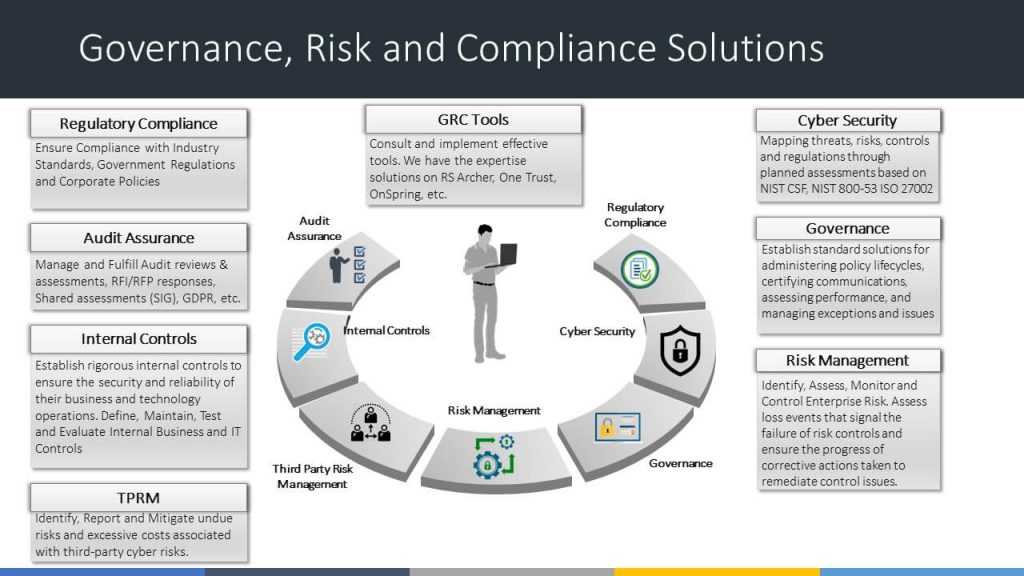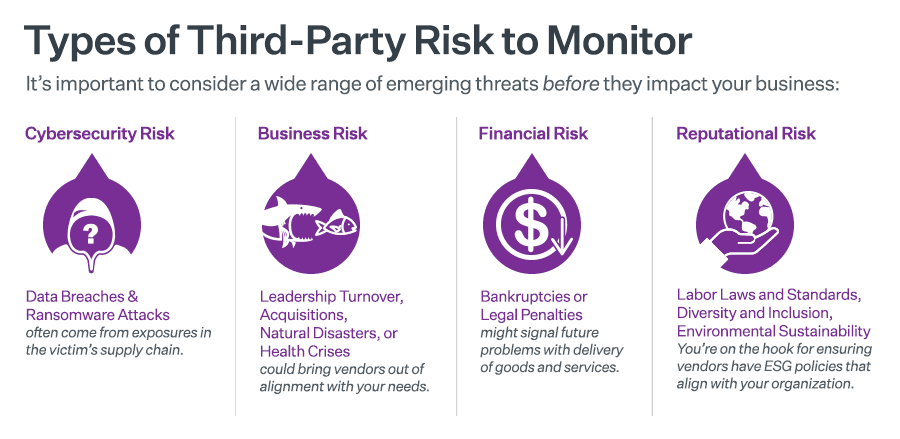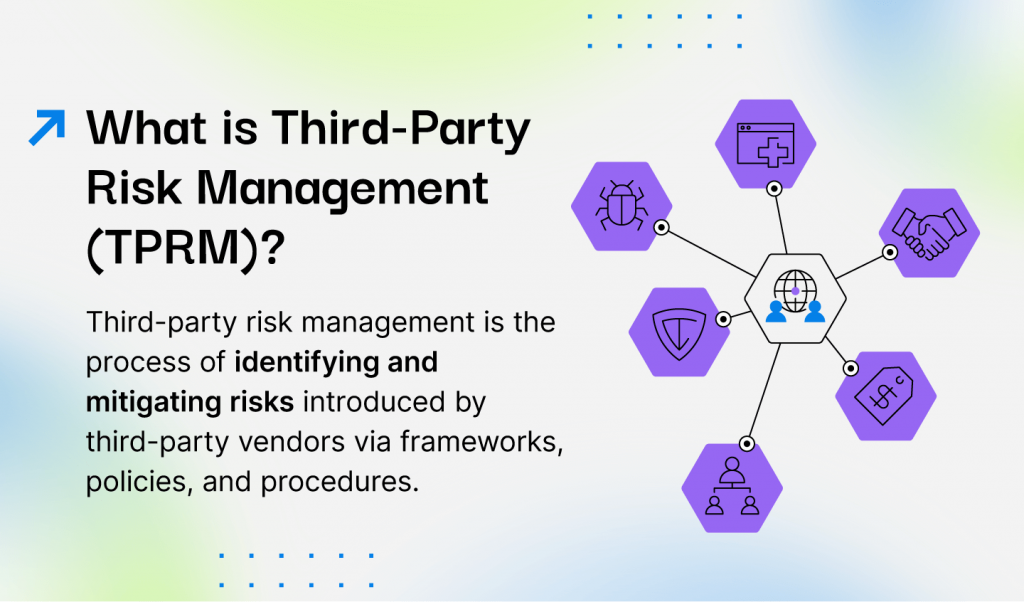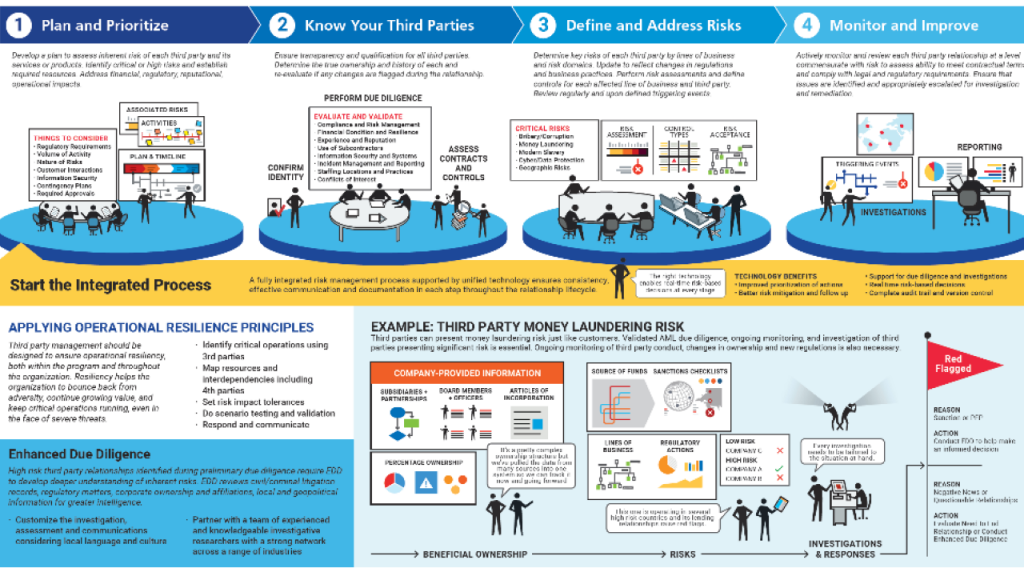
Risk Management and Enterprise Risk Management: A Comparative Overview
In the contemporary business landscape, uncertainty is a constant. Organizations must navigate a myriad of risks ranging from financial and operational to strategic and reputational. Two crucial frameworks that help organizations manage these uncertainties are Risk Management (RM) and