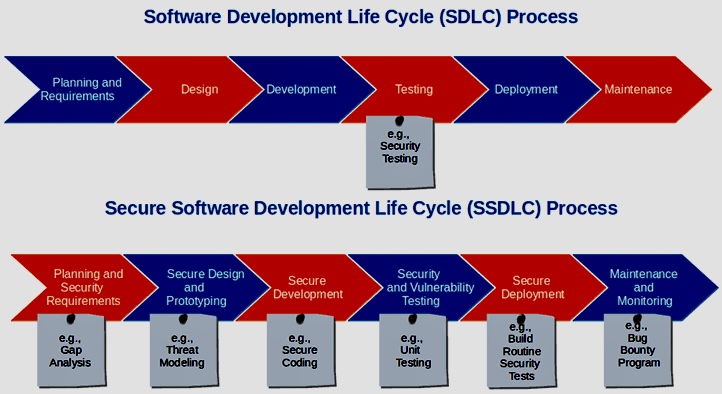
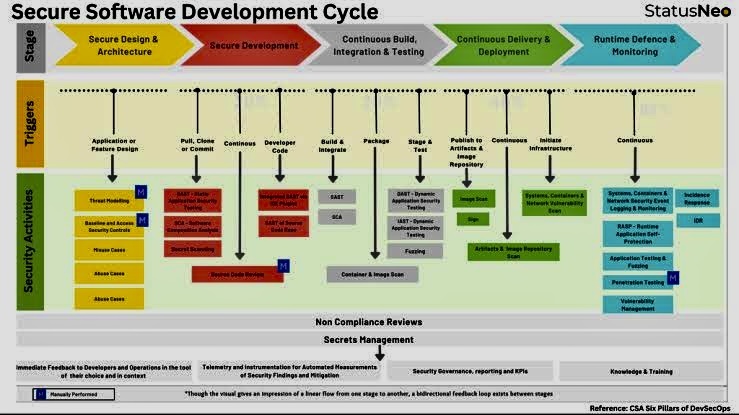
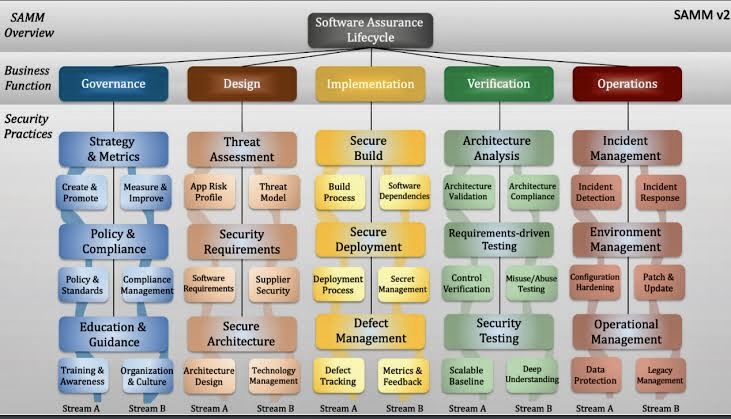
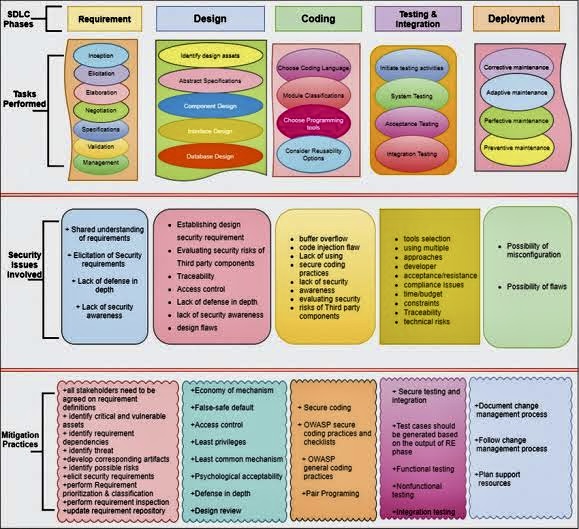
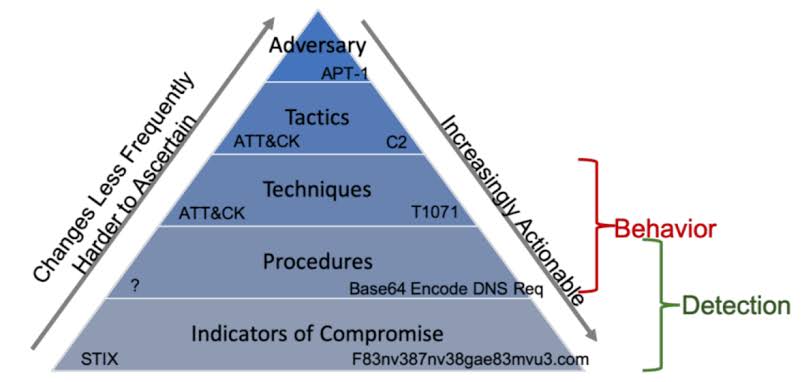
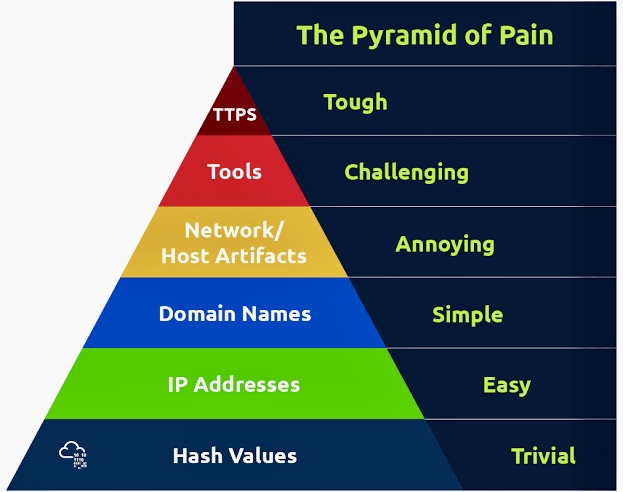
