
Building a Resilient Cybersecurity Strategy with ISO/IEC 27001 and ISO/IEC 27035
ISO/IEC 27001 (ISMS – Information Security Management System) and ISO/IEC 27035 (Information Security Incident Management) are two key standards in the ISO 27000 family that provide a robust and effective framework for setting up and managing cybersecurity.
They assist organizations in building a resilient cybersecurity strategy.
i. Here’s how the two standards can be used to build a robust cybersecurity strategy:
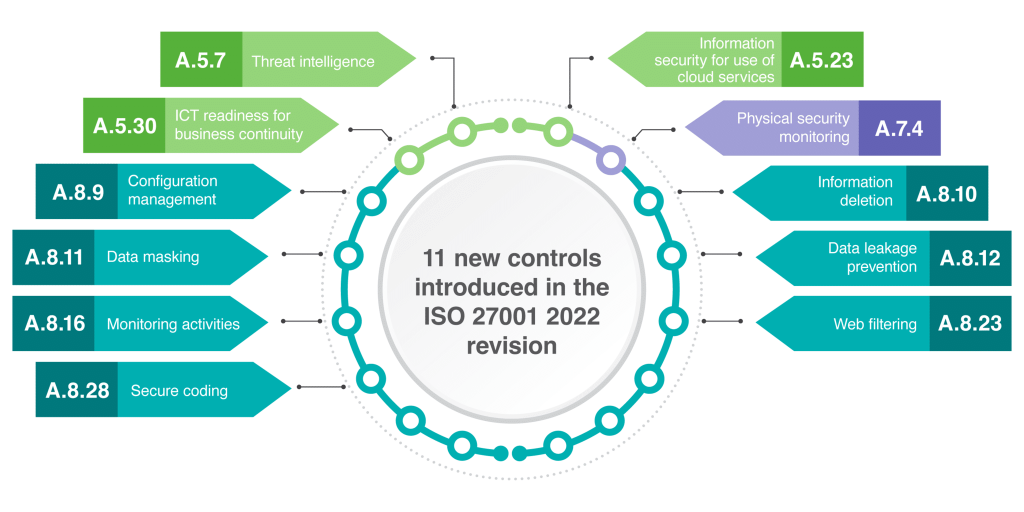
A. ISO/IEC 27001:
a. Establish, Implement, and Operate an ISMS: ISO/IEC 27001 provides a systematic approach for establishing, implementing, operating, monitoring, maintaining, and improving an ISMS. The ISMS is a set of policies and procedures that includes all legal, physical, and technical controls involved in an organization’s information risk management processes.
b. Regular Risk Assessments: The standard encourages regular information security risk assessments to identify cybersecurity risks and set control objectives.
c. Compliance with Laws and Regulations: ISO/IEC 27001 can help organizations stay compliant with regulations as they relate to data protection and cybersecurity.
d. Continual Improvement: The standard follows the Plan-Do-Check-Act (PDCA) model, which means that the ISMS should continually be reviewed and improved upon.
B. ISO/IEC 27035:

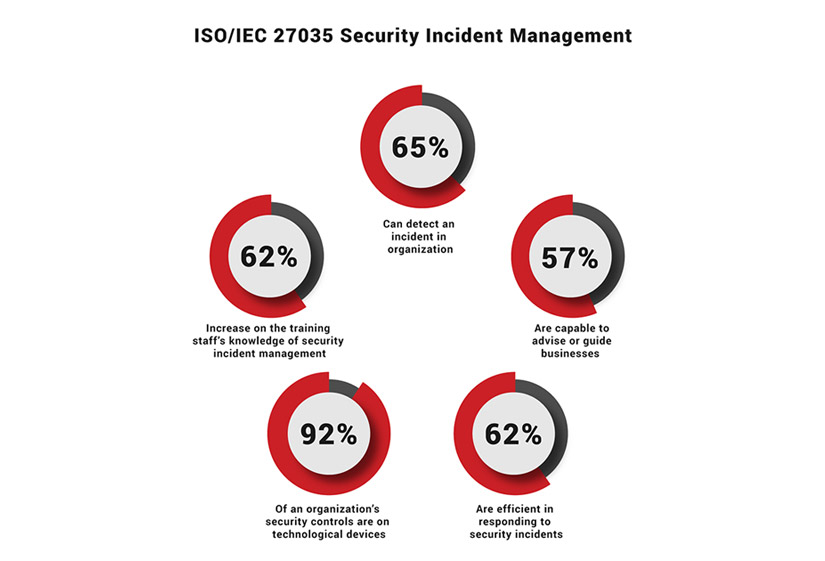
a. Manage Security Incidents: ISO/IEC 27035 provides guidelines for the process of managing information security incidents, including identification, reporting, assessment, response, and learning from incidents to prevent them from recurring.
