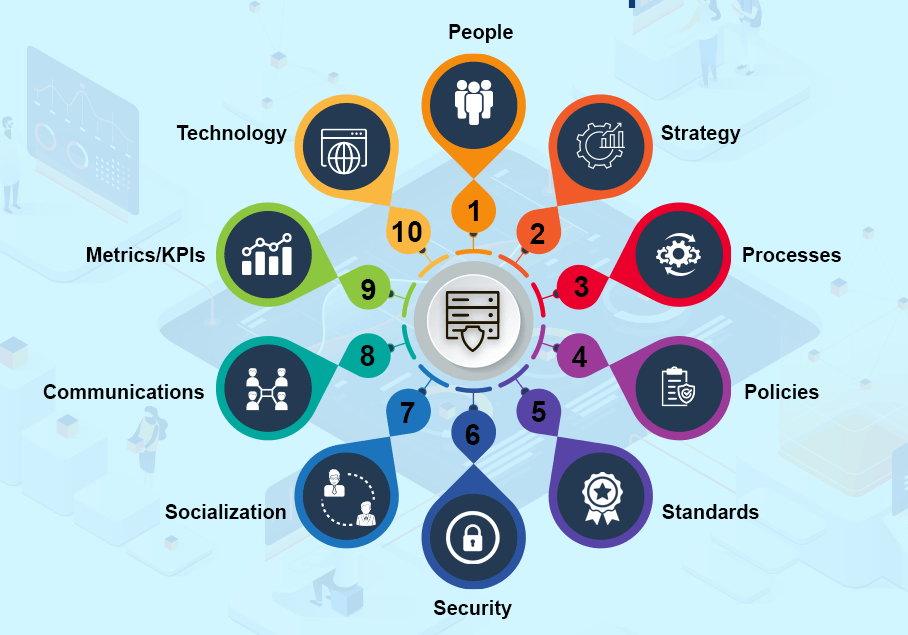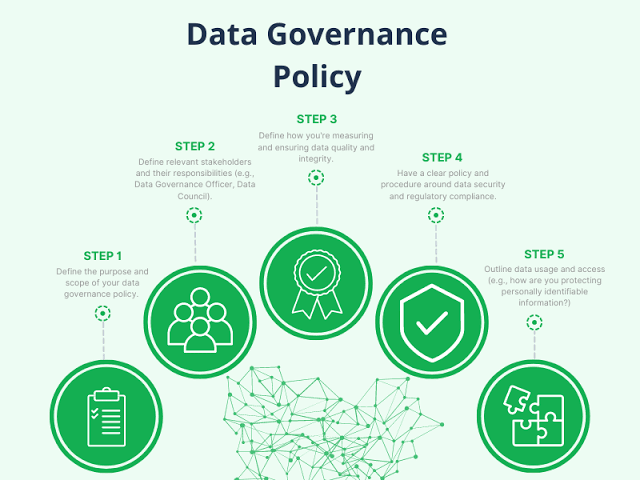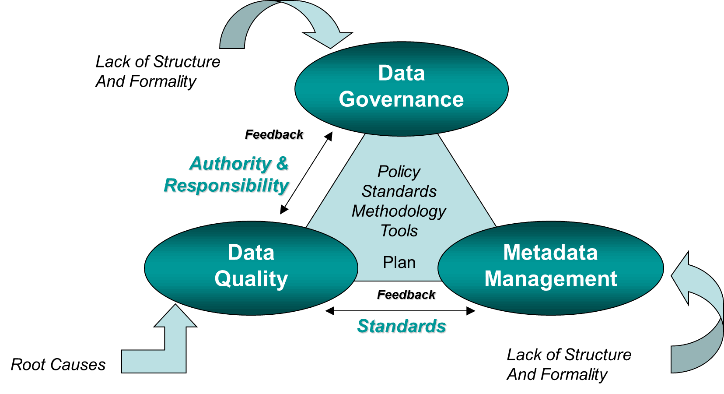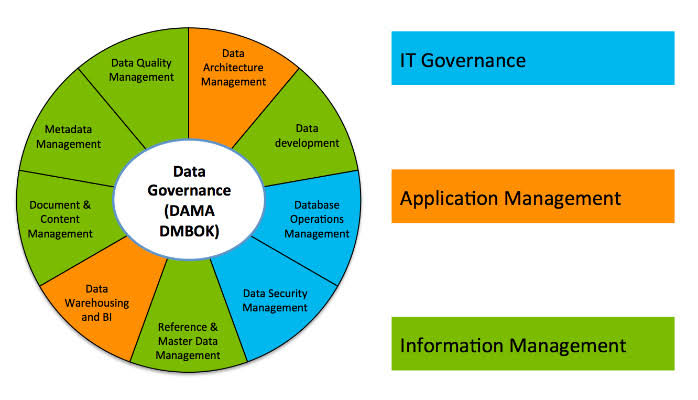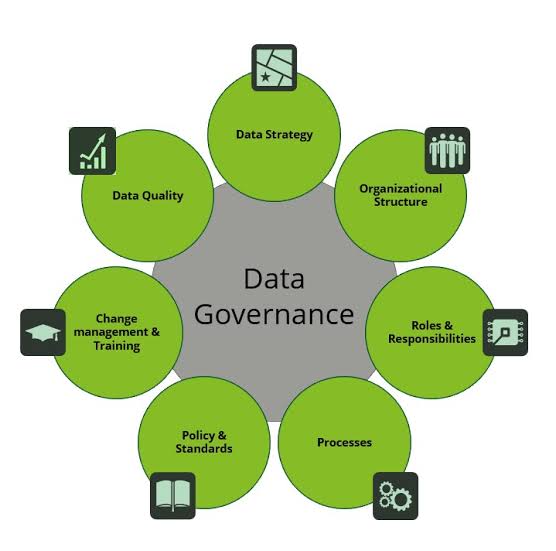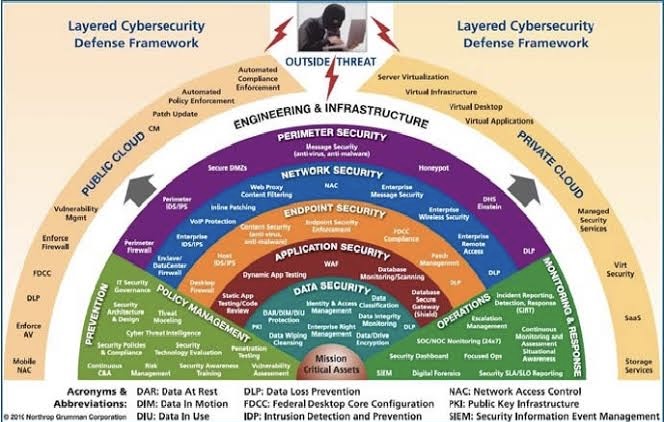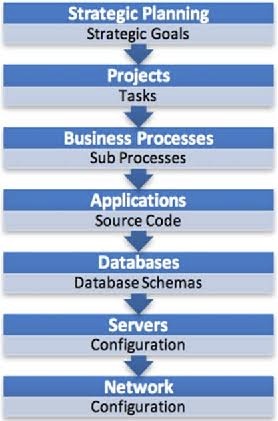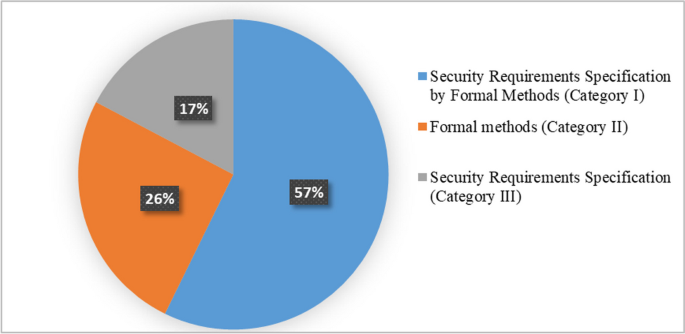