The IT and Security Leader’s Guide to ISO/IEC 27032: Building Cyber Resilience in the Digital Age
ISO/IEC 27032 is an international standard focusing on “Cybersecurity” or “Cyberspace Security,” which provides guidelines for enhancing the state of Cybersecurity, drawing attention to the roles and responsibilities of various stakeholders in cyberspace.
As an IT and Security Leader, understanding and implementing this guidance could be essential for protecting the organization’s information assets.

Here is a brief guide to understanding and utilizing ISO/IEC 27032:
i. Understanding ISO/IEC 27032
A. Developed by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), ISO/IEC 27032 provides best practices for cybersecurity for cloud computing services.
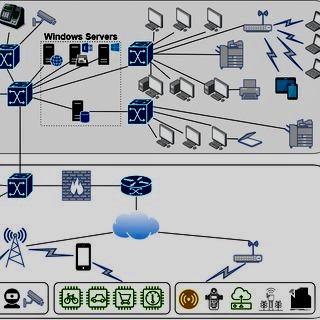
B. Scope of the Standard: ISO/IEC 27032 addresses Cybersecurity risks and controls when it comes to the internet, cloud computing, and other platforms. It is not a certifiable standard but provides guidelines for ensuring secure operation in a collaborative, interconnected environment.
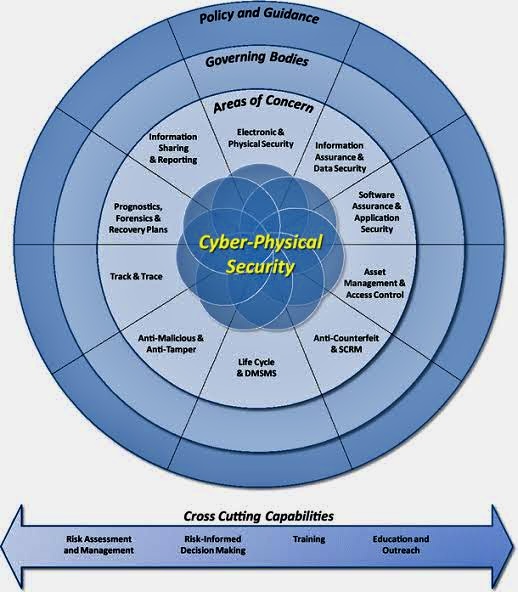
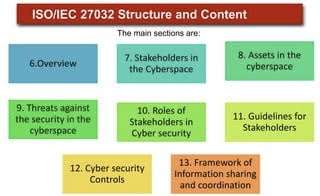
C. The standard outlines controls across 14 domains, encompassing aspects like risk assessment, security requirements, incident management, and business continuity.
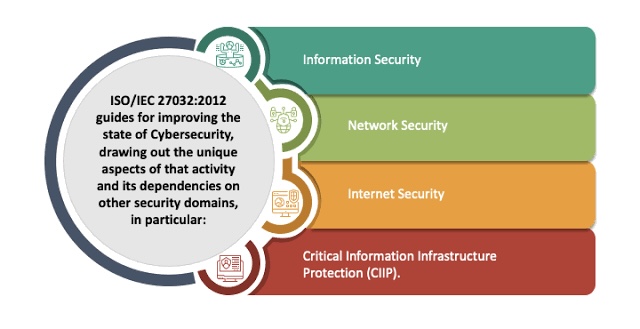
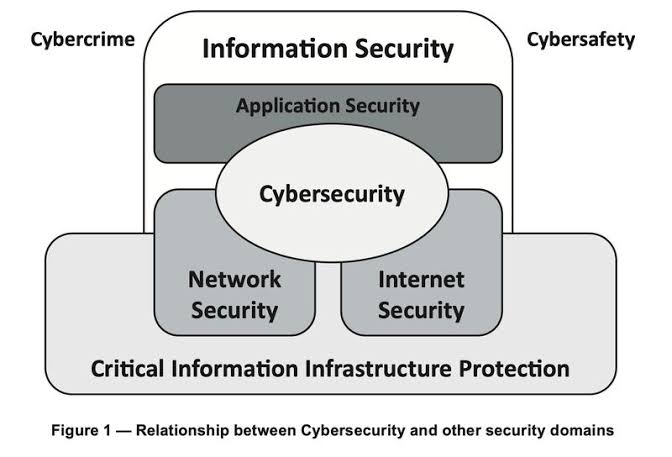
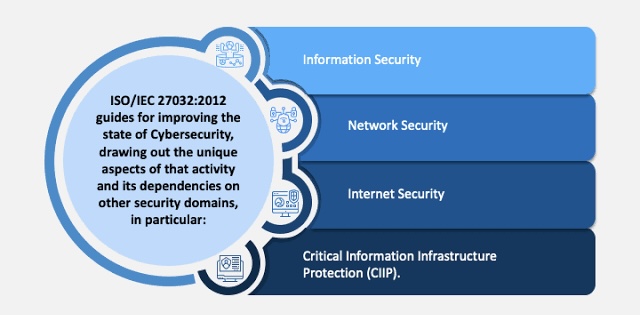
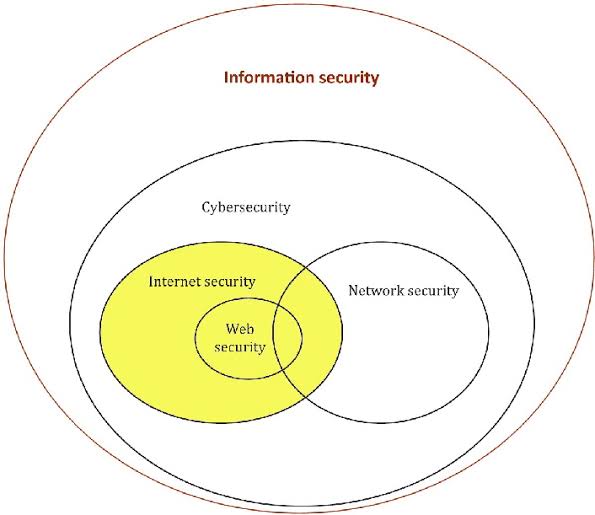
D. Cybersecurity’s Broad Landscape: The standard acknowledges that Cybersecurity is a broader concept than information security since it encompasses the internet and extends to new electronic domains like the Internet of Things (IoT) and social media.
