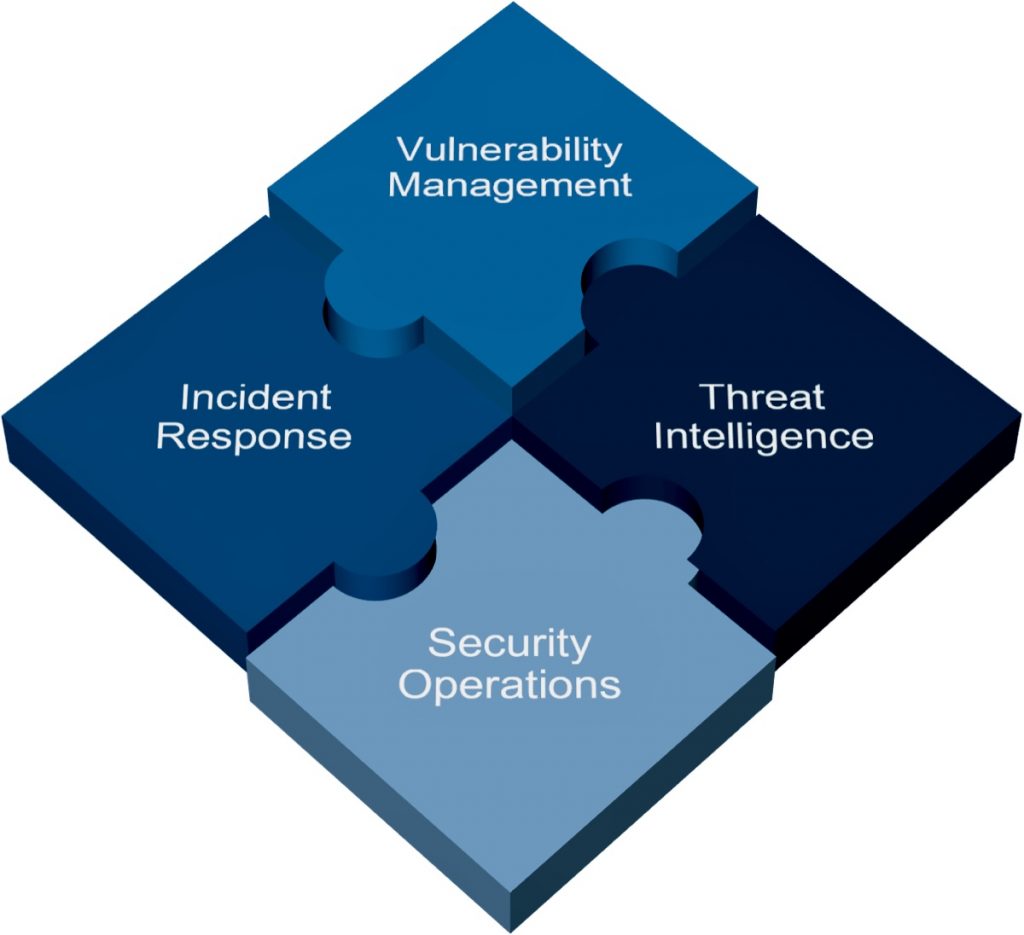
The Security Operations & Incident Management Knowledge Area in the Cyber Security Body of Knowledge (CyBOK) covers the essential procedures, technologies, and principles related to managing and responding to security incidents to limit their impact and prevent them from recurring.
i. Core Concepts:
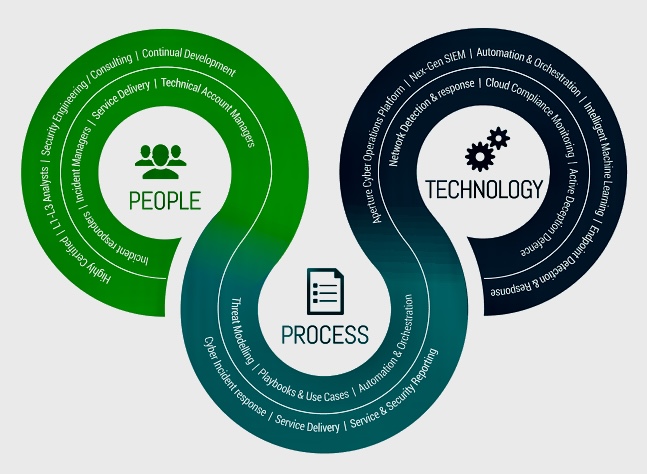
A. Monitor, Analyze, Plan, Execute (MAPE-K) Loop: The SOIM KA utilizes the MAPE-K loop as a foundational principle. This cyclical process continuously gathers information, assesses threats, plans responses, and executes actions, adapting to the evolving security landscape.