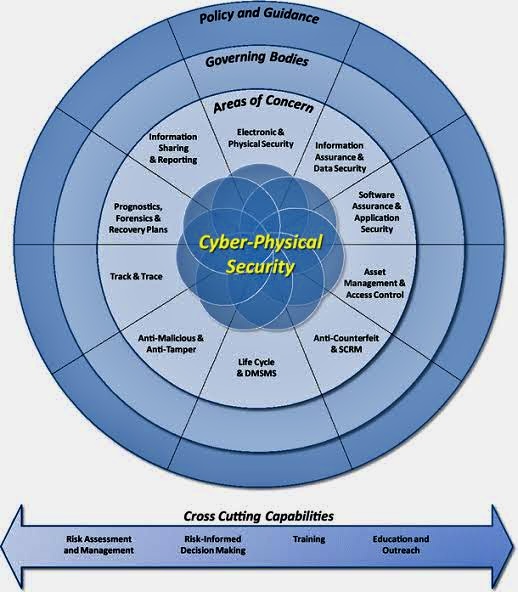
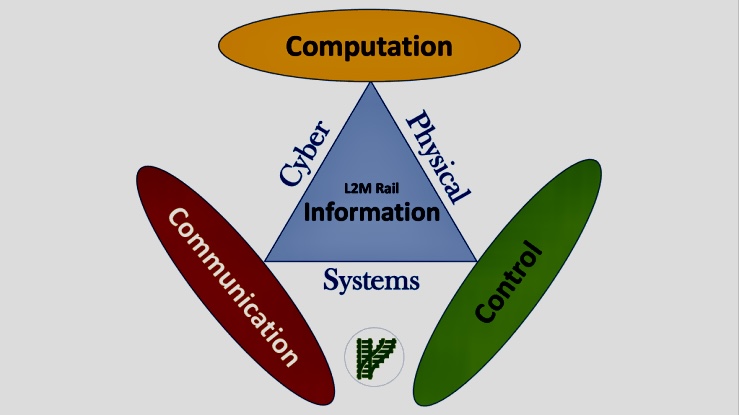
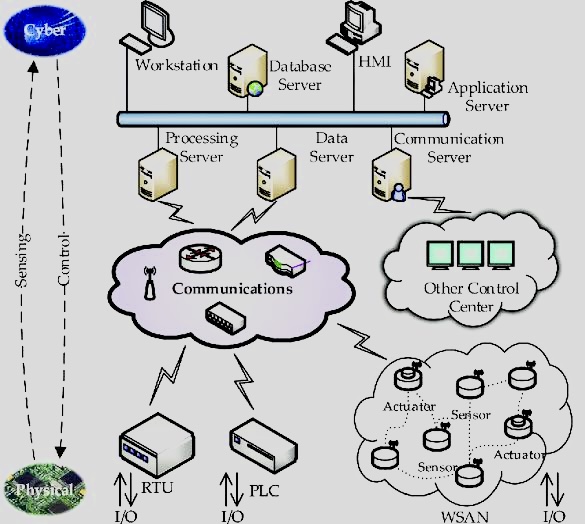
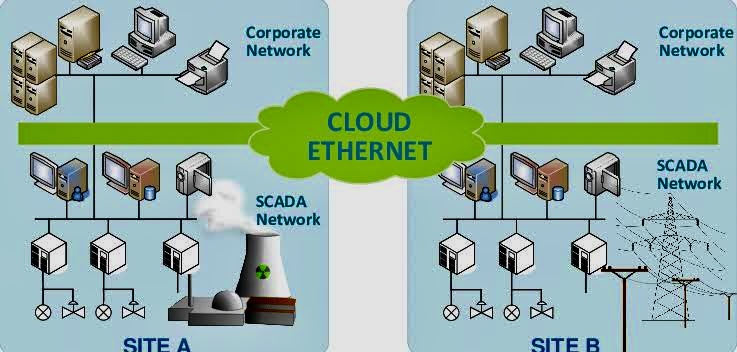
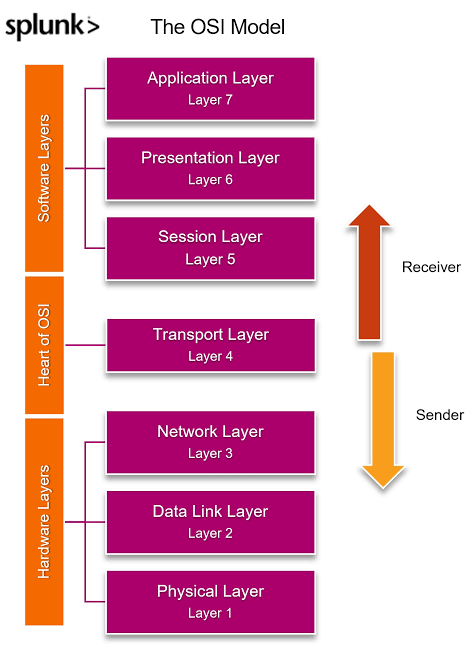
