Bridging the Gap: Augmenting Diversity, Equity, and Inclusion (DEI) Programs with the SFIA Framework for a More Inclusive Digital Future
In the realm of Diversity, Equity, and Inclusion (DEI), organizations are continually searching for more impactful methods to ensure all employees are not only represented but also equipped for success.
However, in today’s increasingly digital world, simply focusing on diversity isn’t enough.
Organizations need to ensure their DEI programs address the digital skills gap and empower a diverse workforce to thrive in the digital age.
This is where the Skills Framework for the Information Age (SFIA) comes in.
i. The Challenge: The Digital Skills Gap and Underrepresented Groups

Underrepresented groups often face barriers to acquiring digital skills, leading to a digital skills gap. This can exacerbate existing inequalities and limit career opportunities. Here’s how:
o Limited Access to Training: Underrepresented groups might have limited access to high-quality digital skills training due to cost, location, or other factors.
o Unconscious Bias: Bias in hiring and promotion practices can disadvantage individuals from underrepresented groups, even if they possess the necessary digital skills.
o Lack of Confidence: Individuals from underrepresented groups might lack confidence in their digital abilities, hindering their pursuit of digital skills development.
ii. The Role of SFIA in DEI
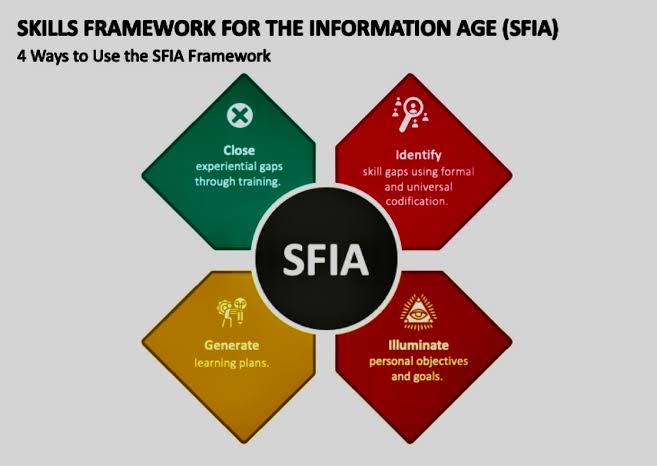
The Skills Framework for the Information Age is already recognized for its role in defining and guiding skills developments in IT and digital roles. It can similarly serve as a cornerstone for DEI programs by ensuring that all employees, regardless of background, have equitable access to skills development and advancement opportunities. SFIA facilitates a common language around skills and competencies that goes beyond traditional markers such as race, gender, or cultural background, focusing instead on the practical and professional attributes necessary for specific roles.
iii. Strategic Integration of SFIA in DEI Programs
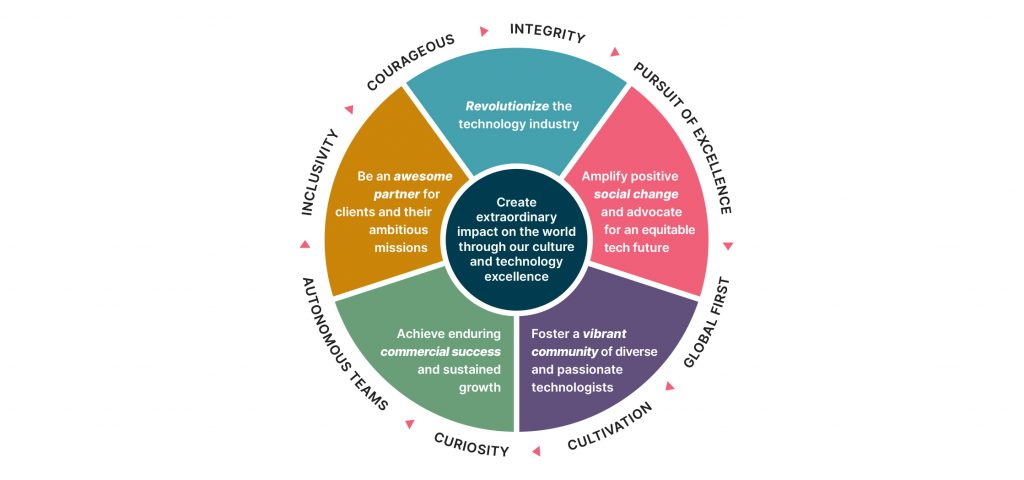
A. Skills Transparency: By clearly defining skills and competencies needed for each role, SFIA makes career paths more transparent and accessible to everyone within the organization. This transparency helps remove unconscious biases related to professional development and performance evaluations.
B. Targeted Training Programs: DEI initiatives can use the SFIA framework to identify skill gaps across different groups within an organization and tailor training programs to address these discrepancies. This approach ensures all employees have the opportunity to develop the skills they need to advance.
C. Inclusive Workforce Planning: SFIA can assist HR and DEI professionals in creating a more inclusive workforce strategy, where talent acquisition and management are aligned with the equitable development of skills across the organization’s demographic.
iv. SFIA: A Framework for Building Inclusive Digital Skills
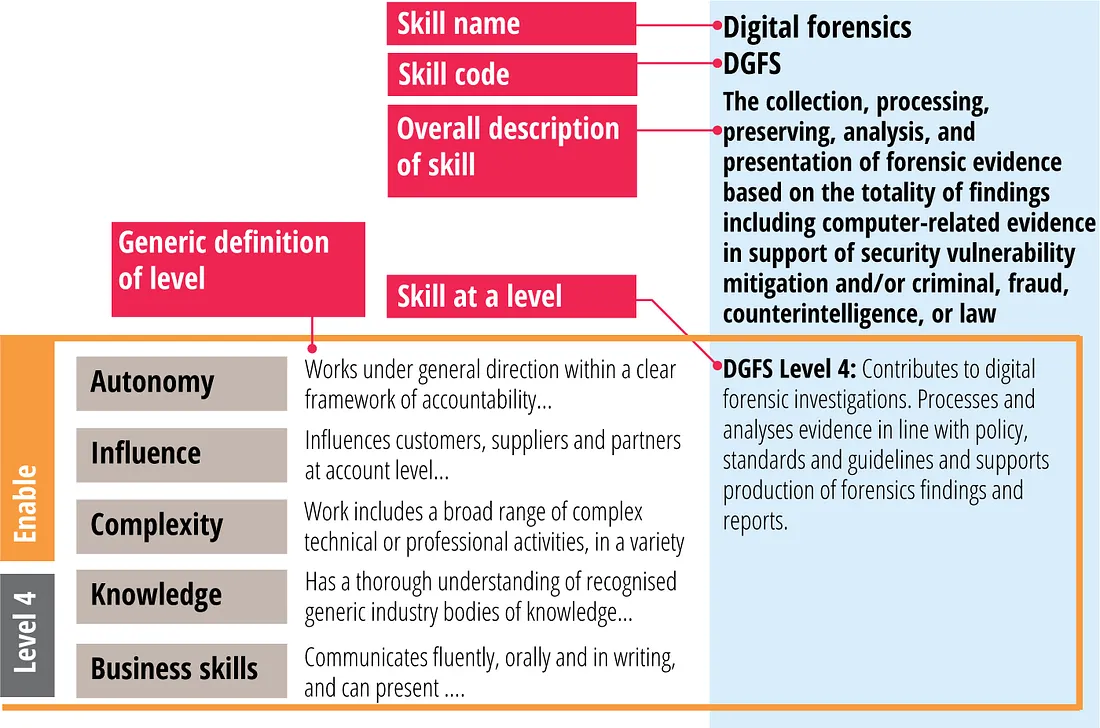
The SFIA framework offers a valuable tool for DEI programs aiming to bridge the digital skills gap:
o Standardized Skills Assessment: SFIA provides a standardized approach to assessing digital skills across different levels and roles. This helps identify the specific skills gaps within underrepresented groups.
o Targeted Skills Development: By understanding specific skill gaps, DEI programs can tailor training and development initiatives to meet the needs of diverse learners.
o Identifying Skills Gaps: The SFIA framework enables organizations to identify specific skills gaps that may exist within their teams and work towards addressing them through targeted training and development programs. For DEI efforts, this means not only addressing technical skill gaps but also identifying where there may be a lack of competencies related to cultural awareness, communication, or leadership in diverse settings. By identifying and addressing these gaps, organizations can enhance their inclusive culture and the effectiveness of their DEI initiatives.
o Promoting Confidence: SFIA’s clear skill level definitions help individuals from underrepresented groups track their progress and build confidence in their digital abilities.
o Personalized Development Plans: A key aspect of promoting equity within the workplace is recognizing that each individual has unique development needs and career aspirations. The SFIA framework supports the creation of personalized development plans that align with an individual’s current competencies and their future career goals. Such an approach ensures that all employees, including those from underrepresented groups, have the support and resources they need to advance within the organization.
o Supporting Inclusive Leadership: For DEI programs to be successful, they must be championed at all levels of an organization, particularly by its leaders. The SFIA framework can help identify the specific skills and competencies that leaders need to effectively support diversity, equity, and inclusion within their teams. This might include skills related to emotional intelligence, cross-cultural communication, conflict resolution, and fostering an inclusive team environment. By developing these skills in their leaders, organizations can create a more supportive and inclusive culture across the entire organization.
v. Benefits of a Skills-Based DEI Approach
o Enhanced Employee Engagement: Employees feel more valued and understood when there is a clear path to advancement and personal growth. SFIA’s clarity in skill requirements and development paths can increase engagement and satisfaction.
o Reduced Bias: Skills-based assessments and development focus on the ability to perform and excel in specific roles, thus actively reducing the scope for bias based on identity.
o Broader Talent Pools: By valuing skills and competencies over traditional credentials, organizations can widen their talent pools, giving opportunities to individuals who may have been overlooked due to conventional hiring practices.
o Clarity and Standardization: SFIA provides a common language for describing skills and competencies across different domains. By incorporating SFIA into DEI programs, organizations can ensure clarity and standardization in the identification and development of skills related to diversity, equality, and inclusion. This common framework helps in articulating the specific skills and behaviors required to promote diversity and foster an inclusive culture.

