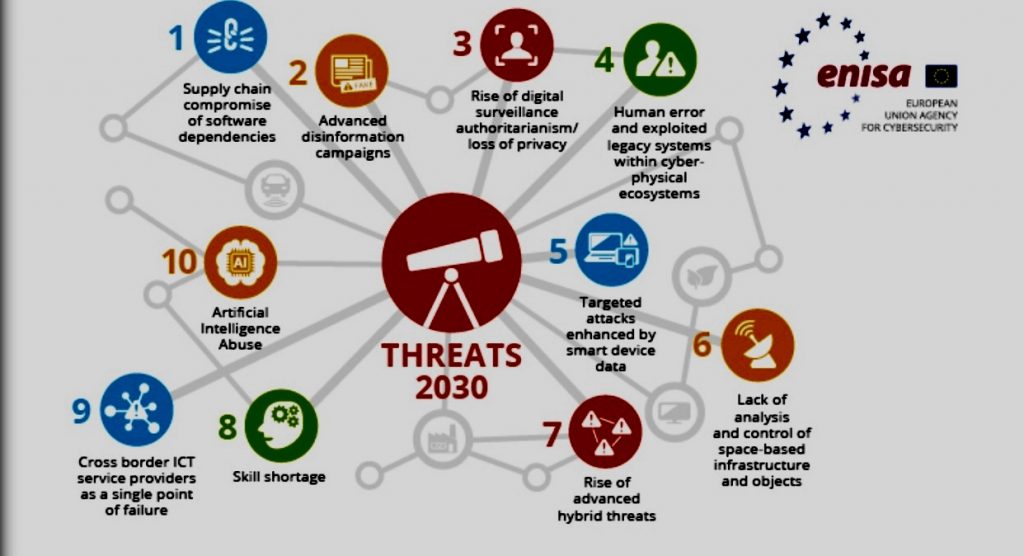
In the ever-evolving landscape of cybersecurity, organizations must proactively prepare for emerging threats to protect their valuable data and systems.
Here are some key steps to effectively prepare for emerging threats:
A. Establish a Comprehensive Risk Management Program: A robust risk management program forms the foundation for a proactive cybersecurity posture. It involves identifying, assessing, and prioritizing risks associated with information assets, vulnerabilities, and potential threats. By understanding the organization’s risk profile, effective mitigation strategies can be developed to address emerging threats.
B. Security Policies and Procedures: Update and enforce security policies and procedures. These can include password policies, data privacy policies, mobile device policies, and more.
C. Implement a Multi-layered Security Architecture: A multi-layered security architecture provides a comprehensive approach to defense, encompassing various security controls and technologies to protect against a wide range of threats. This includes network security, endpoint security, data security, application security, and identity and access management (IAM).
D. Security Hygiene Practices: Enforce strong security hygiene practices, including regular password updates, access control reviews, and secure configuration management. These foundational measures contribute to a more secure environment.