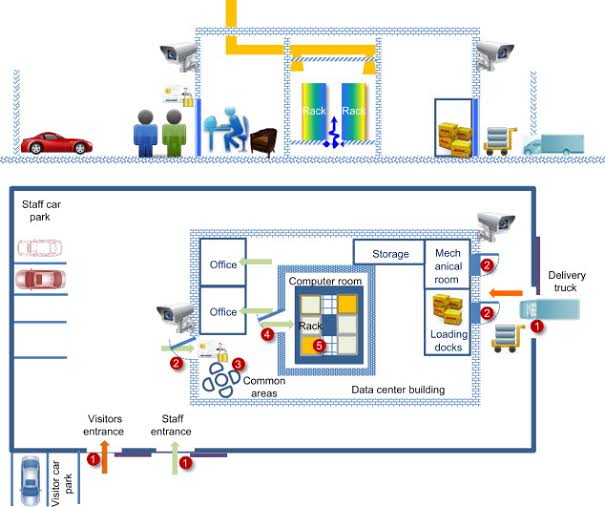
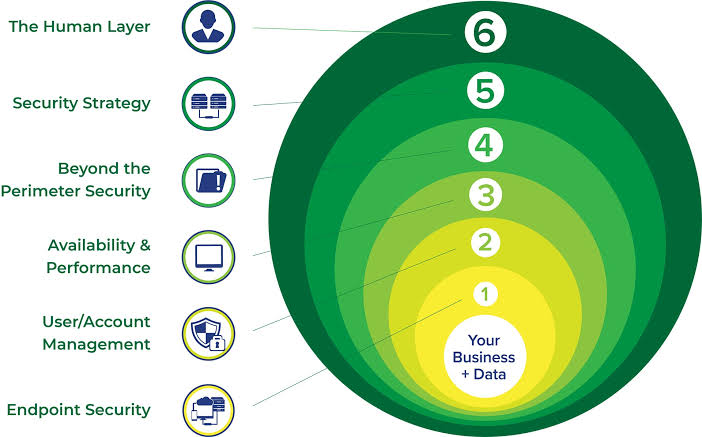
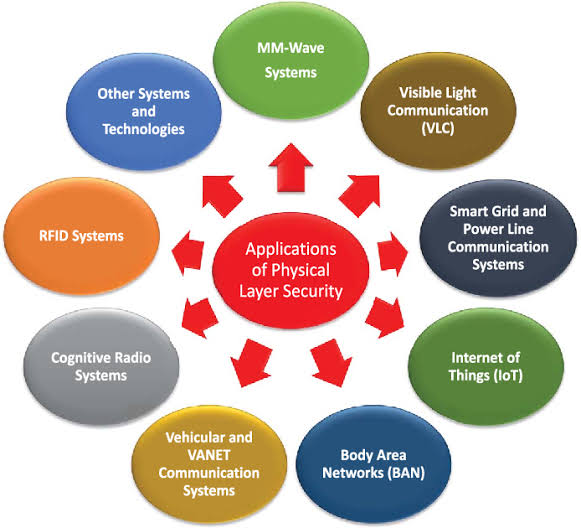
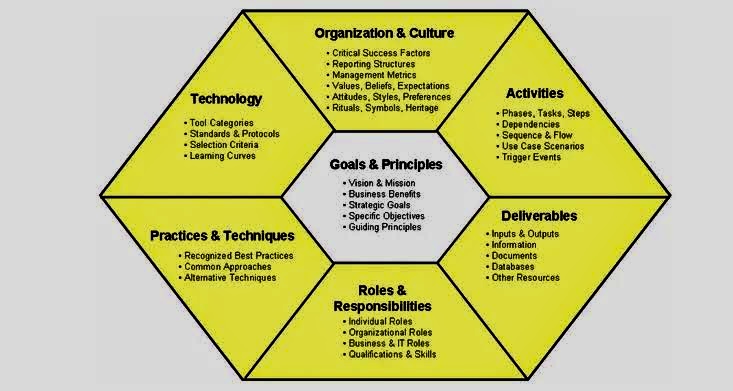
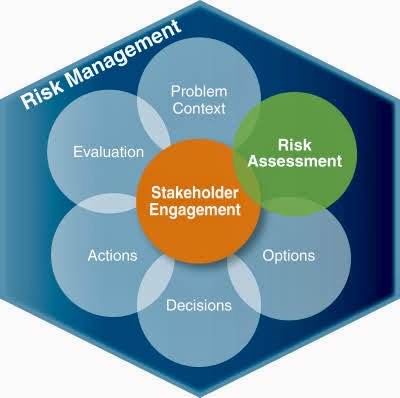
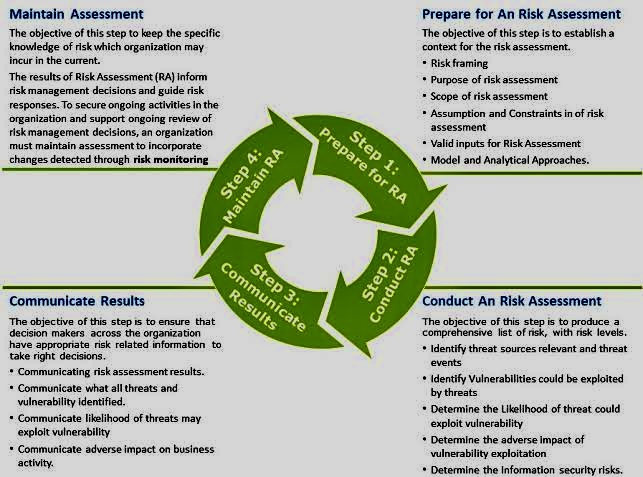
