The concept of “fraud being an opportunity for the internal auditor” is a complex one, and it’s crucial to approach it with careful consideration.
While fraud is undoubtedly a negative occurrence, the role of an internal auditor is not to rejoice in its discovery but to utilize it as a learning experience and implement measures to prevent future occurrences.
i. Challenges and Risks:
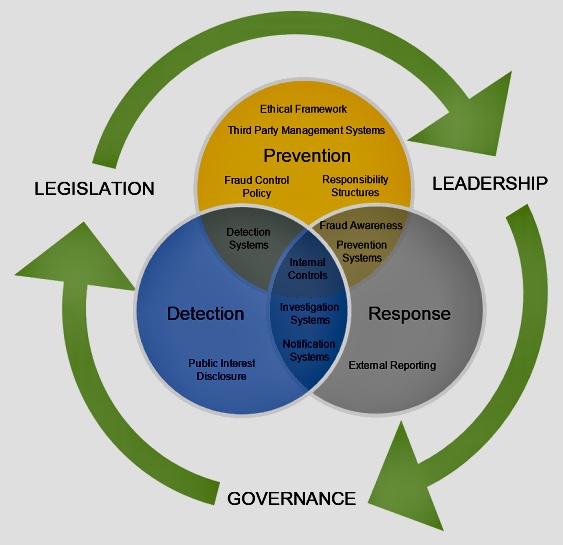
A. Ethical Dilemma: It’s important to remember that fraud is a serious ethical and legal issue. Even discussing it as an “opportunity” can be misconstrued. The focus should always be on preventing and protecting the organization, not on potentially exploiting the situation.
B. Reputational Damage: If an internal auditor is perceived as relishing fraud, it can damage their reputation and the trust placed in them by the organization.
C. Misplaced Focus: Focusing solely on fraud detection can lead to neglecting other important aspects of internal auditing, such as operational efficiency and risk management.
ii. Potential Opportunities:
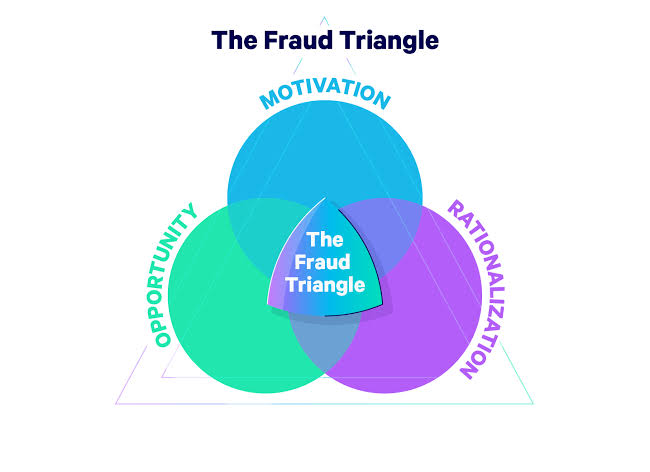
A. Strengthening Controls: By analyzing how and why the fraud occurred, internal auditors can identify weaknesses in internal controls and recommend improvements. This can significantly enhance the organization’s defenses against future fraud attempts.
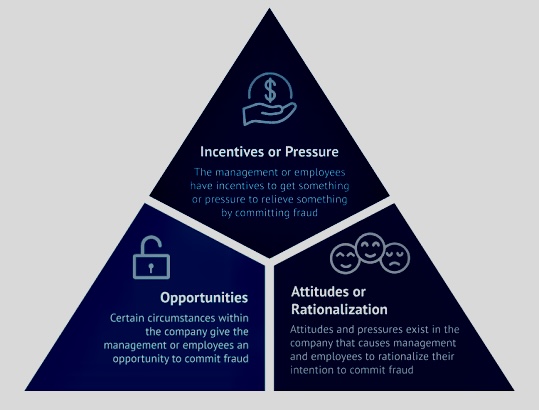
B. Enhancing Risk Assessment: Understanding the fraud triangle (opportunity, pressure/incentive, and rationalization) can help internal auditors develop more effective risk assessments, identifying areas where fraud is more likely to occur.
