
ISO/IEC 27005 and Risk Management in Enterprise Networks: A Crucial Partnership
Enterprise networks, complex ecosystems of hardware, software, and data, are vital to any organization’s operations.
But with increased dependence comes heightened vulnerability. ISO/IEC 27005, a globally recognized standard for information security risk management, plays a crucial role in safeguarding these networks by providing a framework for identifying, assessing, and mitigating potential threats.
i. The Intertwined Threads

Here’s how ISO/IEC 27005 relates to risk management within enterprise networks:
A. Formalizing and Standardizing the Process:
Before ISO/IEC 27005, enterprise network risk management could be haphazard, lacking structure and consistency. The standard introduces a systematic approach, outlining steps for:
o Identifying Assets: Classifying network components and data (servers, routers, financial records, etc.) based on their criticality.
o Identifying Threats and Vulnerabilities: Analyzing potential security breaches, from malware attacks to human error.
o Assessing Risk: Determining the likelihood and impact of identified threats, assigning risk scores to prioritize mitigation efforts.
o Selecting and Implementing Controls: Establishing security measures (firewalls, access controls, awareness training) to address identified risks.
o Monitoring and Continuous Improvement: Regularly reviewing and updating risk assessments and controls to adapt to evolving threats.
B. Minimum Baseline Controls for Network Security:
ISO/IEC 27005 doesn’t just provide a framework; it prescribes minimum baseline controls that address common network security vulnerabilities. These controls encompass physical security, access control, encryption, software security, incident management, and more. Implementing these controls ensures a secure foundation for any enterprise network, regardless of its size or complexity.
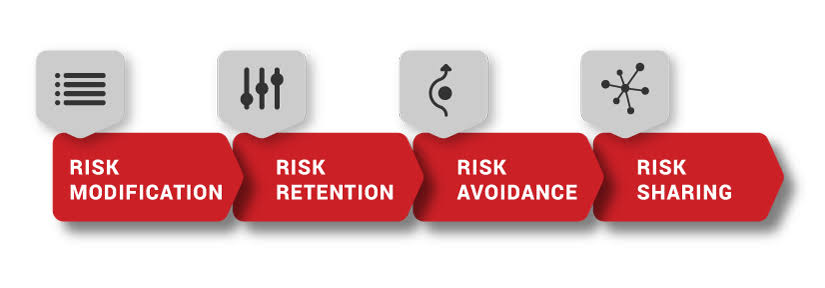
C. Maintaining Confidentiality, Integrity, and Availability:
The core objective of ISO/IEC 27005 aligns perfectly with the fundamental tenets of network security: confidentiality, integrity, and availability (CIA). The standard helps organizations identify and address risks that could compromise the confidentiality of sensitive data, the integrity of network operations, or the availability of critical resources. This ensures reliable and secure network operations, protecting both data and business continuity.
D. Aligning with ISO/IEC 27001 Implementation:
For organizations seeking ISO/IEC 27001 certification (Information Security Management System), implementing ISO/IEC 27005’s risk management framework is a crucial step. The standard provides the specific steps and guidance required to fulfill the risk management requirements of ISO/IEC 27001, simplifying the certification process and strengthening overall information security posture.
ii. Here’s how ISO/IEC 27005 relates to risk management within enterprise networks
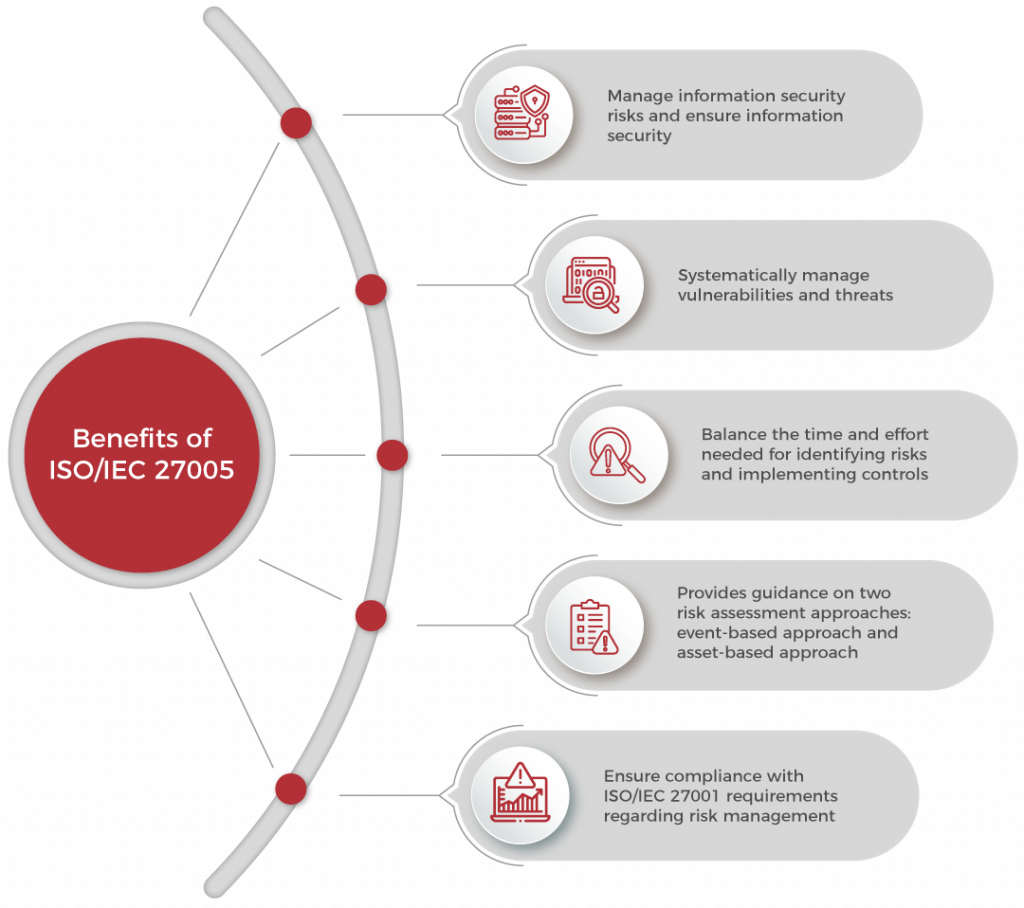
A. Framework for Information Security Risk Management: ISO/IEC 27005 provides a systematic and comprehensive framework for organizations to establish, implement, monitor, review, and improve their information security risk management process.
