
Unveiling the Trio of Cyber Threats: Phishing, Vishing, and Smishing
In the rapidly evolving landscape of cyber threats, understanding and guarding against various forms of attacks is paramount.
Phishing, vishing, and smishing are three closely related methods cybercriminals employ to deceive individuals and organizations.
Each method employs different techniques and communication channels to trick victims.
Here’s what you need to know about them:
i. Phishing: The Art of Deceptive Emails

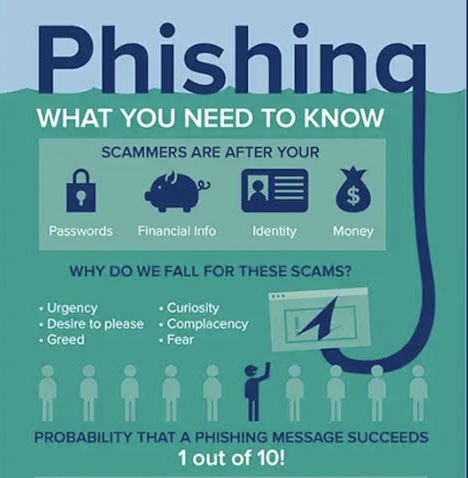
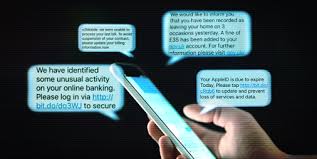
o Phishing is a fraudulent technique where cybercriminals send seemingly legitimate emails, aiming to trick recipients into revealing sensitive information such as passwords or financial details.
o These deceptive emails often mimic trustworthy entities like banks, social media platforms, or even colleagues.
o To make emails look authentic, attackers often replicate the design, language, and tone of official communications from the entities they are impersonating.
o The urgency and authenticity portrayed in these messages can deceive even the most cautious individuals.
o The objective is to lure individuals into providing sensitive data, clicking on malicious links, or downloading infected files.
To safeguard against phishing:
o Be wary of emails that request personal information, regardless of how official they appear.
o Check the sender’s email address for any irregularities.
o Avoid clicking on links or downloading attachments from unknown or suspicious emails.
o Use email filters and maintain updated anti-virus software.
o Scrutinize emails for unusual senders or unexpected requests.
o Hover over hyperlinks to preview the destination URL before clicking.
o Verify suspicious emails by contacting the supposed sender through a trusted means.
ii. Vishing: Manipulating Through Voice
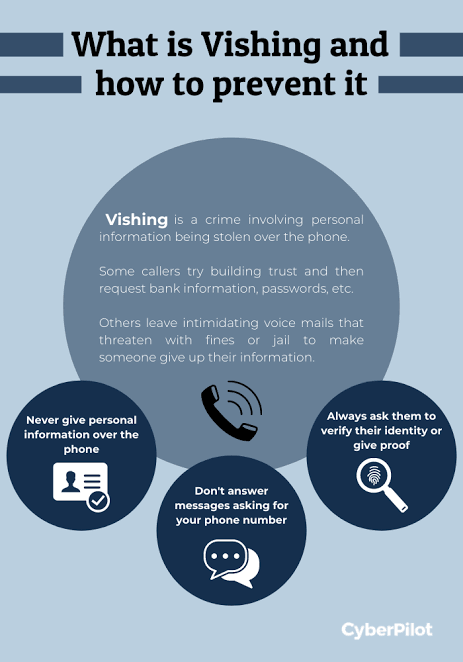
o Vishing, short for voice phishing, involves using phone calls to trick individuals into divulging personal information.
o Cybercriminals may pose as representatives from banks, government agencies, or tech support, creating a sense of urgency or fear to extract sensitive details.
o This method plays on the human element – using pressure, urgency, or exploiting trust – to obtain sensitive data directly.
o Technology such as caller ID spoofing can make vishing calls appear more legitimate, making it harder for individuals to identify the scam.
o The objective is to convince victims to give out personal or financial information over the phone.
Protecting against vishing:

o Be wary of calls that request personal information, regardless of how official they appear.
o Be cautious of unsolicited calls asking for personal or financial information.
o Do not trust caller ID as it can be spoofed.
o If you suspect a call is not legitimate, hang up and contact the organization through verified means.
o Register your number with national “Do Not Call” lists to reduce telemarketing calls, making vishing attempts more identifiable.
o Verify the identity of the caller independently using official contact details.
o Refrain from sharing sensitive information over the phone unless absolutely certain.
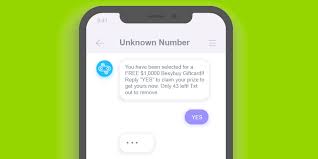
iii. Smishing: The SMS Trap

o Smishing, or SMS phishing, employs text messages to deceive recipients into clicking malicious links or providing sensitive information.
o The attacker sends a message pretending to be from a reputable source, asking the recipient to click on a link or respond with personal information.
o The messages often create a sense of urgency or offer too-good-to-be-true deals, exploiting the credibility and immediacy associated with text messaging.
o These messages often claim urgent actions are required, creating a sense of panic to manipulate individuals into compliance.
o With the increase in smartphone usage, smishing has become a more common attack vector.
To defend against smishing:

