Charting Your Course: How to Prepare for the CIO Role
The role of the Chief Information Officer (CIO) is more critical than ever in today’s technology-driven business landscape. A CIO not only manages the IT department but also plays a pivotal role in shaping the company’s strategic direction. Preparing for this role requires a blend of technical expertise, leadership skills, and strategic vision.
Here’s a, somewhat, comprehensive guide on how to prepare for the CIO role.
i. Business Acumen

- Cultivate a Deep Understanding of the Business
- Go Beyond Technology:
- While technical expertise remains crucial, a successful CIO understands the intricacies of the business they serve. Gain a thorough understanding of your organization’s goals, challenges, and competitive landscape.
- Think Strategically:
- CIOs need to translate business strategy into actionable technology strategies. Hone your strategic thinking skills and learn to develop technology roadmaps aligned with the organization’s overall objectives.
- Go Beyond Technology:
- Understand Business Strategy
- Align IT with Business Goals:
- Gain a thorough understanding of your company’s business model, industry, and competitive landscape.
- Learn how to align IT initiatives with broader business objectives to drive growth and innovation.
- Financial Acumen:
- Develop financial skills to manage budgets, evaluate ROI, and make cost-effective decisions.
- Understand the financial implications of technology investments and how they contribute to the company’s bottom line.
- Align IT with Business Goals:
- Build a Strategic Vision
- Think Long-Term:
- Develop the ability to foresee future technology trends and their potential impact on the business.
- Create a strategic roadmap for IT that supports the company’s long-term goals.
- Foster Innovation:
- Encourage a culture of innovation within the IT department.
- Explore new technologies and processes that can improve efficiency and drive competitive advantage.
- Think Long-Term:
- Gain Experience in Risk Management and Compliance
- Prioritize Cybersecurity
- With increasing cyber threats, CIOs must ensure robust cybersecurity measures are in place. Obtain certifications like CISSP (Certified Information Systems Security Professional) and stay updated on the latest security protocols and threats.
- Ensure Regulatory Compliance
- Stay informed about industry regulations and compliance standards relevant to your sector. Develop policies and protocols to ensure that IT operations comply with these regulations, reducing the risk of legal and financial penalties.
- Prioritize Cybersecurity
ii. Technology Expertise
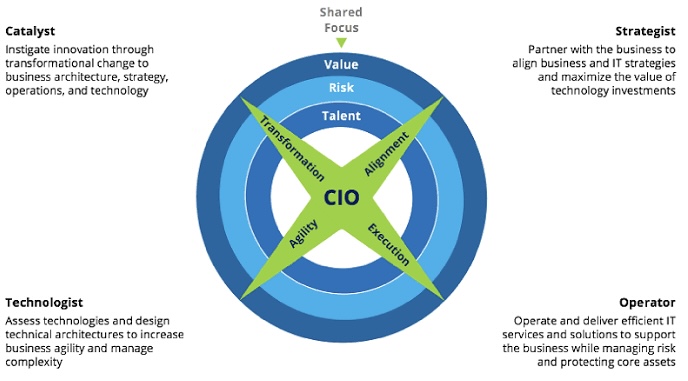
- Sharpen Your Technology Acumen
- Master Core IT Disciplines:
- Ensure a deep understanding of key IT areas such as cybersecurity, data management, cloud computing, and enterprise software.
- Stay current with emerging technologies like artificial intelligence, machine learning, and blockchain to anticipate and leverage technological trends.
- Gain Hands-On Experience:
- Work in various IT roles to build a solid foundation in different technical domains.
- Participate in projects that involve implementing new technologies, managing system integrations, and overseeing IT infrastructure improvements.
- Master Core IT Disciplines:
iii. Leadership Skills

