Risk Assessment of IT Governance: Safeguarding the Digital Foundation
In the rapidly evolving digital landscape, the governance of information technology (IT) has become a critical aspect for organizations worldwide.
Governance, in the context of IT, involves the framework and processes that ensure IT resources are utilized effectively and align with the organization’s objectives.
However, with increased reliance on IT systems, the potential risks also escalate, necessitating comprehensive risk assessments to safeguard organizational integrity, prevent data breaches, and ensure continuity of operations.
i. Understanding IT Governance
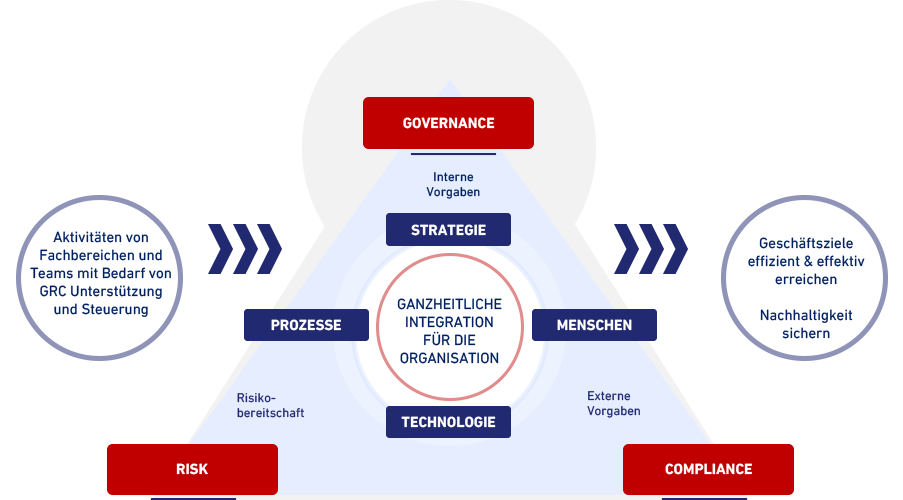
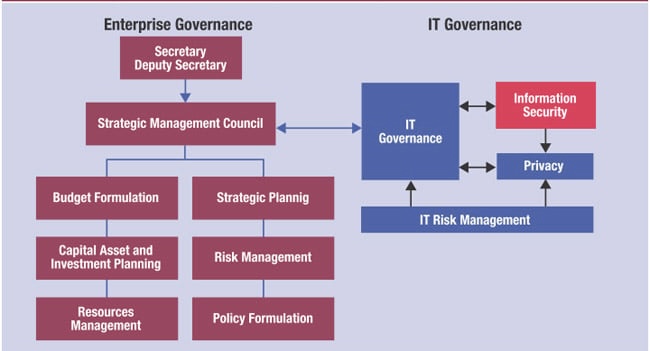
o IT governance is a subset of corporate governance focusing on IT systems and their performance and risk management.
o The primary goal of IT governance is to ensure that the IT infrastructure aligns with the overall objectives of the organization, optimizes resources, and properly manages risk.
o IT governance encompasses the policies, procedures, and structures that guide decision-making and ensure the effective use of IT resources to achieve organizational objectives. o At its core, IT governance aims to align IT strategies with business goals, optimize IT investments, and manage risks effectively.
ii. Why Risk Assess IT Governance?
