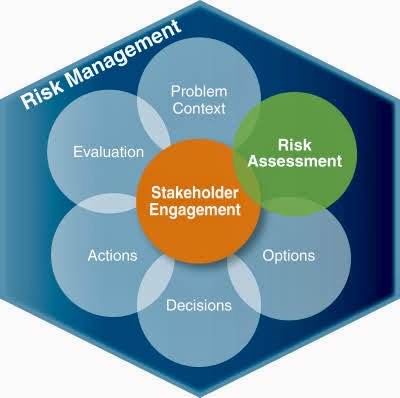
i. Executive Summary
In the digital age, robust information security (InfoSec) is paramount for organizational success. This insight evaluates the efficacy of single security frameworks in adequately addressing InfoSec risks.
While proponents highlight standardization, comprehensiveness, and reduced complexity, limitations like lack of agility, one-size-fits-all limitations, and potential vendor lock-in raise concerns.
Ultimately, a single framework is unlikely to suffice. Instead, a layered, risk-based approach utilizing multiple frameworks and continuous improvement is recommended for effective InfoSec risk mitigation.
ii. Introduction
The ever-evolving threat landscape demands effective InfoSec strategies. Security frameworks offer standardized methodologies for mitigating diverse risks.
However, the question arises: can a single framework adequately address all InfoSec risks?
The efficacy of a single security framework in safeguarding information security (InfoSec) is a topic fraught with complexities and nuances. While the allure of simplicity and standardization beckons, the ever-evolving threat landscape and unique organizational contexts cast doubt on the adequacy of a one-size-fits-all approach.
This insight delves into the merits and limitations of single frameworks, ultimately advocating for a multi-faceted strategy built on layered frameworks, dynamic adaptation, and risk-based prioritization.
iii. The Enticing Allure of Unity
Proponents of single frameworks highlight their promise of standardization, fostering streamlined policy creation, training, and audits. Consistency across departments creates a unified understanding of security best practices, facilitating efficient communication and collaboration.
Additionally, comprehensive frameworks offer a baseline level of protection for diverse assets and systems, addressing common threats and vulnerabilities. This seemingly eliminates the need for navigating complex, competing methodologies, reducing organizational complexity and resource allocation struggles.
Finally, standardized frameworks cultivate a shared understanding of InfoSec principles, empowering employees to identify potential threats and fostering a culture of security awareness.
However, the adequacy of a security framework must also be scrutinized in light of its strengths:
A. A Unified Approach:
A comprehensive framework can help unify disparate processes and standards across an organization, creating a common language and understanding of security.
B. Structured Implementation:
Frameworks provide structured methodologies for implementing security practices, making the process manageable and measurable.
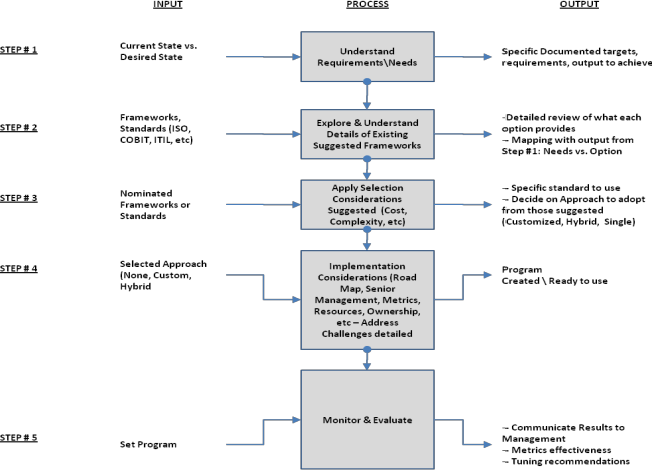
C. Resource Allocation:
Frameworks also guide organizations on how to prioritize resources, including time, personnel, and financial investments, to address the most significant risks.
D. Benchmarking and Improvement:
They offer benchmarks against which an organization can measure its security posture and pursue continuous improvement.
