
The Cybersecurity Trifecta: Capability, Control, and Function
In the digital age, where data breaches and cyber-attacks have become commonplace, understanding the intricate layers of cybersecurity is essential for shielding informational assets and ensuring operational integrity.
As organizations grapple with an ever-evolving threat landscape, understanding the intricate relationship between cybersecurity capability, control, and function becomes paramount.
These three elements are interlinked and play a crucial role in safeguarding sensitive information, maintaining operational integrity, and ensuring business continuity.
i. Cybersecurity Capability
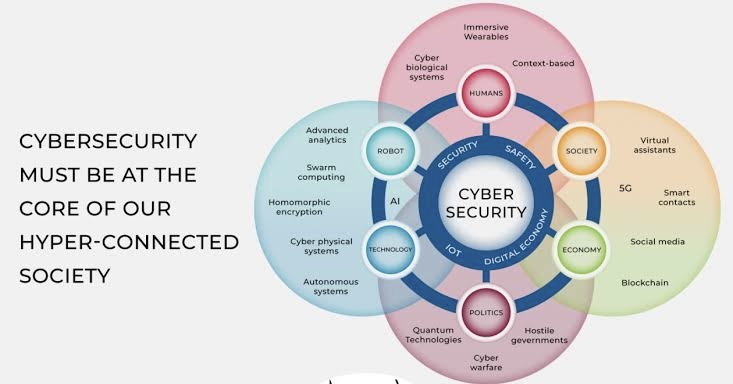
A. Protection of digital assets
Cybersecurity capability refers to an organization’s overall capacity to protect its digital assets from malicious actors and threats. It encompasses a range of components, including technology, processes, people, and resources. A robust cybersecurity capability empowers organizations to detect, prevent, and respond to cyber threats effectively. This includes the tools, technologies, processes, and human expertise employed to protect digital assets. Capabilities encompass a range of activities from threat detection to response and recovery, and they are indicative of an organization’s readiness to handle cyber incidents effectively.
B. Key aspects of cybersecurity capability include:
o Technology: Advanced tools and software that aid in the detection, prevention, and mitigation of cyber threats.
o Processes: Well-defined procedures that guide actions and decision-making in response to various cybersecurity incidents.
o People: Skilled personnel who possess the expertise to implement security measures, respond to incidents, and adapt to the evolving cyber threat landscape.
ii. Cybersecurity Control
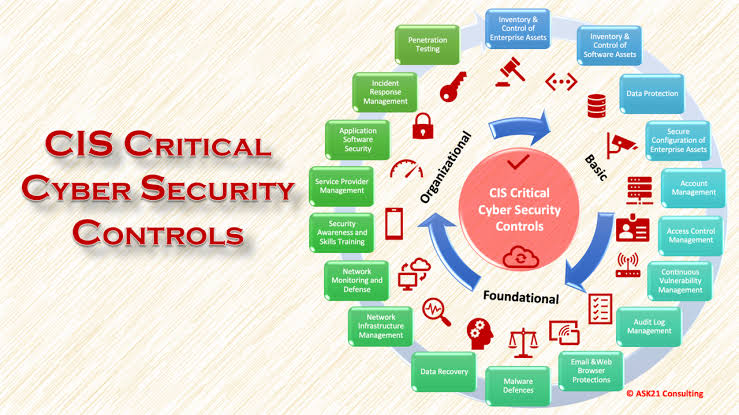
A. Mechanisms and Measures to Mitigate Risks
Control in cybersecurity refers to the mechanisms and measures implemented to manage and mitigate risks effectively. It encompasses a range of activities, including access controls, authentication mechanisms, encryption protocols, and monitoring systems. Controls are essential for enforcing security policies, minimizing vulnerabilities, and safeguarding critical assets from unauthorized access or exploitation.
Access controls, such as role-based access control (RBAC) and least privilege principle, ensure that users have the necessary permissions to perform their roles while restricting access to sensitive information. Encryption plays a vital role in protecting data both at rest and in transit, rendering it unreadable to unauthorized parties. Additionally, continuous monitoring and logging enable organizations to detect anomalous activities and potential security breaches in real-time, facilitating prompt response and remediation efforts.
B. These controls can be categorized into three main types:
preventive, detective, and corrective. Preventive controls aim to stop cyber incidents before they occur, detective controls help identify and monitor potential threats, and corrective controls restore systems and data in the aftermath of a security breach.