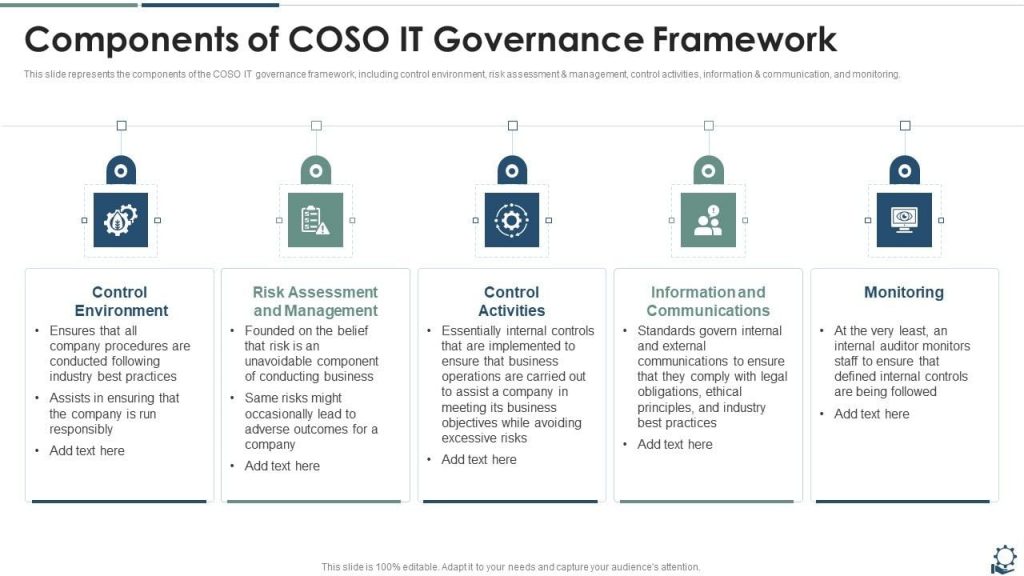
There are several compelling reasons to conduct a regular risk assessment of IT governance:
o Proactive Threat Identification: By proactively identifying vulnerabilities within your IT governance framework,you can address them before they escalate into major disruptions or security breaches.
o Improved Decision-Making: A risk assessment provides valuable data to guide IT governance decisions. You can prioritize resources and investments to address the most critical risks.
o Enhanced Regulatory Compliance: Many regulations require organizations to have a risk management program in place. A risk assessment demonstrates your commitment to IT security and compliance.
o Stakeholder Confidence: A thorough risk assessment instills confidence in stakeholders, including investors,customers, and employees, that their data and operations are secure.
iii. The Role of Risk Assessment in IT Governance
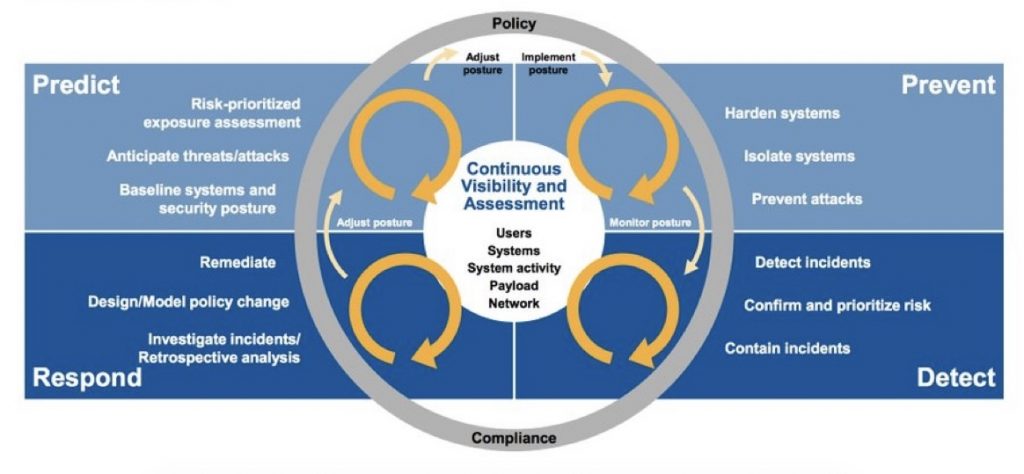
Risk assessment in IT governance is the systematic process of identifying, analyzing, and evaluating risks associated with the IT environment. This process is vital to protect assets, ensure data integrity, and align IT strategies with business objectives. The main components of risk assessment in IT governance include:
A. Identify Risks: Through systematic evaluation, organizations can identify and prioritize potential risks, including cyber threats, data breaches, system failures, and compliance issues.
B. Analyze Impact: Understanding the potential impact of identified risks is crucial for assessing their significance and developing appropriate mitigation strategies. This involves assessing the potential financial, operational, and reputational consequences of a security incident or system failure.