In conclusion, while a single security framework can offer significant benefits in providing a structured and unified approach to managing information security risks, it is unlikely to be wholly adequate given the dynamic and complex nature of threats, the specificity of industries, and the continuous evolution of technology.
iv. The Fissures in the Monolithic Approach
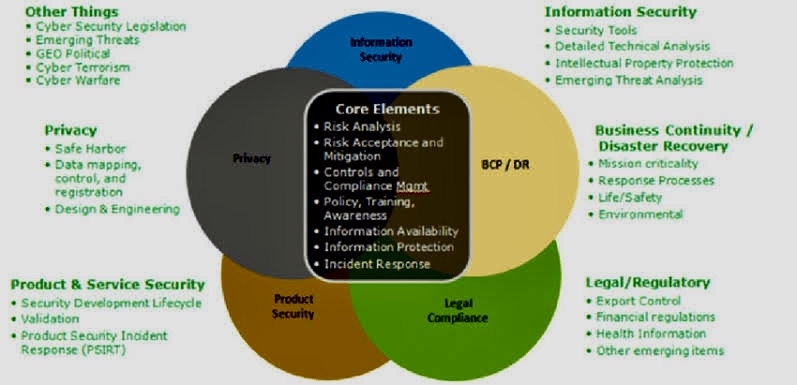
However, beneath the surface of these alluring benefits lie inherent limitations that can severely compromise the effectiveness of single frameworks.
The most glaring issue is the one-size-fits-all fallacy. Generic controls often prove inadequate for addressing the specific threats and vulnerabilities faced by individual organizations.
Industry-specific regulations, unique technological implementations, and varying risk profiles necessitate tailored controls and strategies that a single framework often lacks. This can lead to a false sense of security in areas with insufficient defenses and exposed vulnerabilities in areas requiring more stringent controls.
Furthermore, the static nature of frameworks struggles to keep pace with the rapidly evolving threat landscape. Emerging attack vectors and innovative malware often outmaneuver established controls, leaving organizations vulnerable to novel threats. Single frameworks lack the agility to adapt to these dynamic challenges, potentially creating critical gaps in the security posture.
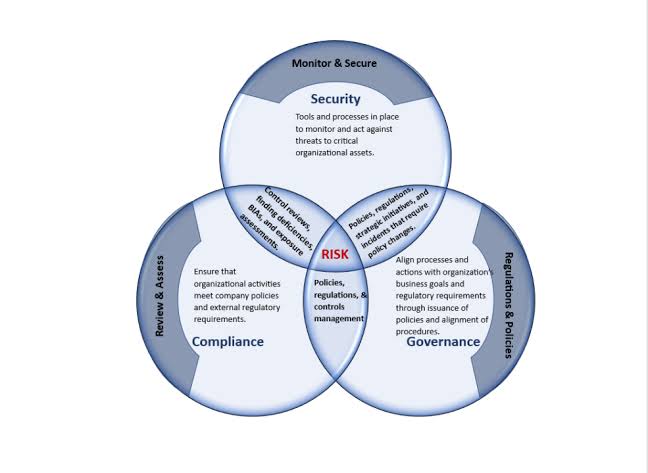
Moreover, frameworks can inadvertently lead to overkill or underkill. In low-risk areas, stringent controls might prove unnecessarily burdensome and resource-intensive.
We must consider a variety of factors including the nature of cyber threats, the diversity of organizational environments, and the evolving landscape of technology and regulations.
A. The Nature of Cyber Threats:
Cyber threats are varied and sophisticated, ranging from targeted attacks by skilled adversaries to broad-spectrum campaigns exploiting common vulnerabilities. The adaptability of attackers means that defense mechanisms have to be equally dynamic. A static, single-framework approach may not provide the agility needed to respond to new threats as they emerge.
B. Organizational Diversity:
Enterprises differ vastly in terms of size, complexity, industry, and the data they handle. For instance, a small business may not require the same depth of controls as a multinational corporation. Similarly, industries like healthcare, finance, and defense have specific regulatory requirements which may not be fully covered by a generic framework.
C. Evolution of Technology:
Technology landscapes are rapidly changing with cloud computing, Internet of Things (IoT) devices, and mobile computing. Each enters new risk vectors which may not have been fully considered when the framework was created. A single framework might struggle to keep pace with the rate of innovation.
D. Compliance and Regulations:
Different jurisdictions have varying laws and regulations that organizations must comply with, such as GDPR, HIPAA, and CCPA. A single framework might not satisfy all legal and regulatory requirements across different geographies.
E. Limitations of Frameworks:
Most security frameworks offer a set of best practices and controls designed to manage risk, but they do not provide specific prescriptions to tackle specific threats. There is always a gap between the generalized recommendations of a framework and the specific implementations that are effective in a given environment.