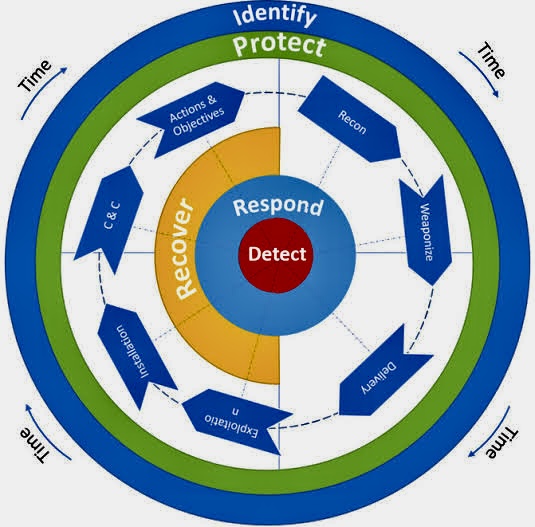
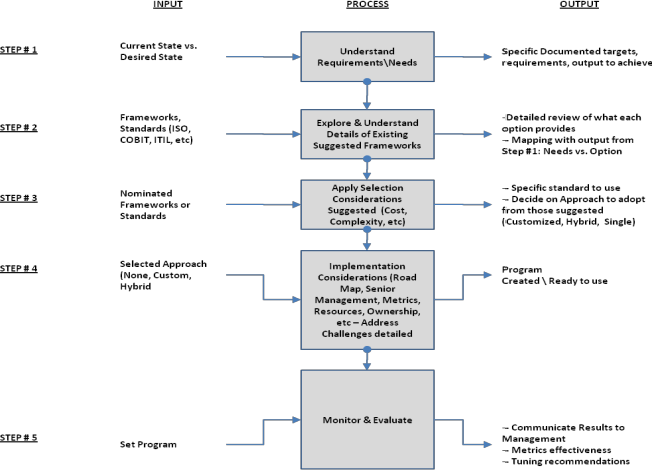
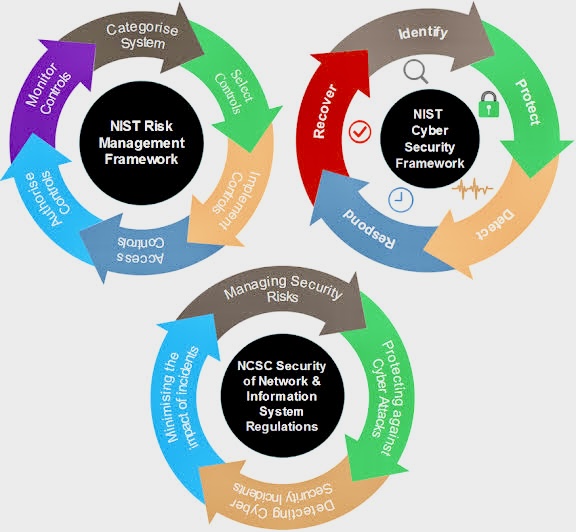
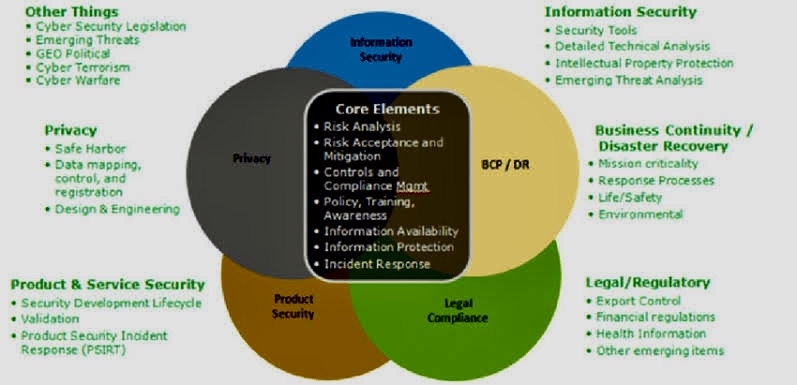
The use of Artificial Intelligence (AI) for Governance, Risk Management, and Compliance (GRC) is becoming increasingly relevant as organizations seek to manage their GRC-related activities more effectively.
By leveraging AI technologies, companies can enhance their capabilities in several GRC areas.