B. Security Architecture: It emphasizes the importance of a well-defined security architecture with concepts like network segmentation, security zones, and data classification for effective monitoring and incident response.
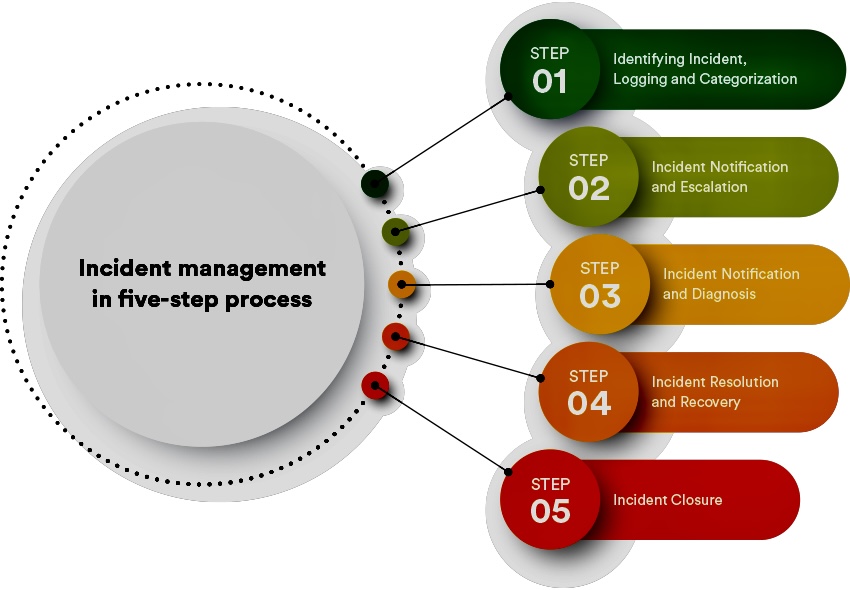
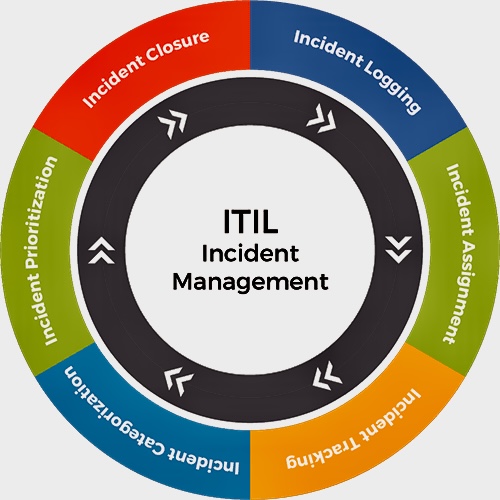
C. Incident Management: This is the core focus of the KA, outlining established frameworks like NIST SP 800-61 and best practices for detection, containment, eradication, recovery, and reporting of security incidents.