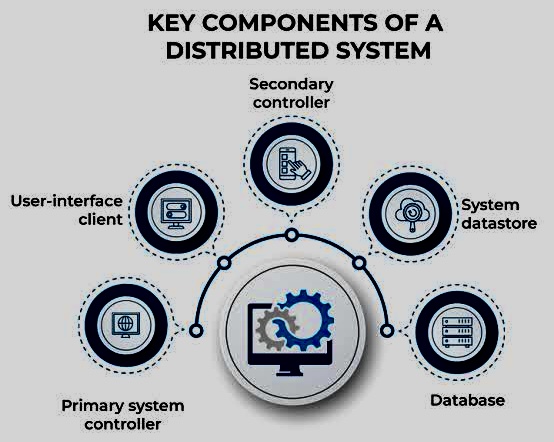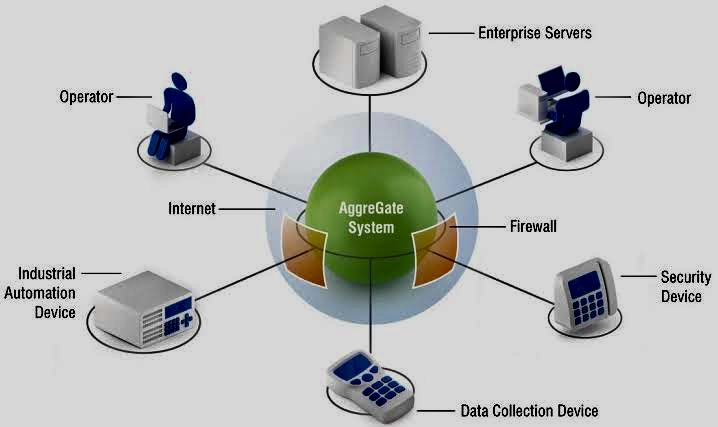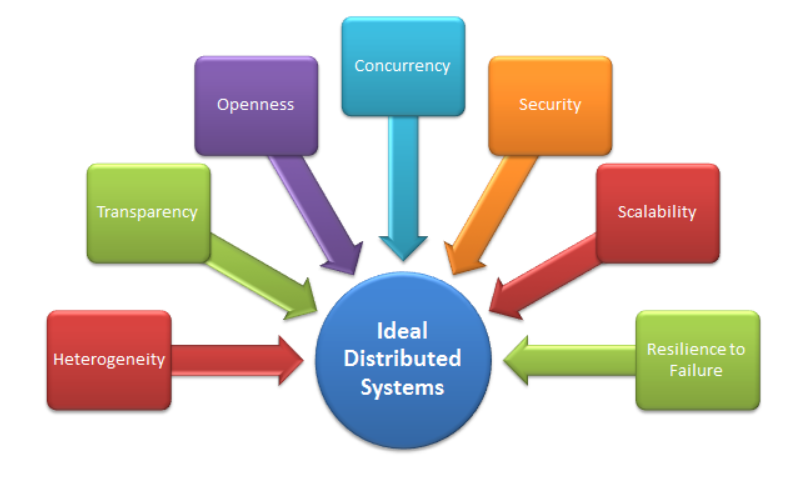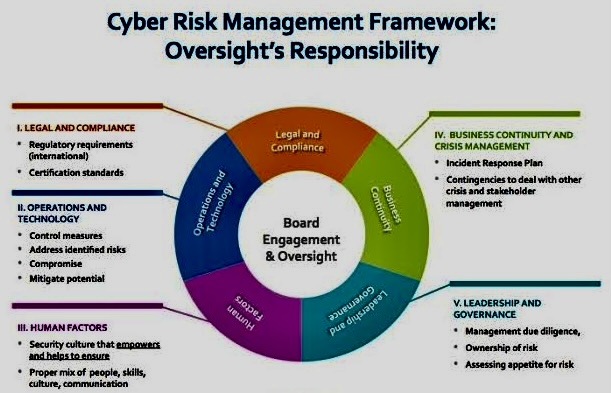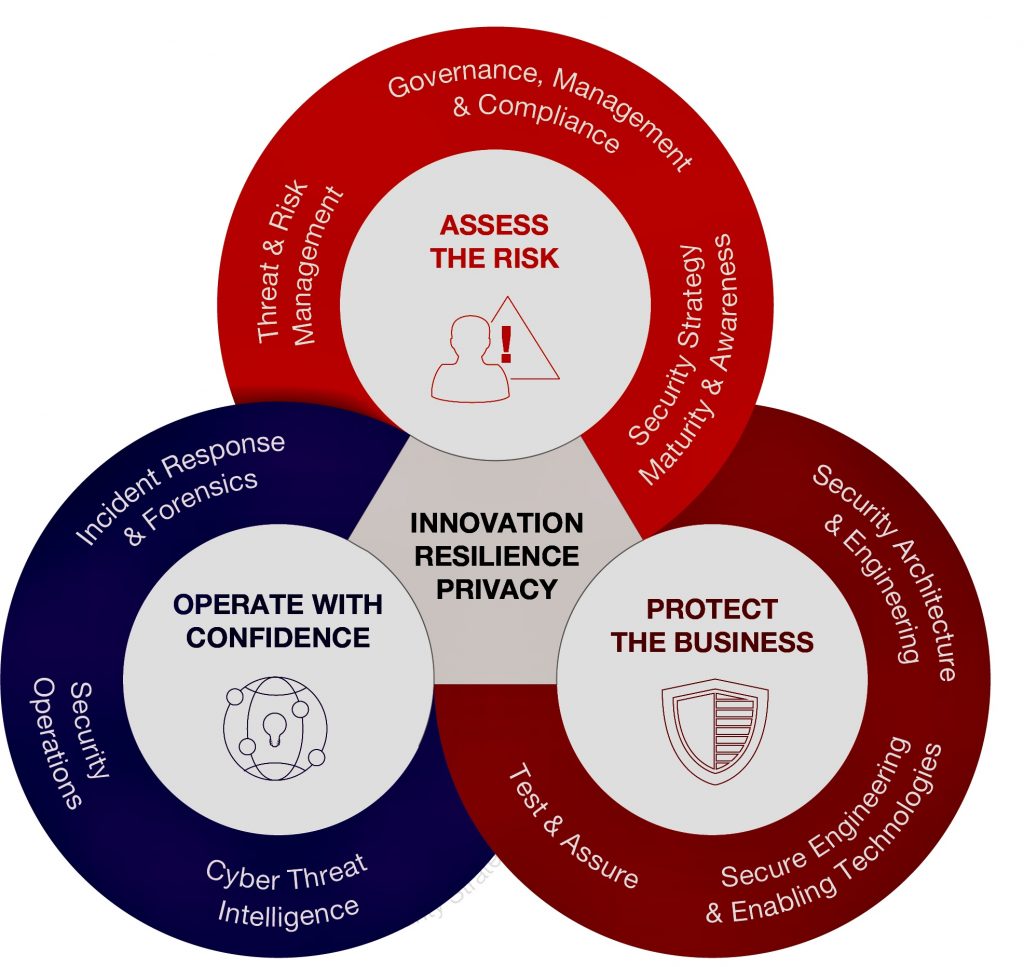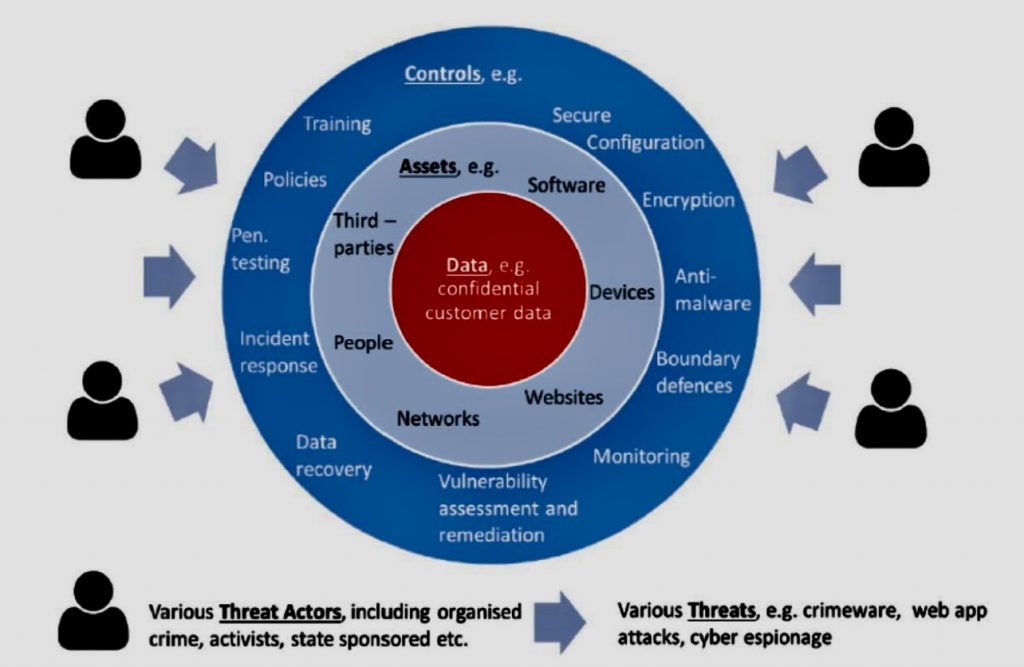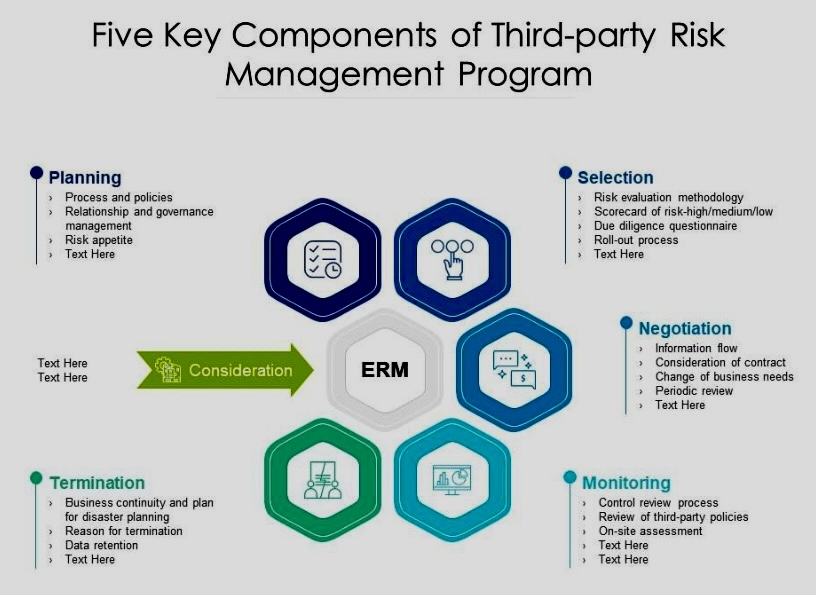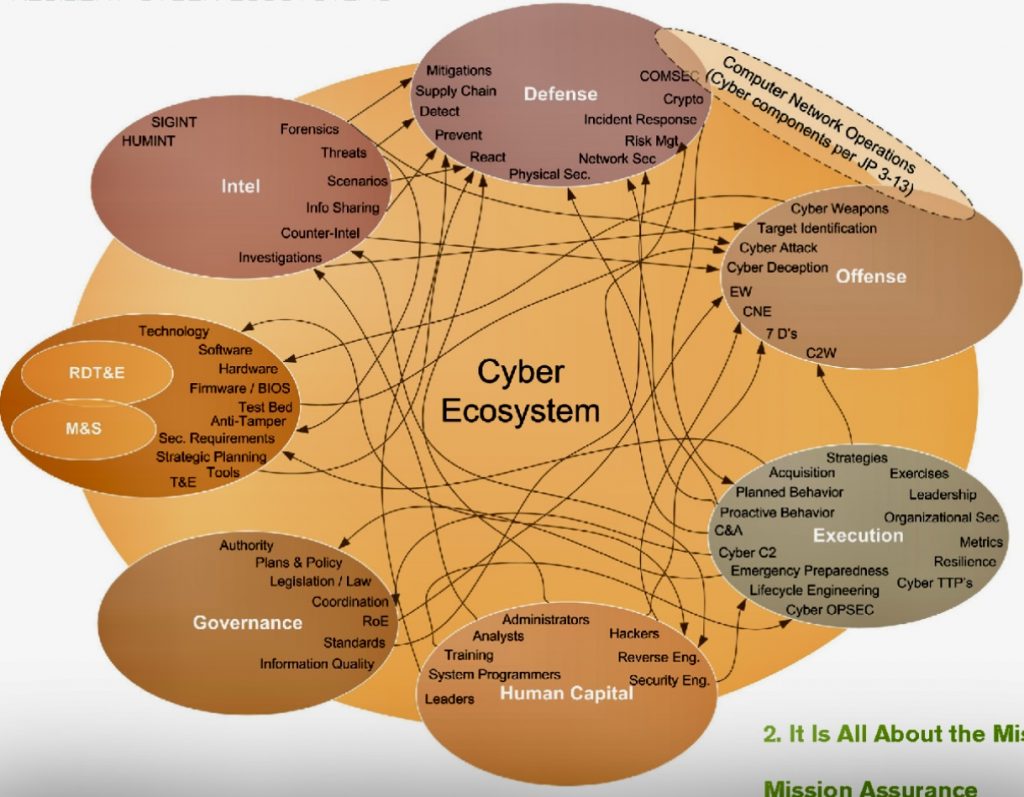