
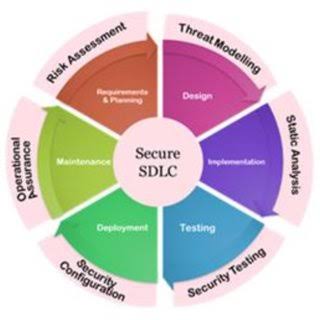
Architecture Risk Analysis (ARA) is a process that specifically focuses on identifying and addressing risks that can compromise the architecture of a software system.
i. What is ARA?
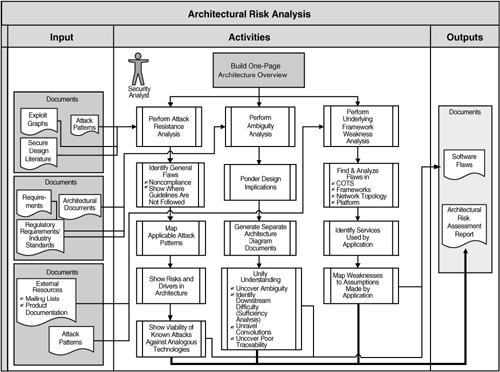
Architecture Risk Analysis (ARA) is a comprehensive review of a system’s design to identify potential security vulnerabilities and weaknesses. It aims to address security flaws early in the development process, preventing costly rework later and ensuring a more secure and resilient system.
ii. Objectives of ARA
A. Security: Ensure the architecture adequately protects assets and meets security requirements.
B. Performance: Verify the architecture can support the required performance levels under expected loads.
C. Availability and Reliability: Ensure the system design is robust, can handle faults, and maximizes uptime.
D. Maintainability and Scalability: Confirm the architecture can adapt to future changes and growth.
iii. Benefits of ARA
A. Early identification and mitigation of risks: Identifying security vulnerabilities early in the design phase saves time and resources compared to fixing them later in development or production.
B. Improved system security: ARA helps ensure that systems adhere to secure design principles, leading to a more robust and secure deployment.
C. Reduced compliance risks: By addressing security concerns early, organizations can reduce the risk of non-compliance with regulations.
D. Enhanced decision-making: ARA provides valuable insights that inform design decisions and promote a security-first approach.
E. Increased stakeholder confidence: By demonstrating a commitment to security, ARAs can build trust and confidence among stakeholders.
iv. ARA Process Steps
A. Scope Definition: Define the parts of the architecture that are to be analyzed, including the system’s components, their interactions, and security boundaries.
B. Information Gathering: Collect all relevant information about the architecture, such as design documents, threat models, workflow diagrams, and use cases.
C. Threat Identification: Recognize potential threats to the system by considering different threat agents, the value of the assets at risk, and known vulnerabilities.
D. Vulnerability Analysis: Identify weaknesses within the architecture that could be exploited by threats, such as design flaws or improper configurations.
E. Risk Assessment: Evaluate the risk level for each identified threat and vulnerability pair, often by considering the potential impact and likelihood of exploitation.
F. Mitigation Strategies: Develop strategies to reduce or eliminate risks, such as adding security controls, redesigning components, or implementing best practices.
G. Decision Documenting: Document decisions made about accepting, mitigating, transferring, or avoiding risks, including rationales for these decisions.
H. Residual Risk Analysis: Analyze and document risks that remain after mitigation strategies have been applied.
I. Action Planning: Define action items and plans to implement the chosen mitigation strategies.
J. Monitoring and Review: Establish procedures for ongoing monitoring of risks and review points to reassess the architecture as the system evolves.
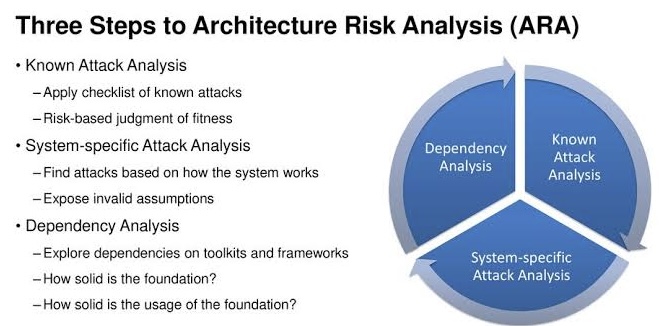
v. ARA Techniques
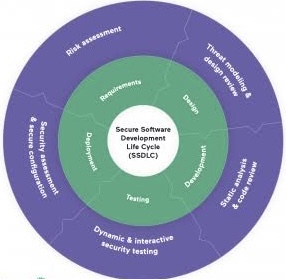
A. Dependency analysis: Identifies critical dependencies between system components and analyzes the potential impact of vulnerabilities in one component on others.
