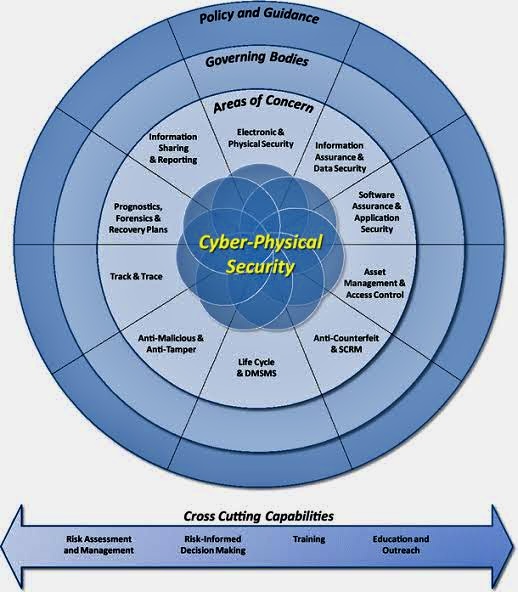
The Cyber-Physical Systems Security (CPS) Knowledge Area is part of the Cyber Security Body of Knowledge (CyBOK). It concerns the security issues that arise in systems where the virtual world of computing intersects the physical world.
Cyber-Physical Systems (CPS) are complex systems where a collection of computing devices interact with the physical world. These can include systems like industrial control systems, autonomous vehicles, medical monitoring, traffic control systems, and many others.
CPSes often have networked sensors, controls, processors, and software components that affect and are affected by their physical surroundings.
i. What are Cyber-Physical Systems (CPS)?
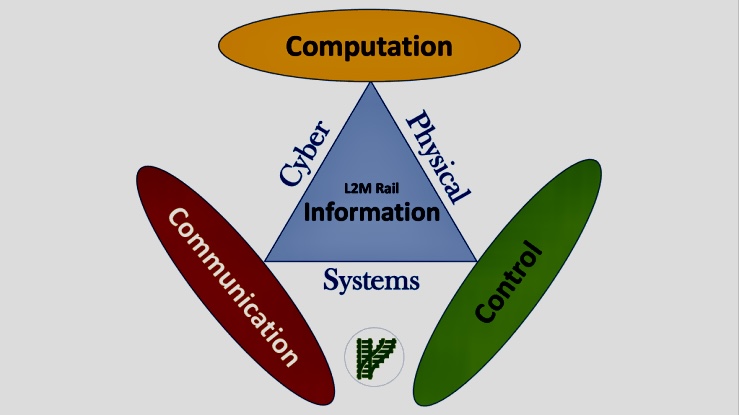
Cyber-physical systems (CPS) are engineered systems that tightly integrate computation, communication, and physical processes.
They are becoming increasingly common in a variety of industries, including:
A. Manufacturing: CPS can be used to automate production lines, optimize resource usage, and improve product quality.
B. Transportation: CPS can be used to improve traffic flow, manage congestion, and prevent accidents.
C. Healthcare: CPS can be used to monitor patients’ health, deliver medication, and perform surgery.
D. Energy: CPS can be used to manage the power grid, optimize energy consumption, and prevent blackouts.
ii. Why is CPS security important?

CPS are often critical infrastructure, and their security is essential for protecting public safety, economic stability, and national security.
Attacks on CPS can have a wide range of consequences, including:
A. Physical damage: For example, an attacker could hack into a power grid and cause a blackout.
B. Loss of life: For example, an attacker could hack into a medical device and harm a patient.
C. Economic damage: For example, an attacker could hack into a manufacturing system and cause production to stop.
iii. What are the challenges of CPS security?
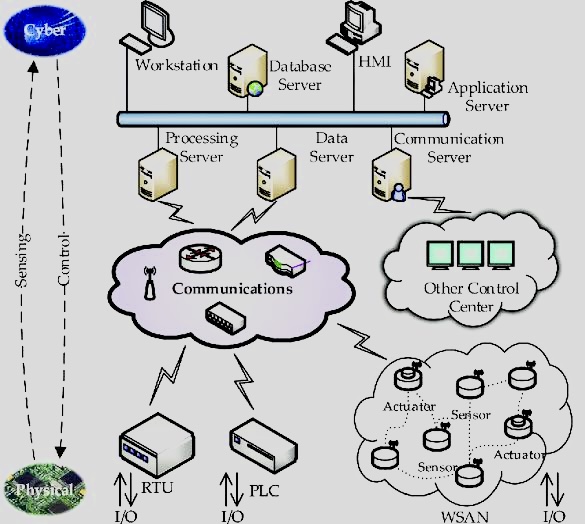
CPS security is challenging for a number of reasons, including:
A. Heterogeneity: CPS are often made up of a variety of different devices and systems, which can make it difficult to secure them effectively.
