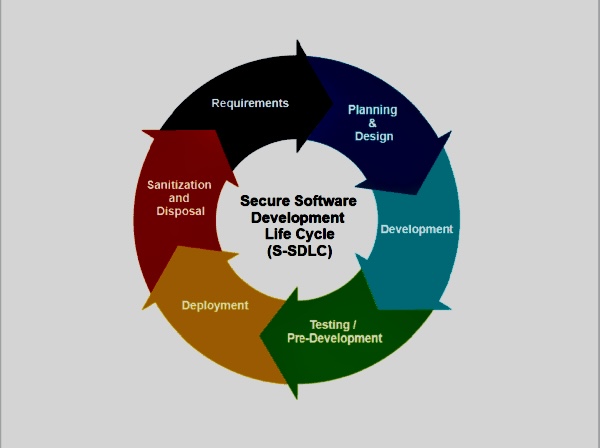
The CyBOK Secure Software Lifecycle Knowledge Area (SSLKA) delves into the processes and practices involved in developing secure software throughout its entire lifecycle, from the initial design phase to deployment and ongoing operation.
i. It’s geared towards both academic and industry audiences, serving as a guide for:
A. Academics:
o Designing courses and curricula: The SSLKA provides a framework for structuring educational programs focused on secure software development.
o Verifying skills and knowledge: It establishes a baseline for assessing expertise in secure software lifecycle practices.
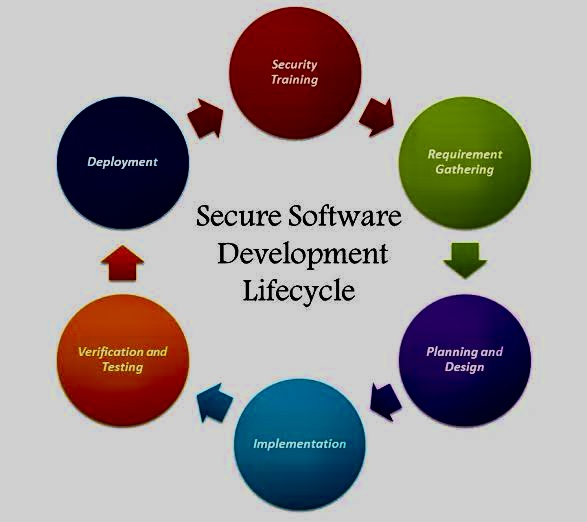
B. Industry Professionals:
o Implementing secure software development processes: The SSLKA offers practical guidance on integrating security considerations into each stage of the software lifecycle.
o Selecting appropriate models and approaches: The knowledge area explores different secure software lifecycle models and helps in choosing the best fit for specific needs.
ii. Here’s a bird view of what the SSLKA covers:
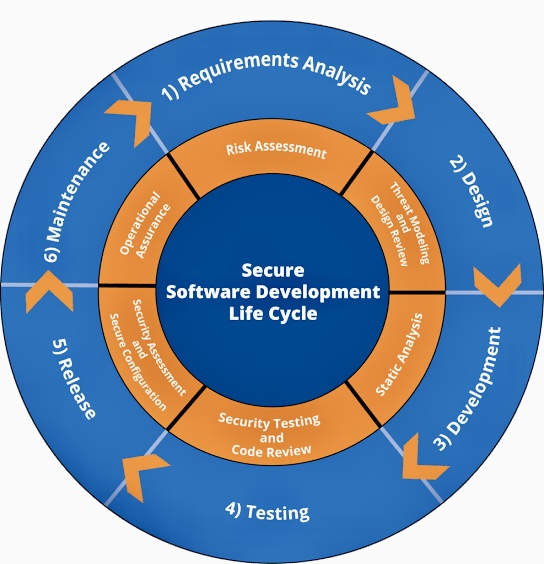
A. History of secure software lifecycle models: It provides an overview of the evolution of secure software development methodologies.
B. Components of a comprehensive software development process: The SSLKA identifies key phases and activities within the lifecycle, emphasizing security integration at each stage.
C. Techniques for preventing and detecting security defects: This section outlines proactive measures and reactive tools for identifying and correcting vulnerabilities throughout the lifecycle.