Enterprise Risk Management (ERM). While they share similarities, they are distinct in their scope, approach, and application. Here’s a brief overview of each:
i. Risk Management
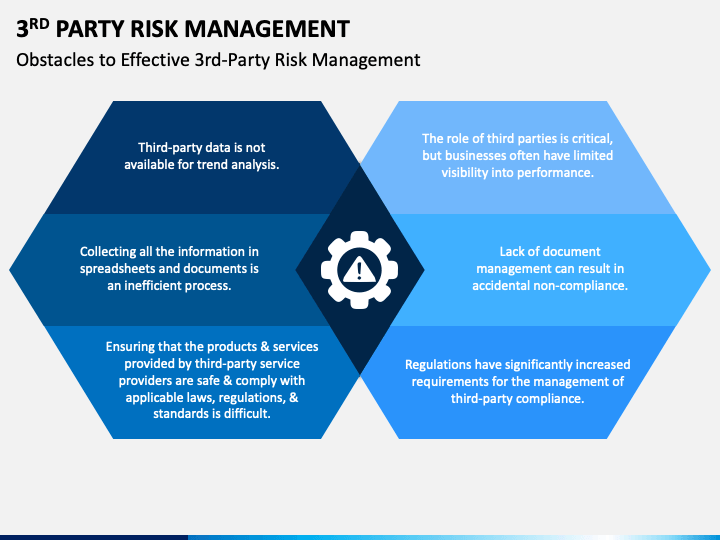
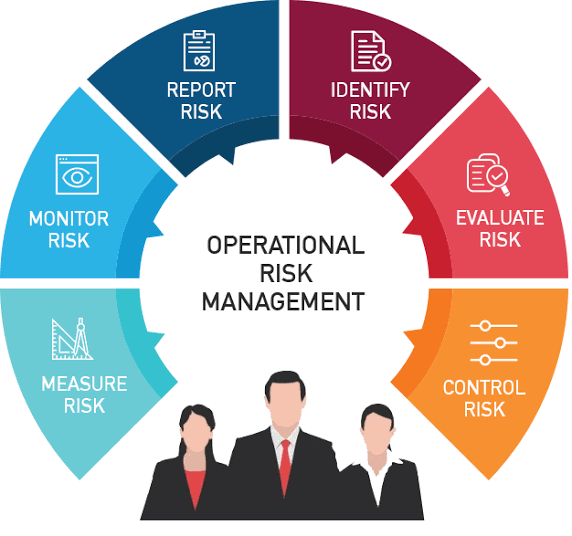
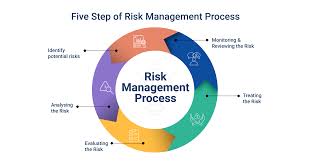
Risk Management is the process of identifying, analyzing, and responding to risks that could potentially affect an organization’s objectives. The key steps typically involved in risk management are:
A. Identification: Recognizing potential risks that could impact the organization.
B. Assessment: Evaluating the likelihood and impact of these risks using qualitative and quantitative methods.
C. Mitigation: Developing strategies to manage, reduce, or eliminate the risks. This may include avoidance, reduction, sharing, or acceptance of the risks.
D. Monitoring and Review: Continuously monitoring the risk environment and reviewing the effectiveness of risk responses to ensure risks are effectively managed.
ii. Enterprise Risk Management (ERM)
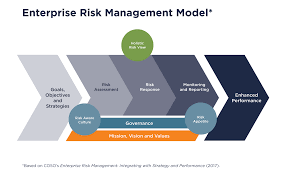
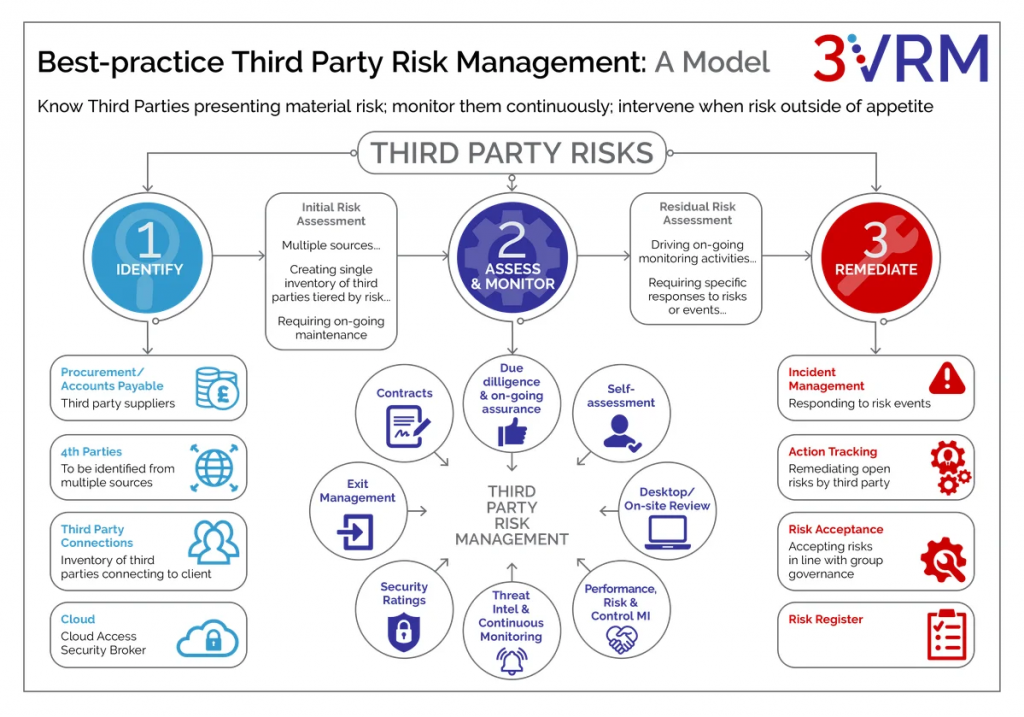
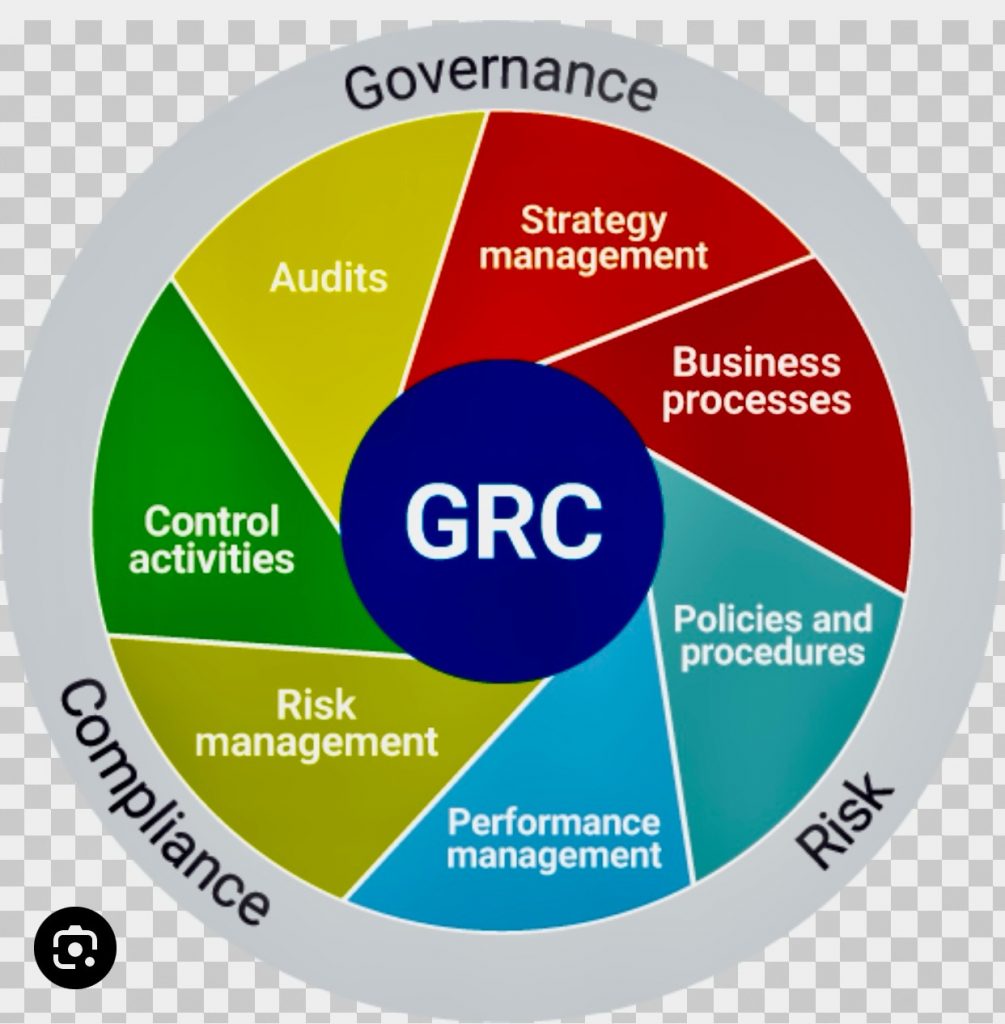
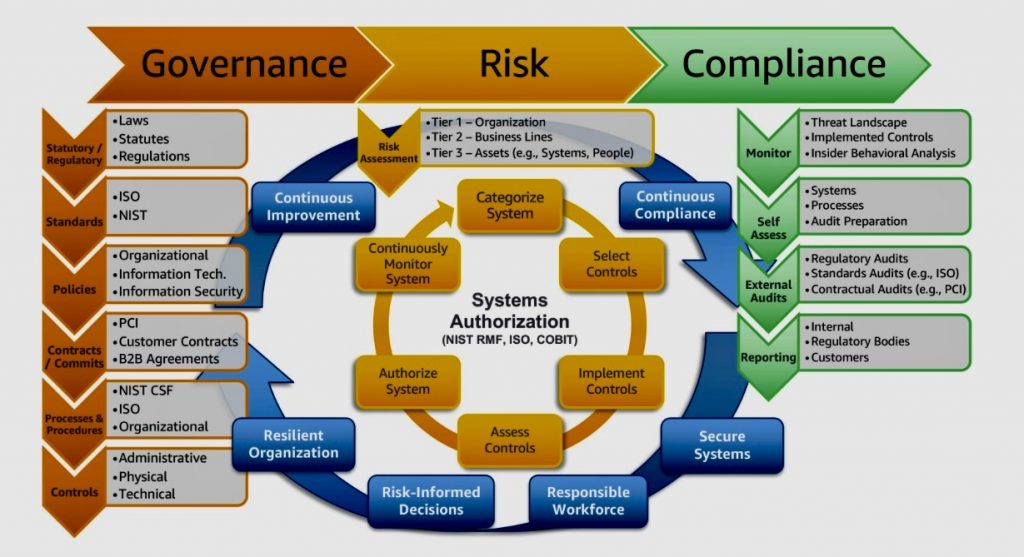
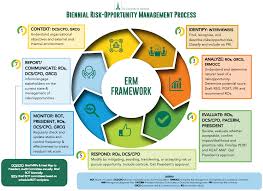
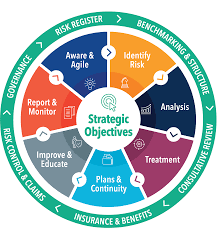
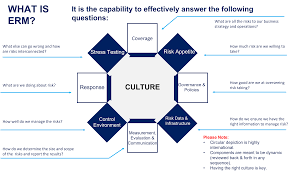
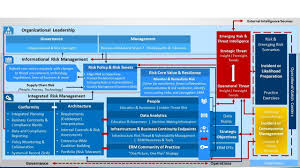
Enterprise Risk Management (ERM) is an integrated framework that goes beyond the traditional risk management approach. It focuses on a holistic and organization-wide