F. The Human Element:
Security frameworks are tools that need human implementation, interpretation, and oversight. People are often the weakest link in the security chain, whether through negligence, lack of training, or malicious intent. A single framework cannot fully address the complexities of human behavior.
Conversely, for high-risk systems, generic controls might be inadequate, creating a risky underinvestment in vital security measures. This inefficient allocation of resources undermines the overall effectiveness of the security posture.
Finally, relying on a single framework can expose organizations to the dangers of vendor lock-in. Adherence to specific controls and methodologies prescribed by the framework might restrict technology choices and limit flexibility when selecting security tools and solutions.
This dependence on specific vendors can potentially inflate costs and hinder access to innovative solutions that might prove more effective in addressing emerging threats.
v. Beyond the Binary: A Layered Defense of Adaptability and Risk
To circumvent the limitations of single frameworks, organizations should embrace a multi-faceted approach. This involves:
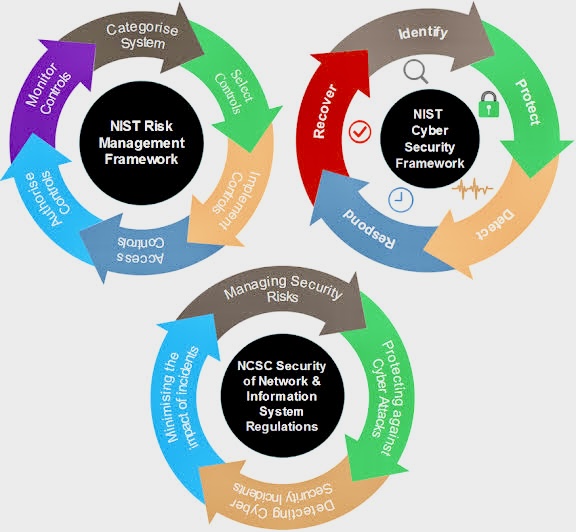
A. Layering Frameworks: Utilize a baseline framework like COBIT or ISO 27001 for overarching guidance, then layer on industry-specific or customized frameworks to address specific risks and vulnerabilities relevant to their unique environment. This offers both standardization and the necessary flexibility to adapt to specific needs.
B. Risk-Based Prioritization: Identify and prioritize risks based on their potential impact and likelihood of occurrence. Allocate resources and apply controls strategically, focusing on high-risk systems and vulnerabilities while reducing burdens in low-risk areas. This ensures efficient resource allocation and targeted mitigation efforts.
C. Continuous Improvement: Foster a culture of continuous learning and improvement. Regularly review and update the security posture, adapting frameworks and controls to keep pace with the evolving threat landscape. Proactive monitoring and vulnerability assessments should become integral parts of the InfoSec strategy.
vi. Conclusion
In conclusion, while single security frameworks offer alluring benefits of standardization and simplicity, their inherent limitations pose significant risks to organizational InfoSec.
Embracing a layered, risk-based approach that leverages multiple frameworks and prioritizes continuous improvement allows organizations to navigate the intricacies of the threat landscape with adaptability and agility.
By recognizing the limitations of a one-size-fits-all solution and actively tailoring their security strategy to their specific needs and evolving risks, organizations can build a truly resilient and effective defense against ever-evolving cyber threats.
vii. Further Exploration
This insight serves as a springboard for deeper exploration. Future research could investigate:
A. Customizing and extending a primary security framework to align with specific organizational needs.
B. Integrating additional practices and controls from other frameworks.
C. Oversight and human factors management through training, awareness, and a security-conscious culture.
D. Staying informed about emerging threats and technologies and being prepared to rapidly update and evolve security practices accordingly.
E. The development of dynamic, adaptable frameworks that can adjust to changes in the threat landscape.
F. The role of artificial intelligence and machine learning in automating risk assessment and control optimization.
G. The efficacy of collaborative threat intelligence sharing and community-driven security models.
By continuously researching and innovating, organizations can stay ahead of the curve and ensure their valuable information assets are protected in the dynamic and ever-challenging world of InfoSec.
https://dergipark.org.tr/en/download/article-file/147957
https://www.onetrust.com/blog/security-framework-types/
https://www.linkedin.com/advice/0/what-steps-choosing-right-security-framework