i. Here’s how AI can contribute to each aspect of GRC:
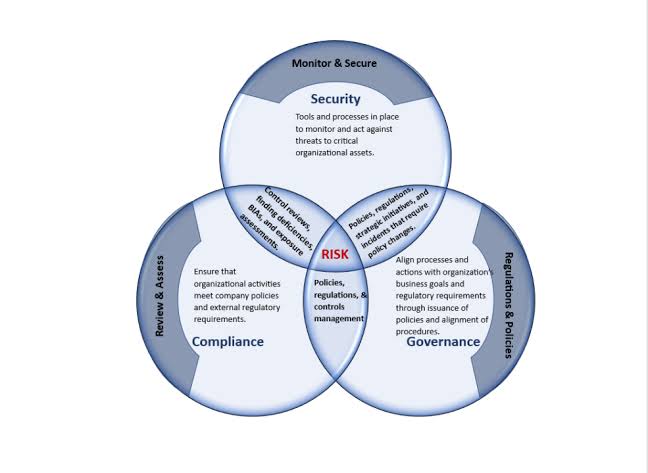
A. Governance:
a. Decision-Making: AI can analyze vast quantities of data to provide insights that assist in making more informed governance decisions.
b. Board Activities: AI tools can help in preparing reports and dashboards for board meetings, summarizing key information for more efficient executive oversight.
c. Policy Management: AI can help in automating the creation, management, and distribution of corporate policies and ensure they are up to date with current regulations and standards.
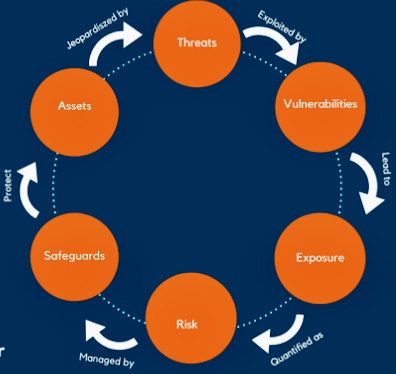
B. Risk Management:
a. Risk Identification: AI systems can continually monitor and analyze data points to identify potential risks before they become issues.
b. Risk Assessment: Advanced AI analytics can simulate various scenarios and their impacts, enhancing an organization’s risk assessment processes.
c. Risk Mitigation Strategies: AI can aid in developing effective risk mitigation strategies by predicting the outcomes of different approaches.
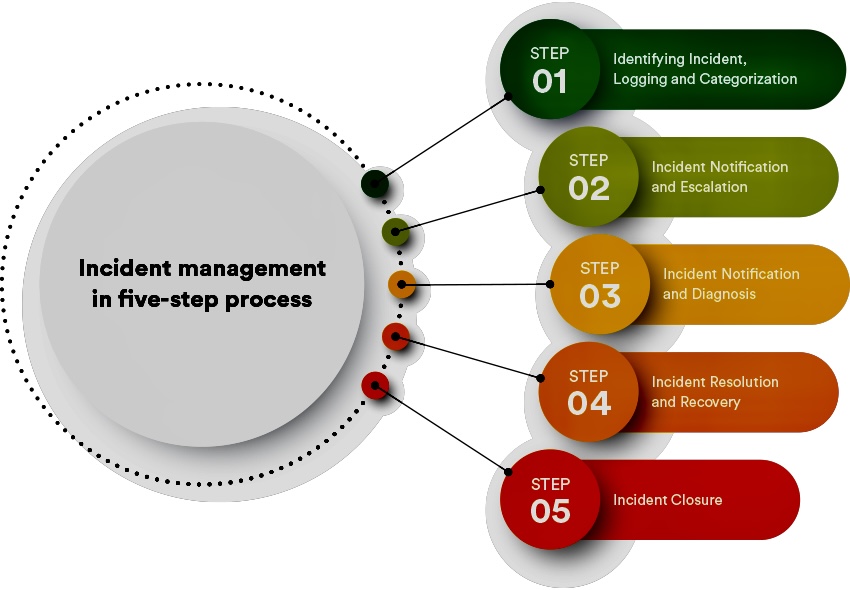
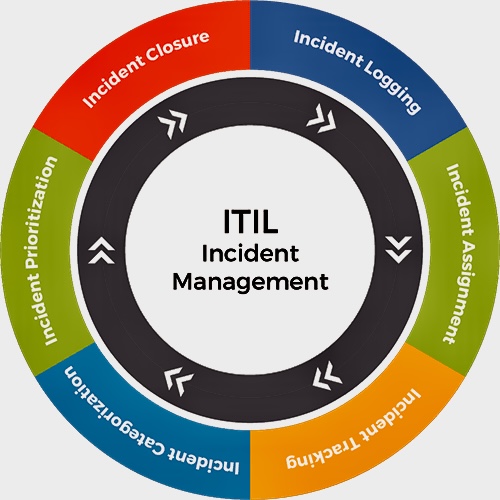
C. Compliance:
a. Through Natural Language Processing (NLP), AI can read and interpret complex regulatory documents, ensuring that organizations understand and align with any legal and regulatory requirements.
b. AI can generate automatic updates each time a change in regulations is processed, helping businesses stay updated with compliance requirements.
c. Regulatory Compliance: AI can keep track of regulatory changes and alert companies to relevant updates, ensuring that compliance measures are always up to date.
d. Monitoring & Reporting: AI tools can continuously monitor compliance controls and generate compliance reports, saving time and reducing human error.
e. Audit Processes: AI can streamline audit processes by automating data collection, flagging outliers, and providing detailed analytics to support audit findings.