perspective of identifying, assessing, managing, and monitoring risks across an entire enterprise. ERM aims to provide a structured and consistent process for managing all types of risks that an organization faces.
iii. Key components of ERM include
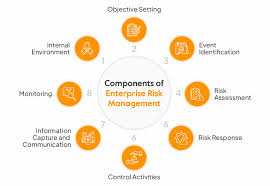
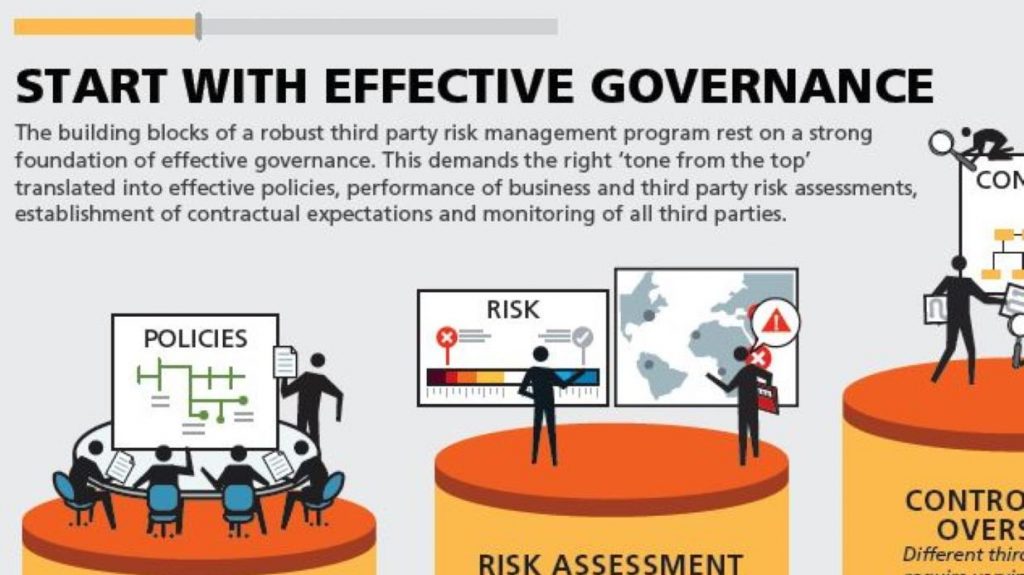
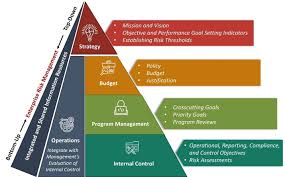
A. Governance and Culture: Establishing the organization’s risk management framework and embedding risk culture within the organization.
