
Embracing Change: Applying Kotter’s Model in the World of Cybersecurity
John Kotter’s 8-step change model has long been recognized as a revolutionary paradigm for executing sustainable, large-scale organizational transformations.
This model, created by Harvard Business School professor John P. Kotter, outlines a series of phases that collectively contribute to successful change management. It aligns especially well in the domain of cybersecurity, where change is a constant, punctuated by evolving threats, novel tools, and shifting approaches to managing risk.
The Intersection of Kotter and Cybersecurity
In the realm of cybersecurity, keeping ahead of potential hazards requires dynamic change.
Cybersecurity isn’t a static field; technology, threat vectors, and hacker methodologies evolve at an alarmingly fast rate. Adapting to, and even staying ahead of, this evolutionary curve demands robust change management strategies.
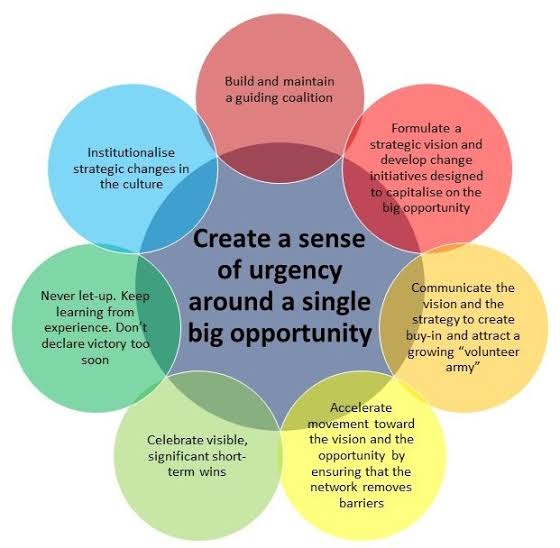
i. Here is how Kotter’s stages fit into a cybersecurity context
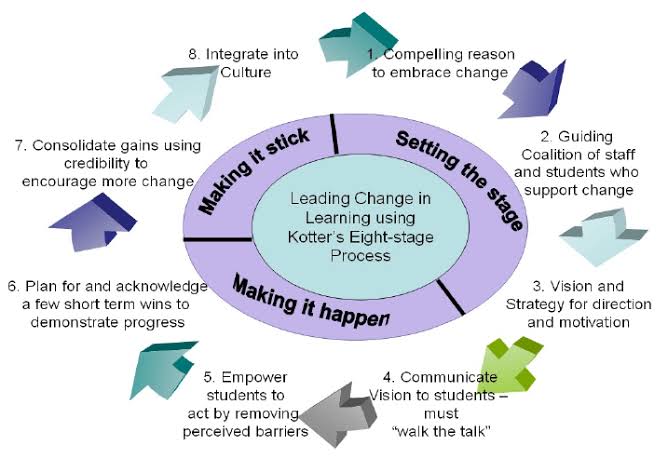
A. Creating a Sense of Urgency: This involves impressing upon all stakeholders the gravity of cyber threats. This can be done by providing evidence of recent cyber-attacks, outlining potential risks, or showing case studies of companies that have faced serious consequences due to cybersecurity breaches.
B. Building a Guiding Coalition: Assemble a cross-functional, powerful team that is responsible for driving the cybersecurity change. This would include top management, IT professionals, and representatives from various departments who would work collectively to address cybersecurity concerns.
C. Forming a Strategic Vision and Initiatives: Define the aim of the cybersecurity strategy, outline the approach, create SOPs for risk management, and plan for disaster recovery. Develop an easily understandable language to communicate this vision so it resonates with all employees.
D. Enlisting a Volunteer Army: Beyond your guiding coalition, you need to engage as many people as possible to ensure a secure environment. This includes educating employees about the vision and their role in achieving it. This will help them understand how they can contribute.
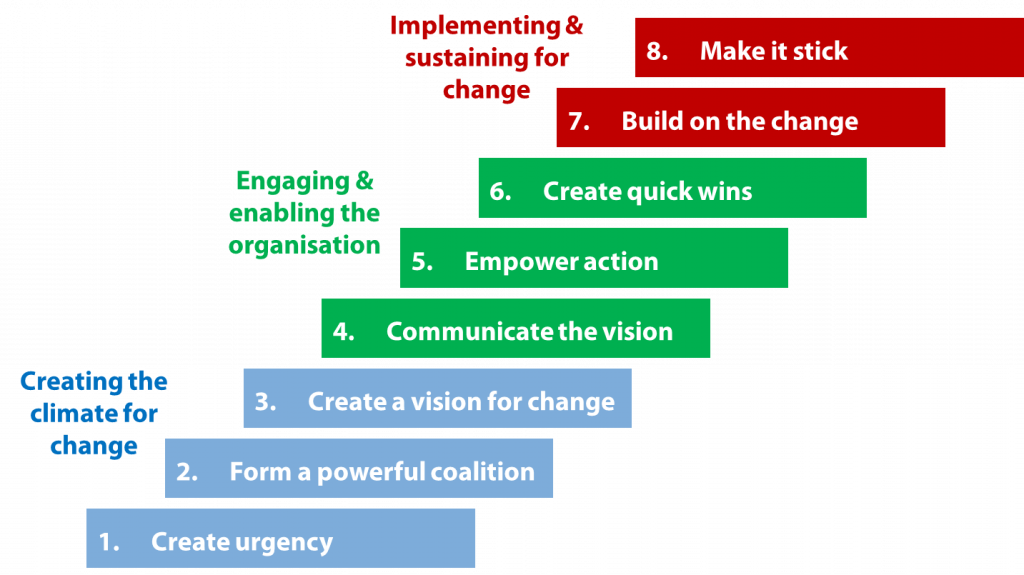
E. Enabling Action by Removing Barriers: Break down silos, encourage information sharing, provide the necessary training and resources to all employees so they can contribute to a secure environment. Also, ensure that the organization’s systems and processes support the cybersecurity vision.
F. Generating Short-Term Wins: Create short-term goals alongside the long-term vision. Celebrate when these are achieved to keep people motivated. These short wins could be successful training sessions, the installation of new security software, or passing an external security audit.
G. Sustaining Acceleration: Don’t slow down after the initial success. Keep improving the cybersecurity program, provide ongoing training, and continuously adapt to the changing technological landscape and attack vectors.
H. Instituting Change: Anchor the changes into the culture to make them stick. Regular reviews and reinforcement of secure behaviors will help in maintaining this culture of cybersecurity.
ii. Benefits of Applying Kotter’s Model in Cybersecurity
o Increased Employee Engagement: A clear vision and communication encourage buy-in and active participation from all stakeholders.
o Improved Collaboration: Breaking down silos and fostering cross-functional collaboration strengthens cybersecurity defenses.
o Accelerated Change: Short-term wins and ongoing feedback loops allow for faster adaptation and progress.
o Sustainable Transformation: Anchoring new approaches in the culture ensures long-term security improvements.

Kotter’s 8-step change model serves as a valuable guide for implementing change in the cybersecurity realm. It encapsulates the need for urgency, collaboration, clear communication, removal of obstacles, acknowledgment of improvements, and the institutionalization of changes.
Applying a human-centered change model like Kotter’s can make the difference between an organization that merely reacts to cybersecurity threats and one that proactively evolves to meet them. Consequently, it offers a roadmap for how organizations can future-proof themselves against potential cybersecurity vulnerabilities.
https://www.osibeyond.com/blog/change-management/
https://www.mstech.com/leading-change-culture-cybersecurity/
https://www.sans.org/blog/the-foundation-to-a-strong-security-culture-feeling-safe-and-included/