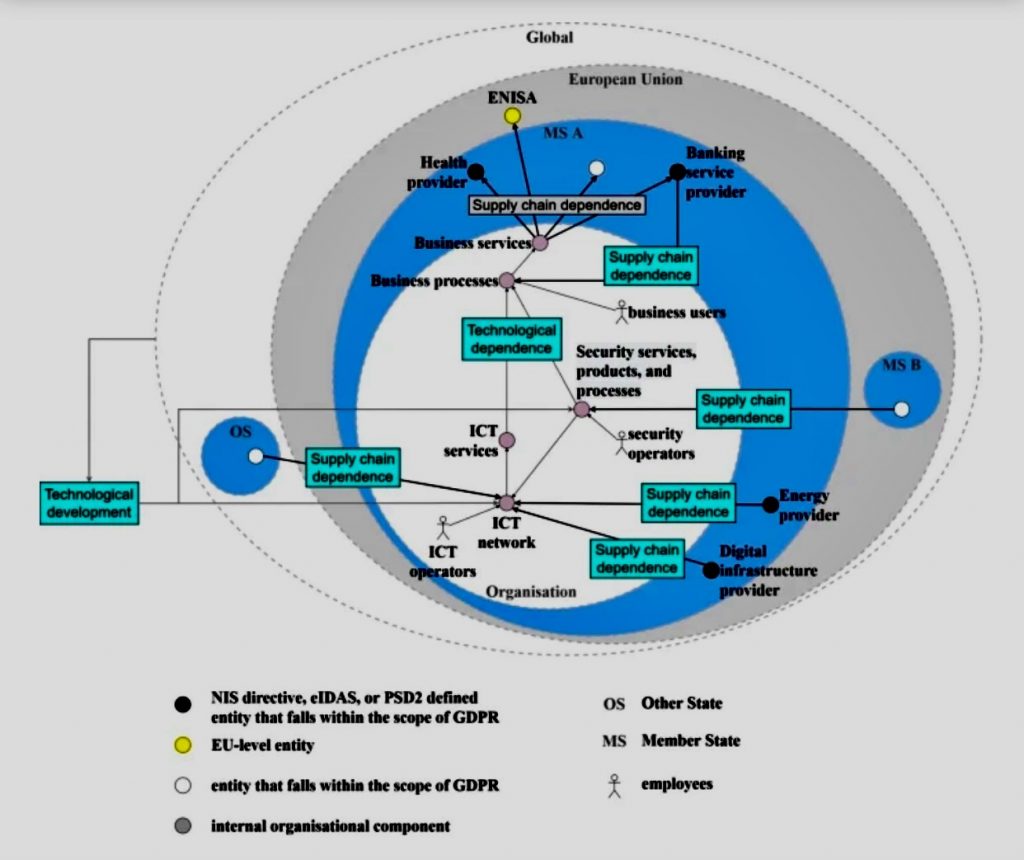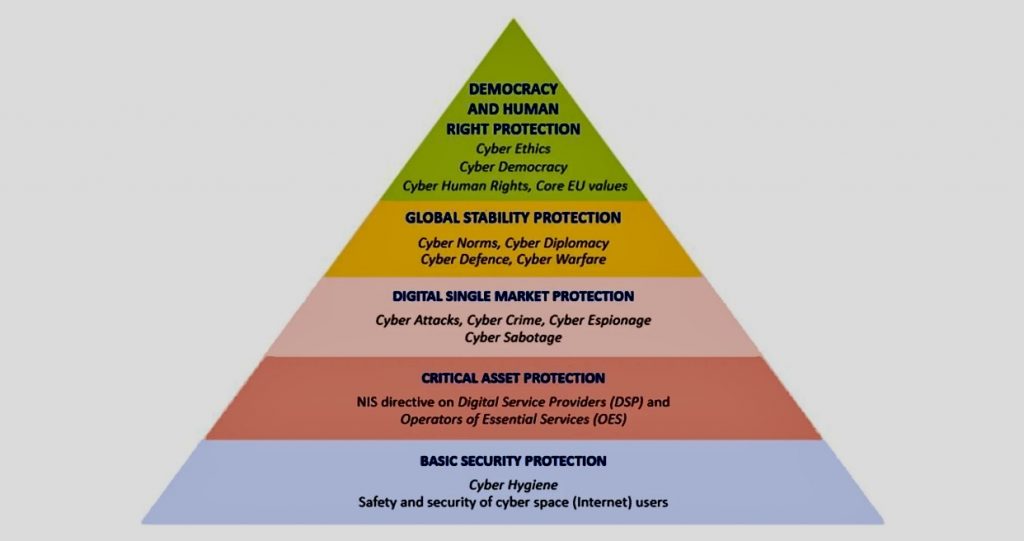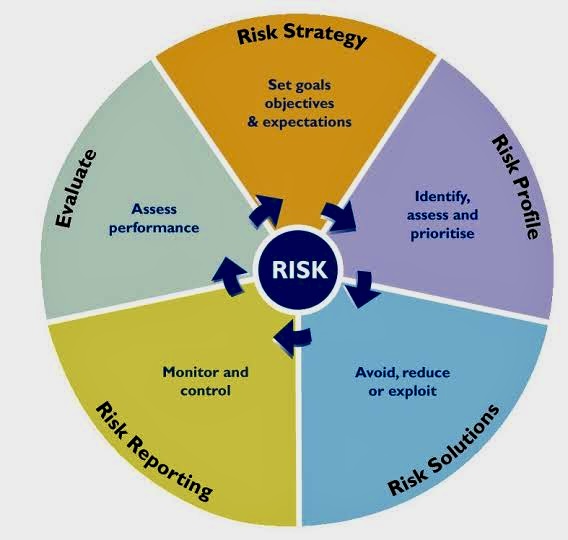
When faced with risk management problems with no apparent solutions, creative thinking and a structured approach are crucial.
i. High level approach
A. Reframe the problem:
o Shift perspective: Look at the problem from different angles. Are you focusing on the symptoms or the root cause? Can you break down the problem into smaller, more manageable parts?
o Challenge assumptions: Don’t take existing solutions or limitations for granted. Question your own biases and consider alternative approaches.
o Consider unintended consequences: What are the potential drawbacks of the obvious solutions? Are there hidden costs or risks associated with them?
B. Gather information and insights:
o Seek diverse perspectives: Consult with people from different backgrounds and disciplines. Experts outside your field may offer fresh ideas.
o Research existing solutions: Look for similar problems in other industries or domains. Have they developed innovative approaches that can be adapted?
o Explore emerging technologies: Can new technologies offer novel solutions to your problem? Stay informed about advancements in relevant fields.