o Be skeptical of text messages that ask for personal information or prompt you to click on a link, especially if the message instills a sense of urgency.
o Verify the authenticity of the message by directly contacting the purported sender through official channels.
o Avoid responding to suspicious texts, even to text “STOP,” as this can confirm to scammers that your number is active.
o Use your phone’s native or third-party apps to block texts from unknown numbers.
o Confirm the legitimacy of the message by contacting the organization directly.
iv. Commonalities Among These Attacks
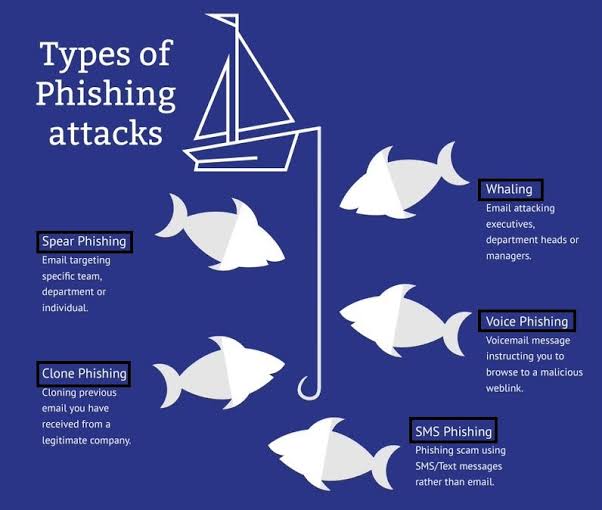
While the delivery methods differ (email for phishing, phone calls for vishing, and text messages for smishing), these attacks share common strategies:
o Impersonation: Pretending to be a trustworthy entity to gain the victim’s confidence.
o Urgency: Creating a sense of urgency to prompt hasty action, often warning of a security threat or financial loss.
o Request for Action: Asking the victim to reveal sensitive information, click on a link, or perform a specific action that compromises security.
v. Staying Vigilant Across the Board
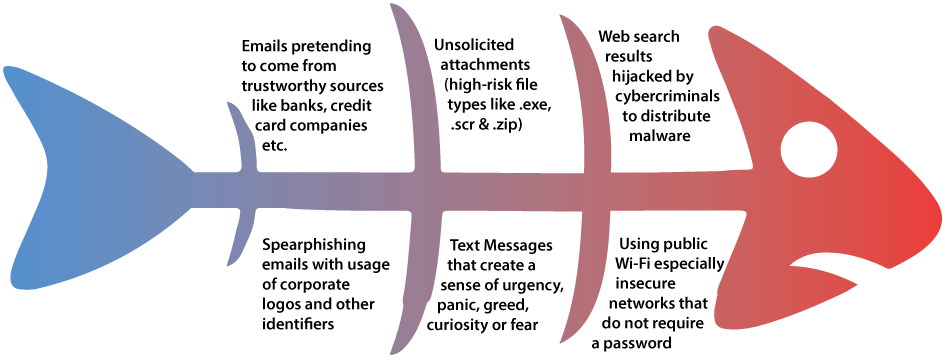
o Be cautious of unsolicited messages: Whether by email, phone call, or text message, be wary of any communication requesting personal information or urging you to click on links.
o Verify the sender: Don’t trust the sender’s name or caller ID at face value. Verify the legitimacy of the communication by reaching out to the supposed sender through their official channels (e.g., website, phone number listed on your account statement).
o Don’t Click on Links or Attachments in Unsolicited Emails or Messages: Instead, go directly to the official website by typing the address into your browser.
o Don’t share personal information over the phone or through text messages: Legitimate companies will never request sensitive information like passwords or social security numbers via phone or text message.
o Report suspicious activity: If you encounter a phishing, vishing, or smishing attempt, report it to the relevant authorities and the platform where you received the message (e.g., email provider, phone carrier).
o Be Skeptical: Always verify the legitimacy of the sender through official channels. Do not use contact details provided in the message itself.
o Use Multi-Factor Authentication (MFA): This adds an additional layer of security, making it harder for attackers to gain access to your accounts even if they have your credentials.
o Keep Software Updated: Ensure your operating system, applications, and anti-virus software are up to date to protect against known vulnerabilities.
o Educate Yourself and Others: Stay informed about the latest phishing tactics, as attackers continuously refine their methods.
Collectively, these threats underline the importance of cybersecurity awareness. Regularly update passwords, enable two-factor authentication, and invest in reliable security software. Training employees and individuals to recognize and report suspicious activities is crucial in combating these threats.
vi. Conclusion
In conclusion, as technology advances, so do the tactics employed by cybercriminals. Being informed and proactive is the key to thwarting phishing, vishing, and smishing attempts. By staying vigilant and adopting a security-first mindset, individuals and organizations can fortify their defenses against these pervasive cyber threats.
By understanding these different forms of social engineering attacks and adopting a cautious and informed approach to communications, you can significantly reduce the risk of falling victim to phishing, vishing, and smishing.
vii. Further references
What are Phishing, Smishing, and Vishing Scams? – Bionic
Experianhttps://www.experian.com › blogsPhishing, Smishing and Vishing: What’s the Difference?
LinkedIn · fraud.com10+ reactions · 4 months agoWhat is phishing, smishing and vishing?
HP.comhttps://www.hp.com › us-en › shopSmishing vs. Phishing vs. Vishing | HP® Tech Takes
Medium · Rajeev Ranjan1 year agoPhishing, Smishing, and Vishing