b. Improved Incident Response: The implementation of ISO/IEC 27035 helps organizations improve their response to incidents, leading to reduced damage, improved recovery time, and increased ability to provide necessary evidence for any legal action that may be required.
c. Proactive and Reactive Management: The standard allows for both reactive and proactive management of incidents.
ii. This is where the synergy of ISO/IEC 27001 and ISO/IEC 27035 comes in.
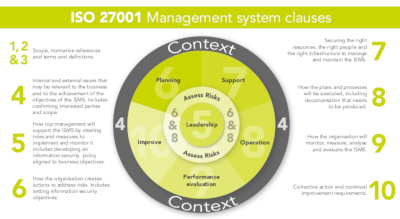
A. ISO/IEC 27001: The Foundation for Information Security Management
This internationally recognized standard provides a framework for establishing an Information Security Management System (ISMS). It helps you identify and analyze your organization’s information security risks, implement appropriate controls, and continuously improve your security posture.
o Key benefits of ISO/IEC 27001:
o Systematic approach: Creates a structured framework for managing information security across all departments.
o Proactive risk management: Identifies and mitigates potential threats before they can cause harm.
o Improved compliance: Aligns with a wide range of regulations and industry best practices.
o Enhanced stakeholder confidence: Demonstrates your commitment to information security.
B. ISO/IEC 27035: Incident Response Excellence
This standard complements ISO/IEC 27001 by providing a robust framework for incident response. It outlines the processes and procedures for detecting, responding to, and recovering from security incidents effectively.
o Key benefits of ISO/IEC 27035:
o Reduced impact of incidents: Minimizes damage and downtime caused by cyberattacks.
o Faster recovery times: Enables a swift and coordinated response to security incidents.
o Improved communication: Clearly defines roles and responsibilities for incident response activities.
o Lessons learned: Helps you learn from incidents and improve your security posture.
iii. Synergy for a Resilient Strategy:
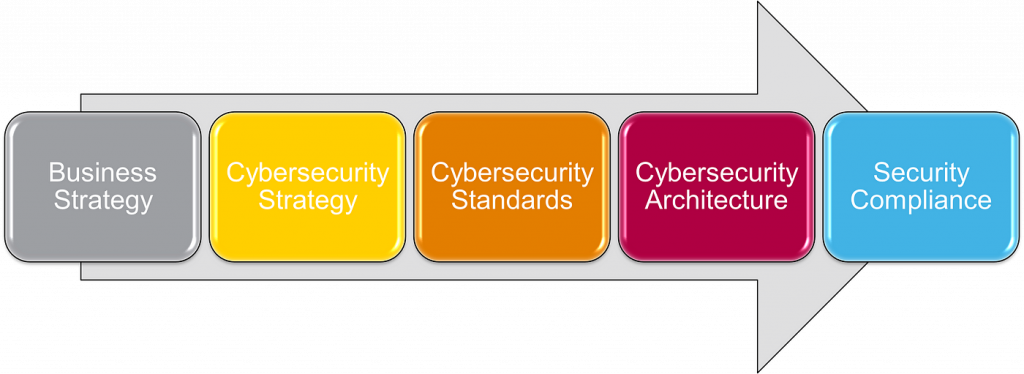
Combining the proactive risk management of ISO/IEC 27001 with the incident response capabilities of ISO/IEC 27035 creates a holistic and resilient cybersecurity strategy. This integrated approach offers several advantages:
o Comprehensive risk mitigation: Proactive controls prevent incidents while effective response minimizes their impact.
o Enhanced preparedness: Defined processes ensure a coordinated and efficient response to security threats.
o Continuous improvement: Lessons learned from incidents inform future risk management efforts.
