Evaluating Privileged Access Rights: A Risk-Based Approach to Categorizing Permissions by Type and Impact
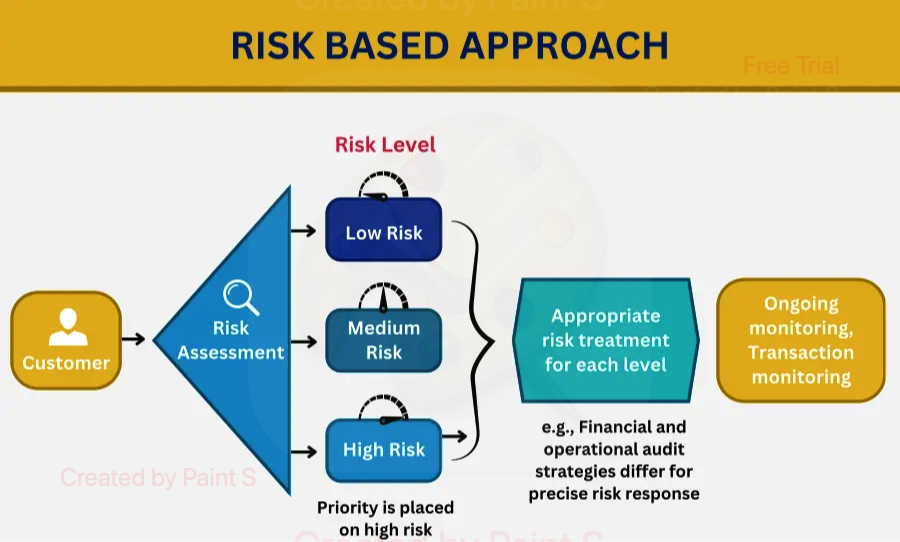
In today’s complex security landscape, effectively managing privileged access rights is essential to protecting an organization’s sensitive data and infrastructure. A risk-based assessment approach helps organizations identify and prioritize risks linked to various types of access permissions.
By categorizing permissions based on their type and potential impact, security teams can better allocate resources and implement controls to mitigate high-risk access. This approach not only strengthens security but also ensures that privileged access is granted and monitored according to its actual risk, reducing the chances of unauthorized use or exploitation.
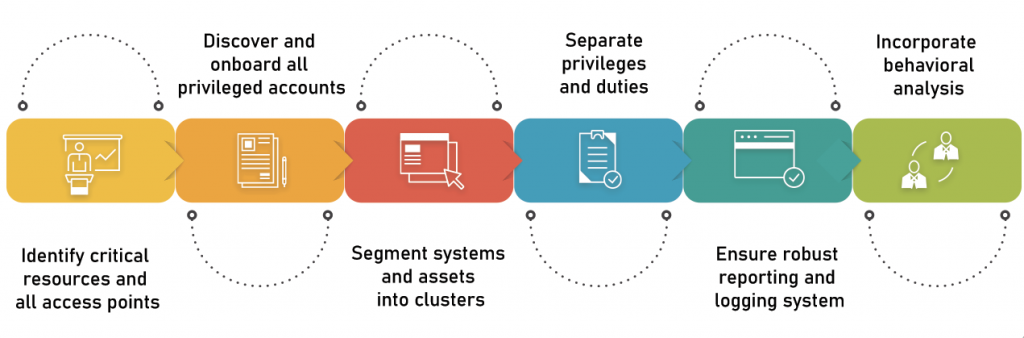
A key element of a comprehensive risk-based assessment model is distinguishing between different types of privileged access rights. Each type of permission carries its own level of risk, and not all privileged access is equally risky.
Let’s break down how you might distinguish between privileged access rights based on specific types of permissions:
Types of Permissions and Privileged Access:
- Administrative Control Rights:
- System Administrator Access: This is typically the highest level of privilege, where a user has full control over the system, including the ability to modify configurations, manage users, install software, and make system-wide changes. This type of access poses the greatest risk and must be subject to strict control and monitoring.
- Network Administrator Access: Similar to system admin access, network administrators can configure and control network devices (routers, switches, firewalls). This access is critical for maintaining security and operational integrity and is considered high-risk due to the potential to disrupt network operations.
- Data Access Permissions:
- Read-Only Privilege: Access to view sensitive data without the ability to modify or delete it is still considered privileged but poses a lower risk compared to write or execute privileges. This access is common in scenarios where users need to analyze or audit information but don’t require editing capabilities.
- Read/Write/Modify Privilege: Access to alter or modify sensitive data (e.g., financial records, HR data, customer information) significantly increases the risk of data integrity and privacy violations. These permissions require additional oversight to prevent misuse or unauthorized changes.
- Delete/Destroy Data: Permissions that allow users to delete critical data pose the highest risk, as they could lead to irrecoverable loss. This should be categorized as a highly privileged access right.
- Security and Audit Privileges:
- Audit Log Access: Access to view and manage security logs can be classified as privileged since it may allow users to conceal unauthorized activities by deleting or altering audit trails. This requires close monitoring, as tampering with logs can hinder security investigations.
- Security Policy Management: Users who can configure or alter security settings (e.g., firewall rules, encryption keys, access control policies) hold highly privileged roles. Their actions can directly affect the organization’s security posture.
- Escalation and Override Rights:
- Privilege Escalation: Some accounts have the ability to grant themselves or others additional permissions (e.g., temporarily elevating their own access to an administrative level). This ability to escalate privileges poses a significant risk and should be strictly controlled.
- Override/Bypass Security Controls: Access to disable or bypass critical security mechanisms (e.g., antivirus, DLP, encryption) should be considered highly privileged as it exposes systems to potential compromise.
Risk-Based Distinction by Type of Privilege:
When designing the risk-based assessment, the model should assign different risk weights to these types of permissions:
- Administrative controls would carry the highest risk, due to the potential for widespread system impact.
- Data modification permissions would carry moderate to high risk, depending on the sensitivity of the data.
- Read-only permissions would be assessed as lower risk, as they do not allow users to alter or manipulate data but could still lead to data leakage if exposed.
- Security management and privilege escalation should be assessed as high-risk, due to the potential to undermine security mechanisms.
Scoring Privileged Access Based on Permission Type:
Each type of permission should be integrated into your risk-scoring model as part of the overall assessment:
- Control Privileges: High-risk score (e.g., 5/5)
- Modification Privileges: Moderate to high-risk score (e.g., 3-4/5)
- Read-Only Privileges: Low to moderate risk score (e.g., 2/5)
- Escalation/Override Rights: High-risk score (e.g., 5/5)
The assessment model should consider not just the role or account type, but also the nature of the permission granted to the user. By evaluating these different permission levels, you can more effectively determine which access rights are truly privileged and require heightened security measures and scrutiny.
Conclusion:
In conclusion, managing privileged access rights is a critical component of safeguarding an organization’s sensitive data and infrastructure in today’s complex security environment. Adopting a risk-based assessment approach enables organizations to identify and address risks associated with different access permissions more effectively.
By classifying permissions based on their potential impact, security teams can prioritize high-risk areas, implement targeted controls, and ensure that access is monitored according to its true risk level. This strategy not only fortifies the organization’s security posture but also minimizes the potential for unauthorized access or misuse of critical systems.