B. Alignment with ISO/IEC 27001: ISO/IEC 27005 aligns with ISO/IEC 27001, the international standard for information security management systems (ISMS). The two standards work together to provide a cohesive approach to managing information security within an organization.
C. Risk Identification and Assessment: The standard guides organizations in identifying and assessing information security risks specific to their enterprise networks. This includes considering the vulnerabilities, threats, and potential impacts on the network.
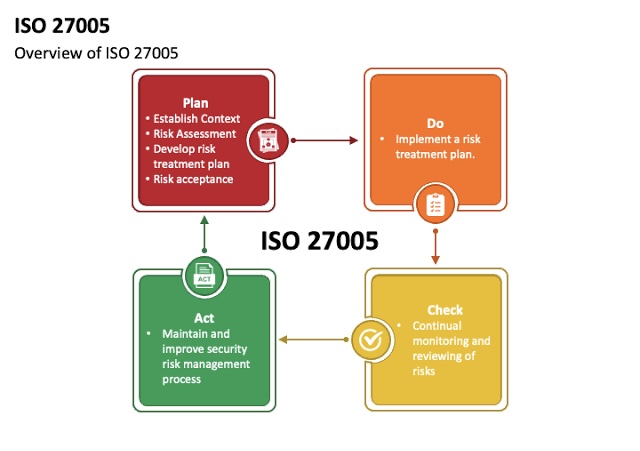
D. Risk Treatment and Mitigation: ISO/IEC 27005 helps organizations in defining and implementing risk treatment plans. This involves selecting and applying appropriate security controls to mitigate or manage identified risks effectively.
E. Communication and Consultation: The standard emphasizes the importance of communication and consultation throughout the risk management process. This ensures that relevant stakeholders within the enterprise network are involved in decision-making and risk treatment strategies.
F. Documentation and Record-Keeping: ISO/IEC 27005 encourages organizations to maintain documentation and records related to the risk management process. This includes documenting risk assessments, treatment plans, and decisions made to manage risks within the enterprise network.
G. Continuous Improvement: Continuous improvement is a key principle of ISO/IEC 27005. Organizations are encouraged to regularly review and update their risk management processes based on changes in the information security environment and the evolving threat landscape within enterprise networks.
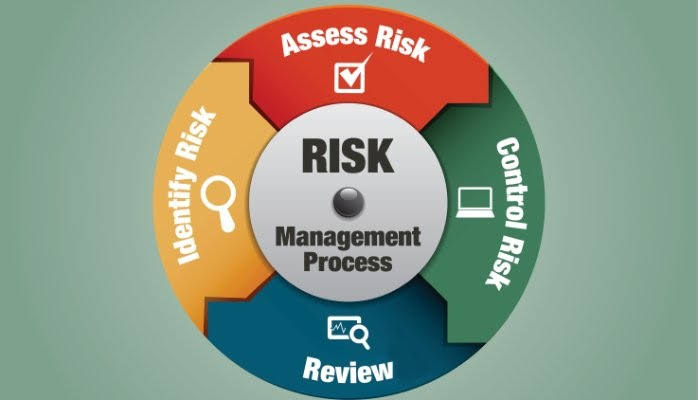
H. Integration with Business Processes: ISO/IEC 27005 advocates for the integration of risk management into an organization’s overall business processes. This ensures that information security risks are considered in the context of broader business objectives and activities.
I. Flexibility and Adaptability: The standard is designed to be flexible and adaptable to different organizational structures and industries. This flexibility allows enterprises to tailor their risk management approach to the specific needs and characteristics of their network environments.
iii. Conclusion:
ISO/IEC 27005 is not just a standard; it’s a powerful tool for building a robust and effective risk management strategy for enterprise networks. By providing a structured framework, minimum baseline controls, and alignment with broader information security goals, it empowers organizations to protect their critical data, maintain network resilience, and ensure business continuity in the face of ever-evolving cyber threats.
For enterprises, adherence to ISO/IEC 27005 demonstrates a commitment to managing risk effectively, which is essential to maintaining trust with stakeholders, customers, and other businesses in an increasingly interconnected and digital world.
It supports the maintenance of robust, secure, and resilient IT environments, which is crucial for protecting against information security breaches and reducing the impact of such events should they occur.
iv. Further references
https://secureframe.com/blog/iso-27005
https://www.isms.online/iso-27005/
https://www.techtarget.com/searchsecurity/tip/Applying-the-ISO-27005-risk-management-standard
https://www.itgovernance.co.uk/iso27005
https://www.c-risk.com/blog/iso-27005
https://www.sisainfosec.com/blogs/comparison-between-iso-27005-octave-nist-sp-800-30-sisa-blog/
https://www.scirp.org/journal/paperinformation?paperid=126165