C. Promoting Ethical Values: The discovery of fraud can be an opportunity to promote a strong ethical culture within the organization. Internal auditors can work with management to raise awareness about fraud, its consequences, and the importance of ethical conduct.
iii. Overall Perspective:
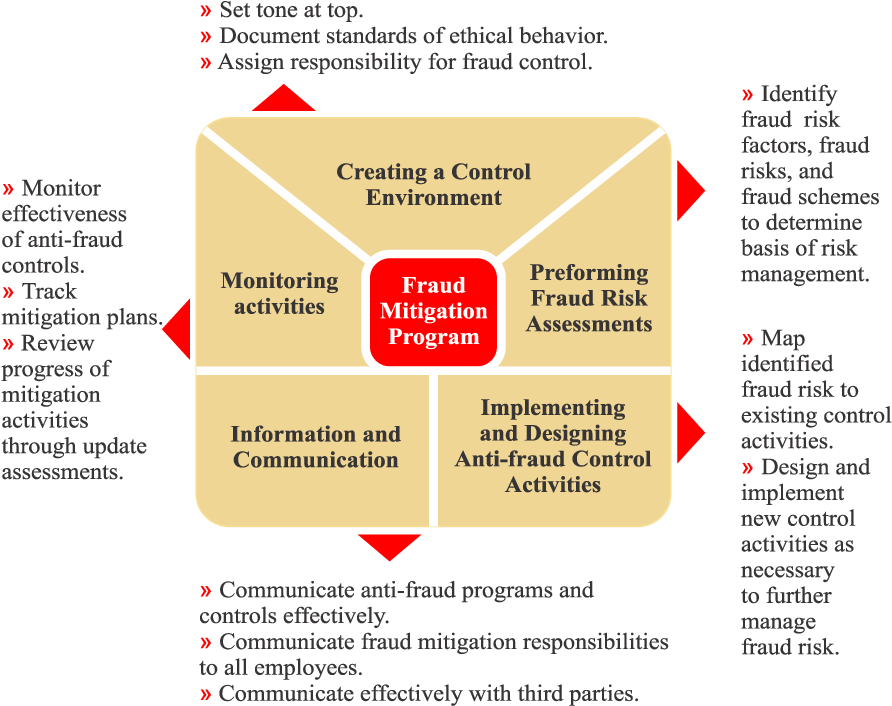
While fraud should never be viewed as desirable, it can present an opportunity for internal auditors to learn from past mistakes and strengthen the organization’s defenses. The key is to approach it with professionalism, ethics, and a focus on prevention rather than exploitation.
iv. Here’s how internal auditors can leverage this opportunity:
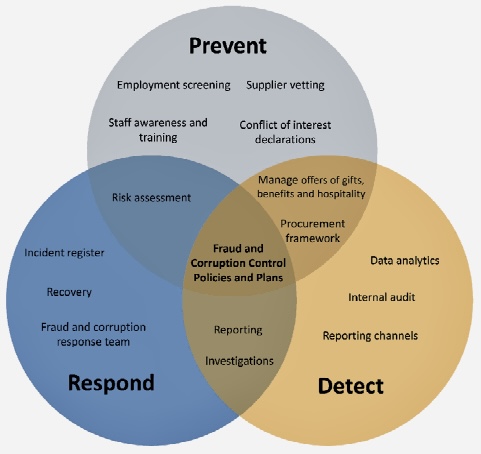
A. Early Detection and Prevention: Internal auditors are well-positioned to identify early signs of fraud through regular and thorough audits. By focusing on preventive measures, auditors can help the organization avoid financial losses and reputational damage.
B. Risk Identification and Assessment: Internal auditors help identify and assess the areas within the company that are most susceptible to fraud. They use their knowledge and understanding of the business, including its processes, systems, and controls, to identify any loopholes that could be exploited.
C. Fraud Risk Assessment: Conducting a comprehensive fraud risk assessment allows internal auditors to identify areas vulnerable to fraudulent activities. This assessment informs audit planning and helps prioritize areas that require closer scrutiny.
D. Implementing Prevention Measures: After identifying risks, internal auditors recommend measures to prevent fraud. These might involve designing and strengthening internal controls, enhancing security measures, or improving processes and policies.
E. Detection of Fraud: Through their regular audits, internal auditors can detect signs of potential fraud. They do this by analyzing financial transactions, reviewing operational data, conducting interviews, and performing surprise audits, among other methods.
F. Investigation: When potential fraud is detected, internal auditors may assist in conducting a detailed investigation, including gathering evidence, interviewing potential suspects, and documenting the case in a clear and unbiased way. They also help management in referring cases to law enforcement if necessary.
