
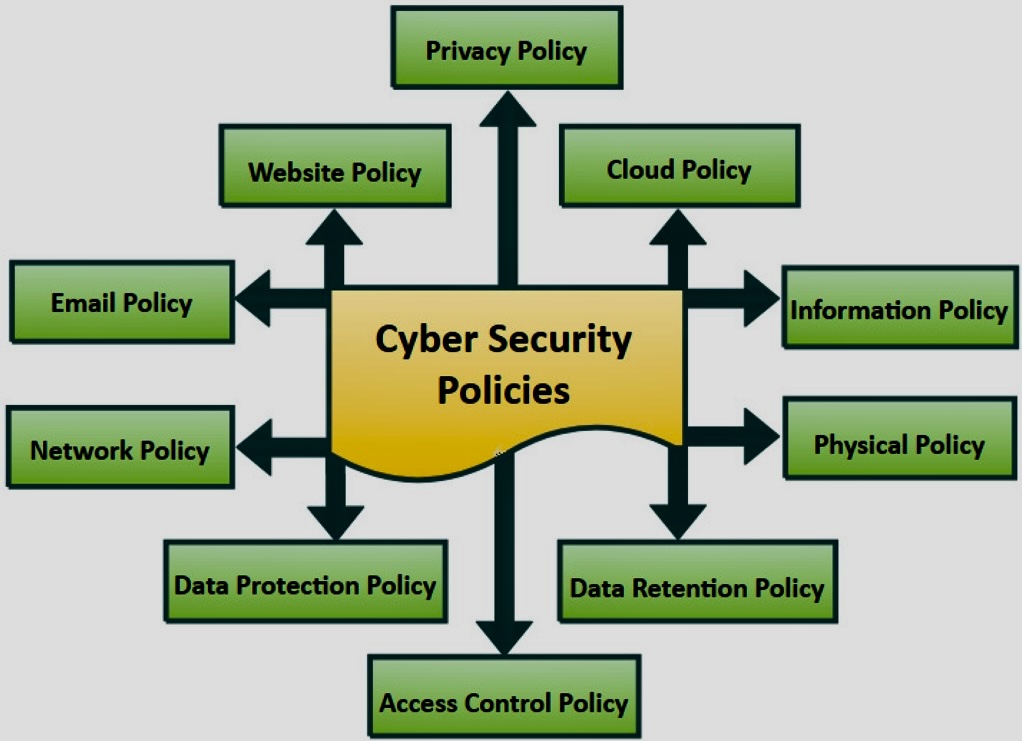
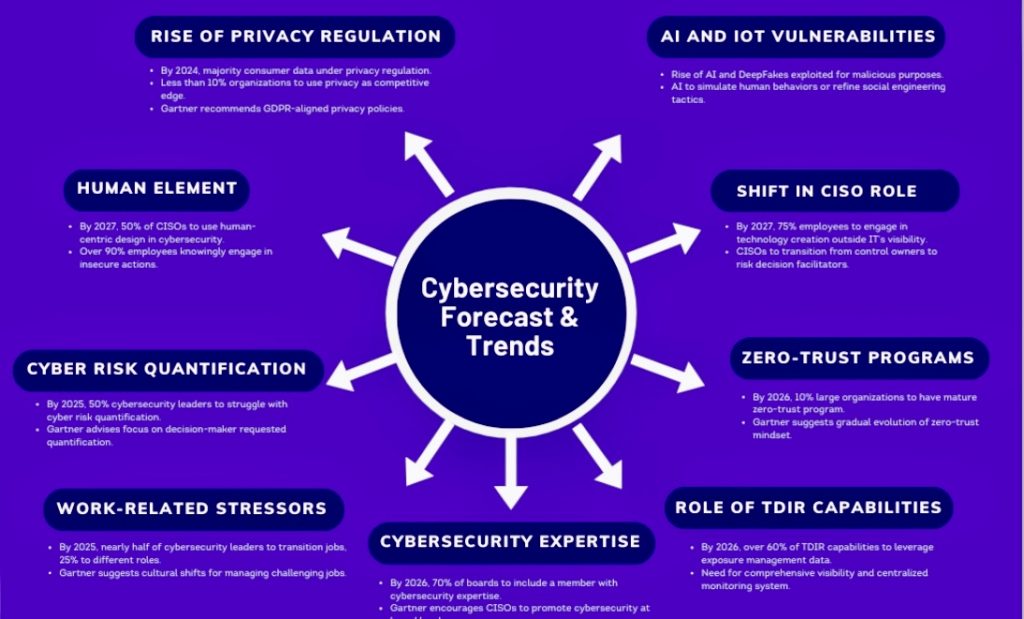
Some fundamental principles, or “laws”, of cybersecurity risk:
A. Law of Complexity: The more complex a system, the harder it is to secure. Complex systems offer more potential points of infiltration for attackers.
B. Law of Constant Risk: No system is entirely secure. Every system, even the most modern and sophisticated, is at constant risk of cyber attacks and requires ongoing protection.

C. Law of Evolving Threats: Cyber threats are constantly evolving as technology progresses. A security strategy must be adaptable and regularly updated to tackle these emerging threats.
D. Law of Exploitation: Given enough time and resources, any system vulnerability can and will be exploited by cybercriminals.
E. Law of Human Factor: The human element is consistently the most significant vulnerability in any cybersecurity framework. Regardless of technology advancements, human error or negligence can always lead to security breaches.
F. Law of Inevitability: Regardless of how robust your system’s security is, it’s not a question of ‘if’ a cyberattack will occur, but ‘when’.
G. Law of Insider Threat: Not all threats come from outside. Insiders (employees, vendors, etc.) can pose a serious risk, whether through malice or negligence.
H. Law of Internet Exposure: The more access points a system or network has to the internet, the greater the risk of a cybersecurity breach.
I. Law of Rapid Response: The efficiency and speed of detecting and resolving threats can make the difference between a minor incident and a major breach.
J. Law of Risk Transference: You can outsource many things, but not responsibility. Even if you outsource your data handling, you’re still responsible for its security.
K. Law of Risk vs Reward: The level of security measures taken should be proportionate to the potential damage a breach could cause. The consequences of not securing valuable data far outweigh the costs of implementing security measures.
L. Law of Speed: The faster a vulnerability is detected and patched, the less likely it becomes that an attacker will exploit it.
M. Law of Technology Limitation: Technology alone cannot fully protect a system from cybersecurity risks. A comprehensive approach including people, processes, and technology is required.
N. Law of Vulnerability: There is no completely secure system. Every system has vulnerabilities, and it’s a matter of time before a malicious party exploits them.
Each of these “laws” emphasizes the need for robust, continuous approaches to managing cybersecurity risk.
Each law underlines the need for a proactive, ongoing strategy for managing cybersecurity risk, as well as the inclusion of every aspect of an organization, from individuals to processes, in this strategy.
https://www.cybernx.com/b-10-laws-of-cyber-security-risks
https://www.linkedin.com/pulse/10-laws-cybersecurity-risk-you-cant?trk=public_post
https://www.knowledgehut.com/blog/security/principles-of-cyber-security
https://www.pwc.co.uk/issues/cyber-security-services/insights/governing-cyber-security-risk.html