iv. Building a resilient cybersecurity strategy with ISO/IEC 27001 and ISO/IEC 27035 involves the following steps:
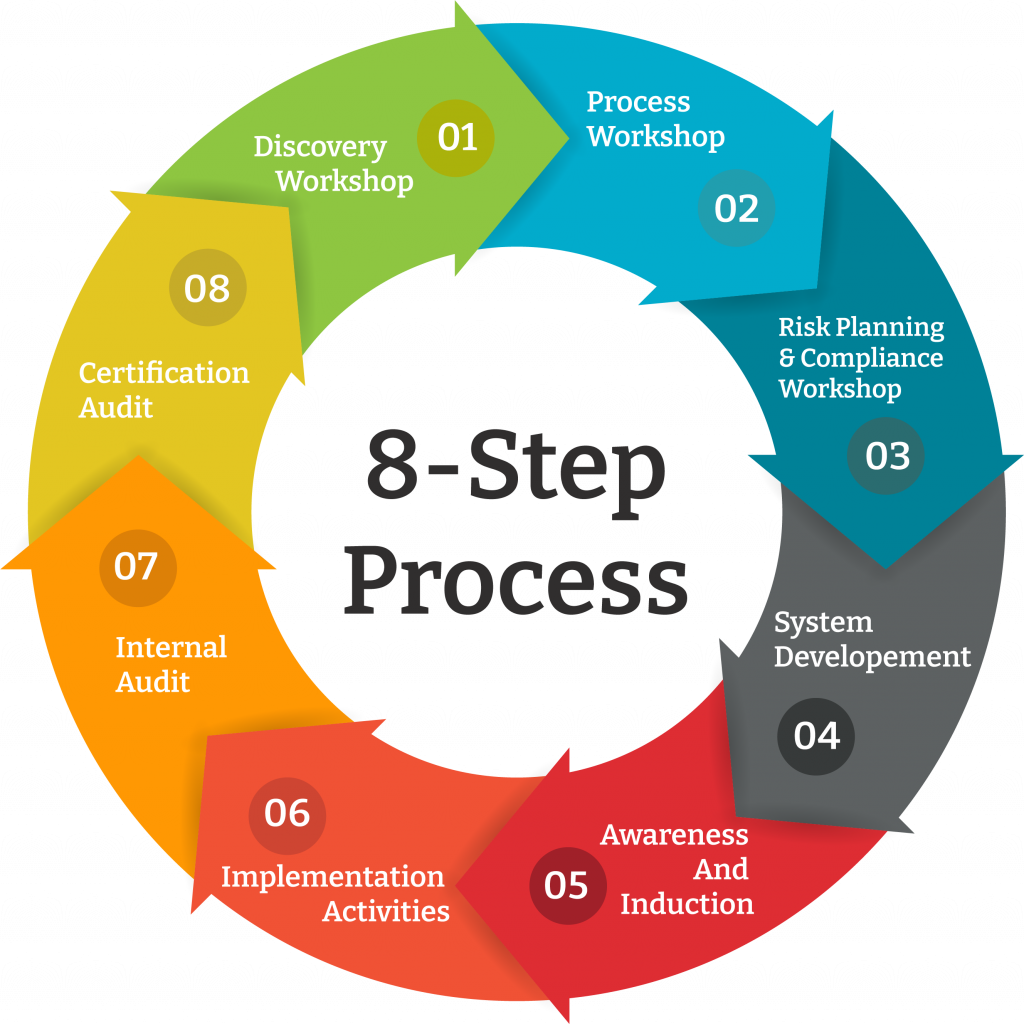
A. ISO/IEC 27001 Implementation:
o Identify and assess information assets and associated risks.
o Develop an Information Security Management System (ISMS) based on ISO/IEC 27001 standards.
o Establish and document security policies, procedures, and controls.
B. Risk Management:
o Perform a thorough risk assessment using ISO/IEC 27001 guidelines.
o Mitigate identified risks by implementing appropriate controls.
o Regularly review and update risk assessments to adapt to changing threats.

C. Incident Response Planning (ISO/IEC 27035):
o Develop an incident response plan aligned with ISO/IEC 27035 standards.
o Establish an incident response team and define roles and responsibilities.
o Conduct regular drills and simulations to ensure preparedness for cyber incidents.

D. Continuous Monitoring:
o Implement continuous monitoring mechanisms to detect and respond to security incidents promptly.
o Use security information and event management (SIEM) tools to monitor and analyze system activities.
E. Training and Awareness:
o Provide comprehensive training on ISO/IEC 27001 and ISO/IEC 27035 principles for employees involved in security functions.
o Foster a culture of cybersecurity awareness across the organization.
F. Compliance Management:
o Ensure ongoing compliance with ISO/IEC 27001 requirements and other relevant regulations.
o Regularly conduct internal audits to assess adherence to established standards.
G. Documentation and Records:
o Maintain detailed documentation of security policies, procedures, and incident response plans.
o Keep records of security incidents, investigations, and corrective actions taken.
