Post-quantum cryptography (PQC), also known as quantum-resistant cryptography, is the development of cryptographic algorithms that are thought to be secure against a cryptanalytic attack by a quantum computer.
This is in contrast to classical cryptography, which is based on mathematical problems that are believed to be difficult to solve for classical computers but could be efficiently solved by quantum computers.
i. The Need for Post-quantum Cryptography
Quantum computers are still in their early stages of development, but they have the potential to break many of the cryptographic algorithms that are currently used to secure our communications and data.
This is because quantum computers can perform certain types of calculations much faster than classical computers. For example, a quantum computer could be used to factor large numbers, which is a key step in breaking many classical cryptographic algorithms.
The development of PQC is important because it will help to ensure that our communications and data remain secure even in the face of advances in quantum computing technology. Without PQC, our current cryptographic algorithms could be broken, which would allow attackers to read our confidential communications and forge our digital signatures.
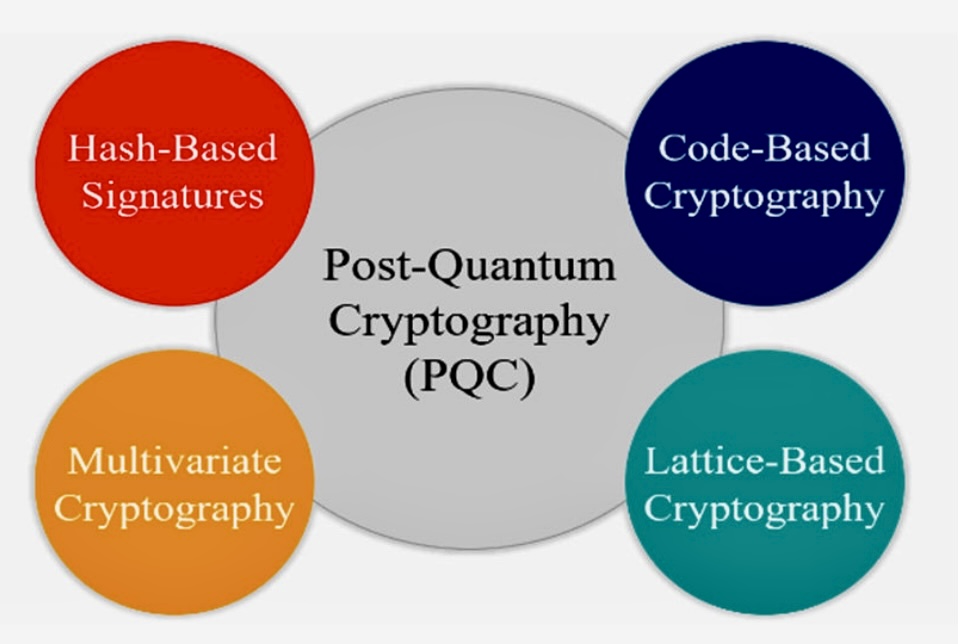
ii. Types of Post-quantum Cryptography
There are several different types of PQC algorithms, each with its own strengths and weaknesses.
key aspects of post-quantum cryptography:
A. Quantum Threat: Shor’s Algorithm: Quantum computers, specifically Shor’s algorithm, have the potential to efficiently solve certain mathematical problems (e.g., integer factorization and discrete logarithms), which are fundamental to widely used cryptographic schemes like RSA and ECC.
B. Algorithmic Diversity: Search for Quantum-Resistant Algorithms: Researchers are exploring new cryptographic algorithms that are believed to be secure against quantum attacks. This includes lattice-based cryptography, hash-based cryptography, code-based cryptography, and multivariate polynomial cryptography.
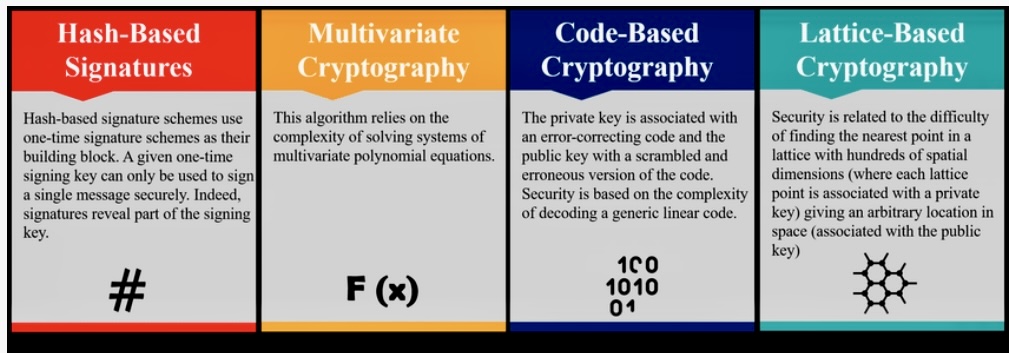
C. Lattice-Based Cryptography: Lattice Problems: Lattice-based cryptography relies on the complexity of certain mathematical problems related to lattice structures. It is considered a promising candidate for post-quantum cryptography due to its resistance to quantum attacks.
D. Hash-Based Cryptography: One-Time Signatures: Hash-based cryptography leverages hash functions to provide quantum-resistant digital signatures. It relies on the security of hash functions and is considered a relatively mature approach.