o Alignment with Best Practices: SFIA is widely recognized and used by organizations globally, making it an ideal framework for aligning DEI initiatives with industry best practices. By mapping DEI program objectives and activities to SFIA’s skill descriptions, organizations can ensure that their efforts are aligned with established standards and benchmarks. This alignment helps in focusing DEI efforts on areas that are most impactful and relevant to organizational goals.
o Structured Skill Development: SFIA offers a structured approach to skill development, with clear competency levels ranging from foundational to mastery. By integrating SFIA into DEI programs, organizations can provide employees with a roadmap for developing diversity, equality, and inclusion-related skills. This structured approach enables employees to track their progress and identify areas for growth in promoting diversity and fostering inclusion within the workplace.
o Personalized Learning Paths: SFIA’s multi-level structure allows organizations to tailor DEI programs to the specific needs and aspirations of individual employees. By assessing employees’ current skill levels and career goals against SFIA’s proficiency levels, organizations can design personalized learning paths that address their unique development needs. This personalized approach enhances employee engagement and ownership in DEI initiatives.
o Measurement and Evaluation: SFIA provides a framework for measuring and evaluating the effectiveness of DEI programs. By using SFIA’s skill descriptions as a basis for assessment, organizations can track progress and identify areas for improvement in promoting diversity, equality, and inclusion. This data-driven approach enables organizations to make informed decisions and adjustments to their DEI strategies, ensuring continuous improvement over time.
vi. Case Studies: DEI Success with SFIA

Several leading organizations have successfully used SFIA to bolster their DEI efforts:
o A tech company implemented SFIA to identify and close skill gaps for underrepresented groups in their engineering department, resulting in a 45% increase in representation in leadership roles within those groups over three years.
o A multinational corporation used SFIA to standardize hiring criteria across its global branches, significantly increasing the diversity of its hires by focusing strictly on essential skills and removing biased criteria.
vii. Integrating SFIA into DEI Programs: A Practical Approach
Here’s how organizations can integrate SFIA into their DEI programs:
o Conduct a Skills Gap Analysis: Use SFIA to assess the digital skills of your workforce, paying particular attention to underrepresented groups.
o Develop Targeted Training Programs: Offer training programs that address the identified skills gaps, considering different learning styles and accessibility needs.
o Promote Mentorship and Sponsorship: Connect individuals from underrepresented groups with mentors or sponsors who can provide guidance and support in their digital skills development journey.
o Track Progress and Celebrate Success: Monitor the progress of DEI programs and celebrate successes to keep participants motivated.
viii. Challenges and Considerations

Employing SFIA within DEI programs requires careful consideration. Organizations must be prepared to continuously update and adapt the skills framework to reflect the changing technological landscape and the evolving needs of their workforce. Moreover, integration of SFIA needs to be executed with sensitivity and awareness of its implications on DEI goals to avoid reinforcing existing disparities.
ix. The Road Ahead: Building a More Inclusive Digital Future
By integrating SFIA into DEI programs, organizations can create a more inclusive digital workplace. This benefits everyone:
o Enhanced Innovation and Problem-solving: A diverse workforce with strong digital skills fosters a culture of innovation and leads to more effective problem-solving.
o Improved Employee Engagement: Employees from underrepresented groups who feel empowered by their digital skills are more likely to be engaged and productive.
o Enhanced Brand Reputation: Organizations committed to a diverse and digitally skilled workforce can attract top talent and strengthen their brand reputation.
x. Conclusion

Augmenting DEI programs with the SFIA framework is a promising approach that foregrounds skills and competencies in promoting workplace diversity and inclusion.
This approach not only aids in creating a more equitable and competitive environment but also aligns with broader organizational goals of innovation and excellence.
SFIA is not a one-size-fits-all solution, but it provides a valuable framework for building a more inclusive digital future.
By integrating SFIA with DEI programs, organizations can empower a diverse workforce to thrive in the digital age and unlock its full potential.
Focusing on what employees can learn and achieve; companies can foster a truly inclusive culture that actively contributes to their success.
xi. Further references
Diversity And Inclusion Training | Develop An Inclusive Mindsetharvardonline.harvard.eduhttps://harvardonline.harvard.edu
Workplace Neurodiversity | Detailed Workplace ReportsGreen Cross Traininghttps://www.greencrossglobal.co.uk
Augmenting DEI Programs with the SFIA FrameworkLinkedIn · John Kleist III7 reactions · 1 month ago
Diversity And Inclusion Training | Harvard Onlineharvardonline.harvard.eduhttps://harvardonline.harvard.edu
About SFIA — EnglishSFIAhttps://sfia-online.org › about-sfia › about-sfia