E. Stakeholder Collaboration: It emphasizes collaboration between stakeholders, including individuals, businesses, organizations, and governments. It ensures that there is clarity on roles and responsibilities to protect the shared cyber environment.
F. Guidelines: It offers comprehensive guidance on policies and procedures, aligning technical and management practices with cybersecurity’s unique demands.
ii. Implementing ISO/IEC 27032
A. Understanding ISO/IEC 27032:
o Familiarize yourself and your team with the ISO/IEC 27032 standard. Understand its principles, objectives, and the role it plays in addressing cybersecurity challenges in cyberspace.
B. Risk Assessment and Management:
o Conduct a thorough risk assessment specific to cyberspace, considering potential threats, vulnerabilities, and the impact of cyber incidents.
o Implement risk management processes aligned with ISO/IEC 27032 to prioritize and address identified risks.
C. Establishing a Cybersecurity Policy:
o Develop a comprehensive cybersecurity policy that aligns with ISO/IEC 27032 requirements.
o Ensure that the policy addresses the organization’s commitment to cybersecurity, roles and responsibilities, and compliance with relevant laws and regulations.
D. Building a Cybersecurity Framework:
o Create a cybersecurity framework based on the guidelines provided by ISO/IEC 27032.
o Integrate the framework with existing IT and security management systems to streamline processes.
E. Engage Leadership and Stakeholders:
o Ensure executive leadership support for cybersecurity initiatives.
o Regularly communicate the importance of ISO/IEC 27032 compliance to stakeholders and demonstrate the positive impact on the organization.
F. Implement Controls: Deploy appropriate technical and organizational controls for the management of cyber risks including, but not limited to, encryption, access controls, penetration testing, and incident management frameworks.
G. Promote Cybersecurity Awareness: Cybersecurity is as much about people as it is about technology—initiate organization-wide awareness programs that inform and educate all stakeholders about cyber risks and best practices.
H. Encourage Collaboration: Facilitate collaboration internally and with external partners to ensure consistent adherence to Cybersecurity measures across all platforms and interactions.
I. Continuous Improvement: IT and security leaders must ensure that their cyber-security measures evolve over time. This includes regularly reviewing and updating policies and procedures, testing them to ensure they remain effective, and revising them when necessary because of changing circumstances or new threats.
J. Training and Awareness: It is fundamental to ensure that all employees, not just security personnel, are fully aware of the guidelines and their roles in maintaining cyber security. This can be achieved through regular training and updates.
K. Incident Response Planning: Develop an incident response plan that anticipates potential cyber incidents and outlines a clear response strategy to handle and recover from such events efficiently.
L. Compliance and Legal Considerations: Understand the legal implications related to Cybersecurity within your jurisdiction and ensure your policies comply with those laws.
M. Compliance Monitoring and Reporting:
o Establish mechanisms for monitoring and reporting on compliance with ISO/IEC 27032.
o Regularly review cybersecurity performance metrics and adjust strategies accordingly.