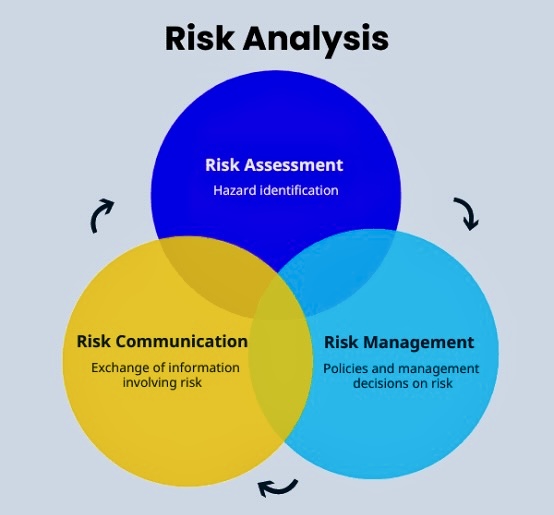
C. Generate and evaluate options:
o Brainstorming: Encourage creative and unconventional ideas. Don’t censor any suggestions at this stage.
o Scenario planning: Explore various potential outcomes based on different courses of action.
o Cost-benefit analysis: Weigh the potential benefits of each option against the associated risks and costs.
o Prioritize and iterate: Don’t be afraid to experiment and adapt your approach as you learn more.
D. Implement and monitor:
o Develop a clear action plan: Define specific tasks, timelines, and responsibilities for implementing your chosen solution.
o Communicate effectively: Keep stakeholders informed about your progress and address any concerns they might have.
o Monitor and adapt: Be prepared to adjust your approach based on new information or unexpected outcomes.
ii. Detailed process steps and approaches
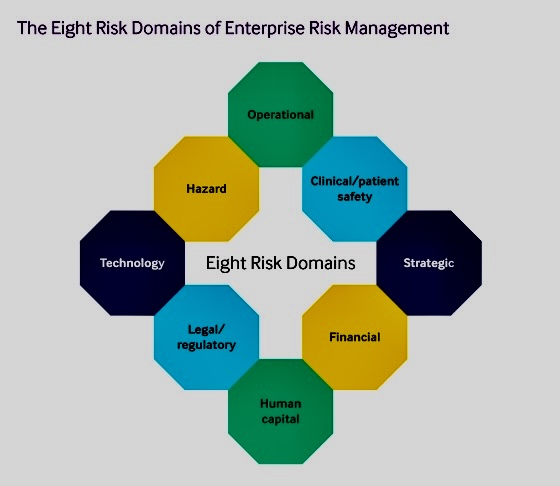
A. Holistic Assessment:
o Approach: Conduct a thorough and holistic assessment of the risk landscape.
o Objective: Gain a comprehensive understanding of the context, potential risks, and their interdependencies to identify nuanced solutions.
B. Identify All Risks:
o Approach: Begin with as detailed a risk identification process as possible.
o Objective: You cannot manage unidentified risks, so use brainstorming, stakeholder interviews, and expert consultation to compile a comprehensive list.
C. Risk Analysis:
o Approach: Analyze each risk to understand its potential impact and the likelihood of it occurring.
o Objective: This will help in prioritizing the risks that need urgent attention. Qualitative and quantitative assessments can be useful here.
D. Scenario Planning:
o Approach: Develop various scenarios to explore potential outcomes and responses.
o Objective: Anticipating different scenarios helps in devising flexible strategies and adaptive risk management plans.
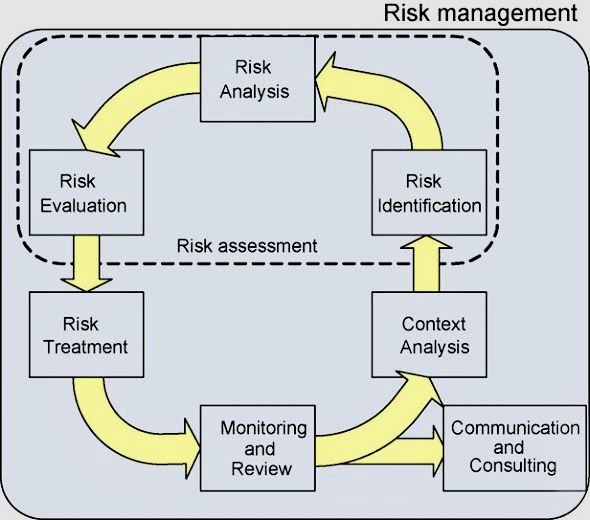
E. Creative Problem-Solving:
o Approach: Invite diverse perspectives from team members with different backgrounds to brainstorm solutions.
o Objective: Diversity in thought can lead to innovative ways of addressing the problem.