D. Regulatory Change Management:
a. AI tools can monitor global regulations and notify businesses of relevant changes.
b. This assures that organizations can adapt swiftly to regulatory modifications, staying compliant efficiently without the need for constant manual scanning of regulatory updates.

E. Fraud Detection and Prevention:
a. AI’s pattern-recognition abilities can enhance fraud detection processes.
b. By examining large volumes of transactions in real-time, AI can identify unusual behavior or discrepancies, alerting the system to possible fraud and potentially saving a company from significant losses.
F. Data Protection and Privacy:
a. AI can help manage and protect data, an increasingly critical aspect of GRC as data regulations tighten.
b. By identifying sensitive data and monitoring how it’s used, AI can help maintain the appropriate data privacy protocols and prevent breaches.
G. Ethics and Compliance Training:
a. Personalized Training Programs: AI can create personalized training modules for employees based on their roles and the specific compliance risks they face.
H. Automating Reports:
a. AI can streamline data collection and automate report generation, reducing human error and improving time efficiency.
b. It provides the ability to monitor essential metrics continuously and generate real-time reports which aid in the decision-making process.
I. Policy Management:
a. AI can also assist in creating robust internal policies by collecting and analyzing data from varied sources, providing insights to formulate policies that are in line with best practices and accomplishing compliant growth.
J. Reduced Operational Costs:
a. Implementing AI can reduce the costs associated with manual labor, errors, non-compliance penalties,

K. Further Enhancements:
a. Automation of Manual Tasks: Many GRC tasks are repetitive and can be automated with AI, such as data collection and report generation.
b. Predictive Analytics: AI can provide predictive insights, allowing organizations to be proactive rather than reactive in their GRC efforts.
c. Enhanced Data Analysis: AI can process and make sense of unstructured data, such as legal documents and regulatory text, which is difficult and time-consuming for humans to analyze.
ii. Benefits of using AI for GRC:

o Increased efficiency: AI can automate many manual tasks, freeing up valuable time and resources for other activities.
o Improved accuracy: AI algorithms can analyze data much faster and more accurately than humans, leading to better risk assessments and compliance monitoring.
o Enhanced insights: AI can uncover hidden patterns and relationships in data that humans might miss, providing valuable insights for risk management, compliance, and governance decisions.
o Proactive approach: AI can predict potential risks and compliance issues before they occur, allowing organizations to take proactive measures to mitigate them.
o Reduced costs: By improving efficiency and effectiveness, AI can help organizations save money on GRC activities.
iii. Challenges of using AI for GRC:
o Data quality: AI models rely on high-quality data to be effective. Ensuring data accuracy and completeness is crucial.
o Transparency and explainability: AI algorithms can be complex and opaque, making it difficult to understand how they reach their conclusions. Transparency and explainability are important for building trust in AI-powered GRC solutions.
o Ethical considerations: Bias in data and algorithms can lead to unfair or discriminatory outcomes. Responsible use of AI in GRC is essential.
While AI can significantly improve GRC processes, it is important to handle it with care. Issues like data privacy, ethical considerations, and ensuring that AI systems are transparent and accountable must be addressed.
Additionally, while AI can provide recommendations and predictions, the ultimate decision-making responsibility lies with human managers and leaders, who must interpret and act on AI insights within the context of their organization’s culture, values, and strategies.
In conclusion, the integration of AI in GRC brings transformative benefits, from automating compliance tasks to enhancing risk prediction and streamlining processes.
As organizations navigate an ever-evolving regulatory landscape, leveraging AI technologies can provide a strategic advantage in achieving effective governance, managing risks proactively, and maintaining compliance with confidence.

https://www.oceg.org/the-rise-of-ai-in-grc-are-you-prepared/