- Cultivate Leadership Skills
- Enhance Your Soft Skills:
- Develop strong communication skills to articulate technical concepts to non-technical stakeholders.
- Build emotional intelligence to manage and motivate your team effectively.
- Lead by Example:
- Take on leadership roles within your current organization to demonstrate your ability to manage teams and projects.
- Show a commitment to continuous learning and professional development.
- Enhance Your Soft Skills:
iv. Experience and Credibility
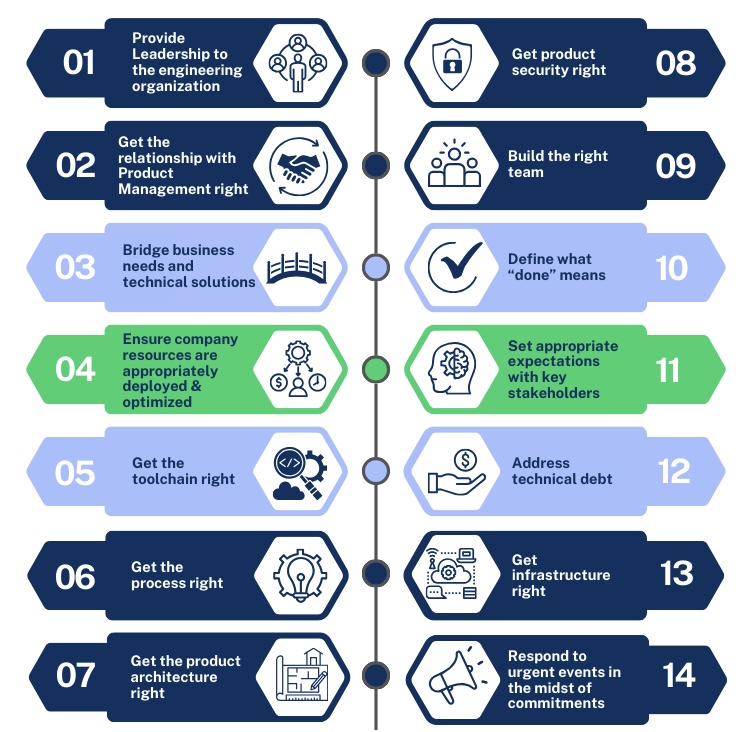
- Gain Experience and Demonstrate Your Skills
- Seek Leadership Opportunities:
- Look for opportunities to lead IT projects or initiatives within your current organization. This allows you to demonstrate your leadership skills and ability to deliver results.
- Consider Additional Certifications:
- While not mandatory, pursuing certifications relevant to the CIO role, such as Certified Information Systems Security Professional (CISSP) or Certified Information Technology Professional (CITP), can demonstrate your commitment to continuous learning and enhance your credibility.
- Seek Leadership Opportunities:
- Network and Build Relationships
- Expand Your Professional Network:
- Join professional organizations and attend industry conferences to connect with other IT leaders.
- Participate in forums and online communities to share knowledge and learn from peers.
- Build Cross-Functional Relationships:
- Collaborate with other departments to understand their needs and challenges.
- Foster strong relationships with key stakeholders, including executives, to ensure alignment and support for IT initiatives.
- Expand Your Professional Network:
v. Continuous Learning

- Pursue Continuous Learning
- Stay Updated:
- Keep abreast of the latest developments in technology and business.
- Read industry publications, attend webinars, and enroll in relevant courses to stay informed.
- Certifications can validate your skills and knowledge. Some valuable certifications include:
- CIO Certification: Programs like the Certified Chief Information Officer (CCIO) provide tailored training for aspiring CIOs.
- Project Management Professional (PMP): Focuses on project management skills.
- Certified Information Systems Security Professional (CISSP): Emphasizes cybersecurity expertise.
- Advanced Education:
- Consider pursuing advanced degrees or certifications in IT management, cybersecurity, or business administration.
- Programs like an MBA or a Master’s in Information Systems can provide valuable knowledge and credentials.
- Stay Updated:
vi. Diverse Experience
- Gain Diverse Experience
- Rotate Across IT Functions
- Experience in various IT roles can provide a well-rounded understanding of the field. Seek opportunities in:
- Infrastructure Management: Oversee hardware, software, and network infrastructure.
- Application Development: Manage software development projects and teams.
- IT Operations: Ensure the smooth operation of IT services and systems.
- Cybersecurity: Lead initiatives to protect the organization’s data and systems.
- Experience in various IT roles can provide a well-rounded understanding of the field. Seek opportunities in:
- Cross-Functional Collaboration
- Work closely with other departments such as finance, marketing, and operations. This experience will enhance your understanding of how IT supports different areas of the business and build your strategic thinking.
- Rotate Across IT Functions
vii. Change Management
- Gain Experience in Change Management
- Lead Transformational Projects:
- Take charge of initiatives that involve significant changes, such as digital transformation projects.
- Learn how to manage resistance to change and ensure smooth transitions.
- Understand Organizational Dynamics:
- Study how different departments interact and how changes in IT can impact the entire organization.
- Develop strategies to manage these dynamics effectively.
- Lead Transformational Projects:
viii. Conclusion
The Journey to becoming a CIO is a marathon, not a sprint. By focusing on these key areas, you can develop the skills and experience necessary to excel in this critical leadership role. Remember, a successful CIO is not just a tech expert; they are a strategic business partner who drives innovation and empowers their organization to thrive in the digital age.
Preparing for the role of CIO is a multifaceted journey. It requires a blend of technical expertise, strategic thinking, business acumen, and leadership skills. By committing to continuous learning, building a versatile skill set, and fostering a forward-thinking mindset, aspiring CIOs can position themselves to effectively lead their organizations through the complexities of the digital landscape. As the bridge between technology and business, the CIO plays a pivotal role in ensuring that technological advancements drive innovation and growth, securing the company’s place in an ever-evolving market.
ix. Further references
CIO Best Practices by Joe Stenzel, Gary Cokins, Bill Flemmingeverand.comhttps://www.everand.com
Transitioning to the CIO roleDeloittehttps://www2.deloitte.com › focus › cio-role-transition
14 power skills to succeed as a CIOCIO Divehttps://www.ciodive.com › news › 14-power-skills-CIO…
First Days on the Job as a CIOInformationWeekhttps://www.informationweek.com › IT Leadership
Instant PDF Download | Organizational Management PDFbusiness-explained.comhttps://www.business-explained.com
Protecting Information—Practical Strategies for CIOs and CISOsisaca.orghttps://www.isaca.org