Controls are the tangible representation of an organization’s cybersecurity capabilities. They are the tools through which capabilities are exercised and manifest in the operational environment. Implementing effective cybersecurity controls requires a deep understanding of the organization’s assets, threat landscape, and the potential impact of cyber incidents.
iii. Cybersecurity Function
A. Operational Aspects of Safeguarding Digital Assets
The function of cybersecurity revolves around the operational aspects of safeguarding digital assets and ensuring the resilience of organizational processes. It encompasses various functions, including risk management, incident response, compliance, and governance. A well-functioning cybersecurity program integrates these functions seamlessly to mitigate threats and minimize the impact of cyber incidents.
B. Driven from Cybersecurity Frameworks Cybersecurity
functions, derived from frameworks such as the NIST Cybersecurity Framework, encapsulate the overarching categories of activities involved in managing and mitigating cyber risk. These functions include Identify, Protect, Detect, Respond, and Recover, providing a holistic view of an organization’s cybersecurity efforts.
iv. The Relation Among Capability, Control, and Function
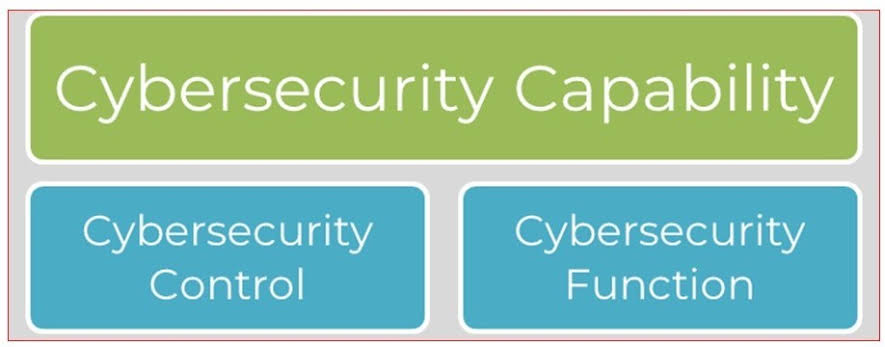
The relationship between capability, control, and function in cybersecurity can be viewed as a framework for constructing a comprehensive defense mechanism against cyber threats.
A. Capability as the Foundation: Capability forms the bedrock upon which controls are established and functions are executed. Without the right capabilities — in terms of technology, skills, and knowledge — controls may be inadequately designed, and functions improperly executed. Building capacity is an ongoing process, involving regular training, updates to technologies, and adoption of best practices.
B. Control as the Implementation: Once an organization understands its capabilities, the next step is to implement controls that align with these capabilities. Controls are direct outcomes of the strategies adopted to use the organization’s cybersecurity capabilities effectively. Whether it’s encrypting data, securing network perimeters, or implementing multi-factor authentication, controls operationalize the cybersecurity strategy.
C. Function as the Execution: Functions bring to life the controls established by utilizing the underlying capabilities. This involves the day-to-day activities of monitoring network traffic, conducting security audits, responding to incidents, and recovering from attacks. Functions are where the plan meets practice, and they require continuous refinement and adjustment based on evolving threats and organizational changes.
v. The Interdependence
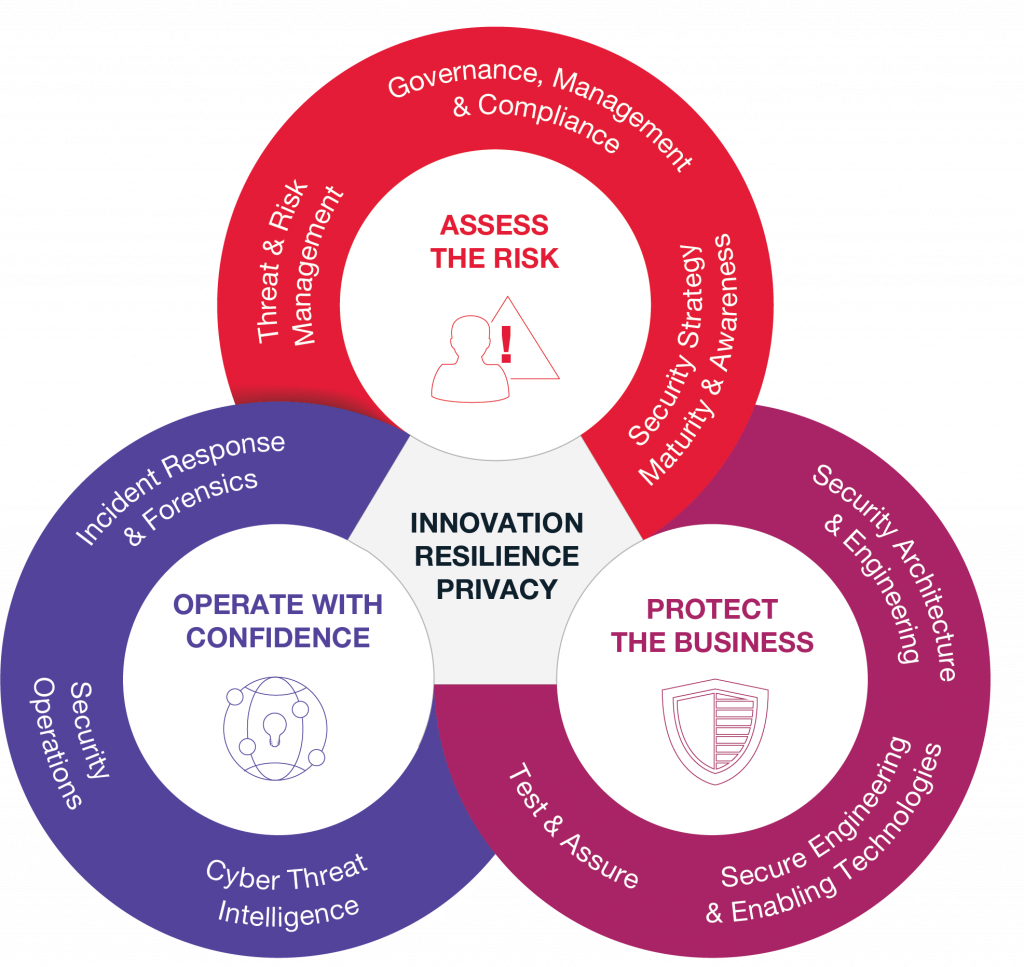
These three elements are interdependent. Strong cybersecurity capability allows for effective controls, which in turn safeguard critical functions. Let’s explore this further:
o Capability as the Foundation: A robust cybersecurity posture requires a comprehensive understanding of threats and vulnerabilities. This capability empowers organizations to implement the right controls.
o Controls in Action: Effective controls translate capability into action. Firewalls, intrusion detection systems, and access controls are examples that mitigate risks and protect functions.
o Protecting Functionality: Ultimately, cybersecurity safeguards an organization’s ability to function. Secure systems ensure data integrity, operational continuity, and protection of sensitive information.
vi. Enhancing the Triad for Robust Cybersecurity
Strengthening the relationship and coherence among capability, control, and function involves several key considerations:
o Continuous Assessment and Improvement: Cybersecurity is not a set-it-and-forget-it affair. Continuous assessment of capabilities, controls, and functions, followed by necessary improvements, ensures that the cybersecurity measures evolve in tandem with changing threat landscapes.
o Integration Across the Enterprise: Cybersecurity should not be siloed. Integrating cybersecurity considerations into all aspects of the business, from IT to operations, human resources, and beyond, ensures a cohesive and comprehensive approach.
o Adaptation to Emerging Threats and Technologies: The digital world is dynamic, with new threats and technologies emerging regularly. Staying informed and adapting the cybersecurity triad to these changes is critical for maintaining robust defense mechanisms.
vii. Conclusion

In conclusion, the relationship between cybersecurity capability, control, and function is symbiotic and essential for safeguarding organizational assets and maintaining operational resilience.
By investing in robust cybersecurity capabilities, implementing effective controls, and integrating cybersecurity functions seamlessly, organizations can mitigate cyber risks effectively and adapt to the evolving threat landscape.
Ultimately, a proactive and holistic approach to cybersecurity is paramount in safeguarding against cyber threats and preserving trust and confidence in digital ecosystems.
viii. Further references
What Is the Relation Between Cybersecurity Capability, Control, and Function? – LinkedIn
LinkedIn · Marc D.10+ reactions · 6 months agoCyber Security controls types and functions
PwChttps://www.pwc.com › publicationsA human-led and tech-enabled cybersecurity function
finantrix.comhttps://www.finantrix.com › productCybersecurity Capabilities Model – Finantrix.Com
Sprintzealhttps://www.sprintzeal.com › blogCybersecurity Controls Explained
Cybereasonhttps://www.cybereason.com › blogThe Cybersecurity Capability the Industry Nearly Forgot
Scytalehttps://scytale.ai › AllThe 5 Functions of the NIST Cybersecurity Framework
Picus Securitywww.picussecurity.comWhat Is Security Control Effectiveness?