ii. Here is an outline of the key topics addressed within this area:
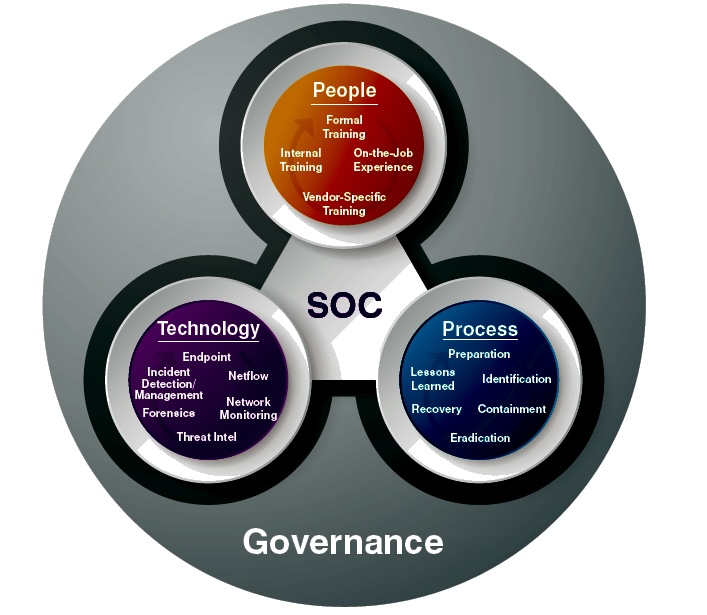
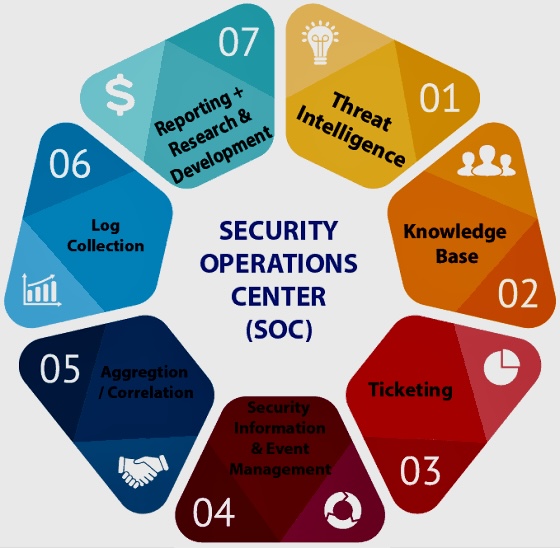
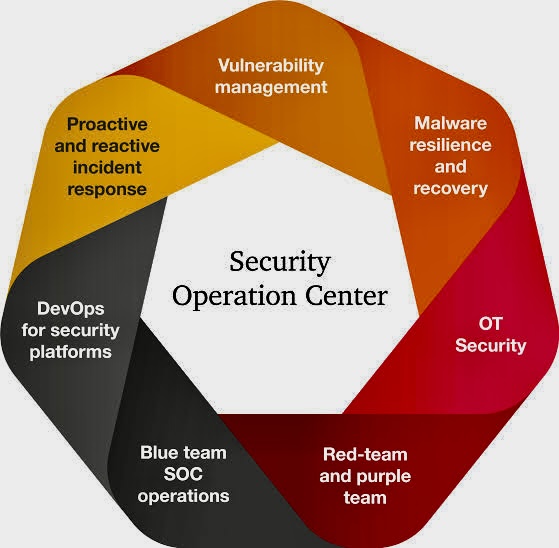
A. Security Operations Center (SOC): A central unit that deals with security issues on an organizational and technical level. The SOC team is responsible for the ongoing, operational component of enterprise information security.
B. Monitoring and Detection: This covers the fundamental concepts of cybersecurity monitoring and the techniques and systems used to detect abnormal behavior or transactions that may indicate a security incident.
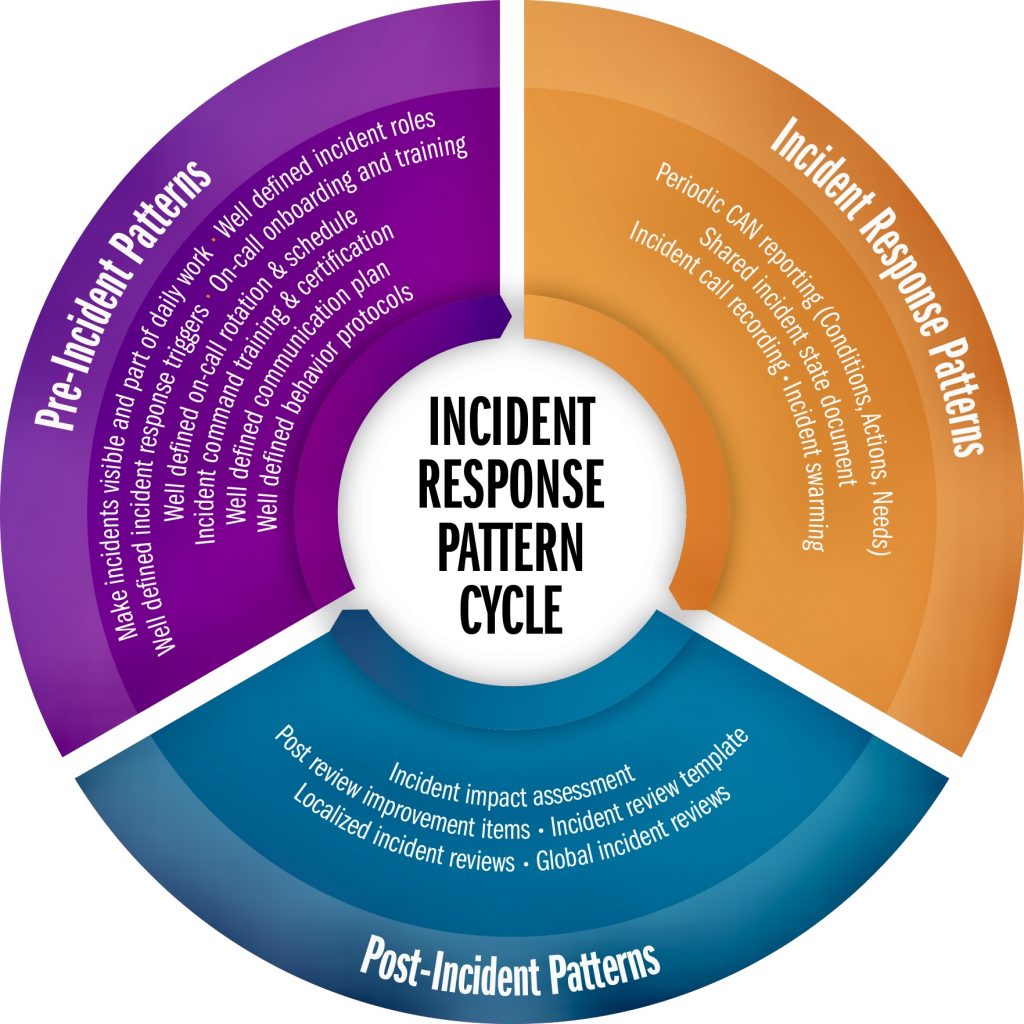
C. Incident Detection and Analysis: Techniques for identifying suspicious activity, analyzing logs and alerts, and determining the scope and nature of incidents are explored.
D. Incident Response: A planned approach to managing the aftermath of a security breach or cyber attack, also known as an IT incident, computer incident, or security incident. The goal is to handle the situation in a way that limits damage and reduces recovery time and costs.
E. Forensics: This part involves investigation and analysis techniques to gather and preserve evidence from a particular computing device in a way that is suitable for presentation in a court of law.
F. Security Information and Event Management (SIEM): SIEM is an approach to security management that combines SIM (security information management) and SEM (security event management) functions into one security management system.
G. Business Continuity and Disaster Recovery (BCDR): The KA emphasizes the importance of robust BCDR plans to ensure operational continuity and data recovery in case of security incidents or other disruptions. These are the processes that an organization implements to recover and protect its business IT infrastructure in the event of a disaster. BCP guarantees that an organization can continue to function during and after a disaster.
