
CyBOK’s Network Security Knowledge Area: Guarding the Gateways
The Cyber Security Body Of Knowledge (CyBOK) is a comprehensive collection aiming to codify the foundational and generally recognized knowledge on Cyber Security. The Network Security Knowledge Area within CyBOK delves into various aspects of securing computer networks, which is an essential part of cyber security.
i. The CyBOK framework’s Network Security Knowledge Area (KA) high level
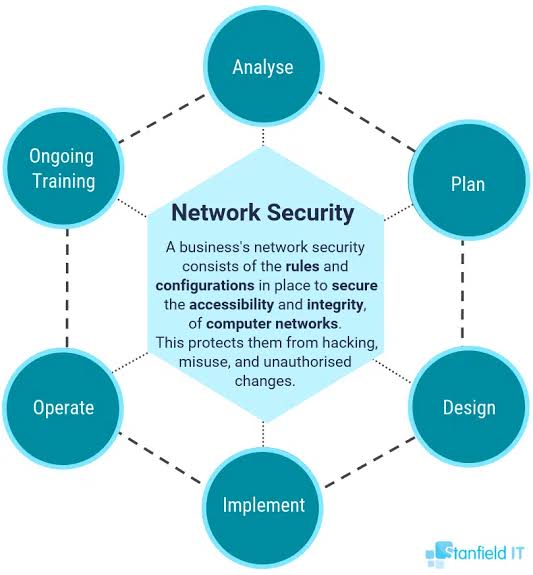
A. Understand the Battlefield:
o Network Architecture: Grasp the layered structure of networks, from the OSI model to specific protocols like TCP/IP, to effectively identify vulnerabilities and implement targeted security measures.
o Network Devices: Familiarize yourself with the critical components of your network infrastructure, such as routers, switches, firewalls, and intrusion detection systems, to configure and manage them for optimal security.
B. Recognize the Threats:
o Network Attacks: Learn about common network attack vectors like denial-of-service (DoS), man-in-the-middle (MitM), and eavesdropping, to anticipate and counter them effectively.
o Emerging Threats: Stay abreast of the latest trends in network security threats, such as zero-day exploits and sophisticated botnets, to adapt your defenses accordingly.
C. Build Your Defenses:
o Network Security Controls: Implement a layered approach to network security, utilizing tools like firewalls, access control lists (ACLs), and intrusion detection/prevention systems (IDS/IPS) to create a robust defense perimeter.
o Network Segmentation: Divide your network into smaller, segmented zones to minimize the impact of potential breaches and prevent attackers from easily traversing your entire network.
D. Monitor and Respond:
o Network Security Monitoring: Continuously monitor your network for suspicious activity and anomalies using dedicated tools and log analysis techniques, enabling early detection of potential threats.
o Incident Response: Develop a comprehensive incident response plan to effectively handle network security breaches, minimizing damage and restoring normal operations promptly.
CyBOK’s Network Security KA goes beyond technical knowledge, fostering a deeper understanding of the attacker’s perspective and motivations.
ii. The CyBOK framework’s Network Security Knowledge Area (KA) insights
A. Adversarial Tactics: Learn how attackers target networks, exploit vulnerabilities, and evade detection, allowing you to anticipate their moves and strengthen your defenses accordingly.
B. Evolving Technologies: Stay informed about the latest advancements in network security technologies and adapt your defenses to address emerging threats.
C. Safeguard your network: Proactively identify and mitigate security risks, minimizing vulnerabilities and protecting your critical assets.
D. Thwart attackers: Effectively counter network attacks, preventing unauthorized access and preserving the integrity of your systems.
E. Maintain operational resilience: Ensure the uninterrupted operation and availability of your network infrastructure even in the face of security challenges.
iii. Network Security Knowledge Area, core topics
A. Security Design Principles: This involves the fundamental concepts that guide the secure design of networks, including the consideration of trust levels, the principle of least privilege, and the need to secure both the data and the endpoints.
B. Threats and Attacks: It looks into common network threats and attacks, such as Denial of Service (DoS), Distributed Denial of Service (DDoS) attacks, man-in-the-middle attacks, and the various forms of eavesdropping and traffic analysis that a network might be subjected to.
C. Defensive Measures: The area covers a range of preventive mechanisms and countermeasures such as firewalls, intrusion detection/prevention systems (IDS/IPS), Secure Sockets Layer (SSL) and Virtual Private Networks (VPNs).
D. Protocol Security: This includes the security measures taken to protect protocols across all layers of network communication —from TCP/IP stack protocols, like TCP and IP, to application layer protocols like HTTP and FTP.
E. Wireless and Emerging Network Technologies: It looks into the unique security challenges presented by wireless communications and emerging network technologies, including mobile networks, cloud computing networks, and the Internet of Things (IoT).
F. Operational Issues and Physical Security: Topics under this heading cover the operationally related issues, including network management, network security policy formulation and implementation, as well as the physical safeguarding of network infrastructure.
G. Privacy Issues: Covers how network security can impact privacy, including discussions around data protection laws, encryption, and anonymity in network communications.
H. Cryptography in Network Security: Discussing the role of cryptography in securing network communications, including symmetric and asymmetric encryption, digital signatures, secure hash functions, and certificates.
I. Incident Response and Forensics: This includes how organizations respond to network security breaches and the process of collecting and analyzing data for forensic purposes to understand and mitigate cyber threats.
J. Secure Network Architecture: Discussing network segmentation, the role of secure network architecture in resisting and containing intrusions, and the importance of designing networks with security in mind.
iv. Key Components of Network Security Knowledge Area
A. Network Architecture:
CyBOK emphasizes the importance of understanding network architectures, including topologies, protocols, and communication patterns. Professionals need to navigate the complexities of modern network infrastructures to implement robust security measures.
B. Cryptographic Techniques:
Encryption lies at the heart of securing communications. CyBOK delves into cryptographic principles, ensuring that cybersecurity practitioners possess the knowledge to implement and manage encryption protocols effectively.
C. Secure Network Design:
Building security into network architecture is a proactive approach to thwarting cyber threats. CyBOK provides insights into designing networks with security in mind, considering factors like segmentation, access controls, and secure configurations.
D. Firewalls and Intrusion Detection Systems:
Network security isn’t complete without robust perimeter defenses. CyBOK covers the deployment and management of firewalls, as well as the implementation of intrusion detection systems to identify and respond to potential threats.
E. Network Protocols:
An in-depth understanding of network protocols is crucial for securing data in transit. CyBOK explores various protocols, their vulnerabilities, and secure alternatives, enabling professionals to make informed decisions when configuring network communication.
Remember, a secure network is the foundation of a resilient cybersecurity posture. Invest in CyBOK’s Network Security KA and build a robust defense against the ever-evolving threats in the digital landscape.
CyBOK’s Network Security Knowledge Area is designed to provide professionals with insights into the best practices, techniques, and strategic approaches to sustainably defend networked systems against cyber threats and ensure data integrity and service continuity.
https://www.cybok.org/media/downloads/Network_Security_v2.0.0.pdf
https://www.techtarget.com/searchnetworking/definition/network-security
https://www.paloaltonetworks.com/cyberpedia/what-is-network-security