B. Strategy and Objective-Setting: Aligning risk management with the organization’s strategy and setting clear objectives.
C. Performance: Identifying and assessing risks that may impact the achievement of organizational objectives, and integrating risk considerations into performance management.
D. Review and Revision: Monitoring and reviewing risk performance, and making necessary adjustments to the ERM framework and activities.
E. Information, Communication, and Reporting: Ensuring effective communication and reporting of risk information across all levels of the organization.
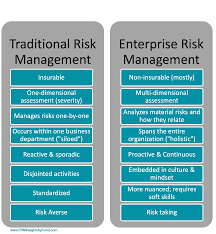
iv. Differences between Risk Management and ERM
A. Risk Management:
- Focus: Risk management is a broad term encompassing the identification, assessment, and mitigation of risks that can impact any aspect of an organization. This could be financial risks, operational risks, strategic risks, or even reputational risks.
- Approach: The RM approach is often reactive and siloed, addressing risks as they arise within specific areas of the organization. It typically involves the following steps:
- Scope: Risk management can be applied to specific departments, projects, or initiatives within an organization. It’s often a localized approach, focusing on the risks relevant to a particular area.
- Specificity: Targets specific risks within specific departments or aspects of operations.
- Reactivity: Often implemented in response to the identification of potential risks.
- Tactical Approach: Focuses on tactics for handling individual risks.
- Process: The risk management process typically involves:
- Identifying potential risks
- Assessing the likelihood and severity of each risk
- Developing plans to mitigate or avoid these risks
- Monitoring and updating risk management strategies as needed
- Applications: Risk Management is commonly applied within project management, IT security, health and safety, financial auditing, and compliance. Each department or project team may have its risk management process, often leading to isolated risk assessments and responses.
B. Enterprise Risk Management (ERM):
- Focus: ERM takes a holistic approach to risk management, considering all potential risks that could affect the entire organization and its ability to achieve its objectives. It goes beyond departmental silos and considers the interconnectedness of various risks.
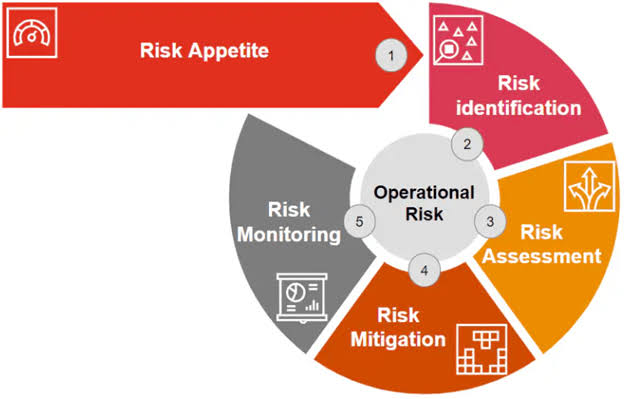
- Approach: ERM takes a holistic and proactive approach to risk management. It involves:
- Risk Culture and Governance: Establishing a risk-aware culture and defining roles and responsibilities for risk management.
- Risk Appetite and Strategy: Defining the level of risk the organization is willing to accept in pursuit of its objectives.
- Risk Identification and Assessment: Identifying and assessing risks across the organization in a unified manner.