C. Prioritize Mitigation Efforts: Not all risks are equal, and resources are limited. Risk assessment helps organizations prioritize mitigation efforts by focusing on the most significant and probable risks that could have the greatest impact on the organization’s objectives.
D. Enhance Decision-Making: Armed with insights from risk assessment, organizations can make informed decisions about resource allocation, security investments, and strategic initiatives. This ensures that IT governance efforts are aligned with overall business priorities and risk appetite.
iv. Methodologies for Conducting IT Governance Risk Assessment
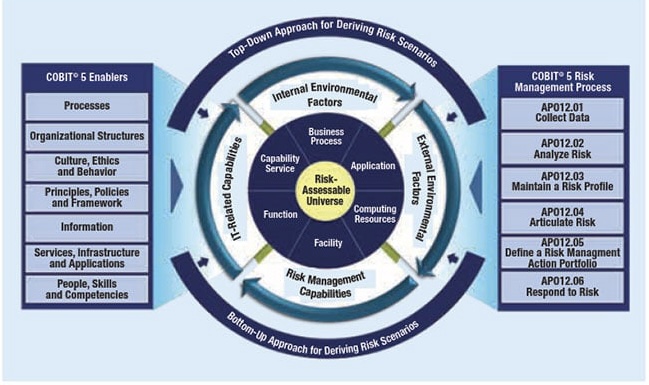
Several methodologies can be employed to perform risk assessments effectively:
o OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation): This approach focuses on organizational risk and security practices to identify IT vulnerabilities that could potentially harm the organization.
o FAIR (Factor Analysis of Information Risk): FAIR provides a model for understanding, analyzing, and quantifying information risk in financial terms. It helps organizations balance the needs to protect information with the needs to create value.
o ISACA’s Risk IT Framework: Developed by an international professional association focused on IT governance, this framework provides a thorough understanding of risks related to IT and the investments necessary to mitigate them.
v. Risk Assessment Methodologies for IT Governance
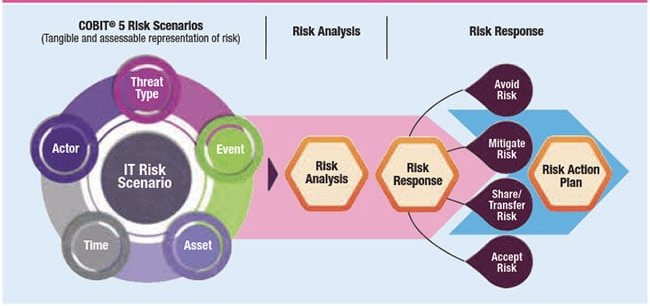
There are various methodologies for conducting a risk assessment:
o Qualitative Assessments: These methods identify risks by analyzing past incidents, industry trends, and expert opinions.
o Quantitative Assessments: These methods assign a probability and severity score to each identified risk, allowing for a more objective evaluation.
o Hybrid Approaches: Many organizations combine qualitative and quantitative methods for a more comprehensive assessment.
vi. What to Focus on During an IT Governance Risk Assessment
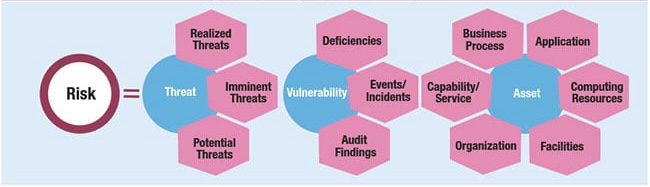
An effective IT governance risk assessment should encompass various aspects:
o Strategic Alignment: Does your IT governance framework support your overall business strategy? Are IT investments aligned with business goals?
o Security Vulnerabilities: Identify potential security weaknesses within your IT infrastructure, access controls, and data management practices.