H. Threat Intelligence: Gathering and analyzing threat intelligence plays a crucial role in proactive defense. The KA covers various sources of threat intelligence and its integration into security operations. This includes the collection and analysis of information regarding emerging or existing threat actors and threats to understand their motives, intentions, and methods.
iii. Benefits of Utilizing the SOIM KA:
A. Standardized Knowledge and Skills: The KA provides a common language and framework for security professionals, facilitating improved communication and collaboration within security teams.
B. Effective Incident Response: Implementing the principles and strategies outlined in the KA leads to more efficient and effective incident response, minimizing damage and downtime.
C. Cybersecurity Maturity: Integrating the SOIM KA into organizational security practices contributes to overall cybersecurity maturity, enhancing the organization’s resilience against cyber threats.
iv. Resources:
o The CyBOK SOIM KA document is available for free download on the CyBOK website: [https://www.cybok.org/knowledgebase1_1/](https://www.cybok.org/knowledgebase1_1/)
o Additional resources like presentations, webinars, and training materials are also available on the website.
The Security Operations & Incident Management Knowledge Area of CyBOK is essential to anyone responsible for maintaining an organization’s security posture and responding to security incidents.
By leveraging the CyBOK SOIM KA, cybersecurity professionals can gain valuable knowledge and skills to enhance their incident response capabilities, protect critical information, and ensure the resilience of their organizations in the face of ever-evolving cyber threats.
https://www.cybok.org/media/downloads/Security_Operations_Incident_Management_v1.0.2.pdf