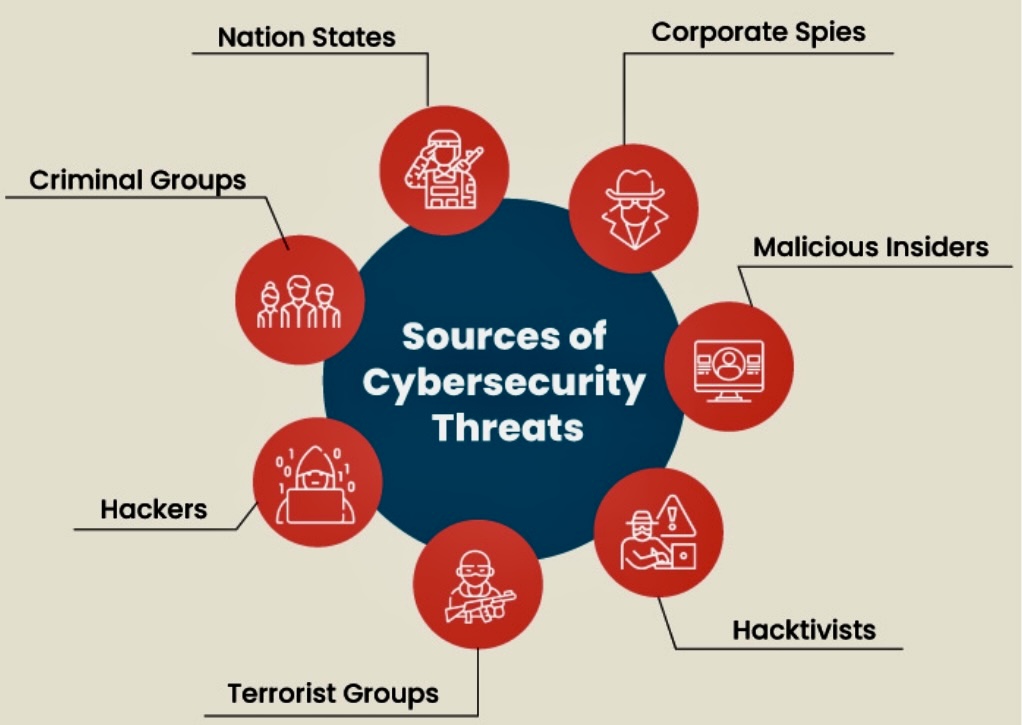
E. Zero Trust Architecture: Implement a Zero Trust architecture that assumes breaches can occur and enforces strict verification for all users and devices accessing your network. This approach helps mitigate the impact of potential compromises.
F. Continuously Monitor and Analyze Threat Landscape: Continuous monitoring and analysis of the threat landscape are crucial for staying ahead of evolving threats. This involves tracking emerging attack vectors, malware trends, and vulnerabilities in various technologies and systems. Organizations should utilize security intelligence feeds, threat research reports, and industry forums to stay informed about the latest cybersecurity threats.
G. Risk Assessments and Vulnerability Scanning: Conduct regular risk assessments and vulnerability scans to identify potential weaknesses in your systems. Prioritize addressing high-risk areas to enhance overall cybersecurity resilience.
H. Implement a Data Loss Prevention (DLP) Strategy: DLP solutions help prevent sensitive data from being accidentally or intentionally leaked or stolen. Organizations should implement DLP policies and technologies to control the movement of sensitive data and prevent unauthorized access.
I. Develop an Incident Response Plan: An incident response plan outlines the procedures and communication protocols to effectively handle cybersecurity incidents. It should include clear roles and responsibilities, notification procedures, and steps for containment, eradication, and recovery.
J. Stay Informed About Emerging Regulatory Requirements: Cybersecurity regulations are constantly evolving, and organizations must stay informed about new requirements and compliance guidelines. This includes data privacy regulations, such as GDPR and CCPA, and industry-specific regulations.
K. Continuously Adapt and Refine Security Strategies: As cyber threats evolve, organizations must continuously adapt and refine their security strategies to remain effective. This involves adopting new technologies, implementing emerging security best practices, and staying vigilant about the latest threat trends.