B. Known attack analysis: Examines known attack patterns and techniques to identify vulnerabilities in the system design that could be exploited.
C. System-specific analysis: Analyzes specific aspects of the system design, such as authentication mechanisms, access control, and data security controls, to identify weaknesses.
D. Threat modeling: Identifies potential threats to the system and analyzes their impact on system assets.
vi. ARA Tools and Technologies
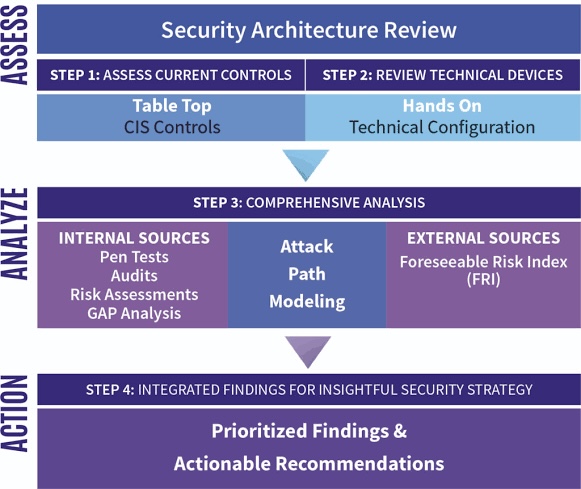
A. Security architecture modeling tools: These tools help visualize the system architecture and identify potential vulnerabilities.
B. Vulnerability scanning tools: These tools scan the system for known vulnerabilities and weaknesses.
C. Threat modeling tools: These tools help to identify and analyze potential threats to the system.
vii. Best Practices for Effective ARA
A. Involve stakeholders across the organization: Ensure key stakeholders from various departments participate in the ARA process.
B. Focus on critical assets: Prioritize the analysis of risks that could impact critical assets and data.
C. Use a structured methodology: Employ a standardized approach for conducting ARAs to ensure consistency and effectiveness.
D. Continuously monitor and update: Regularly review and update the ARA as the system evolves and new threats emerge.
E. Communicate findings and recommendations: Clearly communicate identified risks and mitigation strategies to stakeholders for informed decision-making.
viii. Tools and Techniques Used in ARA
A. Checklists: Pre-defined lists of risks, vulnerabilities, and checks specific to the architecture.
B. Modeling and Simulation: Creating models to simulate the architecture behaviors under various conditions and attacks.
C. Expert Elicitation: Leveraging the knowledge of experienced professionals in identifying and mitigating risks.
D. Automated Analysis Tools: Utilizing software tools to scan and analyze the architecture against known vulnerabilities.
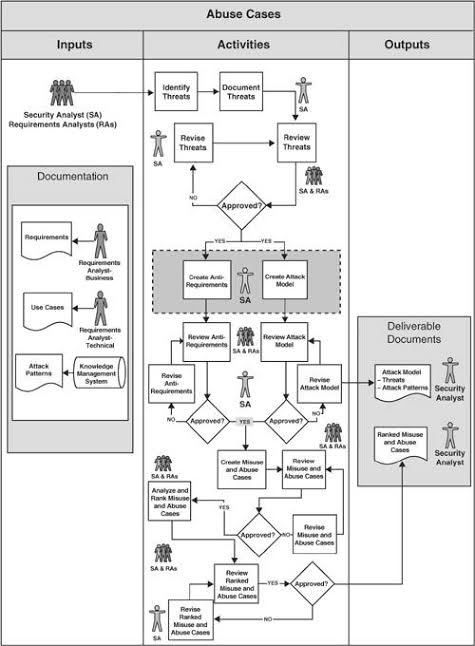
ix. Stakeholders Involved in ARA
A. Architecture Team: Ensure the architectural choices align with business objectives and risk thresholds.
B. Security Team: Provide expertise in identifying and addressing security risks.
C. Development Team: Implement necessary changes to mitigate risks.
D. Business Owners/Product managers: Understand the impact of risks on business objectives and make risk management decisions.
Architecture Risk Analysis is a process of identifying potential risks and vulnerabilities in a system architecture or design. It helps in evaluating the potential impact of risks on the system and formulating strategies to mitigate them.
ARA is an integral part of systems development and is carried out at multiple points in the system lifecycle, providing a structured technique for understanding the risk in the context of system architecture. By systematically reviewing potential risks to the architecture, stakeholders can make informed decisions about how to manage those risks in alignment with their overall risk management and business strategies.
https://www.guardrails.io/blog/security-debt-vs-technical-debt/
https://www.garymcgraw.com/wp-content/uploads/2020/02/BIML-ARA.pdf
