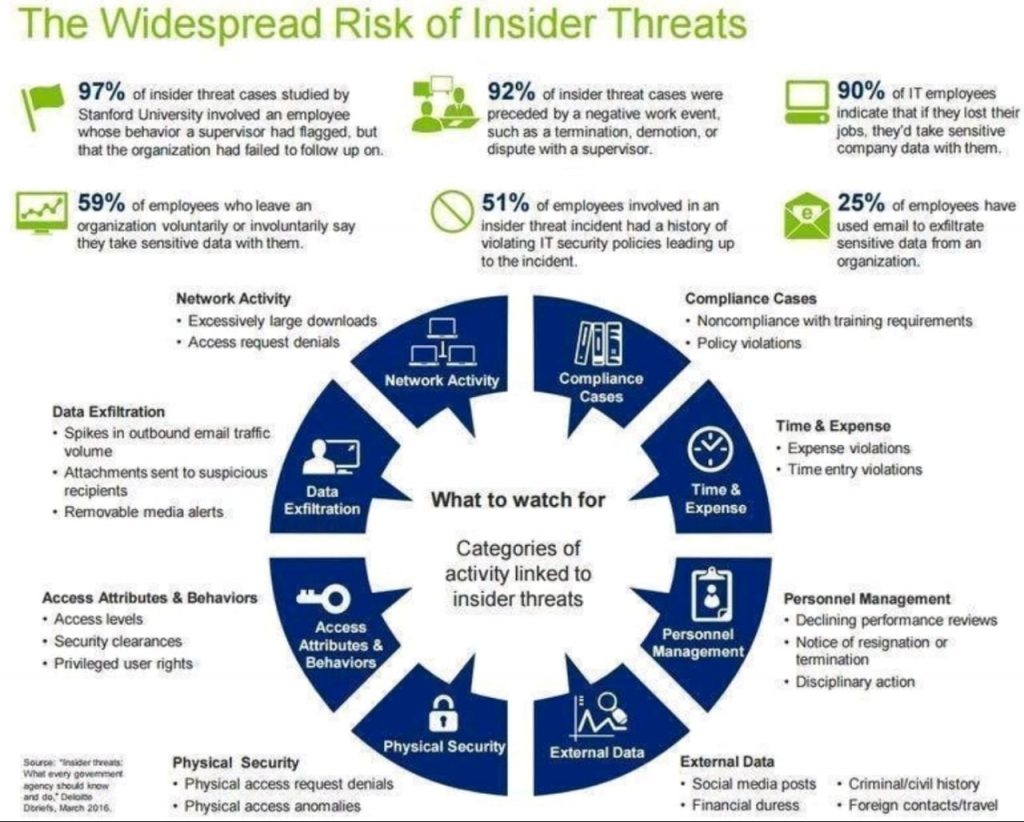
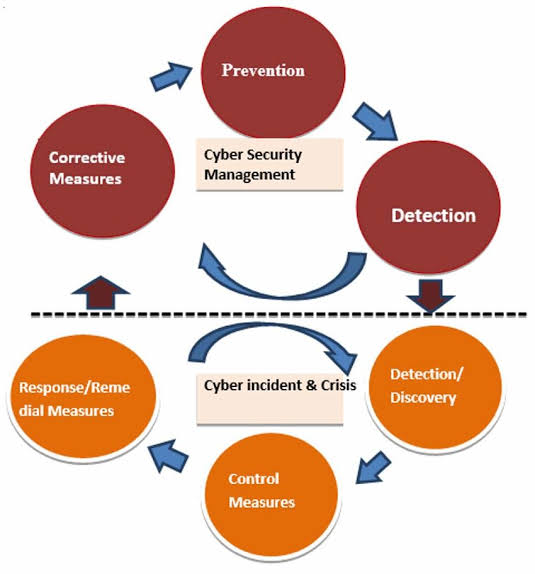
K. Incident Response Planning
o Proactive Planning: Develop and periodically review incident response plans to ensure they are up-to-date.
o Incident Simulations: Conduct regular drills to prepare the team for various scenarios.
L. Continuous Monitoring: Implement continuous monitoring of network activities, user behavior, and security logs. Utilize security information and event management (SIEM) tools to detect and respond to anomalies.
M. Audits and Compliance Checks
o Regular Audits: Conduct internal and external security audits to uncover and address weaknesses.
o Compliance Verification: Continuously verify compliance with relevant laws and regulations, such as GDPR, HIPAA, or PCI-DSS.
N. Compliance with Regulations: Stay informed about and comply with relevant data protection and privacy regulations. This is crucial as the work environment evolves, especially with the rise of remote work and global data transfer.
O. Secure Development Practices: If developing custom applications or software, incorporate secure coding practices from the beginning. Regularly update and patch software to address security vulnerabilities.