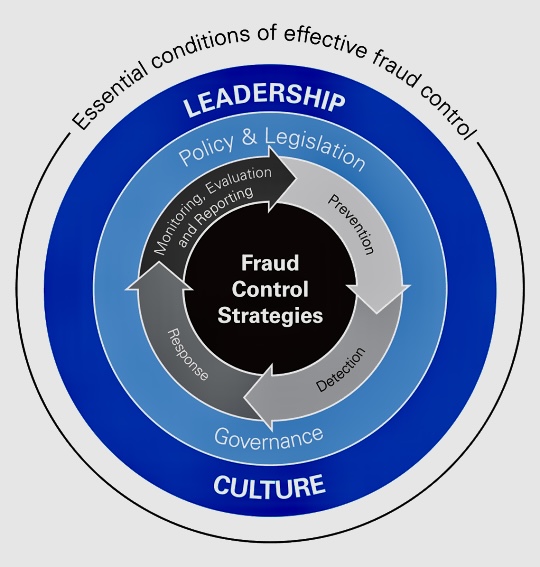
G. Promoting an Ethical Culture: Internal auditors also promote a culture of ethics and integrity within the organization. They can provide fraud awareness training and promote a whistleblowing system to encourage employees to report any suspicious activities.
H. Policy Development: Auditors can help in the creation or refinement of anti-fraud policies. This adds to their strategic role in ensuring the organization is protected against fraudulent activities.
I. Audit Planning and Execution: Integrate fraud-specific audit procedures into the overall audit plan. This may include examining transactional data, analyzing patterns, and conducting targeted testing to uncover irregularities.
J. Data Analytics and Forensic Tools: Leverage data analytics and forensic tools to identify anomalies and patterns indicative of fraudulent activities. Analyzing large datasets can reveal hidden patterns that may be challenging to detect through traditional audit methods.
K. Whistleblower Programs: Encourage the use of whistleblower programs to facilitate the reporting of suspected fraud. Internal auditors can play a role in ensuring the effectiveness of these programs and investigating reported concerns.
L. Internal Controls Enhancement: Internal auditors can recommend improvements to internal controls to mitigate fraud risks. This involves assessing the design and effectiveness of existing controls and proposing enhancements where weaknesses are identified.
M. Fraud Awareness Training: Provide fraud awareness training to employees at all levels. Educating staff about common fraud schemes, red flags, and reporting mechanisms creates a vigilant organizational culture that contributes to fraud prevention.

N. Collaboration with Other Departments: Work collaboratively with legal, compliance, and risk management teams to address fraud-related issues comprehensively. A cross-functional approach ensures a more robust response to fraud risks.
O. Continuous Monitoring: Internal auditors are involved in the continuous monitoring of the organization’s internal control and governance systems to ensure their effectiveness and agility to adapt to organizational changes and prevent fraud.
P. Investigation Support: In cases where fraud is suspected or identified, internal auditors can support investigations by providing relevant data, analysis, and insights. This collaboration with investigative teams contributes to effective resolution.
Q. Reporting to Management and Board: Regularly communicate findings related to fraud risks, controls, and audit results to senior management and the board. Transparent reporting enhances organizational awareness and encourages proactive risk management.
R. Stay Informed on Fraud Trends: Stay abreast of evolving fraud trends and tactics. This knowledge equips internal auditors to adapt their audit strategies and focus on emerging threats.
S. Adherence to Professional Standards: Ensure that audit activities adhere to professional standards and ethical guidelines. Maintaining the highest level of integrity is crucial to preserving the credibility and effectiveness of the internal audit function.
T. Continuous Improvement: Fraud detection tools and techniques are constantly evolving. Internal auditors have the opportunity to stay ahead of the curve by continually improving their skills and the tools they use to detect and prevent fraud.
As such, not only is fraud detection an opportunity for an internal auditor, but it’s a fundamental part of their role. However, it is a shared responsibility within the organization, as a part of the overall corporate governance structure.
By actively addressing fraud risks and incorporating anti-fraud measures into their work, internal auditors can not only protect the organization but also demonstrate their role as strategic partners in safeguarding assets and promoting ethical business practices.
It should not be seen as a sole responsibility of the internal audit function. Everyone in the organization has a responsibility to prevent and detect fraud, from executives and board members to employees. The internal auditors help to establish and ensure the efficiency of this system.
https://www.researchgate.net/publication/235301198_The_internal_auditor_as_fraud-buster