o Operational Inefficiencies: Assess processes for IT service delivery, change management, and incident response.Identify areas for improvement to streamline operations and reduce costs.
o Compliance Gaps: Evaluate your current IT governance practices against relevant industry regulations and compliance standards.
o Third-Party Risk Management: Assess the security posture and potential risks associated with third-party vendors involved in your IT operations.
vii. The Stages of Risk Assessment in IT Governance
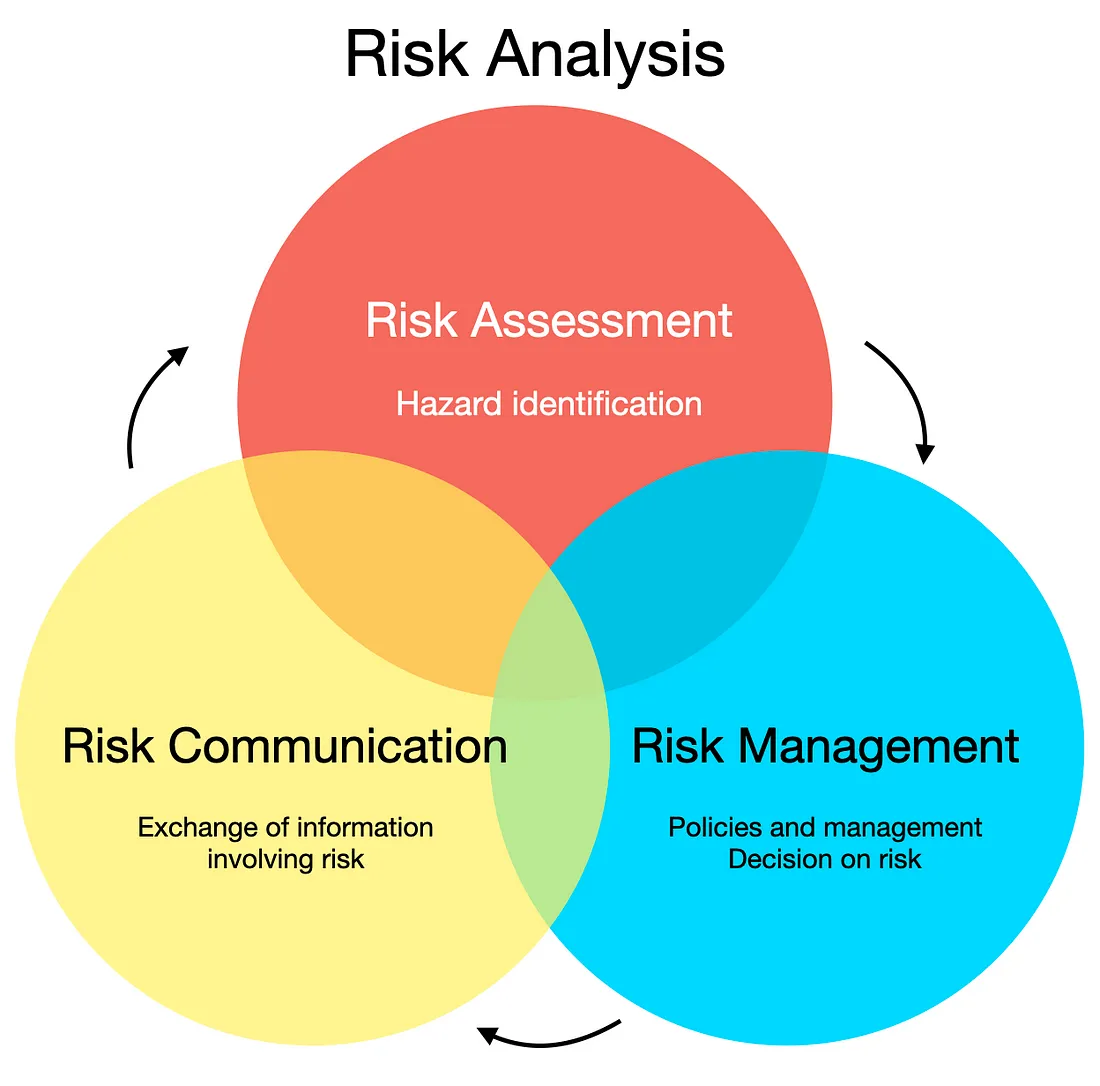
Risk assessment within IT governance can be segmented into several key stages:
A. Identification of Assets and Threats
The first step involves cataloging the organization’s IT assets, including hardware, software, data, and networks, and identifying potential threats to these assets. Threats can be internal or external, tangible or intangible, and may include malicious attacks, system failures, natural disasters, or human error.