B. Legacy systems: Many CPS are based on legacy systems that were not designed with security in mind.
C. Physical access: Attackers may be able to gain physical access to CPS, which can make them more vulnerable to attack.
iv. The CPS Security Knowledge Area typically covers the following topics:
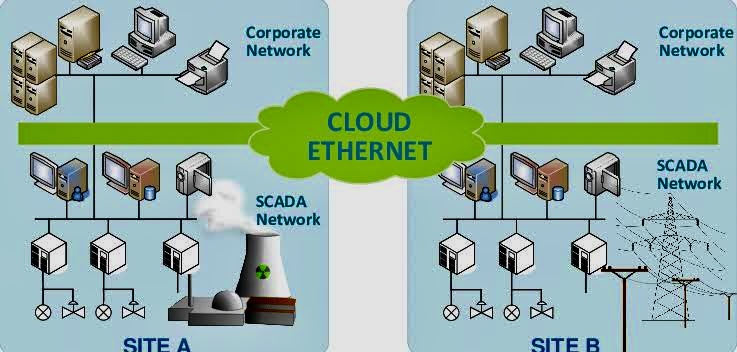
A. CPS Concepts: Understanding the basics of how CPS operates, including systems theory, real-time computing, and control theory.
B. Physical Process and System Modeling: This covers the modeling of physical systems, understanding the physical processes involved, and learning how to derive and use these models in a cybersecurity context.
C. Attacks, Threat Actors, and Incentives: This part discusses potential threats to CPS, including the motivations behind such attacks and the vulnerabilities they may target.
D. Security Technologies and Their Limitations: Understand the cybersecurity tech available for protecting CPS. This includes encryption, intrusion detection systems, secure communication protocols, etc., and understanding their limitations in different scenarios.
E. Risk Management and Security Measures: This encompasses the identification, assessment, and prioritization of risks followed by coordinated application of resources to minimize, monitor, and control the probability or impact of incidents.
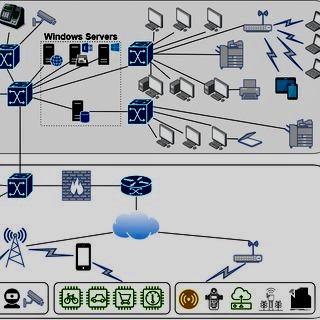
F. Resilience and Fault Tolerance: This includes strategies to ensure the CPS can continue operating safely even during attacks or failures.
G. Safety and Security Co-engineering: Simultaneous consideration and integration of both safety and security aspects during the development process can result in more robust and secure systems.
H. Security Governance and Management: Discussing the management, organization, and regulation of CPS security in various contexts, including industrial, transportation, and healthcare settings.
I. Security Lifecycle Management: Understanding the stages of the lifecycle of CPS, from requirements analysis, design, implementation, operation, maintenance, and decommission, and how security considerations are integrated at each stage.
J. Regulatory and Compliance Aspects: Discussion of legal and regulatory aspects related to critical infrastructures, and specific sectors that rely heavily on CPS.
v. Some additional resources that you may find helpful:
o The National Institute of Standards and Technology (NIST) Cybersecurity Framework for Cyber-Physical Systems (CSFv2)
o The International Electrotechnical Commission (IEC) 62443 standard for industrial automation and control systems security.
By understanding the Cyber-Physical Systems Security knowledge area, cybersecurity professionals can better protect systems that are deeply embedded in the physical world, ensuring not only digital but also physical safety.
A solid understanding of CPS Security is very useful for professionals working in fields where systems intersect with the physical world. This can range from security experts in industries using industrial control systems to software engineers working on autonomous vehicles or IoT (Internet of Things).
https://www.startus-insights.com/innovators-guide/cyber-physical-systems/
https://research.ncl.ac.uk/cplab/aboutthelab/whatarecyber-physicalsystems/
https://www.linkedin.com/pulse/cyber-physical-systems-omegaconsulting-online