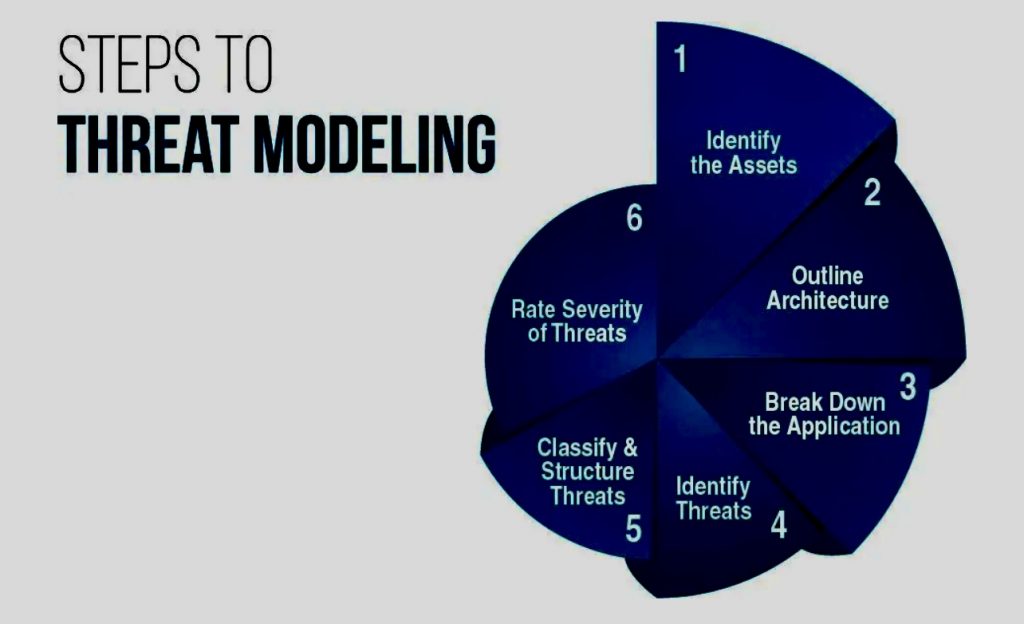
L. Regularly Update Software and Systems: Software and systems vulnerabilities can serve as entry points for attackers. Organizations should implement a regular patching and updating process to ensure that all systems and applications are running the latest secure versions. This includes operating systems, software applications, firmware, and security patches.
M. Continuous Threat Intelligence Monitoring: Establish a system for continuous monitoring of threat intelligence sources. Stay informed about emerging threats, attack vectors, and vulnerabilities relevant to your industry and technology stack.
N. Employee Training and Awareness: Invest in comprehensive training programs to educate employees about evolving cyber threats. Increased awareness can empower your workforce to recognize and respond effectively to potential risks.
O. Incident Response Planning: Develop and regularly update an incident response plan. Ensure that your team is well-prepared to respond swiftly and effectively in the event of a security incident, minimizing potential damage.
P. Patch Management: Establish a robust patch management process to promptly apply security updates. Regularly update software, firmware, and operating systems to address known vulnerabilities and enhance overall system security.
Q. Collaboration with Industry Peers: Engage in information sharing and collaboration with industry peers. Participate in threat intelligence sharing communities to benefit from collective insights and experiences in combating emerging threats.
R. Secure Configuration Management: Ensure that systems are configured securely based on industry best practices and security standards. Misconfigurations can introduce vulnerabilities that attackers may exploit.
S. Security Awareness Training for Executives: Provide targeted security awareness training for executives and decision-makers. Ensuring that leadership understands the evolving threat landscape is crucial for making informed decisions on cybersecurity investments and strategies.
T. Advanced Security Analytics: Deploy advanced security analytics tools to detect anomalous activities and potential threats. Utilize machine learning and behavioral analytics to identify patterns indicative of emerging cyber threats.
U. Regular Tabletop Exercises: Conduct regular tabletop exercises to simulate cyberattack scenarios. This practice helps test the effectiveness of your incident response plan and enhances the team’s readiness for real-world incidents.
V. Evaluate and Adopt New Technologies: Stay abreast of emerging cybersecurity technologies and trends. Evaluate their relevance to your organization and consider adopting those that align with your security strategy and address specific emerging threats.
W. Backup and Recovery Planning: Establish robust backup and recovery procedures. Regularly test backups to ensure data can be quickly restored in case of ransomware attacks or data breaches.
X. Regulatory Compliance Monitoring: Stay vigilant about changes in cybersecurity regulations and compliance requirements. Regularly review and update your security measures to align with evolving legal and regulatory standards.
Y. Regular Audits: Conduct regular security audits to assess the effectiveness of your security measures, and identify any areas of weakness or non-compliance. This can help improve your defense strategy and better prepare for emerging threats.
By systematically addressing these key steps, organizations can enhance their readiness to face emerging cyber threats. Proactive measures, combined with a comprehensive security strategy, contribute to building a resilient cybersecurity posture in the face of an ever-evolving threat landscape.
https://www.aus.com/blog/emerging-threats-and-emergency-preparedness
https://www.embroker.com/blog/cybersecurity-threats/
https://www.simspace.com/blog/threat-detection-and-response-best-practices-and-tips-for-success