H. Third-Party Collaboration:
o Engage with external stakeholders, suppliers, and partners to align cybersecurity practices.
o Include third-party risk assessments within your overall risk management strategy.

I. Review and Improvement:
o Conduct regular reviews of your cybersecurity strategy, considering lessons learned from incidents and audits.
o Implement improvements based on emerging threats and organizational changes.
v. To leverage these standards in building a resilient cybersecurity strategy:
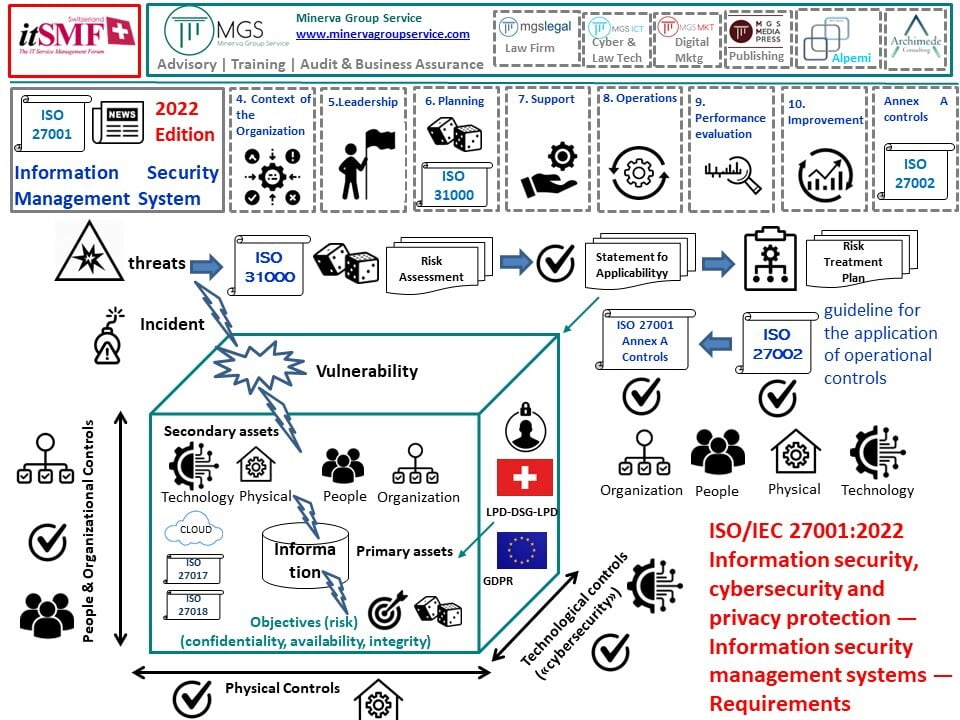
o Integrate Both Standards: ISO/IEC 27001 and ISO/IEC 27035 should be integrated, using the broader security management controls of 27001 to support the incident management processes of 27035.
o Holistic Approach: Employ both standards for a holistic approach to cybersecurity that covers prevention, detection, response, and post-incident actions.
o Periodic Reviews: Implement periodic reviews and updates of policies, controls, plans, and procedures to ensure they are current and in alignment with these standards.
o Conduct thorough risk assessments.
o Ensure there’s leadership commitment and adequate resources available.
o Certification and Training: Consider achieving certification for both standards, which can increase stakeholder confidence and may provide a competitive advantage. Staff training in these standards can increase organizational resilience and readiness.
o Continuously monitor and improve upon your information security controls and responses.
vi. Conclusion:

By building a cybersecurity strategy around ISO/IEC 27001 and ISO/IEC 27035, organizations can ensure they are well-prepared not only to protect their information assets but also to handle and recover from security incidents effectively. This approach positions an organization to better navigate the complexities of information security risk and the ever-evolving cybersecurity threat-scape.
Remember, securing your organization is an ongoing journey. By leveraging the combined power of ISO/IEC 27001 and 27035, you can build a resilient cybersecurity strategy that protects your assets, safeguards your operations, and fosters trust in the digital age.
vii. Additional Resources:
o International Organization for Standardization (ISO): [https://www.iso.org/home.html]
o International Electrotechnical Commission (IEC): [https://www.iec.ch/homepage]
o PECB o PECB Insights: [https://pecb.com/en/education-and-certification-for-individuals/iso-iec-27001]
ISO/IEC 27001 and ISO/IEC 27035: Building a Resilient …Medium · PECB1 month ago
Academy of Resilience & ContinuityXhttps://twitter.com › AcademyOfRC › status