- Risk Response: Developing strategies that align risk management with the organization’s strategic goals.
- Risk Monitoring and Reporting: Continuously monitoring risk exposures and reporting to senior management and the board of directors.
- Scope: ERM has an enterprise-wide perspective, looking at the big picture and how different risks can interact and amplify each other. It considers strategic risks alongside operational and financial risks.
- Holistic Perspective: Considers all types of risks across the organization as interrelated components that affect each other.
- Proactivity: Focuses on identifying and mitigating risks before they occur.
- Strategic Approach: Integrates risk management with corporate strategy and decision-making processes.
- Process: ERM builds upon the core principles of risk management but expands them to encompass the entire organization. It involves:
- Identifying all potential risks across the organization
- Assessing the enterprise-wide impact of each risk
- Developing a comprehensive risk management strategy that considers all departments and functions
- Integrating risk management into the organization’s overall strategy and decision-making processes
- Continuously monitoring and updating the ERM framework
- Applications: ERM is applied at the strategic level, influencing decision-making processes across the entire organization. It integrates risk management into business planning, performance management, and corporate governance, ensuring that risk considerations are embedded in all significant business activities.
v. Importance of Risk Management and ERM
Both risk management and ERM are critical for an organization’s success. They help in:
o Protecting Assets: Mitigating potential losses and safeguarding resources.
o Enhancing Decision-Making: Providing information that can support informed decision-making.
o Improving Resilience: Preparing the organization to respond to adverse events effectively.
o Achieving Objectives: Ensuring that risks do not derail the organization from reaching its goals.
vi. Strategic Integration
Whereas RM is often tactical, focusing on immediate concerns or specific areas of risk, ERM is inherently strategic. ERM is designed to be part of the organizational fabric, influencing the strategic planning process itself. It helps ensure that risk considerations are an integral part of decision-making at the highest levels.
vii. Value Creation

ERM extends beyond mere risk prevention and mitigation. By integrating risk management with strategic objectives, ERM positions organizations to not only protect value but also to identify and exploit opportunities in a way that RM typically does not. This proactive stance towards risk can lead to innovation and competitive advantage.
viii. Here’s an analogy to illustrate the difference
- Risk Management: Imagine a house. Risk management is like checking the roof for leaks, the foundation for cracks, and the electrical wiring for safety hazards. It focuses on individual aspects of the house.
- ERM: ERM is like looking at the entire house and considering all potential hazards, from natural disasters to break-ins. It considers how a leaky roof could lead to electrical problems and how a strong foundation can withstand various threats. It’s a comprehensive approach to ensuring the safety and security of the entire structure.
ix. Benefits of ERM Over Traditional RM
A. Strategic Alignment: ERM ensures that risk management practices are aligned with the organization’s strategic goals, facilitating better decision-making.
B. Holistic View: By considering all types of risks and their interdependencies, ERM provides a comprehensive view of the organization’s risk profile.
C. Improved Performance: Organizations with effective ERM practices can better anticipate and respond to risks, leading to improved operational performance and resilience.
D. Enhanced Communication: ERM promotes transparent communication about risks across the organization, ensuring that all stakeholders are informed and engaged in risk management processes.
E. Regulatory Compliance: ERM helps organizations comply with regulatory requirements by providing a structured approach to identifying and managing risks.
x. Conclusion
An effective risk management or ERM framework can help organizations navigate uncertainties and improve their overall risk posture, ultimately contributing to sustained success and growth.
While Risk Management and Enterprise Risk Management share the common goal of mitigating risks, their approaches, scopes, and outcomes significantly differ. RM offers a focused, tactical method for addressing specialized risks within particular segments of an organization. In contrast, ERM provides a holistic, strategic framework for understanding and managing the array of risks affecting the entire enterprise, thereby enhancing decision-making and promoting value creation. As businesses navigate increasingly complex and volatile environments, integrating ERM into their strategic planning and execution becomes not just advantageous but essential for sustainable success.
xi. Further references
https://www.oracle.com/eg/erp/risk-management/what-is-enterprise-risk-management
https://www.theirm.org/what-we-do/what-is-enterprise-risk-management
https://erm.ncsu.edu/resource-center/what-is-enterprise-risk-management
https://legal.thomsonreuters.com/blog/what-is-enterprise-risk-management