E. Code-Based Cryptography: Error-Correcting Codes: Code-based cryptography is based on the difficulty of decoding certain linear error-correcting codes. It offers a level of quantum resistance and is being explored for digital signatures and key exchange.
F. Supersingular Elliptic Curve Isogeny Cryptography: A form of public-key cryptography that involves computing isogenies between supersingular elliptic curves, a task considered difficult even for quantum computers.
G. Multivariate Polynomial Cryptography: Algebraic Equations: Multivariate polynomial cryptography involves solving systems of multivariate polynomial equations, making it resistant to Shor’s algorithm. It is used for digital signatures and public key encryption.
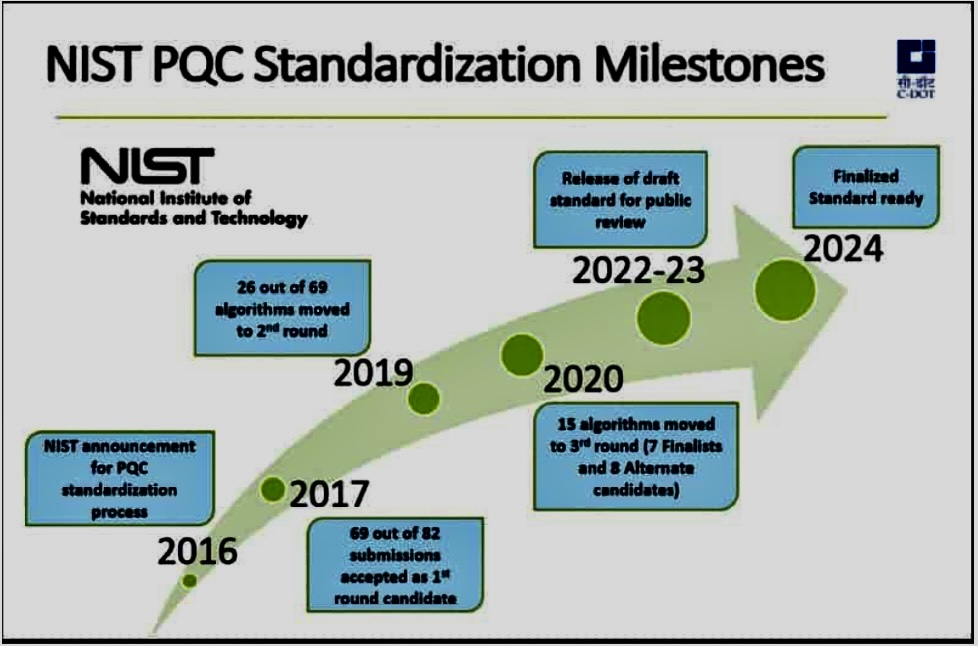
H. NIST’s Post-Quantum Cryptography Standardization: Competition: The National Institute of Standards and Technology (NIST) initiated a process to standardize post-quantum cryptographic algorithms. The NIST PQC Standardization project aims to identify and standardize quantum-resistant algorithms for various cryptographic purposes.
I. Integration Challenges: Transition Period: Implementing post-quantum cryptography in existing systems poses challenges due to the need for a smooth transition. Hybrid cryptographic schemes and protocols that combine classical and post-quantum algorithms are being explored.
J. Quantum Key Distribution (QKD): Secure Communication Channels: QKD leverages the principles of quantum mechanics to establish secure communication channels. While not a direct replacement for traditional cryptography, it offers a quantum-resistant approach to key exchange.
K. Awareness and Preparation: Industry Readiness: Organizations are encouraged to be aware of the potential risks posed by quantum computing to existing cryptographic systems and to prepare for the eventual transition to post-quantum cryptography.
L. Ongoing Research and Development: Collaborative Efforts: Researchers and cryptographic communities globally are actively involved in ongoing research and development to explore new quantum-resistant algorithms and cryptographic approaches.
M. Timeline Considerations: Quantum Computing Development: The adoption of post-quantum cryptography is closely tied to the development timeline of quantum computers. The transition is expected to occur gradually as quantum computing capabilities advance.
It is important to note that none of these algorithms have been proven unconditionally secure, and many are relatively new and have not yet been subjected to decades of cryptanalysis like traditional algorithms. Therefore, post-quantum cryptography remains an active and important area of research.
iii. Standardization of Post-quantum Cryptography
The National Institute of Standards and Technology (NIST) is currently in the process of standardizing PQC algorithms. This process involves selecting a number of promising PQC algorithms and subjecting them to a rigorous public review process. The goal of this process is to select a set of PQC algorithms that are secure, efficient, and interoperable.
iv. Adoption of Post-quantum Cryptography
The adoption of PQC is still in its early stages, but it is slowly increasing. Some organizations have already begun to deploy PQC algorithms, and others are planning to do so in the near future. The adoption of PQC is likely to accelerate as quantum computers become more powerful and the threat of attacks against classical cryptography becomes more real.
Post-quantum cryptography is a critical area of research and development as the field of quantum computing progresses. The goal is to ensure the long-term security of digital communications and information in a world where quantum computers could potentially compromise current cryptographic mechanisms.
https://www.mitre.org/news-insights/news-release/post-quantum-cryptography-coalition-launches