D. Responding to exploits: The knowledge area guides on addressing security incidents after software deployment.
The Secure Software Lifecycle Knowledge Area within CyBOK deals with the principles, practices, and techniques that ensure software is developed and maintained in a manner that preserves its security.
iii. It encompasses the following concepts and activities:
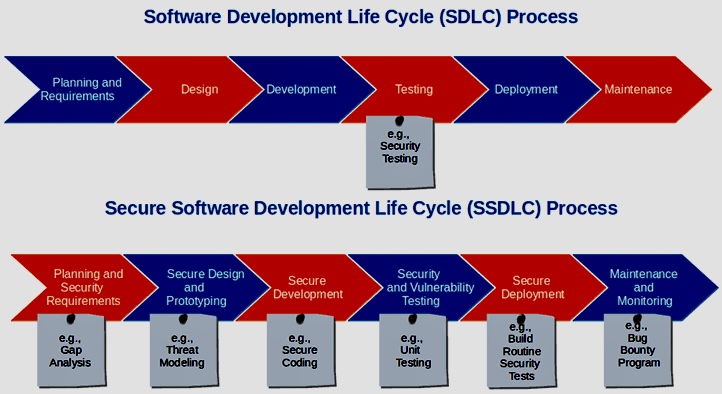
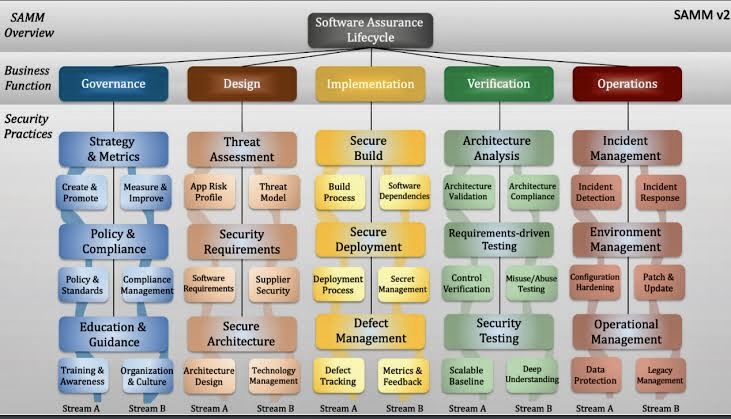
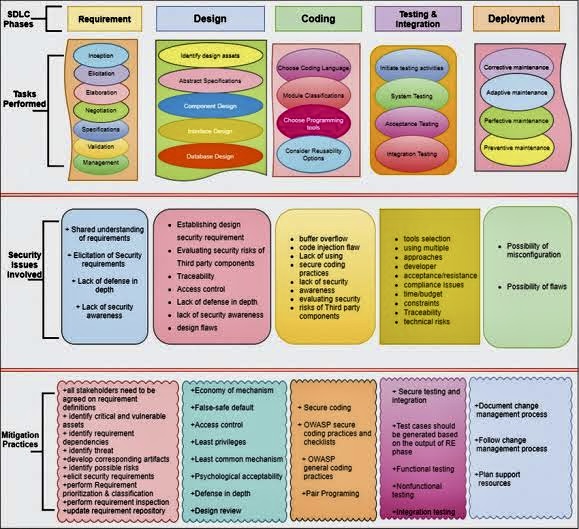
A. Security in the Software Development Lifecycle (SDLC): This discusses the importance of incorporating security right from the planning stage through to the maintenance stage in the SDLC.
B. Secure Development Policies and Standards: Establishing organizational policies and standards that guide secure software development practices.
C. Security Requirements Engineering:
o Identification of Security Requirements: Identifies and documents the necessary security controls required for the system based on the vulnerabilities that may be exploited.
o Secure Functional Requirements: Establishes secure functions the software should be able to perform.
o Secure Software Assurance Requirements: Ensures that the software meets certain security standards.
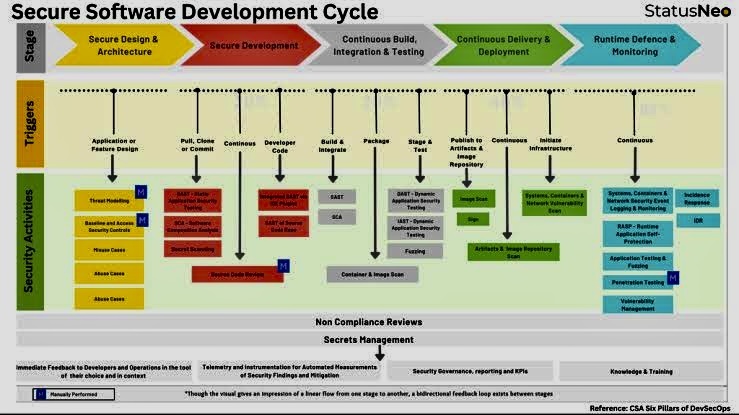
D. Secure Design:
o Threat Modelling: Involves identifying potential threats and vulnerabilities to devise mechanisms to counteract them.
o Security Architecture and Design Reviews: Discusses the need for rigorous reviews of software’s architecture design from a security perspective.