P. Secure Communication Channels: Encrypt communication channels, both within the organization and with external partners. Use secure protocols for data transmission to prevent unauthorized access.
Q. Adaptive Security Measures: Embrace adaptive security measures that can evolve with the changing landscape. This includes artificial intelligence and machine learning solutions for threat detection and response.
R. Regular Updates and Patch Management
o Automated Updates: Use automated tools to ensure that all systems are regularly updated with the latest security patches.
o EOL (End of Life) Strategies: Have a process in place for replacing or upgrading software and hardware that is no longer supported.
S. Collaborative Security Approach
o Partner with IT Vendors: Work with technology providers who understand and support your evolving work environment.
o Information Sharing: Participate in industry groups and forums to stay aware of the latest security trends and solutions.
ii. Here are some key security measures to consider for your evolving work environment:
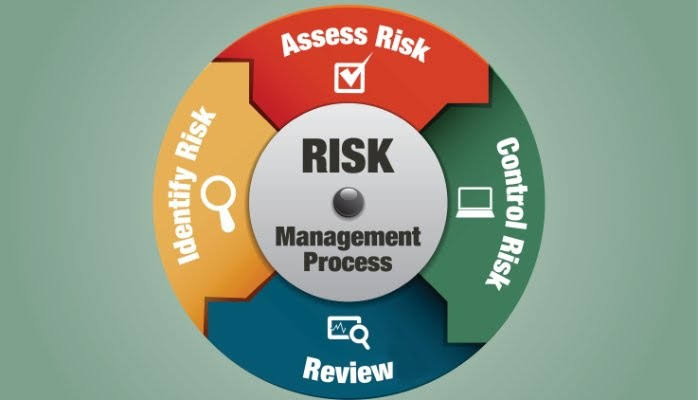
A. Identifying Security Needs and Risks:
The establishment of an evolving work environment begins with identifying an organization’s security needs and assessing any potential risks. This involves understanding the framework of the organization’s operations, including the nature of the business, employees’ roles, and day-to-day functions.
B. Embrace the Cloud, Securely:
Cloud-based tools and platforms offer incredible flexibility and scalability, but they also introduce new security concerns. Implement robust data encryption, access controls, and multi-factor authentication to safeguard your information in the cloud. Consider adopting a Zero Trust Security approach, where every access request is verified regardless of location or device.
C. Empower Your People:
Security isn’t just about technology; it’s about people. Invest in security awareness training to educate your employees on best practices like phishing identification, password hygiene, and responsible social media use. Foster a culture of open communication where employees feel comfortable reporting suspicious activity.
D. Fortify Your Endpoints:
Laptops, tablets, and smartphones are increasingly the workhorses of the modern workforce. Secure these endpoints with antivirus software, firewalls, and endpoint detection and response (EDR) solutions. Implement policies for device encryption, secure password management, and software updates.
E. Build a Culture of Continuous Improvement:
The threat landscape is ever-evolving, so your security measures should be too. Conduct regular security audits and penetration testing to identify vulnerabilities and stay ahead of potential threats. Encourage a culture of continuous improvement, where feedback and best practices are constantly shared and implemented.
F. Embrace Flexibility, Securely:
The rise of remote and hybrid work arrangements necessitates flexible security solutions. Invest in tools that enable secure remote access, collaboration, and communication. Leverage virtual private networks (VPNs) and secure cloud-based communication platforms to ensure data safety regardless of location.
G. Confidentiality, Integrity, and Availability (CIA):
These are the three core principles of data security. Confidentiality means that sensitive information is accessible only to authorized individuals. Integrity ensures that data is accurate and unchanged during transit. Availability means that data should be accessible to authorized personnel when needed.
H. Catering to Remote Work or Hybrid Work Models:
In an evolving work environment, more people are working remotely or in hybrid models. Organizations should include VPNs, secure collaboration tools, and secure devices in their security plan.
iii. Conclusion
Remember, security is not a one-time thing, it’s an ongoing journey. By implementing these measures and fostering a culture of security awareness, you can build an evolving work environment that is both secure and inspiring, allowing your team to thrive in the ever-changing digital landscape.
By integrating these security measures into your evolving work environment, you can create a resilient and adaptive security posture. Regularly reassess and update your security protocols to stay ahead of emerging threats and technology changes.
To sum up, security measures lay the groundwork for an adaptable and evolving work environment that accommodates changing business needs, threats, and workforce practices. In an age of rapid digital transformation, security measures must not be an afterthought but an integral part of strategic planning.
iv. Further references
LinkedInhttps://www.linkedin.com › adviceHow can you create a security-conscious work environment?
StitchDXhttps://stitchdx.com › blog › shift-fr…The Shift From Digital to Modern Workplace