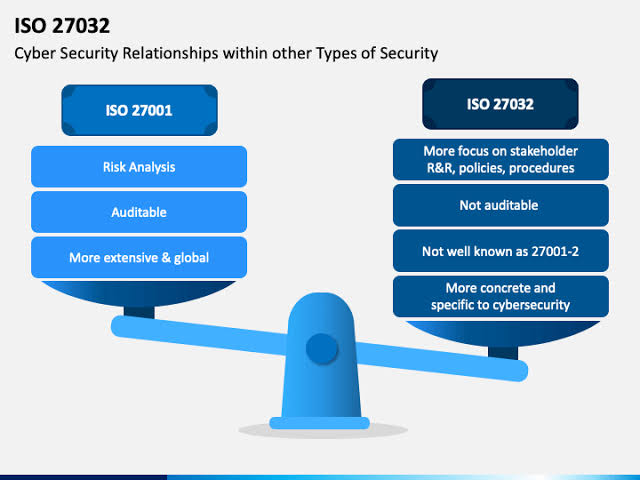
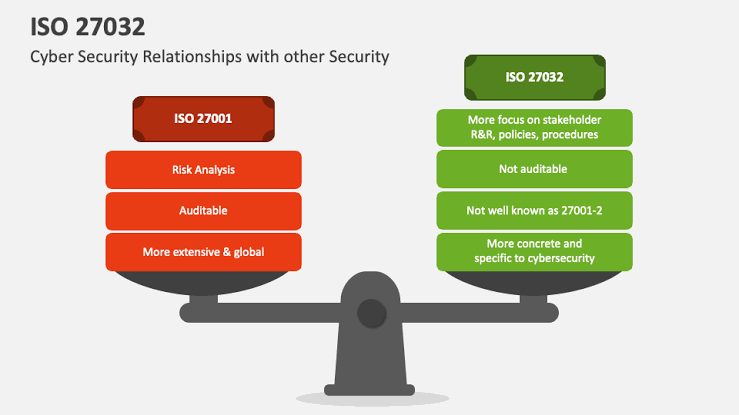
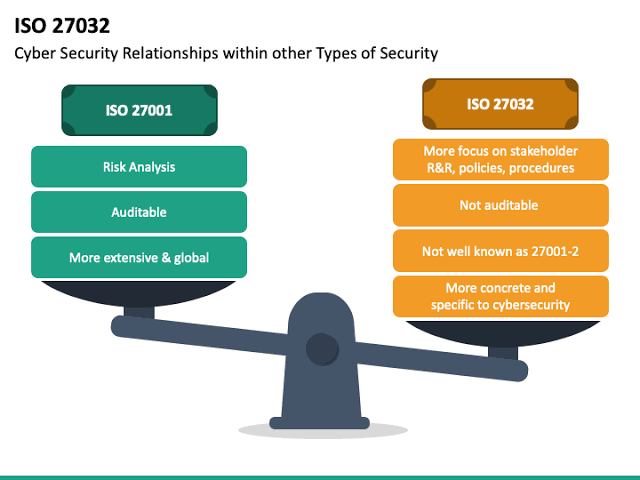
N. Cross-referencing with Other Standards: ISO/IEC 27032 may be used in conjunction with other standards such as ISO/IEC 27001 (ISMS) and ISO/IEC 27002 (code of practice for information security controls), ensuring a comprehensive approach to Cybersecurity.
iii. Benefits of Implementation
o Enhanced Cybersecurity Posture: Proactive risk management and mitigation strategies lead to a more secure cloud environment.
o Improved Data Protection: Implementing strong data security controls safeguards sensitive information in the cloud.
o Compliance and Regulation: Adherence to industry standards and regulations demonstrates commitment to data security and builds trust with customers and partners.
o Increased Business Continuity: Robust incident response and disaster recovery plans minimize disruptions and ensure continuous operations.
o Competitive Advantage: Demonstrating a proactive approach to cybersecurity can differentiate your organization and attract clients.
iv. Challenges and Considerations
o Resource Requirements: Implementing and maintaining ISO/IEC 27032 requires dedicated resources, including personnel with expertise in cloud security and compliance.
o Complexity of Cloud Environments: Adapting controls to dynamic and complex cloud environments can be challenging and require ongoing adjustments.
o Change Management: Transitioning to a new security framework necessitates effective change management strategies to overcome resistance and ensure widespread adoption.
v. Conclusion
Embracing ISO/IEC 27032 as IT and security leaders is not just a compliance exercise; it’s an investment in building a more secure and resilient future for your organization in the digital age. By understanding the benefits, key steps, and challenges, you can effectively navigate the implementation process and reap the rewards of enhanced cybersecurity posture, data protection, and sustainable business success.
As an IT and Security Leader, by aligning with ISO/IEC 27032, you not only protect the organization against Cybersecurity threats but also demonstrate commitment to best practices in Cybersecurity, which can enhance the trust and confidence of customers, stakeholders, and partners.
As IT and security leaders, navigating the ever-evolving cybersecurity landscape can be daunting. Fortunately, standards like ISO/IEC 27032 provide a valuable framework to build robust cybersecurity practices and mitigate evolving threats. This guide offers a comprehensive overview of how IT and security leaders can benefit from implementing ISO/IEC 27032:
Remember: ISO/IEC 27032 is a dynamic standard, so staying updated on revisions and emerging threats is crucial to maintain an effective cloud security posture. Continuous improvement and adaptation are key to achieving the full potential of this valuable framework.
vi. Further references
https://www.linkedin.com/pulse/fundamentals-isoiec-27032-what-you-need-know-polyd-1c
https://medium.com/@386konsult.com/iso-27032-guidelines-for-cybersecurity-management-cbb025267888