B. Vulnerability Assessment
This stage entails assessing the susceptibility of IT assets to identified threats. This involves evaluating the existing security controls and identifying any weaknesses or gaps in the IT infrastructure that could be exploited.
C. Impact Analysis
Impact analysis quantifies the potential damage that could result from a threat exploiting a vulnerability. This includes considering both direct impacts, such as financial loss and disruption of services, and indirect impacts, such as reputational damage.
D. Risk Evaluation
This phase involves combining the information from the vulnerability assessment and impact analysis to evaluate the overall risk to the organization’s IT assets. Risks are typically prioritized based on their likelihood and the severity of their impact.
E. Mitigation Strategies
Based on the risk evaluation, organizations then develop and implement mitigation strategies to manage identified risks. These strategies may involve enhancing security measures, improving system configurations, revising policies and procedures, and conducting regular training and awareness programs.
F. Monitoring and Review
Finally, the effectiveness of the risk mitigation strategies is monitored, and the risk assessment process is periodically reviewed to ensure it remains relevant in the face of changing threats and business objectives.
viii. Best Practices for IT Governance Risk Assessment
o Regular Assessments: Conduct risk assessments regularly to ensure new and evolving risks are recognized and addressed promptly.
o Broad Involvement: Include stakeholders from multiple departments to ensure all potential risks are examined from various perspectives.
o Use of Technology: Leverage software tools for risk assessment that can provide real-time analysis and enhance decision-making capabilities.
o Risk Appetite Definition: Clearly define the organization’s tolerance for risk to guide the risk management process.
ix. Beyond the Assessment: Taking Action
A risk assessment is only the first step. Following through with mitigation strategies is essential. This involves:
o Developing Action Plans: Create specific action plans for each identified risk, outlining mitigation strategies,resource allocation, and timelines.
o Implementing Robust Security Measures: Such as firewalls, intrusion detection systems, and comprehensive cybersecurity protocols.
o Continuous Monitoring and Improvement: Risk assessments should be conducted regularly to assess the effectiveness of mitigation strategies and identify any emerging threats.
o Communication and Awareness: Keep all stakeholders informed about IT governance risks and ongoing mitigation efforts. This fosters a culture of security awareness within the organization.
o Disaster Recovery Planning: Develop and test disaster recovery plans to ensure quick restoration of IT services in case of a significant incident.
x. Conclusion
In conclusion, risk assessment plays a vital role in the effective governance of information technology. It is an ongoing process, not a one-time event.
By systematically identifying, analyzing, and mitigating risks, organizations can safeguard their IT assets, enhance decision-making, and achieve their business objectives in a rapidly evolving digital landscape.
Embracing a proactive approach to risk assessment is essential for organizations seeking to navigate the complexities of IT governance and ensure long-term success.
xi. Further references
IT Governance and Risk Management | Focal Point Data Risk
PwChttps://www.pwc.com › it-grcIT Governance, Risk and Compliance (IT GRC)
Medium · BeccaElle10+ likes · 6 months agoIT Governance and Risk Management | by BeccaElle
IT Governance Ltdhttps://www.itgovernance.co.uk › ermEnterprise Risk Management
heflo bpmhttps://www.heflo.com › blog › it-g…IT governance and risk management: Control …
ResearchGatehttps://www.researchgate.net › 227…(PDF) Risk Management in IT Governance Framework
COREhttps://core.ac.uk › pdfPDFRisk Management in IT Governance Framework
ISACAwww.isaca.orgHolistic IT Governance, Risk Management, Security and Privacy …
KPMGhttps://kpmg.com › home › advisoryIT Governance – IT Risk Management
PwChttps://www.pwc.com › rcs › it-grcIT Governance, Risk and Compliance (IT GRC)