F. Expert Collaboration:
o Approach: Engage subject matter experts, both internal and external.
o Objective: Leverage diverse perspectives and expertise to generate innovative solutions and insights.
G. Risk Modeling and Simulation:
o Approach: Utilize risk modeling and simulation tools.
o Objective: Simulations can help visualize the impact of various risk mitigation strategies and inform decision-making.
H. Adaptive and Flexible Strategies:
o Approach: In some cases, no single solution may be available, necessitating the use of multiple strategies deployed over time.
o Objective: These strategies should be adaptable as the situation changes.
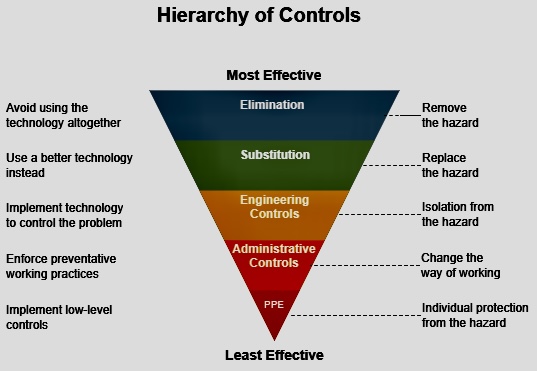
I. Contingency Planning:
o Approach: Develop contingency plans for risks that cannot be solved immediately.
o Objective: These are “Plan B” options you can implement if a risk materializes.
J. Cross-Functional Collaboration:
o Approach: Foster collaboration across different departments and teams.
o Objective: Diverse input can lead to creative problem-solving and a more comprehensive understanding of potential solutions.
K. Continuous Monitoring and Adaptive Strategies:
o Approach: Implement continuous monitoring of risk factors and adjust strategies as needed.
o Objective: Enables real-time adaptation to emerging risks and changing circumstances.
L. Red Team Exercises:
o Approach: Conduct red team exercises to simulate adversarial perspectives.
o Objective: Identifies vulnerabilities and challenges assumptions, leading to more robust risk management strategies.
M. Learning from Past Incidents:
o Approach: Analyze past incidents and failures.
o Objective: Extract lessons learned to inform future risk management approaches and improve resilience.
N. Ethical Considerations:
o Approach: Consider the ethical implications of risk management decisions.
o Objective: Ensures that risk mitigation strategies align with ethical standards and organizational values.
O. Regulatory Compliance Review:
o Approach: Ensure compliance with relevant regulations.
o Objective: Understanding regulatory requirements helps shape risk management strategies and avoids legal issues.
P. Innovative Technologies:
o Approach: Explore the use of innovative technologies.
o Objective: Technologies like AI, machine learning, and advanced analytics can offer new insights and solutions in risk management.
Q. Iterative Problem-Solving:
o Approach: Adopt an iterative approach to problem-solving.
o Objective: Break down the problem into manageable parts, address them incrementally, and refine strategies based on ongoing feedback.
R. External Consultation:
o Approach: Seek advice from external consultants or industry peers.
o Objective: External perspectives can provide fresh insights and alternative viewpoints.
S. Risk Transfer:
o Approach: In some cases, risks can be transferred to a third party; for instance, through insurance or outsourcing.
T. Mitigation Measures:
o Approach: For risks that cannot be eliminated, determine what actions can reduce either the likelihood of the event occurring or the impact if it does occur.
U. Acceptance:
o Approach: For some risks, the best “solution” may be to accept them. This is typically for risks that are unlikely to occur, or have a minor impact that can be absorbed by the project.
V. Continuous Monitoring:
o Approach: Often, risks evolve with time. Regular monitoring can help you spot when a risk’s likelihood or impact changes, signaling the need for different management strategies.
W. Communication:
o Approach: Maintain open lines of communication with all stakeholders. Informing them about risks and potential solutions can lead to support and additional ideas.
X. Education and Training:
o Approach: Provide team members with training to better understand risk management processes and sharpen their problem-solving skills.
Y. Document Lessons Learned:
o Approach: Keep records of how risks were managed (successfully or not), to inform future projects or when similar issues arise.
Z. Iterative Approach:
o Approach: Risk management is not a one-time task. An iterative approach, regularly revisiting and reassessing risks, ensures that new solutions can be identified as circumstances change.
There is rarely a single “correct” answer in risk management. By employing these strategies and fostering a culture of innovation, you can effectively navigate complex problems and find creative solutions even when the path forward seems unclear.
These strategies can help in finding solutions or at least in managing the situation in a way that minimizes the negative impact on the organization or project.
Risk management is not always about finding a clear-cut solution but rather about managing the uncertainty as effectively as possible.
https://www.adlittle.com/en/insights/viewpoints/reinvigorating-enterprise-risk-management
https://www.linkedin.com/advice/3/how-can-you-solve-problems-risk-management-when-60ihe