E. Secure Coding Practices: Writing code that adheres to best practices to mitigate common vulnerabilities, such as those listed in the OWASP Top 10 or CWE listings.
F. Security Testing: Applying a variety of testing methods to identify and rectify security weaknesses. This includes static and dynamic analysis, penetration testing, and code reviews.
G. Secure Deployment and Configuration Management:
Security should not end with the development phase; deployment is a crucial juncture. CyBOK advocates for secure deployment practices and meticulous configuration management to ensure that the software operates securely in its intended environment.
H. Secure Software Lifecycle Management: Overseeing the entire lifecycle with a focus on maintaining security at every phase, from initial conception through to end-of-life.
I. Operational Security and Maintenance:
o Patch and Vulnerability Management: Discusses managing software updates and handling discovered vulnerabilities.
o Incident reporting and Response: Covers the process of responding to and handling security threats after deployment.
J. Security Incident Management in Software: Preparing for and responding effectively to security incidents that may affect software.
K. Supply Chain Security: Understanding and managing the risks associated with third-party components, including open-source software and vendor-supplied systems.
L. Security Awareness and Training:
Recognizing that human factors play a pivotal role in security, CyBOK promotes security awareness and training programs. Educated and informed personnel are less likely to engage in risky behaviors that could compromise security.
M. End-of-Life Software: Managing the risks associated with software that has reached its end of support or end of life.
iv. Overall, the SSLKA aims to:
o Reduce the risk of vulnerabilities entering production software.
o Improve the overall security posture of developed applications.
o Embed security as a core principle within software development practices.
It’s important to note that the SSLKA complements other CyBOK Knowledge Areas, particularly the Software Security Knowledge Area, which focuses on specific vulnerabilities and mitigation techniques.
v. Conclusion:
In conclusion, CyBOK’s Secure Software Lifecycle Knowledge Area provides a comprehensive framework to embed security throughout the software development process.
By integrating security measures from the requirements phase to deployment and beyond, organizations can enhance their resilience against the ever-evolving landscape of cyber threats. Embracing these principles not only fortifies individual software projects but contributes to a more secure digital ecosystem as a whole.
vi. Here are some additional resources that might assist in acquiring more knowledge in this area:
A. Books:
o “Software Security: Building Security In” by Gary McGraw
o “Secure by Design” by Dan Bergh Johnsson, Daniel Deogun, and Daniel Sawano
o “Threat Modeling: Designing for Security” by Adam Shostack
B. Research Papers & Reports:
o IEEE papers on secure software development life cycle
o NIST Special Publication 800-160, Volume 1 o Systems Security Engineering
o OWASP Software Assurance Maturity Model (SAMM)
C. Websites & Online Resources:
o The Open Web Application Security Project (OWASP): Offers a range of resources, including the OWASP Top 10, a standard awareness document for developers and web application security. OWASPhttps://owasp.org › www-project-sa…OWASP SAMM
o SANS (System Administration, Networking, and Security) Institute: Provides resources on various topics related to secure software development. SANS Institutehttps://www.sans.orgSANS Institute: Cyber Security Training, Degrees & Resources
o Microsoft’s Security Development Lifecycle (SDL): A software development process that helps developers build more secure software and address security compliance requirements while reducing development costs. Microsofthttps://www.microsoft.com › en-usMicrosoft Security Development Lifecycle (SDL)
D. Courses & Tutorials:
o Coursera offers courses in software security provided by the University of Maryland. Courserahttps://www.coursera.org › coursesBest Software Security Courses & Certificates Online [2024] – Coursera
o CYBRScore’s Secure Coding Practices course itsmsolutions.comhttps://www.itsmsolutions.com › …PDFCYBRSCORE® ACADEMY – itSM Solutions
o ISC(2) CSSLP o secure software lifecycle professional certification. ISC2https://www.isc2.org › certificationsCSSLP – Certified Secure Software Lifecycle Professional
E. Webinars, Podcasts, & Videos:
o CyberWire’s Podcasts related to Secure Software Development. TechTargethttps://www.techtarget.com › feature10 best cybersecurity podcasts to check out
o RSA Conference’s webcasts and videos around the topic of Secure Software Development. Secure Software Development Framework: An Industry and Public Sector ApproachYouTube · RSA ConferenceFeb 28, 2020
o YouTube channels such as OWASP, SANS Cyber Defense, and BlackHat have tons of content about Secure Software Development.
